Introduction
This document describes the required permissions for OpenDNS_Connector users.

Note: In line with re-branding efforts, the assumed AD user name "OpenDNS_Connector" has recently been updated to now be "Cisco_Connector" instead.
Overview
The Windows Connector script normally sets the required permissions for the Cisco_Connector user. However, in strict AD environments, some administrators may not be permitted to run VB scripts on their Domain Controllers, and thus need to manually replicate the actions of the Windows Configuration script. This article details what permissions are required to be set on the DC.

Note: For the purpose of this article, Cisco_Connector is assumed to be the sAMAccountName of your Connector account in AD. If you are using a custom name instead, use the same instructions with the sAMAccountName of your connector account instead of Cisco_Connector.
If the Cisco_Connector user has insufficient permissions to operate, an AD Connector shows an alert or error state in the dashboard, and the message listed when you hover over the alert is Access Denied to one of the registered domain controllers.
Ensure that the Cisco_Connector user is a member of the AD Groups:
- Enterprise Read-only Domain Controllers
- Event Log Readers (only if the deployment includes Virtual Appliances)
In addition, the Cisco_Connector user must belong to the "Domain Users" and "Users" groups. You can verify the group membership of the Cisco_Connector user with the command:
dsquery user -samid Cisco_Connector | dsget user -memberof -expand
The Umbrella AD Connector performs two primary tasks for which these permissions are needed. First, it pulls LDAP information from Active Directory in order to allow you to create policies based on AD group, and to be able to display AD usernames and group names in the Umbrella Dashboard. The Replicate Directory Changes permission allows this.
Second, it collects login events from Domain Controllers, passing them to the Virtual Appliances. This allows the Virtual Appliances to create their IP-to-user mappings and thus identify users. All of the permissions apply to this with the exception of the Replicate Directory Changes permission. These permissions are required only if the deployment includes Virtual Appliances in the same Umbrella site as the Domain Controllers.

Note: In addition to setting the required permissions for the Cisco_Connector user, the Domain Controller Configuration script also registers a domain controller by issuing API calls to Umbrella. If you manually modify the permissions instead of using the configuration script, then this registration must also be done manually. Refer to Umbrella documentation on how to manually add domain controllers on the Umbrella dashboard.
Permissions required
- Replicate Directory Changes
- Event Log Readers
- Remote Admin
- Audit Policy
Replicate Directory Changes
This permission allows the Cisco_Connector user to query LDAP. This is the required permission typically given with the "Enterprise Read-Only Domain Controllers" group. This provides the Umbrella Dashboard with the information needed to display the names of AD objects, and to determine group memberships. The connector requests these attributes:
cn—The common name.
dn—The distinguished name.
dNSHostName—The device name as it is registered in DNS.
mail—Email addresses associated with the user.
memberOf—The groups that include the user.
objectGUID—The group ID of the object. This property is sent to Secure Access as a hash.
primaryGroupId—The primary group ID that is available for Users and Groups.
primaryGroupToken—The primary group token that is available only for Groups. Passwords or password hashes are not retrieved. Secure Access uses the
primaryGroupToken data in the access policy and configuration and reporting. This data is also required for each user or per-computer filtering.
sAMAccountName—The username that you use to sign into the Cisco AD Connector.
userPrincipalName—The user's principal name.
From these objectClasses:
(&(objectCategory=person)(objectClass=user))
(objectClass=organizationalunit)
(objectClass=computer)
(objectClass=group)
The built-in "Enterprise Read-only Domain Controllers" group must provide this permission, and thus the Cisco_Connector user must be a member of this group. You can verify the group's permissions or specify the permissions specifically for the Cisco_Connector user (if the group does not supply these permissions):
- Open the Active Directory Users and Computers snap-in
- On the View menu, click Advanced Features.
- Right-click the domain object, such as "company.com", and then click Properties.
- On the Security tab, select either "Enterprise Read-only Domain Controllers" or the "Cisco_Connector" user.
- If necessary, you can add the "Cisco_Connector" user by clicking "Add".
- In the Select Users, Computers, or Groups dialog box, select the desired user account, and then click Add.
- Click OK to return to the Properties dialog box.
- Click to select the Replicating Directory Changes and Read check boxes from the list.
- Click Apply, and then click OK.
- Close the snap-in.

