Introduction
This article describes how to troubleshoot the ASA Firewall blocking DNScrypt functionality.
Overview
The Cisco ASA Firewall can block the DNScrypt functionality offered by the Umbrella Virtual Appliance. This results in this Umbrella Dashboard warning:
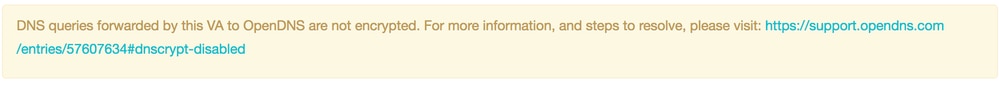
These error messages can also be seen in the ASA firewall logs:
Dropped UDP DNS request from inside:192.168.1.1/53904 to outside-fiber:208.67.220.220/53; label length 71 bytes exceeds protocol limit of 63 bytes
DNSCrypt encryption is designed to protect the contents of your DNS queries and as such also stops firewalls from performing packet inspection.
Cause
These errors must not cause any user facing impact with DNS resolution.
The Virtual Appliance sends test queries to determine the availability of DNScrypt and it is those test queries that are blocked. However, these error messages do indicate that the Virtual Appliance is not adding additional security by encrypting your company's DNS traffic.
Resolution
We recommend disabling DNS packet inspection for traffic between the Virtual Appliance and Umbrella's DNS resolvers. Although this disables the logging and protocol inspection on the ASA, it enhances security by allowing DNS encryption.

Note: These commands are provided for guidance only and it is recommended that a Cisco expert be consulted prior to making any changes to a production environment.
Also be aware this defect on ASA might affect DNS over TCP, which can also cause problems with DNSCrypt:
CSCsm90809 DNS inspection support for DNS over TCP
Packet Inspection Exceptions – IOS Commands
- Create a new ACL called 'dns_inspect' with rules to deny traffic to 208.67.222.222 and 208.67.220.220.
access-list dns_inspect extended deny udp host <Appliance IP> host 208.67.220.220 eq domain
access-list dns_inspect extended deny tcp host <Appliance IP> host 208.67.220.220 eq domain
access-list dns_inspect extended deny udp host <Appliance IP> host 208.67.222.222 eq domain
access-list dns_inspect extended deny tcp host <Appliance IP> host 208.67.222.222 eq domain
access-list dns_inspect extended permit udp any any eq domain
access-list dns_inspect extended permit tcp any any eq domain
For VA 2.2.0, please also add our 3rd and 4th resolver IPs which are also enabled for encryption. This will not be needed for 2.2.1+
access-list dns_inspect extended deny udp host <Appliance IP> host 208.67.220.222 eq domain
access-list dns_inspect extended deny tcp host <Appliance IP> host 208.67.220.222 eq domain
access-list dns_inspect extended deny udp host <Appliance IP> host 208.67.222.220 eq domain
access-list dns_inspect extended deny tcp host <Appliance IP> host 208.67.222.220 eq domain
- Remove the current DNS inspection policy on the ASA. For example:
ciscoasa(config)# policy-map global_policy
ciscoasa(config-pmap)# class inspection_default
ciscoasa(config-pmap-c)# no inspect dns
- Create a class-map matching the ACL created in Step #1:
class-map dns_inspect_cmap
match access-list dns_inspect
- Configure a policy-map under the global_policy. This must match the class-map created in Step #3. Enable DNS inspection.
policy-map global_policy
class dns_inspect_cmap
inspect dns
- Once enabled you can verify that traffic is hitting the exclusions by running:
sh access-list dns_inspect
Packet Inspection Exceptions – ASDM Interface
- First disable any DNS packet inspection if applicable.This is done in Configuration > Firewall > Service Policy Rules.
