Introduction
This document describes how to troubleshoot hardware provider connections issues from Nutanix Foundation Central to Cisco Intersight.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics.
- Basic understanding of network connectivity.
- Basic understanding of Intersight API Keys.
- Intersight Account with at least Server Administrator privileges.

Note: Intersight provides Role-Based Access Control (RBAC) to authorize or restrict system access to a user, based on user roles and privileges. A user role in Intersight represents a collection of the privileges a user has to perform a set of operations and provides granular access to resources. Intersight provides role-based access to individual users or a set of users under Groups.
Components Used
The information in this document is based on these software and hardware versions:
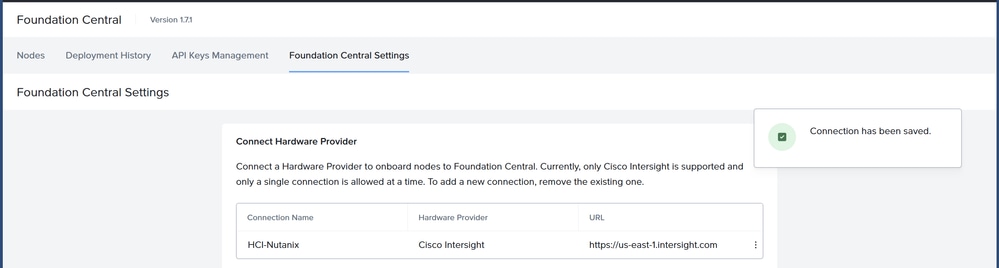
- Foundation Central 1.7.1 or higher.
- Intersight SAAS, CVA and PVA.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
It is required to connect Foundation Central to Cisco Intersight as the hardware provider to deploy the Cisco HCI with Nutanix solution in Intersight Standalone Mode ISM or Intersight Managed Mode IMM.
Intersight Standalone mode: The nodes are connected to a pair of Top-of-Rack (ToR) switches and servers are centrally managed using Cisco Intersight®. While a minimum of three nodes are required to deploy a standard Nutanix cluster, we also offer an option to deploy a single node cluster and a two-node cluster for Edge and branch locations and situations that already have a high-performance network fabric installed.
Intersight Managed mode: Intersight Managed Mode unifies the capabilities of the UCS Systems and the cloud-based flexibility of Intersight, thus unifying the management experience for the standalone and Fabric Interconnect attached systems. Intersight Management Model standardizes policy and operation management for UCS-FI-6454, UCS-FI-64108, UCS-FI-6536, UCSX-S9108-100G Fabric Interconnects and Cisco UCS C-Series (M5, M6, M7, M8), and Cisco UCS X-Series (M6, M7, M8) servers.
Troubleshoot
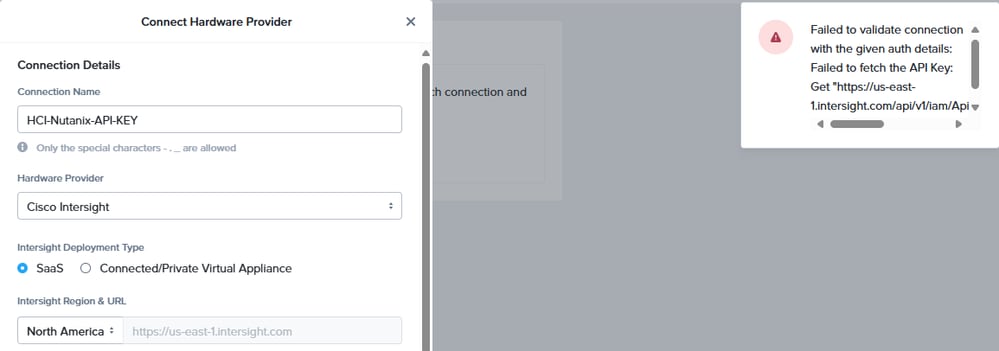
Context Deadline Exceeded
"Failed to validate connection with the given auth details: Failed to fetch the API Key: context deadline exceeded."
Ensure that you have proper connectivity from Prism Central and Foundation central to the next URLS through the ports 443 TCP/UDP and 80 TCP.
|
Region
|
URL
|
URLs required by Device Connectors
|
|
North America
|
intersight.com
us-east-1.intersight.com
Ips:
52.223.48.112
99.83.178.202
|
svc.intersight.com
svc.us-east-1.intersight.com
svc-static1.intersight.com
ucs-starship.com*
ucs-connect.com*
|
|
EMEA
|
Intersight.com
eu-central-1.intersight.com
Ips:
52.223.57.109
99.83.140.236
|
svc.eu-central-1.intersight.com
svc-static1.eu-central-1.intersight.com
|

Note: Cisco Intersight supports two regions: the existing North America region (us-east-1) and the Europe, Middle East and Africa (EMEA) region (eu-central–1).