Note: In a Parent/Child domain scenario, the "Enterprise Read-only Domain Controller" only exists in the parent domain. In this case, the permissions must be manually added for the Cisco_Connector as shown.
Event Log Readers
This change is required only if the deployment includes Virtual Appliances in the same Umbrella site as the Domain Controller. Membership in this group allows the Cisco_Connector user to read the logon events from the Event Logs.
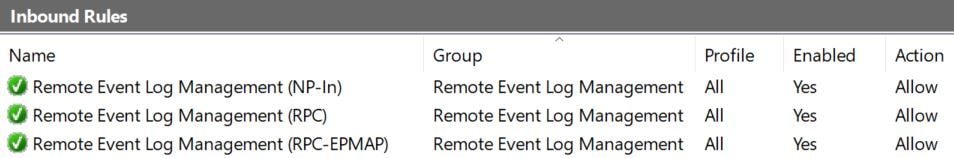
On the Domain Controller machine, in the Windows Advanced Firewall settings ensure that the Inbound rules for Remote Event Log Management (NP-In, RPC and RPC-EPMAP) are allowed. The Umbrella AD Connector may log an error saying "The RPC Server is unavailable" and may not be able to read login events if these rules are not allowed.
 360090909832
360090909832
You can also enable these rules through this command:netsh advfirewall firewall set rule group="Remote Event Log Management" new enable=yes
Remote Admin
Remote Administration is needed to allow the connector to read login events on the domain controller. This permission is required only if the deployment includes Virtual Appliances in the same Umbrella site as the Domain Controller.
From a Command prompt, please run these commands:
netsh advfirewall firewall set rule group="remote administration" new enable=yes
netsh advfirewall set currentprofile settings remotemanagement enable
 4413613529492
4413613529492
Audit Policy
This change is required only if the deployment includes Virtual Appliances in the same Umbrella site as the Domain Controller. The Audit policy defines what events get logged in the Event Log of the Domain Controller. The Connector requires that successful logon events are recorded so that users can be mapped to their IP addresses.
In normal Windows Server 2008+ environments, the legacy "Audit logon events" setting must be configured. Specifically, the "Audit logon events" policy must be set to "Success". This can be verified by running this command at a Command Prompt:
GPRESULT /z
This policy is defined as a Group Policy Object. To modify it, edit the appropriate Group Policy for your DC (typically the "Default Domain Controller Policy"), and set this policy to include "Success" events:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit Policy\Audit logon events
Please ensure that you update the Group Policy on the DC after making this change.
However, Windows Server 2008 also introduced the Advanced Audit Policy Configuration. While the legacy Windows Audit Policies can still be used, they are ignored if any of the Advanced Audit Policies are defined. Refer to Microsoft documentation to understand how the two Audit Policies interact.
For the purposes of the Connector, if any Advanced Audit Policies are defined (including ones not related specifically to logon), then the Advanced Audit Policies MUST be used.
The Advanced Audit Policy must be set for all DCs using Group Policy. Edit the appropriate Group Policy for your DC (typically the "Default Domain Controller Policy"), and go to this section:
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Logon/Logoff
In that section, set these policies to include both "Success" and "Failure" events:
Audit Logon
Audit Logoff
Audit Other Logon/Logoff Events
Ensure that you update the Group Policy on the DC after making this change.

Note: If you are deploying the AD Connector with Virtual Appliances, the firewall rule changes and audit policy settings must be done on all Domain Controllers in the domain which the Connector communicates with.
If after confirming/changing the aforementioned settings, you are still seeing "Access Denied" messages in the Dashboard, please send Umbrella Support the Connector logs as outlined in this article: Provide Support with AD Connector Logs
When providing this information to Support, include the output of these two commands:
auditpol.exe /get /category:* > DCNAME_auditpol.txt
GPRESULT /H DC_NAME.htm




 Feedback
Feedback