Configure IKEv1 IPsec Site-to-Site Tunnels with the ASDM or CLI on the ASAv
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document describes how to configure an IKEv1 IPsec site-to-site tunnel between two Cisco Secure Firewall Virtual (ASAv) running v9.18.3.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- The end-to-end IP connectivity must be established
- These protocols must be allowed:
- User Datagram Protocol (UDP) 500 and 4500 for the IPsec control plane
- Encapsulating Security Payload (ESP) IP Protocol 50 for the IPsec data plane
Components Used
The information in this document is based on these software and hardware version:
- Cisco Secure Firewall ASA Virtual that runs the software version 9.18.3
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
This section describes how to configure the site-to-site VPN tunnel via the Adaptive Security Device Manager (ASDM) VPN wizard or via the CLI.
Network Diagram
This topology is used for the examples throughout this document:
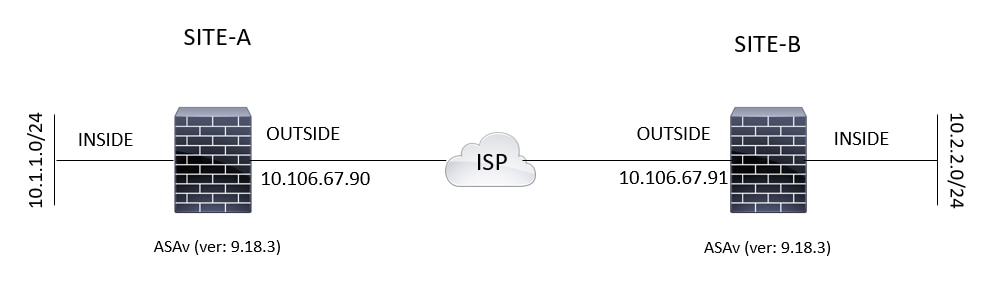 Topology Diagram
Topology Diagram
Configure Via the ASDM VPN Wizard
Complete these steps in order to set up the site-to-site VPN tunnel via the ASDM wizard:
- Open the ASDM and navigate to
Wizards > VPN Wizards > Site-to-site VPN Wizard.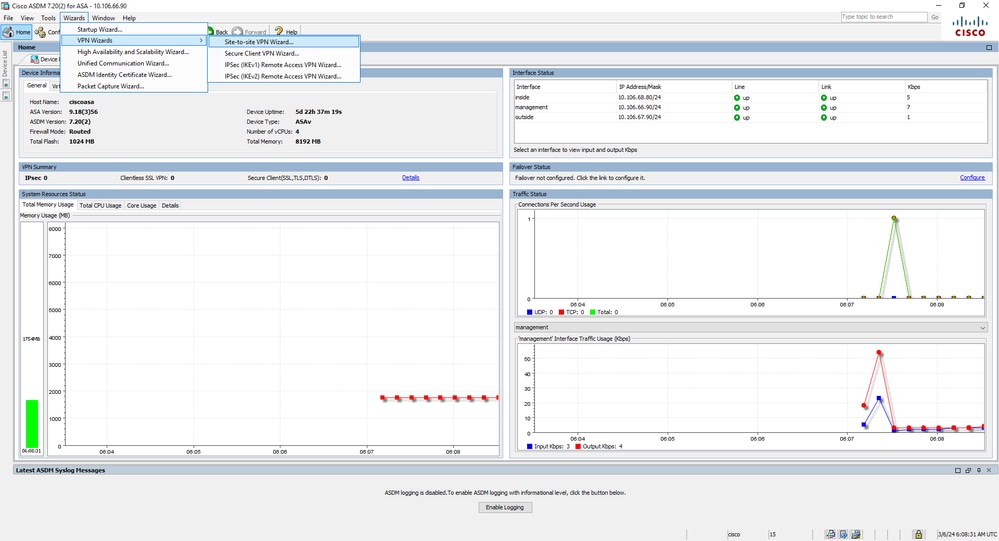 VPN Wizard Navigation
VPN Wizard Navigation
- Click
Nextonce you reach the wizard home page.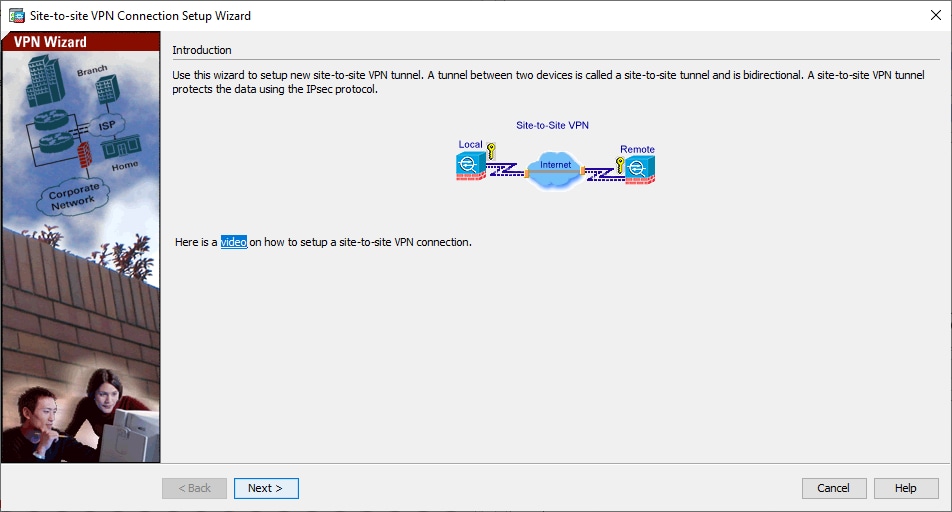 VPN Wizard Window 1
VPN Wizard Window 1
Note: The most recent ASDM versions provide a link to a video that explains this configuration.