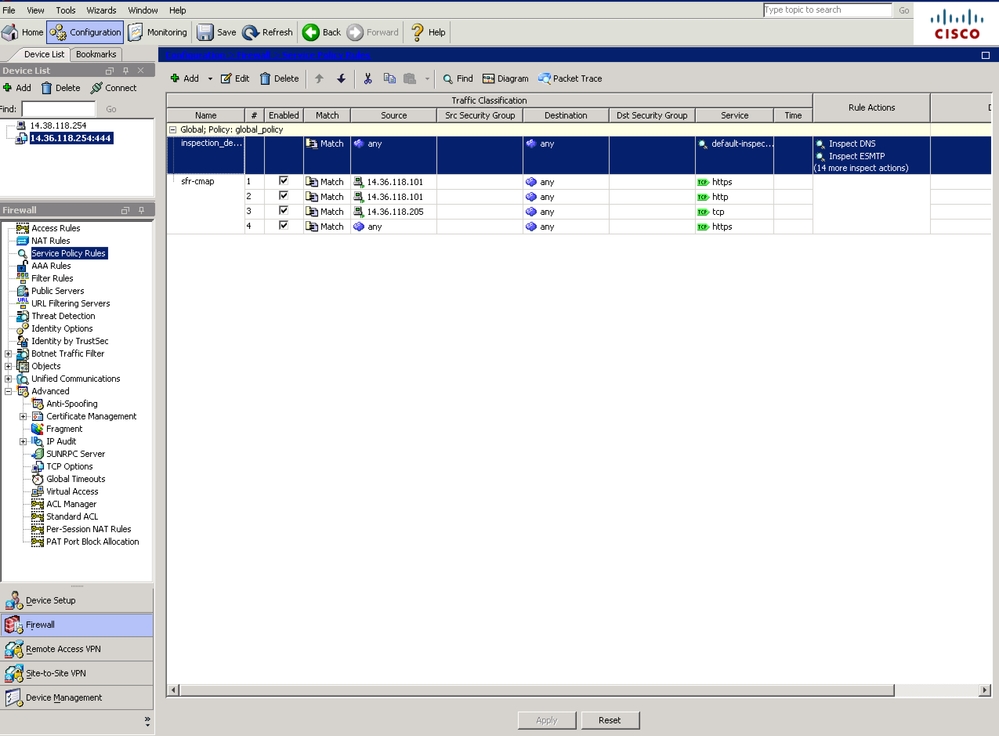
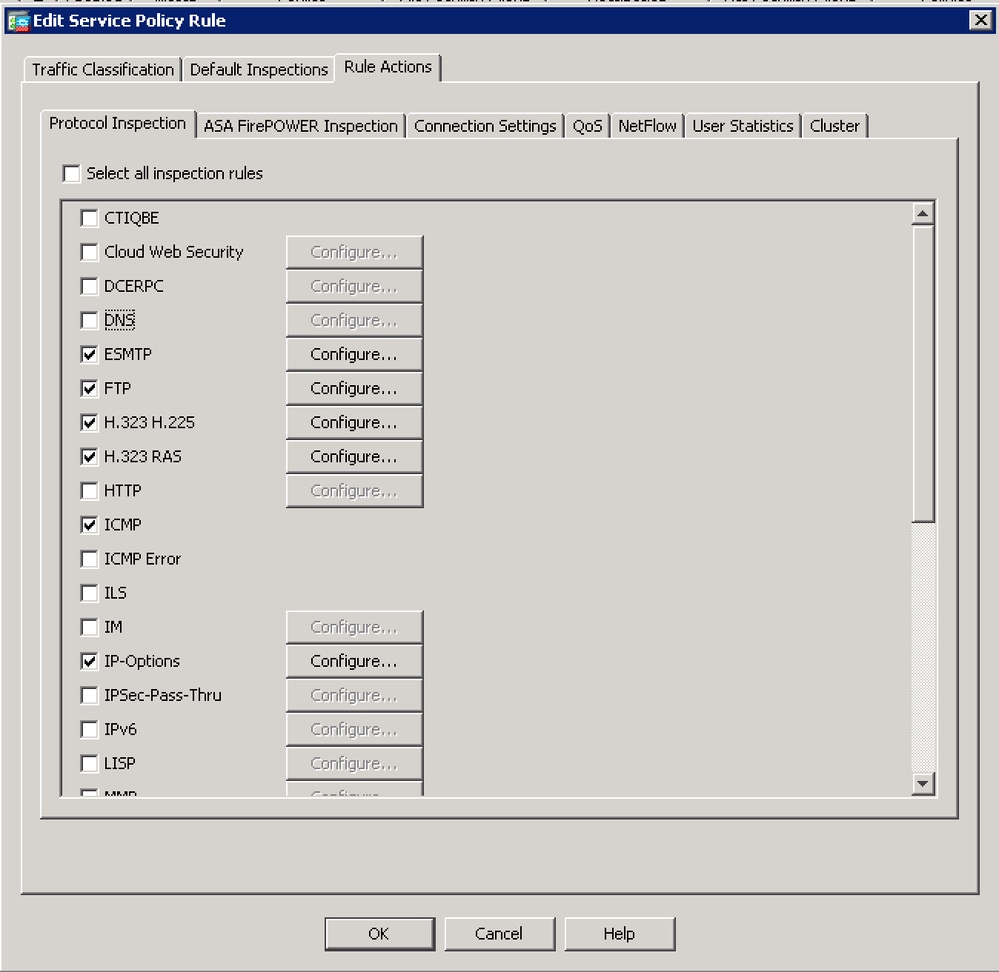
- In the example the DNS inspection is enabled under the Global Policy and 'inspection_default' class. Highlight it and click on Edit. On the new window uncheck the box for 'DNS' under the "Rule Action" tab.