To validate the previous information, please SSH into your Prism Central or Foundation Central VM and perform a curl command to the mentioned URLS and ports.
curl -v -k https://svc.intersight.com
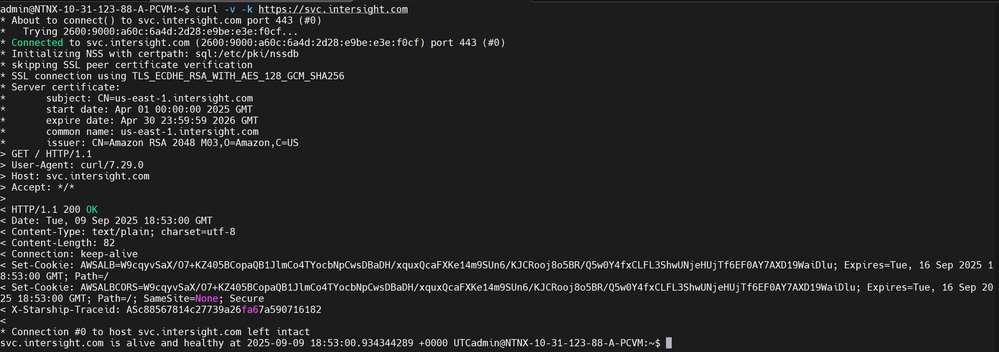 Successful curl connectivity test.
Successful curl connectivity test.
If the curl command fails, please check with your firewall team that the URLS and ports are allowed into the firewall or access list.
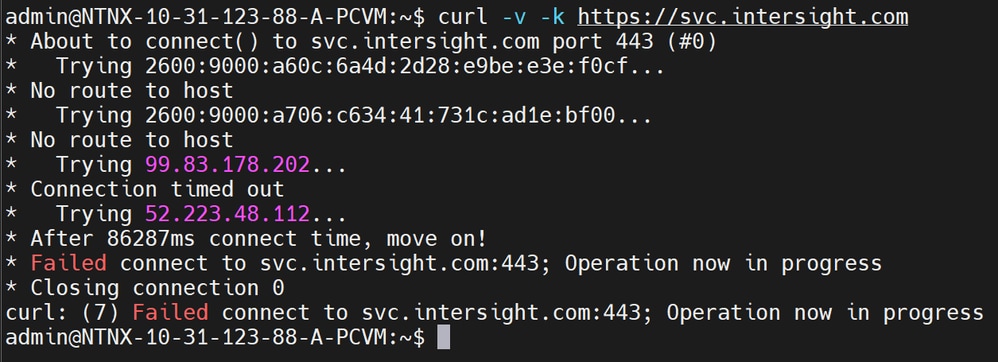 Failed curl connectivity test.
Failed curl connectivity test.
DNS Proper Name Resolution
Some firewall or access list requires adding the resolving IP from the mentioned URLS, Both of these URLs resolve to these IPv4 and IPv6 addresses:
- 52.223.48.112
- 99.83.178.202
- 2600:9000:a60c:6a4d:2d28:e9be:e3e:f0cf
- 2600:9000:a706:c634:41:731c:ad1e:bf00
This can be validated by using nslookup commad.
nslookup svc.intersight.com
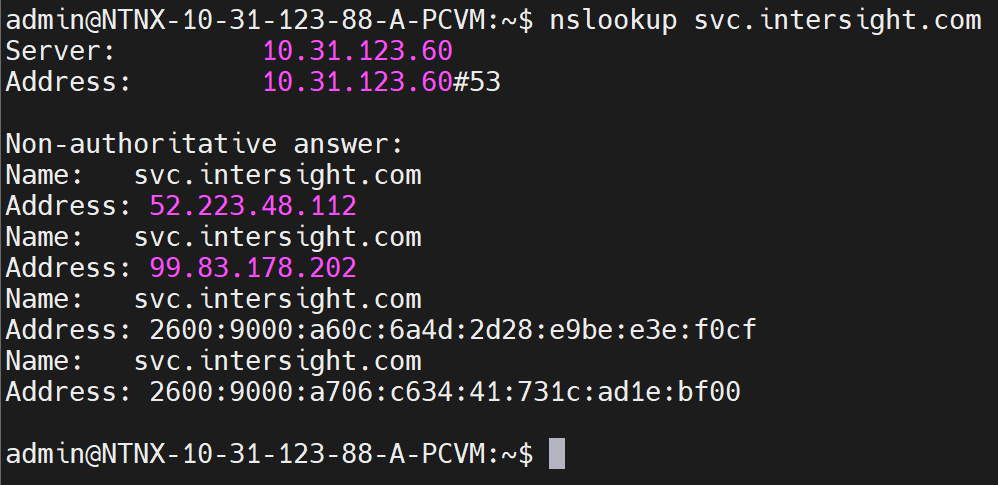 nslookup command
nslookup command
Prism Central VM Can´t Connect To Intersight CVA / PVA
When there is a direct connection from Prism Central to Intersight CVA / PVA make sure to allow connection on Port 443.