- Configure the peer IP address. In this example, the peer IP address is set to 10.106.67.91 on Site B. If you configure the peer IP address on Site A, it must be changed to 10.106.67.90. The interface through which the remote end can be reached is also specified. Click
Nextonce complete.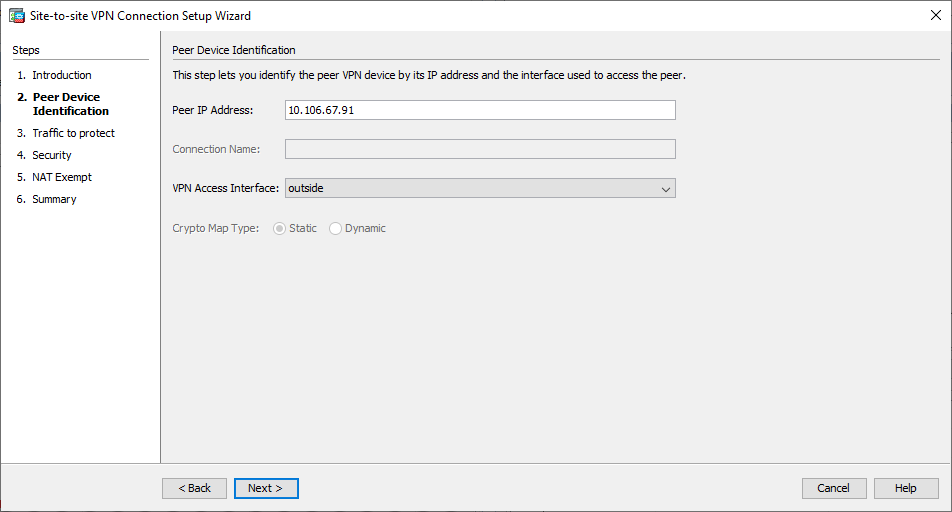 VPN Wizard Window 2
VPN Wizard Window 2
- Configure the local and remote networks (traffic source and destination). This image shows the configuration for Site B (the reverse applies to Site A).
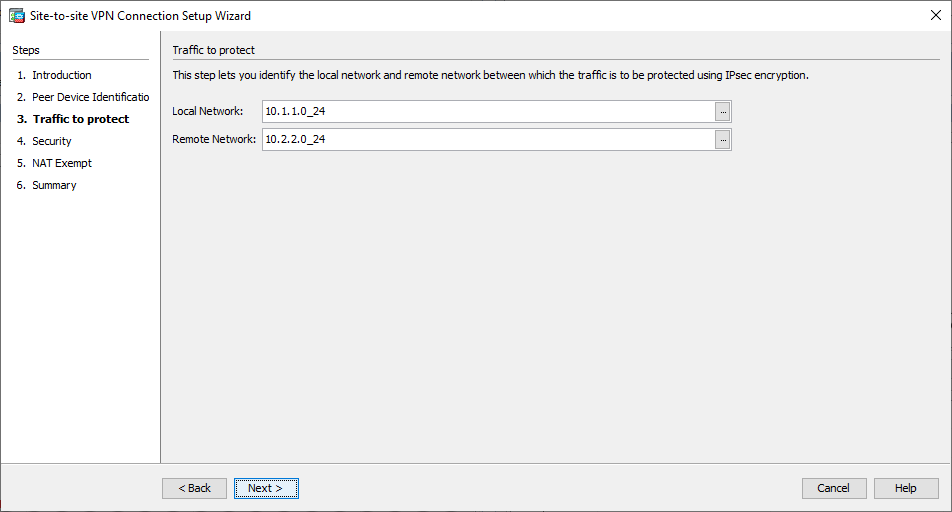 VPN Wizard Window 3
VPN Wizard Window 3
- On the Security page, configure the pre-shared key (it must match on both ends). Click
Nextonce complete.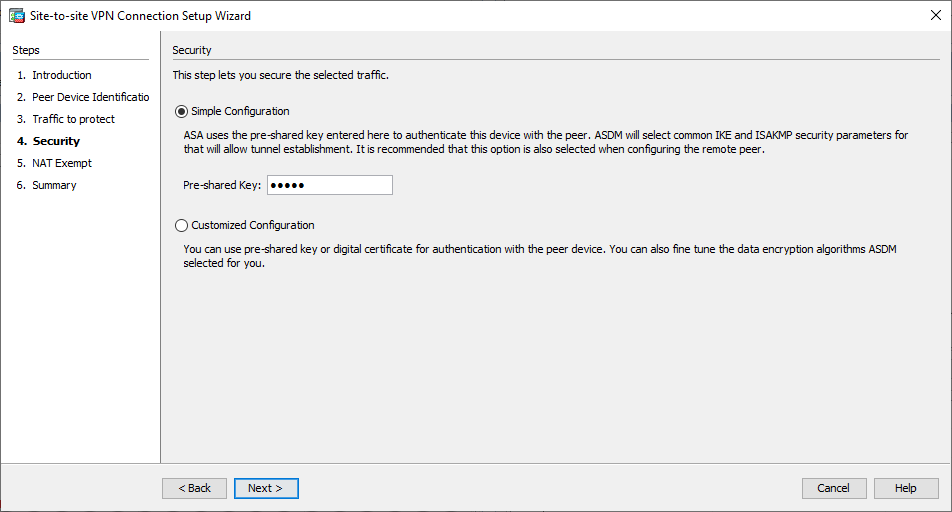 VPN Wizard Window 4