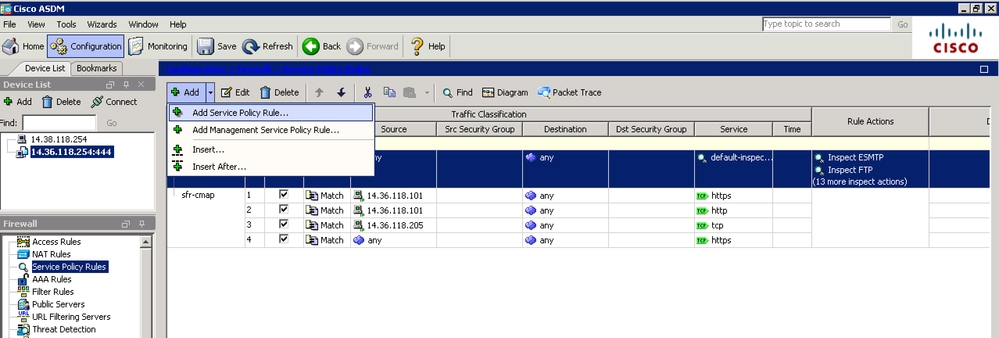
- Now you can re-configure the DNS inspection, this time with additional traffic exemptions. Click on Add > Add Service Policy Rule...
- Select "Global - Applies to all interfaces" and click on Next (you can also apply this to a specific Interface if you wish).
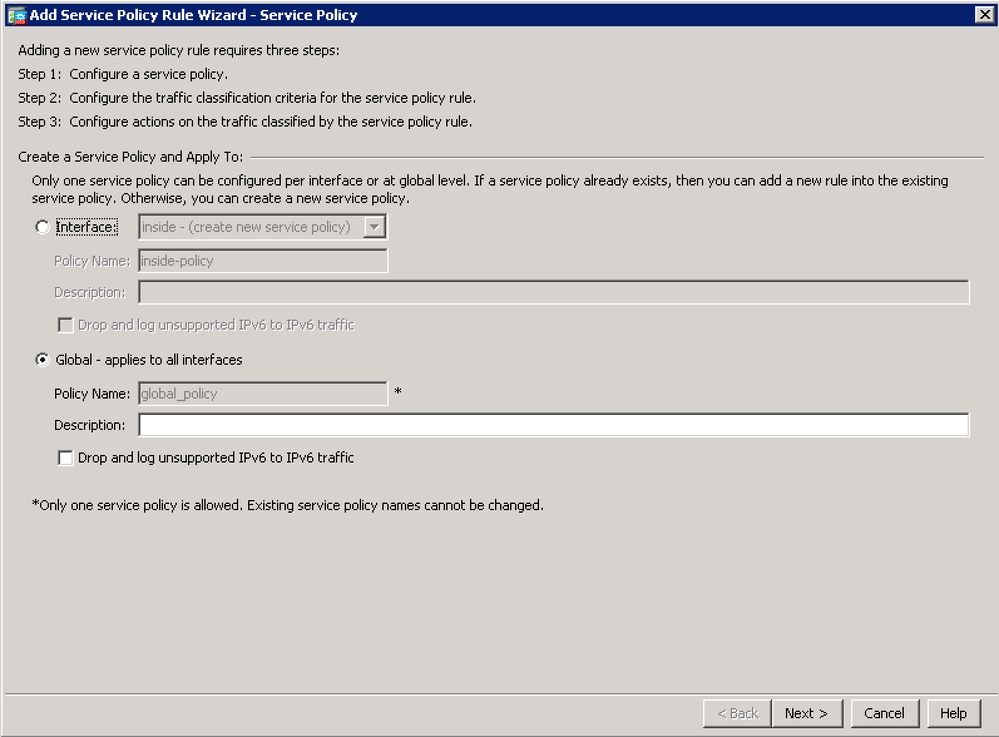
- Give a name to the class-map (for example 'dns-cmap') and check the option "Source and Destination IP Address (uses ACL)". Click Next.