If PC VM has a proxy configured to connect to the internet for tasks like software downloads or LCM, you need to whitelist the Intersight CVA / PVA FQDN and IP adress at Prism Central Proxy settings.

Note: A whitelist entry is a single host identified by IP address or a network identified by the network address and subnet mask. Adding a whitelist entry means “ignore proxy settings for this address or network”.
To correct this in Prism Central navigate to: Settings > Network > HTTP Proxy > Click on pencil icon to edit >Whitelist.
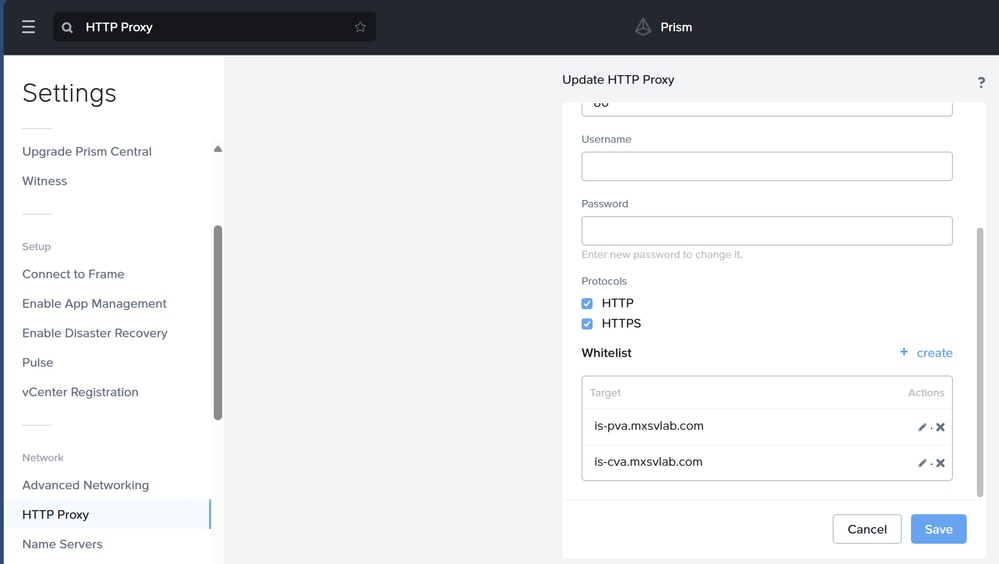 HTTP Proxy
HTTP Proxy
You can confirm if these steps were successful by testing the connectivity to Intersight CVA / PVA with a curl command.
curl -v -k https://is-pva.mxsvlab.com
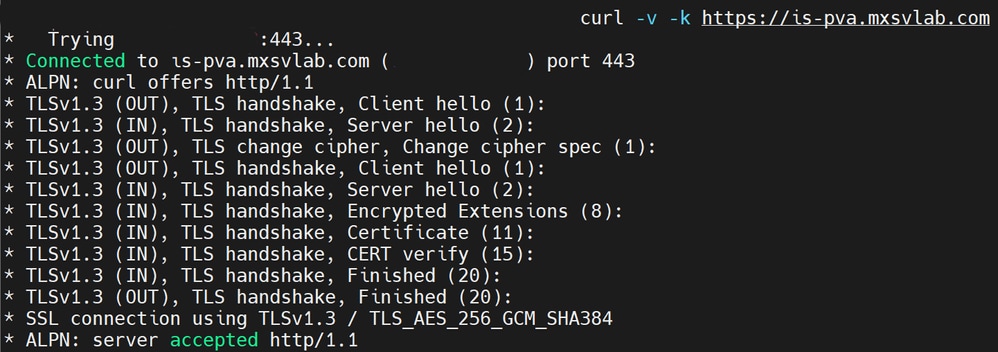 Curl test
Curl test
Network Commands To Test Connectivity
|
Command
|
Description
|
|
curl -v -k https://<Intersight URL>
curl -v -k https://svc.intersight.com
|
Test connectivity towards a Intersight required URL
|
|
curl -v -k --proxy <proxy address>:<port> <Intersight URL>
curl -v -k --proxy http://proxy.esl.cisco.com:8080 https://svc.intersight.com
|
Test connectivity when proxy is required
|
|
curl -4|6 -v -k https://<Intersight URL>
curl -4 -v -k https://svc.intersight.com
|
Specify connectivity test to IPV4 or IPV6 addressing
|
|
tracepath <Intersight IP>
tracepath 99.83.178.202
|
Traces packets towards a destination host
|
|
nslookup <URL>
nslookup svc.Intersight.com
|
Determines IP address associated with specific address
|
Auth Details Provided Are Invalid
"Failed to save hardware manager auth data: Auth details provided are invalid. Please provide valid API Key and secret."