VPN Wizard Window 4
- Configure the source interface for the traffic on the ASA. The ASDM automatically creates the Network Address Translation (NAT) rule based on the ASA version and pushes it with the rest of the configuration in the final step.
Note: For the example that is used in this document, 'inside' is the source of the traffic.
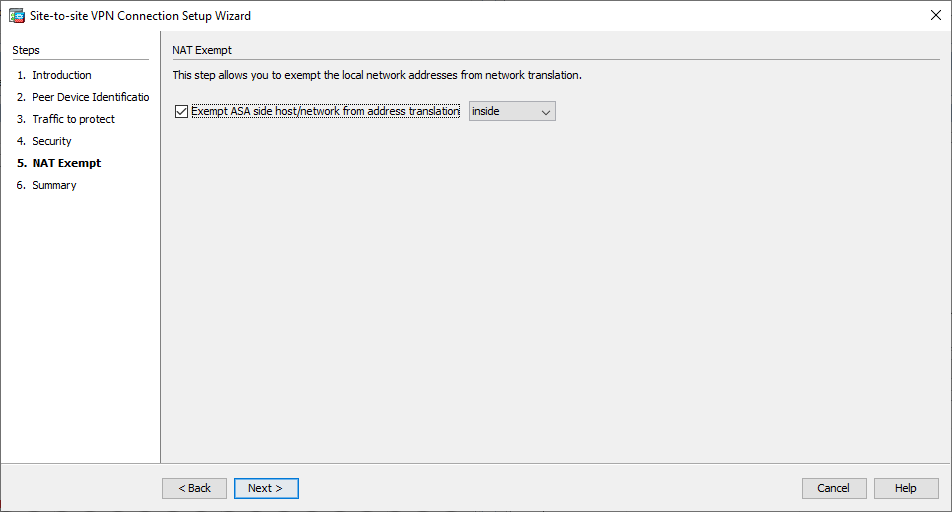 VPN Wizard Window 5
VPN Wizard Window 5
- The wizard now provides a summary of the configuration that is pushed to the ASA. Review and verify the configuration settings, and then click
Finish.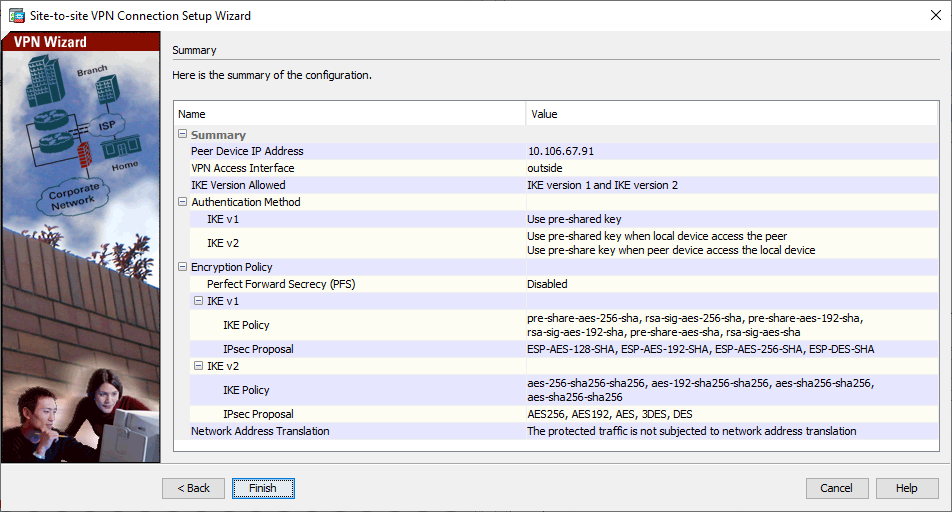 VPN Wizard Window 6
VPN Wizard Window 6
Configure Via the CLI
This section describes how to configure the IKEv1 IPsec site-to-site tunnel via the CLI.
