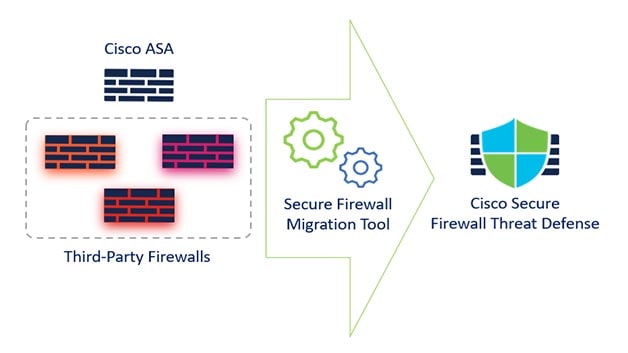
Learn more about your migration use cases
Need more detail to help with your migration? Refer to our in-depth guides.
- Migration of ASA configurations to Firewall Management Center (FMC)
- Migration from ASA with Firepower Services (FPS) to Firewall Threat Defense (FTD)
- Migration from Firewall Device Manager (FDM) to Firewall Management Center (FMC)
- Migration from third-party firewalls: Check Point, Palo Alto Networks, Fortinet