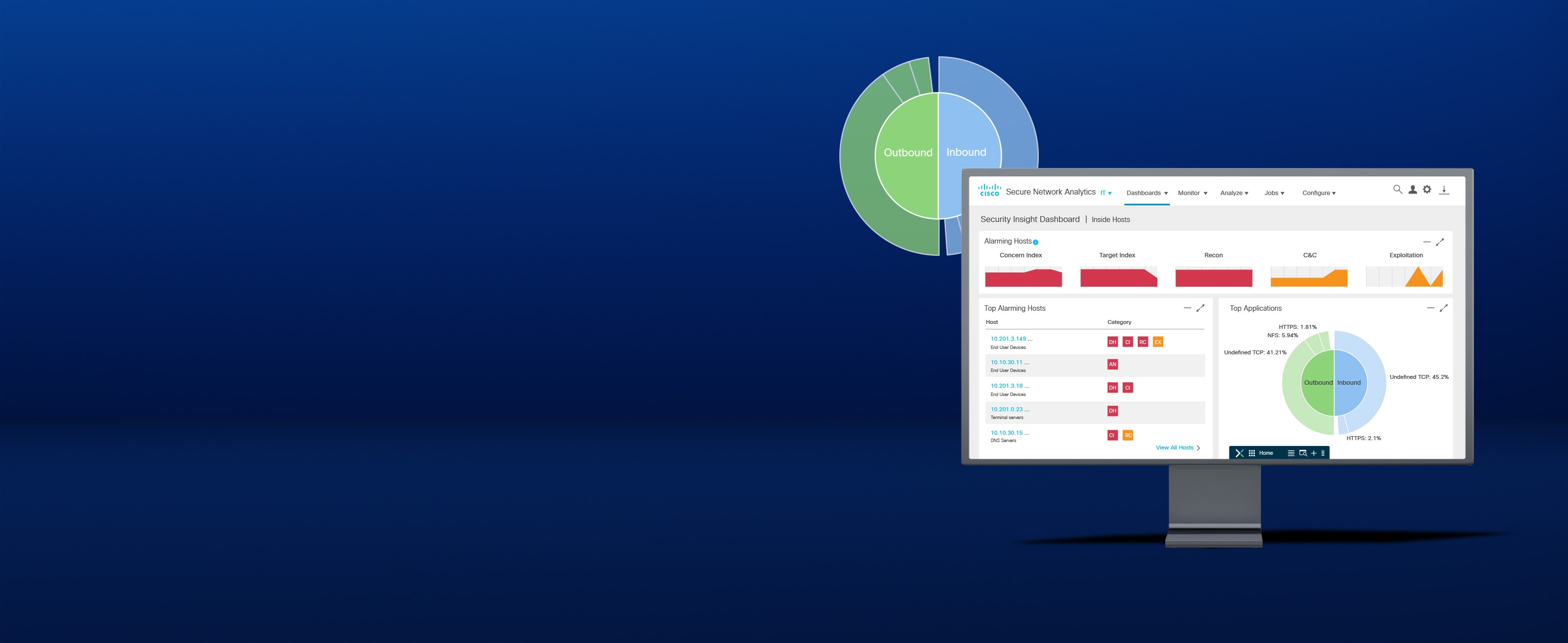
Where mayhem meets its match
Analyze your existing network data to help detect threats that may have found a way to bypass your existing controls, before they can do serious damage.
Forewarned is forearmed
Detect attacks in real time across the dynamic network with high-fidelity alerts enriched with context, including user, device, location, timestamp, and application.
Reduce policy violations
Validate the efficacy of policies, adopt the right ones based on your environment's needs, and streamline policy violation investigations.
Reveal the unknown
Use advanced analytics to quickly detect unknown malware, insider threats like data exfiltration and policy violations, and other sophisticated attacks.
Analyze with ease
Identify and isolate threats in encrypted traffic without compromising privacy and data integrity.
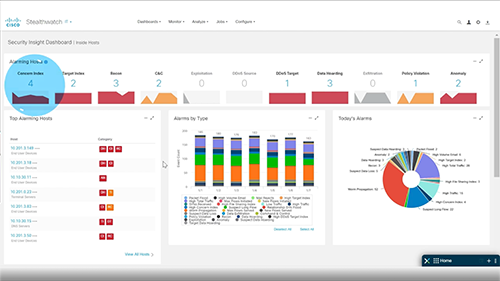
Experience Secure Network Analytics in action
This demo walkthrough provides an overview of what end-to-end detection and response looks like within the latest release of Secure Network Analytics. It also showcases new capabilities such as firewall log ingestion, automated response actions and Secure Network Analytics' integration with Cisco XDR.
Security that's even better than the sum of its parts
Where network nuances are never a problem
Use Secure Network Analytics with Identity Services Engine (ISE) to define smarter segmentation policies, create custom alerts to detect unauthorized access, and ensure compliance.
Advanced network monitoring and threat detection
Cisco Secure Network Analytics + Splunk delivers deep visibility, optimized data management, and advanced threat detection, transforming your network into a sensor for enhanced security.
Security operations simplified
Detect the most sophisticated threats sooner across all vectors and prioritize by impact for faster responses.
Add value to security solutions
Cisco Security Enterprise Agreement
Instant savings
Experience security software buying flexibility with one easy-to-manage agreement.
Services for security
Let the experts secure your business
Get more from your investments and enable constant vigilance to protect your organization.