Configure Site B
Tip: For an IKEv2 configuration example with the ASA, take a look at the Site-to-Site IKEv2 Tunnel between ASA and Router Configuration Examples Cisco document.
Phase 1 (IKEv1)
Complete these steps for the Phase 1 configuration:
- Enter this command into the CLI in order to enable IKEv1 on the outside interface:
crypto ikev1 enable outside
- Create an IKEv1 policy that defines the algorithms/methods to be used for hashing, authentication, Diffie-Hellman group, lifetime, and encryption:
crypto ikev1 policy 1
! The 1 in the above command refers to the Policy suite priority (1 highest, 65535 lowest)
authentication pre-share
encryption aes-256
hash sha
group 14
lifetime 86400 - Create a tunnel group under the IPsec attributes and configure the peer IP address and the tunnel pre-shared key:
tunnel-group 10.106.67.90 type ipsec-l2l
tunnel-group 10.106.67.90 ipsec-attributes
ikev1 pre-shared-key cisco
! Note the IKEv1 keyword at the beginning of the pre-shared-key command.
Phase 2 (IPsec)
Complete these steps for the Phase 2 configuration:
- Create an access list that defines the traffic to be encrypted and tunneled. In this example, the traffic of interest is the traffic from the tunnel that is sourced from the 10.2.2.0 subnet to 10.1.1.0. It can contain multiple entries if there are multiple subnets involved between the sites.
object network 10.2.2.0_24
subnet 10.2.2.0 255.255.255.0
object network 10.1.1.0_24
subnet 10.1.1.0 255.255.255.0
access-list 100 extended permit ip object 10.2.2.0_24 object 10.1.1.0_24 - Configure the Transform Set (TS), which must involve the keyword
IKEv1. An identical TS must be created on the remote end as well.
crypto ipsec ikev1 transform-set myset esp-aes-256 esp-sha-hmac
- Configure the crypto map, which contains these components:
- The peer IP address
- The defined access list that contains the traffic of interest
- The TS
- An optional Perfect Forward Secrecy (PFS) setting, which creates a new pair of Diffie-Hellman keys that are used in order to protect the data (both sides must be PFS-enabled before Phase 2 comes up)
- Apply the crypto map on the outside interface:
crypto map outside_map 20 match address 100
crypto map outside_map 20 set peer 10.106.67.90
crypto map outside_map 20 set ikev1 transform-set myset
crypto map outside_map 20 set pfs
crypto map outside_map interface outside
NAT Exemption
Ensure that the VPN traffic is not subjected to any other NAT rule. This is the NAT rule that is used:
nat (inside,outside) 1 source static 10.2.2.0_24 10.2.2.0_24 destination static 10.1.1.0_24 10.1.1.0_24 no-proxy-arp route-lookup
Note: When multiple subnets are used, you must create object groups with all of the source and destination subnets and use them in the NAT rule.
object-group network 10.x.x.x_SOURCE
network-object 10.4.4.0 255.255.255.0
network-object 10.2.2.0 255.255.255.0
object network 10.x.x.x_DESTINATION
network-object 10.3.3.0 255.255.255.0
network-object 10.1.1.0 255.255.255.0
nat (inside,outside) 1 source static 10.x.x.x_SOURCE 10.x.x.x_SOURCE destination static 10.x.x.x_DESTINATION 10.x.x.x_DESTINATION no-proxy-arp route-lookup
Complete Sample Configuration
Here is the complete configuration for Site B:
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 14
lifetime 86400
tunnel-group 10.106.67.90 type ipsec-l2l
tunnel-group 10.106.67.90 ipsec-attributes
ikev1 pre-shared-key cisco
!Note the IKEv1 keyword at the beginning of the pre-shared-key command.