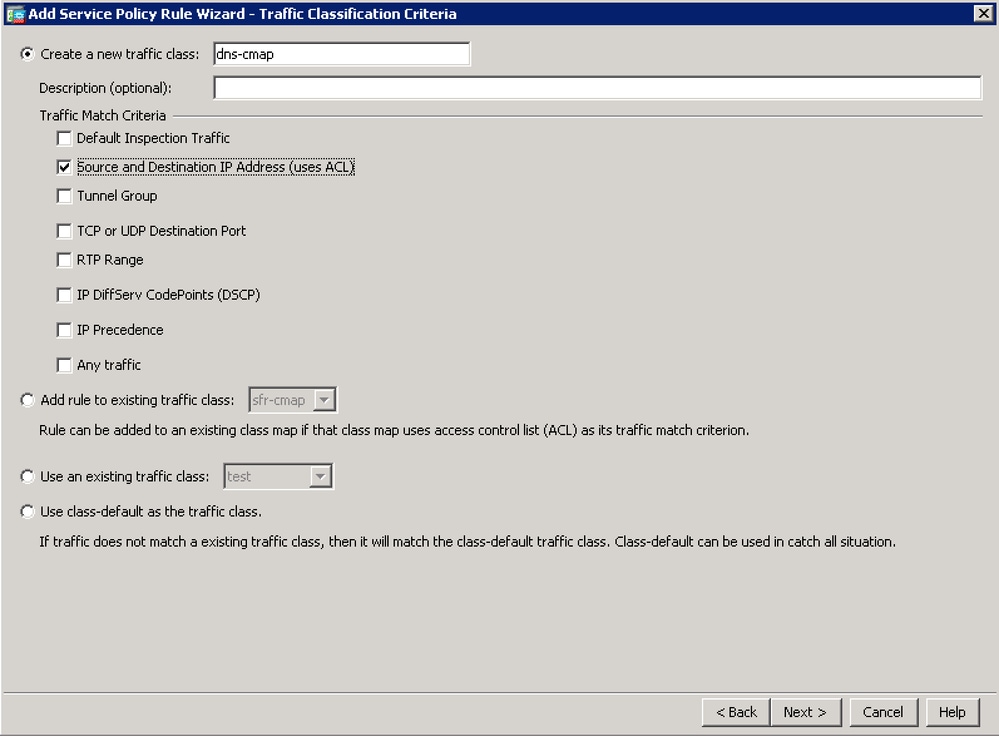
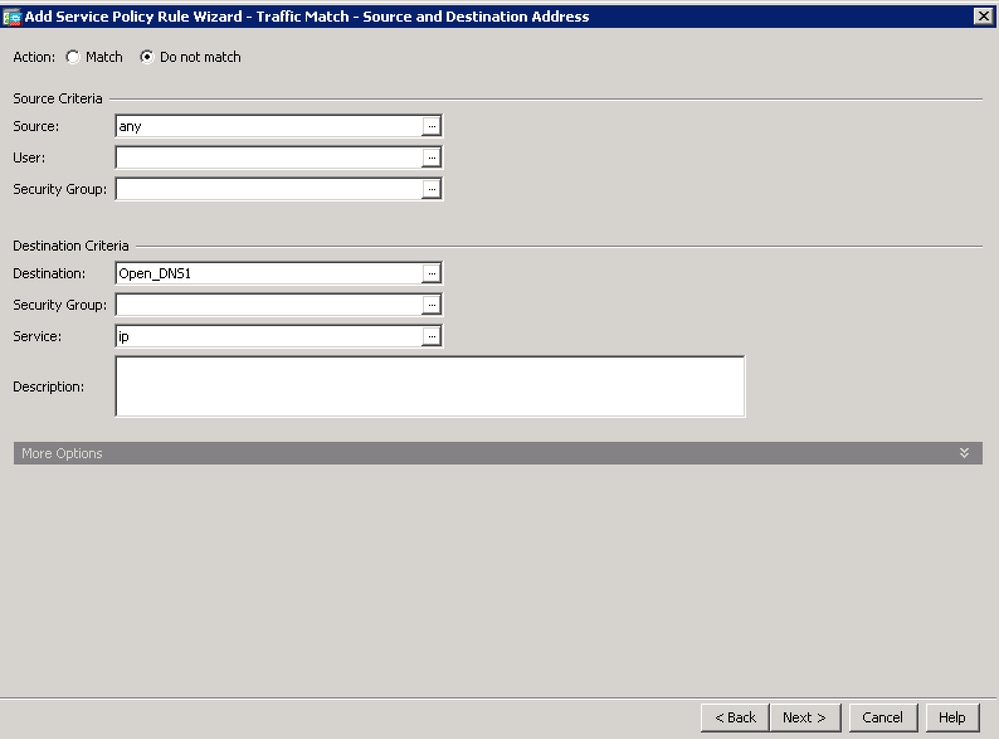
- Start by configuring the traffic that you do not want to be inspected by using the "Do not match" action.
For Source, you can use the option 'any' to exempt all traffic destined to Umbrella's DNS servers. Alternatively, you can create a Network Object definition here to only exempt the specific Virtual Appliance IP address.