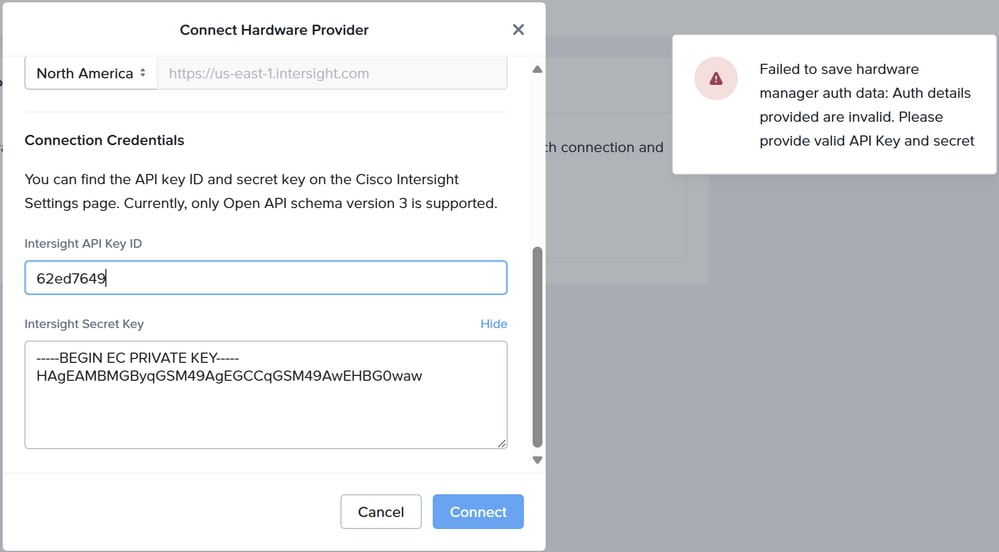
You need to confirm that there are no typographical errors or missing characters while typing or pasting the Intersight Secret Key otherwise it fails to establish the connection to the hardware provider.
Unable To Fetch The EULA List
"Failed to validate connection with the given auth details: Unable to fetch the EULA list. Failed with error: Your token has expired due to inactivity in the last 30 days."
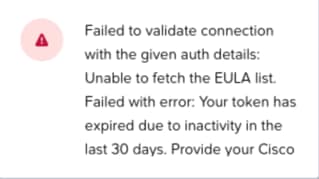
During the Nodes Onboarding phase, you might encounter an error "Failed to connect to INTERSIGHT hardware manager with UUID" or "Your user credentials could have expired.". This appears if there is an Intersight account issue with regards to the EULA.

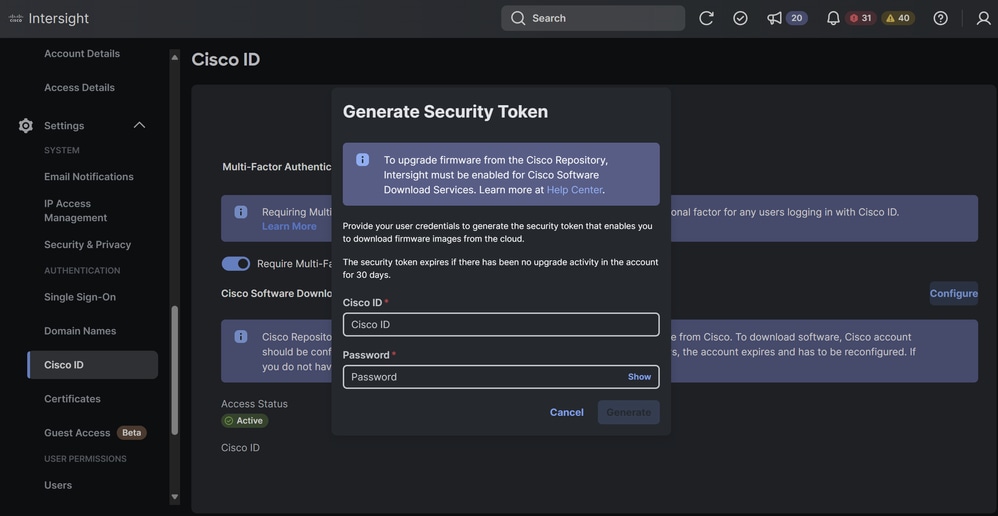
Note: As of today, EULA acceptance is REQUIRED for ISM. This is going to change in the future since we no longer rely on the EULA for firmware downloads.
To correct this in Intersight Navigate to: Settings > Cisco ID > Configure > Enter Cisco ID and Password.
Related Information














 Feedback
Feedback