object network 10.2.2.0_24
subnet 10.2.2.0 255.255.255.0
object network 10.1.1.0_24
subnet 10.1.1.0 255.255.255.0
access-list 100 extended permit ip object 10.2.2.0_24 object 10.1.1.0_24
crypto ipsec ikev1 transform-set myset esp-aes esp-sha-hmac
crypto map outside_map 20 match address 100
crypto map outside_map 20 set peer 10.106.67.90
crypto map outside_map 20 set ikev1 transform-set myset
crypto map outside_map 20 set pfs
crypto map outside_map interface outside
nat (inside,outside) 1 source static 10.2.2.0_24 10.2.2.0_24 destination static 10.1.1.0_24 10.1.1.0_24 no-proxy-arp route-lookup
Group Policy
Group policies are used in order to define specific settings that apply to the tunnel. These policies are used in conjunction with the tunnel group.
The group policy can be defined as either internal, which means that the attributes are pulled from that which is defined on the ASA, or it can be defined as external, where the attributes are queried from an external server. This is the command that is used in order to define the group policy:
group-policy SITE_A internal
Note: You can define multiple attributes in the group policy. For a list of all possible attributes, refer to the Configuring Group Policies section.
Group Policy Optional Attributes
The vpn-tunnel-protocol attribute determines the tunnel type to which these settings must be applied. In this example, IPsec is used:
vpn-tunnel-protocol ?
group-policy mode commands/options:
IPSec IP Security Protocol l2tp-ipsec L2TP using IPSec for security
svc SSL VPN Client
webvpn WebVPN
vpn-tunnel-protocol ikev1 - Version 8.4 and later
You have the option to configure the tunnel so that it stays idle (no traffic) and does not go down. In order to configure this option, the vpn-idle-timeout attribute value must use minutes, or you can set the value to none, which means that the tunnel never goes down.
Here is an example:
group-policy SITE_A attributes
vpn-idle-timeout ?
group-policy mode commands/options:
<1-35791394> Number of minutes
alert-interval Specify timeout alert interval in minutes
none Site-to-Site (IKEv1, IKEv2) and IKEv1 remote-access: Disable
timeout and allow an unlimited idle period; AnyConnect (SSL,
IPSec/IKEv2): Use value of default-idle-timeout
The default-group-policy command under the general attributes of the tunnel group defines the group policy that is used in order to push certain policy settings for the tunnel that is established. The default settings for the options that you did not define in the group policy are taken from a global default group policy:
tunnel-group 10.106.67.91 general-attributes
default-group-policy SITE_A
Verify
Use the information that is provided in this section in order to verify that your configuration works properly.
ASDM
In order to view the tunnel status from the ASDM, navigate to Monitoring > VPN. This information is provided:
- The peer IP address
- The protocol that is used in order to build the tunnel
- The encryption algorithm that is used
- The time at which the tunnel came up and the up-time
- The number of packets that are received and transferred
Tip: Click Refresh in order to view the latest values, as the data does not update in real time.
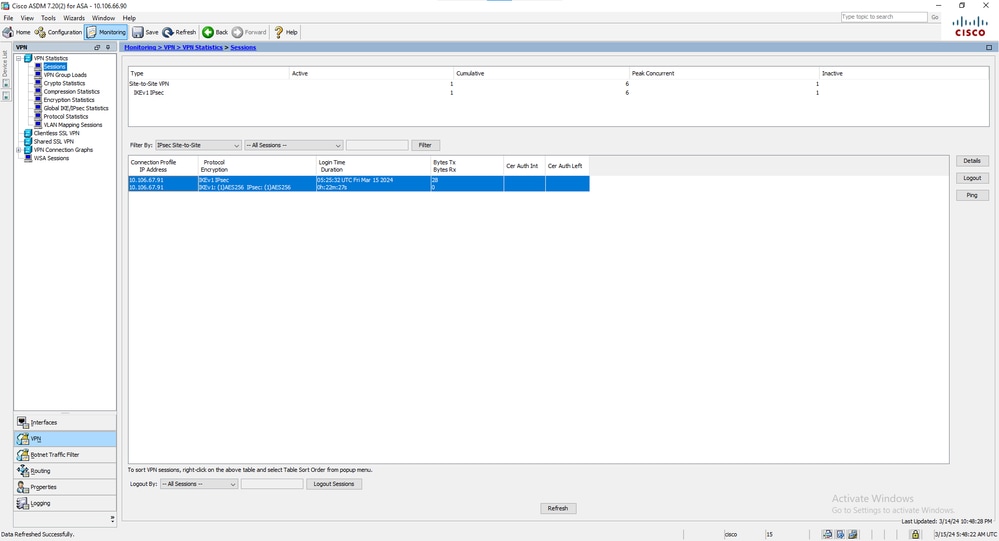 VPN Monitoring Window
VPN Monitoring Window
CLI
This section describes how to verify your configuration via the CLI.