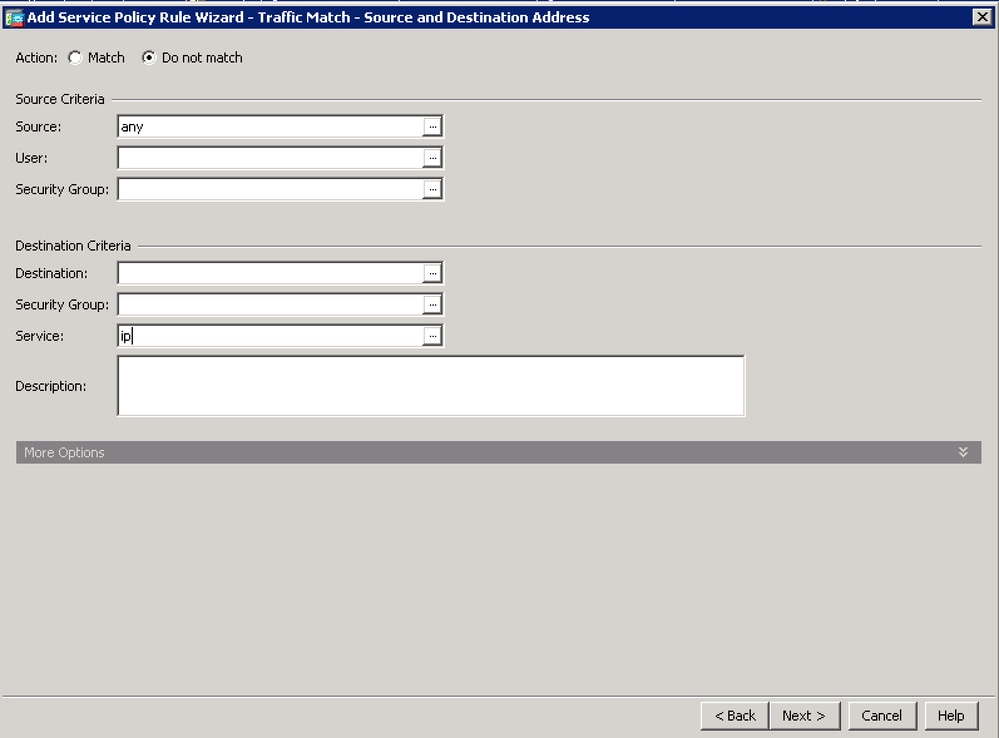
- Click ... on the Destination field. On next window, click on Add > Network Object and create an object with the IP Address of '208.67.222.222'. Repeat this step to create an object with IP Address of '208.67.220.220'.
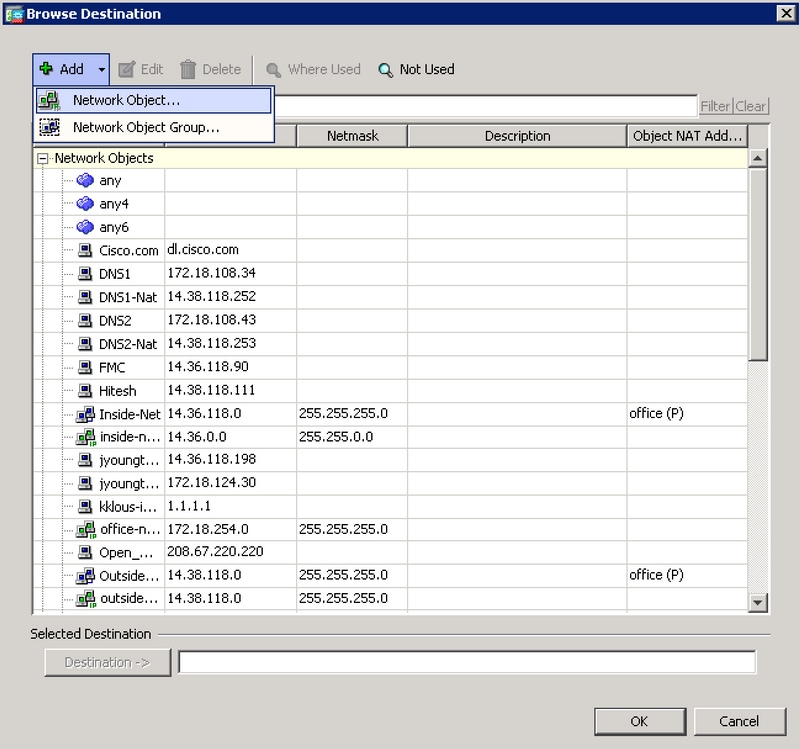
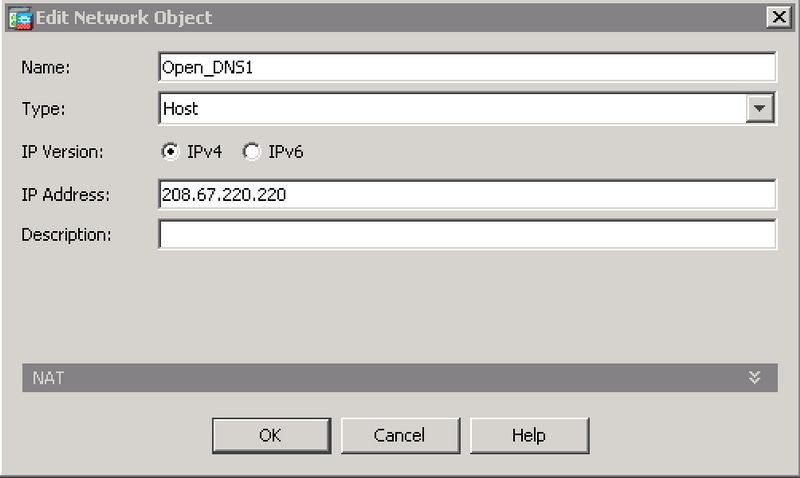
- Add both Umbrella network objects to the Destination field and click OK.
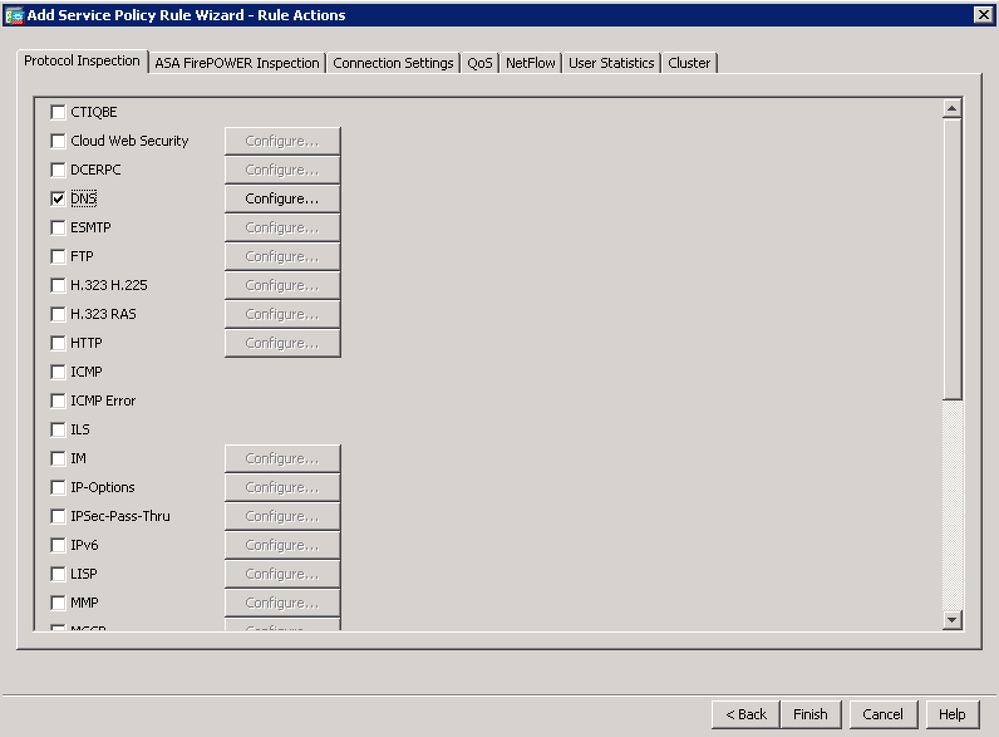
- On the next window check the box for 'DNS' and click on Finish.
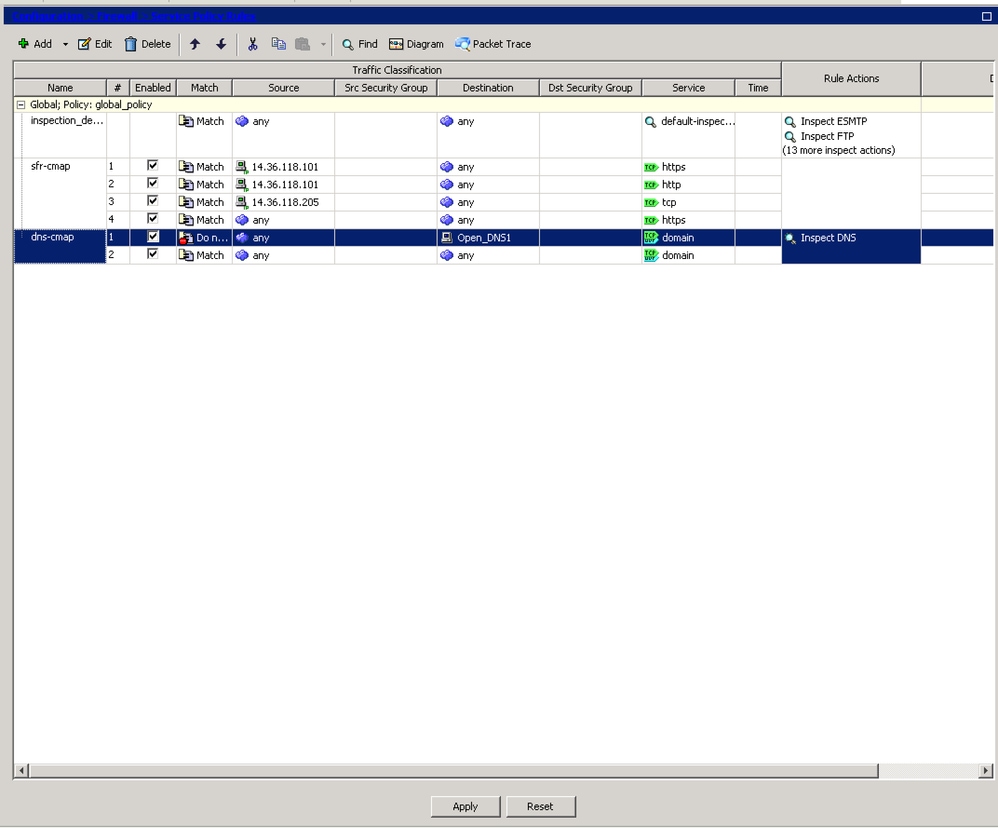
- The ASA now shows the new Global-Policy for 'dns-cmap'. Now you need to configure the remaining traffic that is inspected by the ASA. This is done by right clicking on 'dns-cmap' and selecting the option "Insert After..." which creates a new rule.
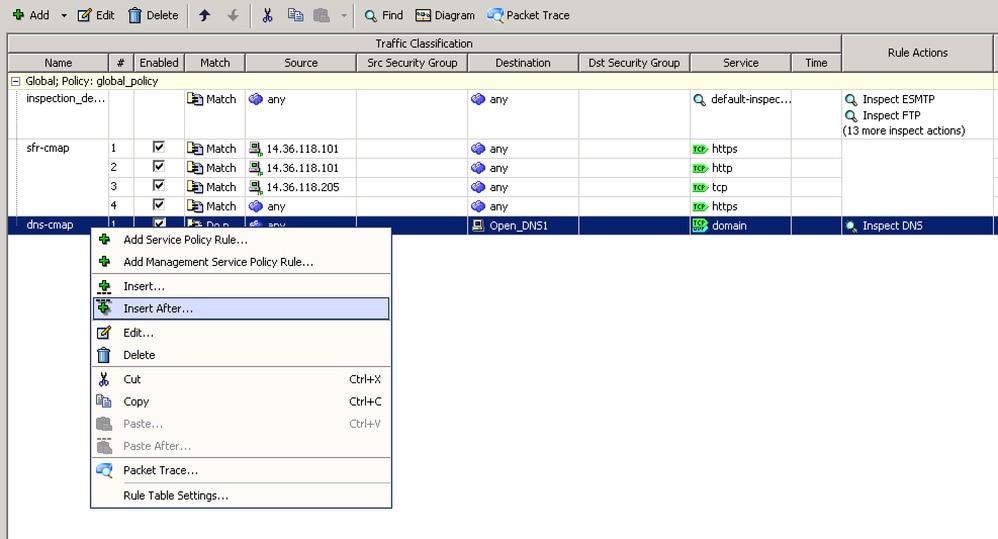
- On first window click on Next and on then check the "Add rule to existing traffic class:" radio button. Select 'dns-cmap' from the drop-down and then click Next.
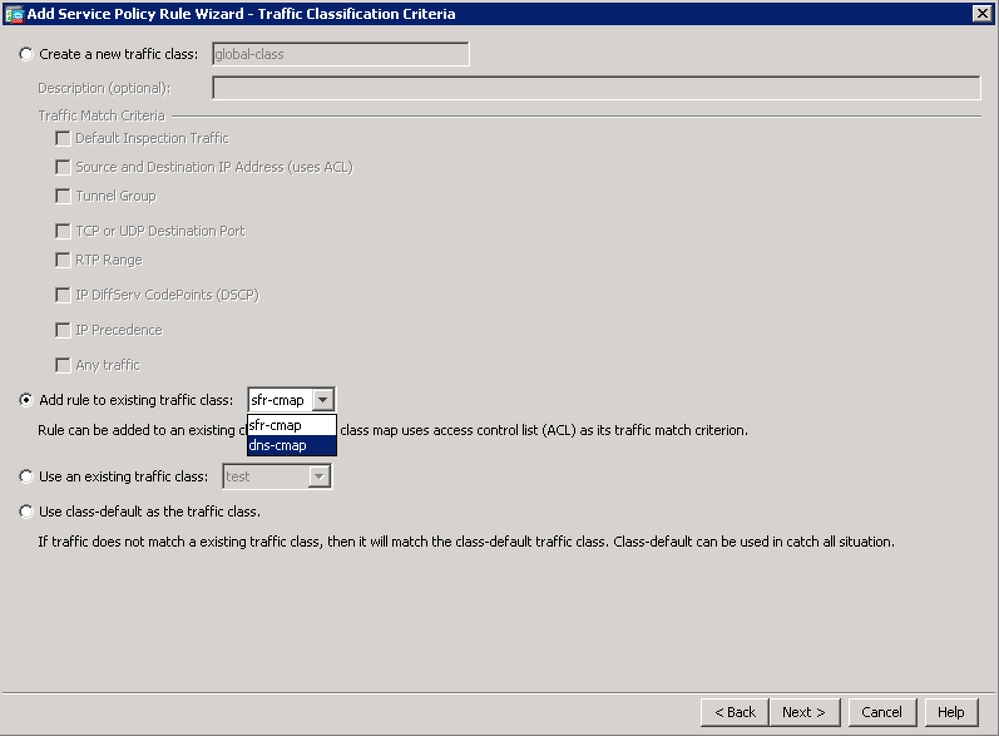
- Leave the Action as 'Match'. Choose the Source, Destination and Service of traffic that is subject to DNS inspection. Here, for example, we are matching traffic from any client going to any TCP or UDP DNS Server. Click Next.
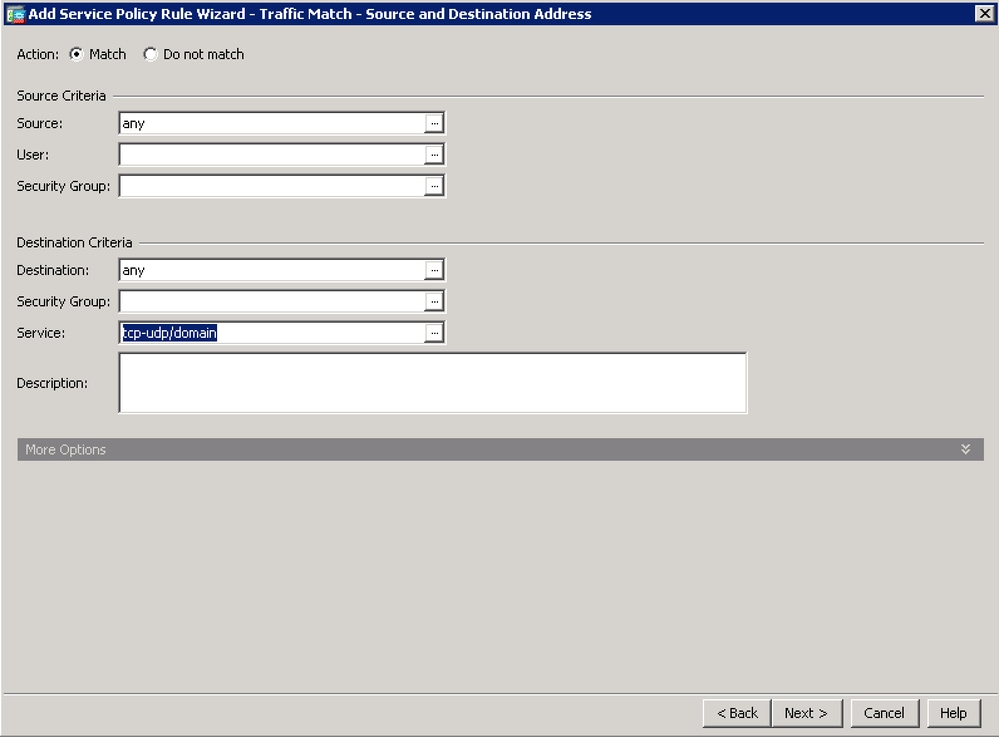
- Leave the 'DNS' option checked and click on Finish.
- Click on Apply at the bottom of the window.
Further Information
If you would prefer to disable DNScrypt rather than configuring ASA exemptions, please contact Umbrella support.

















 Feedback
Feedback