Phase 1
Enter this command into the CLI in order to verify the Phase 1 configuration on the Site B side:
show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 10.106.67.91
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Phase 2
The show crypto ipsec sa command shows the IPsec SAs that are built between the peers. The encrypted tunnel is built between IP addresses 10.106.67.90 and 10.106.67.91 for the traffic that flows between the networks 10.1.1.0 and 10.2.2.0. You can see the two ESP SAs built for the inbound and outbound traffic. The Authentication Header (AH) is not used because there are no AH SAs.
Enter this command into the CLI in order to verify the Phase 2 configuration on the Site A side:
interface: outside
Crypto map tag: outside_map, seq num: 20, local addr: 10.106.67.90
access-list 100 extended permit ip 10.1.1.0 255.255.255.0 10.2.2.0 255.255.255.0
local ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.2.2.0/255.255.255.0/0/0)
current_peer: 10.106.67.91
#pkts encaps: 20, #pkts encrypt: 20, #pkts digest: 20
#pkts decaps: 20, #pkts decrypt: 20, #pkts verify: 20
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 20, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.106.67.90/0, remote crypto endpt.: 10.106.67.91/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: F8951DA2
current inbound spi : 662C7ABE
inbound esp sas:
spi: 0x662C7ABE (1714191038)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (3914998/28074)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x001FFFFF
outbound esp sas:
spi: 0xF8951DA2 (4170522018)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (3914998/28073)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Enter this command into the CLI in order to verify the Phase 2 configuration on the Site B side:
interface: outside
Crypto map tag: outside_map, seq num: 20, local addr: 10.106.67.91
access-list 100 extended permit ip 10.2.2.0 255.255.255.0 10.1.1.0 255.255.255.0
local ident (addr/mask/prot/port): (10.2.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.1.1.0/255.255.255.0/0/0)
current_peer: 10.106.67.90
#pkts encaps: 20, #pkts encrypt: 20, #pkts digest: 20
#pkts decaps: 20, #pkts decrypt: 20, #pkts verify: 20
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 20, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.106.67.91/0, remote crypto endpt.: 10.106.67.90/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 662C7ABE
current inbound spi : F8951DA2
inbound esp sas:
spi: 0xF8951DA2 (4170522018)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (4373998/27737)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x001FFFFF
outbound esp sas:
spi: 0x662C7ABE (1714191038)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv1, }
slot: 0, conn_id: 1, crypto-map: outside_map
sa timing: remaining key lifetime (kB/sec): (4373998/27737)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Troubleshoot
Use the information that is provided in this section in order to troubleshoot configuration issues.
Enter these debug commands in order to determine the location of the tunnel failure:
debug crypto ikev1 127(Phase 1)debug crypto ipsec 127(Phase 2)
Here is a complete example of debug output:
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=10.1.1.10, sport=23043, daddr=10.2.2.10, dport=23043
IPSEC(crypto_map_check)-3: Checking crypto map outside_map 20: matched.
Mar 15 05:41:39 [IKEv1 DEBUG]Pitcher: received a key acquire message, spi 0x0
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=10.1.1.10, sport=23043, daddr=10.2.2.10, dport=23043
IPSEC(crypto_map_check)-3: Checking crypto map outside_map 20: matched.
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE Initiator: New Phase 1, Intf inside, IKE Peer 10.106.67.91 local Proxy Address 10.1.1.0, remote Proxy Address 10.2.2.0, Crypto map (outside_map)
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing ISAKMP SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Traversal VID ver 02 payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Traversal VID ver 03 payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Traversal VID ver RFC payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing Fragmentation VID + extended capabilities payload
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 172
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + SA (1) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 132
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Oakley proposal is acceptable
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received NAT-Traversal RFC VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received Fragmentation VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, IKE Peer included IKE fragmentation capability flags: Main Mode: True Aggressive Mode: True
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing Cisco Unity VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing xauth V6 VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Send IOS VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Constructing ASA spoofing IOS Vendor ID payload (version: 1.0.0, capabilities: 20000001)
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Send Altiga/Cisco VPN3000/Cisco ASA GW VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, constructing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NAT-D (20) + NAT-D (20) + NONE (0) total length : 432
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + KE (4) + NONCE (10) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NAT-D (20) + NAT-D (20) + NONE (0) total length : 432
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing ISA_KE payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received Cisco Unity client VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received xauth V6 VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Processing VPN3000/ASA spoofing IOS Vendor ID payload (version: 1.0.0, capabilities: 20000001)
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Received Altiga/Cisco VPN3000/Cisco ASA GW VID
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, processing NAT-Discovery payload
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, computing NAT Discovery hash
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, Connection landed on tunnel_group 10.106.67.91
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Generating keys for Initiator...
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing ID payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Computing hash for ISAKMP
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Constructing IOS keep alive payload: proposal=32767/32767 sec.
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing dpd vid payload
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Automatic NAT Detection Status: Remote end is NOT behind a NAT device This end is NOT behind a NAT device
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + ID (5) + HASH (8) + IOS KEEPALIVE (128) + VENDOR (13) + NONE (0) total length : 96
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ID payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, ID_IPV4_ADDR ID received 10.106.67.91
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Computing hash for ISAKMP
Mar 15 05:41:39 [IKEv1 DEBUG]IP = 10.106.67.91, Processing IOS keep alive payload: proposal=32767/32767 sec.
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing VID payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Received DPD VID
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, Connection landed on tunnel_group 10.106.67.91
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Oakley begin quick mode
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator starting QM: msg id = ad712fa9
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, PHASE 1 COMPLETED
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, Keep-alive type for this connection: DPD
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Starting P1 rekey timer: 73440 seconds.
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Add to IKEv1 Tunnel Table succeeded for SA with logical ID 8192
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Add to IKEv1 MIB Table succeeded for SA with logical ID 8192
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0001B739
IPSEC: New embryonic SA created @ 0x00007f05294f4620,
SCB : 0x294CFE60,
Direction : inbound
SPI : 0x50EF49AD
Session ID : 0x00002000
VPIF num : 0x00000002
Tunnel type : l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0001B739
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, IKE got SPI from key engine: SPI = 0x50ef49ad
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, oakley constructing quick mode
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing blank hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing IPSec SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing IPSec nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing pfs ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing proxy ID
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Transmitting Proxy Id:
Local subnet: 10.1.1.0 mask 255.255.255.0 Protocol 0 Port 0
Remote subnet: 10.2.2.0 Mask 255.255.255.0 Protocol 0 Port 0
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator sending Initial Contact
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, constructing qm hash payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator sending 1st QM pkt: msg id = ad712fa9
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=ad712fa9) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + KE (4) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 464
Mar 15 05:41:39 [IKEv1]IKE Receiver: Packet received on 10.106.67.90:500 from 10.106.67.91:500
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE RECEIVED Message (msgid=ad712fa9) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + KE (4) + ID (5) + ID (5) + NONE (0) total length : 436
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing hash payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing SA payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing nonce payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ke payload
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ISA_KE for PFS in phase 2
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ID payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, ID_IPV4_ADDR_SUBNET ID received--10.1.1.0--255.255.255.0
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, processing ID payload
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, ID_IPV4_ADDR_SUBNET ID received--10.2.2.0--255.255.255.0
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, loading all IPSEC SAs
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Generating Quick Mode Key!
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Generating Quick Mode Key!
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, Security negotiation complete for LAN-to-LAN Group (10.106.67.91) Initiator, Inbound SPI = 0x50ef49ad, Outbound SPI = 0xea689811
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, oakley constructing final quick mode
Mar 15 05:41:39 [IKEv1 DECODE]Group = 10.106.67.91, IP = 10.106.67.91, IKE Initiator sending 3rd QM pkt: msg id = ad712fa9
Mar 15 05:41:39 [IKEv1]IP = 10.106.67.91, IKE_DECODE SENDING Message (msgid=ad712fa9) with payloads : HDR + HASH (8) + NONE (0) total length : 76
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x00024311
IPSEC: New embryonic SA created @ 0x00007f05294fd920,
SCB : 0x294CCDB0,
Direction : outbound
SPI : 0xEA689811
Session ID : 0x00002000
VPIF num : 0x00000002
Tunnel type : l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x00024311
Rule Lookup for local 10.1.1.0 to remote 10.2.2.0
Peer matched map outside_map sequence 20
PROXY MATCH on crypto map outside_map seq 20
IPSEC DEBUG: Using NP outbound permit rule for SPI 0xEA689811
IPSEC: Completed host OBSA update, SPI 0xEA689811
IPSEC: Creating outbound VPN context, SPI 0xEA689811
Flags : 0x00000005
SA : 0x00007f05294fd920
SPI : 0xEA689811
MTU : 1500 bytes
VCID : 0x00000000
Peer : 0x00000000
SCB : 0x02CEE703
Channel: 0x00007f0533c4f700
IPSEC: Completed outbound VPN context, SPI 0xEA689811
VPN handle: 0x000000000000763c
IPSEC: New outbound encrypt rule, SPI 0xEA689811
Src addr: 10.1.1.0
Src mask: 255.255.255.0
Dst addr: 10.2.2.0
Dst mask: 255.255.255.0
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 0
Use protocol: false
SPI: 0x00000000
Use SPI: false
IPSEC: Completed outbound encrypt rule, SPI 0xEA689811
Rule ID: 0x00007f05294f8a60
IPSEC: New outbound permit rule, SPI 0xEA689811
Src addr: 10.106.67.90
Src mask: 255.255.255.255
Dst addr: 10.106.67.91
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0xEA689811
Use SPI: true
IPSEC: Completed outbound permit rule, SPI 0xEA689811
Rule ID: 0x00007f05294f9110
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, IKE got a KEY_ADD msg for SA: SPI = 0xea689811
IPSEC: New embryonic SA created @ 0x00007f05294f4620,
SCB : 0x294CFE60,
Direction : inbound
SPI : 0x50EF49AD
Session ID : 0x00002000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0001B739
Rule Lookup for local 10.1.1.0 to remote 10.2.2.0
Peer matched map outside_map sequence 20
PROXY MATCH on crypto map outside_map seq 20
IPSEC DEBUG: Using NP inbound permit rule for SPI 0x50EF49AD
IPSEC: Completed host IBSA update, SPI 0x50EF49AD
IPSEC: Creating inbound VPN context, SPI 0x50EF49AD
Flags: 0x00000006
SA : 0x00007f05294f4620
SPI : 0x50EF49AD
MTU : 0 bytes
VCID : 0x00000000
Peer : 0x0000763C
SCB : 0x02CE8BB3
Channel: 0x00007f0533c4f700
IPSEC: Completed inbound VPN context, SPI 0x50EF49AD
VPN handle: 0x00000000000086bc
IPSEC: Updating outbound VPN context 0x0000763C, SPI 0xEA689811
Flags: 0x00000005
SA : 0x00007f05294fd920
SPI : 0xEA689811
MTU : 1500 bytes
VCID : 0x00000000
Peer : 0x000086BC
SCB : 0x02CEE703
Channel: 0x00007f0533c4f700
IPSEC: Completed outbound VPN context, SPI 0xEA689811
VPN handle: 0x000000000000763c
IPSEC: Completed outbound inner rule, SPI 0xEA689811
Rule ID: 0x00007f05294f8a60
IPSEC: Completed outbound outer SPD rule, SPI 0xEA689811
Rule ID: 0x00007f05294f9110
IPSEC: New inbound tunnel flow rule, SPI 0x50EF49AD
Src addr: 10.2.2.0
Src mask: 255.255.255.0
Dst addr: 10.1.1.0
Dst mask: 255.255.255.0
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 0
Use protocol: false
SPI: 0x00000000
Use SPI: false
IPSEC: Completed inbound tunnel flow rule, SPI 0x50EF49AD
Rule ID: 0x00007f05294f8180
IPSEC: New inbound decrypt rule, SPI 0x50EF49AD
Src addr: 10.106.67.91
Src mask: 255.255.255.255
Dst addr: 10.106.67.90
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0x50EF49AD
Use SPI: true
IPSEC: Completed inbound decrypt rule, SPI 0x50EF49AD
Rule ID: 0x00007f05294f7ad0
IPSEC: New inbound permit rule, SPI 0x50EF49AD
Src addr: 10.106.67.91
Src mask: 255.255.255.255
Dst addr: 10.106.67.90
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0x50EF49AD
Use SPI: true
IPSEC: Completed inbound permit rule, SPI 0x50EF49AD
Rule ID: 0x00007f05294f4510
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Pitcher: received KEY_UPDATE, spi 0x50ef49ad
Mar 15 05:41:39 [IKEv1 DEBUG]Group = 10.106.67.91, IP = 10.106.67.91, Starting P2 rekey timer: 24480 seconds.
Mar 15 05:41:39 [IKEv1]Group = 10.106.67.91, IP = 10.106.67.91, PHASE 2 COMPLETED (msgid=ad712fa9)
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
10-Jul-2015
|
Initial Release |
Contributed by Cisco Engineers
- Venkata Aditya BCisco TAC Engineer
- Rahul GovindanCisco TAC Engineer
- Pavan GunduTechnical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback