Cisco Secure Cloud Insights Ordering Guide
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
1.1 Purpose, Audience, and Scope
This document describes the pricing and packaging structure and ordering process for Cisco® Secure Cloud Insights.
Audience: This guide is for Cisco sales teams and Cisco specialized channel partners, as well as Cisco customers.
Scope: This ordering guide describes the pricing and ordering for Cisco Secure Cloud Insights.
For more detailed information on Cisco Secure products, go to https://www.cisco.com/c/en/us/products/security/secure-cloud-insights/index.html.
1.2 Ordering and Quoting Tools
Solution expert assists Cisco Systems® field and Cisco [Product/Series] specialized channel partners in designing and quoting solutions using the Cisco Unified Communications bundles or the traditional design model.
Cisco Commerce provides a Deals and Quotes application that enables specialized channel partners to build a system quote with:
● Products, required modules, and software
● Autoderived services based on products and install site location
● Customized leasing options from Cisco Capital®, where available
● Design documentation
For additional information about the Cisco Commerce Experience, go to: https://apps.cisco.com/Commerce/home.
Cisco Commerce includes several helpful tools to estimate, configure, and order solutions, enabling you to configure products and view lead times and prices for each selection. It also allows you to view lead time and price changes under a variety of price lists and service contract terms. You can also track your order.
The following Cisco products and applications are supported in the Cisco Estimates and Configurations Tool:
● Cisco Secure Analytics Subscription (CSA-SUB): The top-level Assemble to Order (ATO)
● Cisco Secure Insights (SCA-INS): The billing Product Identifier (PID)
The Cisco Service Contract Center is an integrated solution that makes it easy for Cisco service sales teams and partners to manage and grow their service business, profitably. It will:
● Quote and book your service orders and manage your service contracts and renewals all with one simple, easy-to-use solution.
● Allow you to spend less time solving administrative problems, searching for opportunities, and creating quotes.
● Allow you to spend more time growing your business using data you can trust; you don’t need to spend time fixing or verifying data.
● Enable partners to create and proactively manage their contracts.
Here is the link: https://wwwin.cisco.com/CustAdv/globalops/wwsso/service.shtml.
1.3 Orderability and First Customer Shipment (FCS)
Orderability for the following products/applications in [Product/Series] will be enabled on November 2, 2021:
● Cisco Secure Analytics: Top-level product family
● Cisco Secure Cloud Insights: Billable licenses
The projected First Customer Shipment (FCS) date for all of the products/applications listed above is November 2, 2021.
2. Cisco Secure Cloud Insights
Cisco Secure Cloud Insights® is a cloud-native platform brought to market in partnership with JupiterOne® and provides deep insights into an enterprise’s universe of ephemeral and evolving cyberassets. The service monitors multicloud deployments, both public and private cloud, as well as hybrid environments with a mix of on-premises infrastructure. Secure Cloud Insights is API driven and relies on agentless integrations to ingest data needed to map configuration and interactions between entities in an organization’s digital environment. This rich and connected data set can be investigated using approximately 550 prebuilt queries and can be presented in an easy-to-consume visual graph. Users can also easily create their own queries in J1QL, the proprietary JupiterOne Query Language. These queries can then be turned into security alerts, augment existing compliance benchmarks such as SOC-2, or be grouped to author custom standards.
These powerful capabilities greatly limit exposure resulting from an ever-increasing attack surface by identifying security and compliance gaps and allow continuous monitoring of an organization’s security posture, including, but not limited to, Cloud Security Posture Management (CSPM). Knowledge of relationships and interactions also fast-tracks investigations and aids threat containment and response. Finally, outbound integrations allow alerts to be routed to ticketing systems, email aliases, and messaging applications or publication/queuing services. Context can also be shared with other services via custom APIs. It is this capability that is leveraged for sharing context with other Cisco properties such as Secure Cloud Analytics and Cisco SecureX™.
The following table(s) outlines the product information and pricing for Cisco Secure Cloud Insights.
Cisco Secure Cloud Insights Software as a Service licenses:
| Product Number |
Description |
List Price ($US) |
| CSA-SUB |
Cisco Secure Analytics family of product |
$0, Category only |
| SCA-INS |
Secure Cloud Insights |
Variable based on # Billable Entities |
| SVC-CSA-SUP-B |
Basic Support for Cisco Secure Analytics family |
Embedded, $0 |
Billable Entities
Cisco Secure Cloud Insights licenses are based on the size or volume of the environments monitored, as measured in Billable Entites. An entity is a node stored in the graph database. Entities typically come from an integration and can also be added via the Asset Inventory web app or API (custom scripts).
Each entity represents an object from the organization's digital operational environment. Examples include an AWS EC2 instance, RDS DB cluster, RDS DB instance, IAM role, IAM policy, user endpoint, user, etc. Not all entities count toward billable category. For more details, refer to the online documentation or the table appended here.
The basic support option of Cisco Software Support for Security is available for Cisco Secure Cloud Insights in Cisco Commerce. Embedded as part of the service is basic online foundational support for the full term of the purchased software subscription, including access to support through online tools or email. Cisco will respond to a submitted case no later than the next business day during standard business hours.
For more information about Cisco Software Support for Security, refer to the service description.
Table 1. PIDs for Basic Services–Transaction
| Service Product Number |
Description |
Cost |
| SVS-CSA-SUP-B |
Basic embedded software support for Cisco Secure Analytics family of products |
$0 |
4. Cisco Tools for Quoting and Ordering
At the time of this document’s publishing, Cisco Secure Cloud Analytics is only available for ordering à la carte in Cisco’s Commerce website, with participation in buying programs scheduled for 2022. Here are the steps to order:
1. Start by searching for the CSA-SUB category and choosing it for editing options.
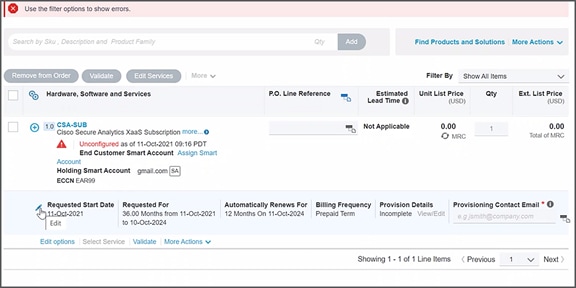
2. The order defaults to Secure Cloud Insights License SCA-INS nested under the only category available today, Secure Cloud Anaytics.
3. Enter the number of Billable Entities to be ordered. Note: The minimum order size is 3000 billable entities.
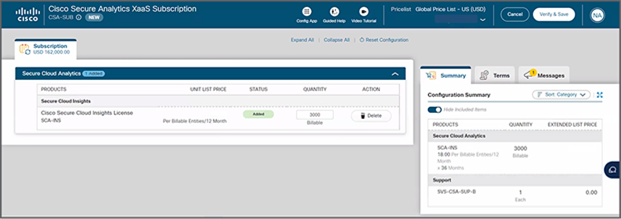
4. A $0 Technical Services Product Identifier SVS-CSA-SUP-B for basic support is attached with the order.
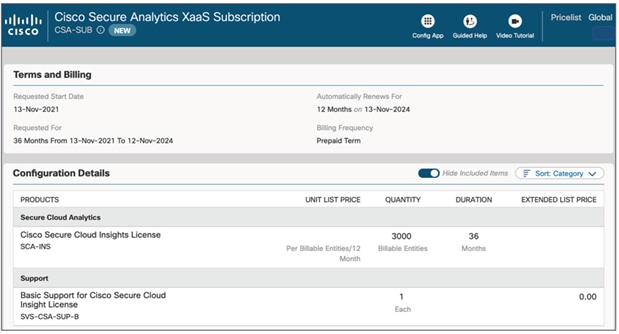
5. Modify the term of the subscription and payment term if desired. The default selection is a three-year term subscription, but one- and five-year terms are also available. Similarly, for payment options, choose between monthly, quarterly, annual, or prepaid.
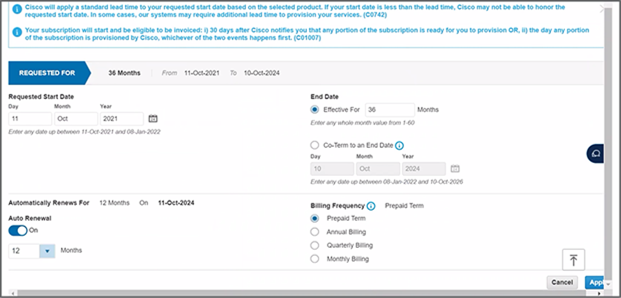
6. You are now ready to save and continue to add your order to the Cisco Commerce web account.
The significant benefits offered by [[Product/Series]] make it the natural choice [[for function]]. As with any technology investment, the question is the affordability of the new system. The answer is financing from Cisco Capital. Whether through flexible repayments to match expenditure in order to benefit and help mitigate cash flow issues, or an operating lease to help negate capital expenditure, we can give customers the financing solution that works best for them.
Cisco Capital can help remove or reduce the barriers preventing organizations from obtaining the technology they need. Total solution financing programs help customers and partners:
● Achieve business objectives
● Accelerate growth
● Acquire technology to match current strategies and future needs
● Remain competitive
Cisco Capital also helps your customers achieve financial goals such as optimizing investment dollars, turning CapEx into OpEx, and managing cash flow. And there’s just one predictable payment. Cisco Capital operates in more than 100 countries, so regardless of location, customers and partners have access to a trusted means to secure Cisco products and services.
For more information about Cisco Capital financing, visit the following.
● For Channel Partners: www.ciscocapital.com
● For Cisco Field: https://wwwin.cisco.com/FinAdm/csc/
| Description |
Billable |
|
| AccessKey |
A key used to grant access, such as ssh-key, access-key, api-key/token, mfa-token/device, etc. |
Yes |
| AccessPolicy |
A policy for access control assigned to a Host, Role, User, UserGroup, or Service. |
Yes |
| AccessRole |
An access control role mapped to a Principal (e.g., user, group, or service). |
Yes |
| Account |
An organizational account for a service or a set of services (e.g., AWS, Okta, Bitbucket Team, Google G-Suite account, Apple Developer Account). Each Account should be connected to a Service. |
Yes |
| Application |
A software product or application. |
Yes |
| ApplicationEndpoint |
An application endpoint is a program interface that either initiates or receives a request, such as an API. |
Yes |
| Assessment |
An object to represent an assessment, including both compliance assessment such as a HIPAA Risk Assessment or a technical assessment such as Penetration Testing. Each assessment should have findings (e.g., Vulnerability or Risk) associated. |
Yes |
| Attacker |
An attacker or threat actor. |
Yes |
| Backup |
A specific repository or data store containing backup data. |
Yes |
| Certificate |
A digital Certificate such as an SSL or S/MIME certificate. |
Yes |
| Channel |
A communication channel, such as a Slack channel or AWS SNS topic. |
Yes |
| Cluster |
A cluster of compute or database resources/workloads. |
Yes |
| CodeCommit |
A code commit to a repo. The commit id is captured in the _id property of the Entity. |
No |
| CodeDeploy |
A code deploy job. |
Yes |
| CodeModule |
A software module. Such as an npmmodule or javalibrary. |
Yes |
| CodeRepo |
A source code repository. A CodeRepo is also a DataRepository and therefore should carry all the required properties of DataRepository. |
Yes |
| CodeReview |
A code review record. |
Yes |
| Configuration |
A Configuration contains definitions that describe a resource such as a Task, Deployment, or Workload. For example, an aws_ecs_task_definition is a Configuration. |
Yes |
| Container |
A standard unit of software that packages up code and all its dependencies and configurations. |
Yes |
| Control |
A security or IT Control. A control can be implemented by a vendor/service, a person/team, a program/process, an automation code/script/configuration, or a system/host/device. Therefore, this is most likely an additional Class applied to a Service (e.g., Okta SSO), a Device (e.g., a physical firewall), or a HostAgent (e.g., Carbon Black CbDefense Agent). Controls are mapped to security policy procedures and compliance standards/requirements. |
Yes |
| ControlPolicy |
A technical or operational policy with rules that govern (or enforce, evaluate, monitor) a security control. |
Yes |
| CryptoKey |
A key used to perform cryptographic functions, such as an encryption key. |
Yes |
| DataObject |
An individual data object, such as an aws-s3-object, sharepoint-document, source-code, or a file (on disk). The exact data type is described in the _type property of the Entity. |
No |
| DataStore |
A virtual repository where data is stored, such as aws-s3-bucket, aws-rds-cluster, aws-dynamodb-table, bitbucket-repo, sharepoint-site, or docker-registry. The exact type is described in the _type property of the Entity. |
Yes |
| Database |
A database cluster/instance. |
Yes |
| Deployment |
A deployment of code, application, infrastructure, or service. For example, a Kubernetes deployment. An autoscaling group is also considered a deployment. |
Yes |
| Device |
A physical device or media, such as a server, laptop, workstation, smartphone, tablet, router, firewall, switch, wifi-access-point, usb-drive, etc. The exact data type is described in the _type property of the Entity. |
Yes |
| Directory |
Directory, such as LDAP or Active Directory. |
Yes |
| Disk |
A disk storage device such as an AWS EBS volume. |
Yes |
| Document |
A document or data object. |
No |
| Domain |
An internet domain. |
Yes |
| DomainRecord |
The DNS Record of a Domain Zone. |
No |
| DomainZone |
The DNS Zone of an Internet Domain. |
Yes |
| Finding |
A security finding, which may be a vulnerability or just an informative issue. A single finding may impact one or more resources. The IMPACTS relationship between the Vulnerability and the resource entity that was impacted serves as the record of the finding. The IMPACTS relationship carries properties such as 'identifiedOn', 'remediatedOn', 'remediationDueOn', 'issueLink', etc. |
No |
| Firewall |
A piece of hardware or software that protects a network/host/application. |
Yes |
| Framework |
An object to represent a standard compliance or technical security framework. |
Yes |
| Function |
A virtual application function. For example, an awslambdafunction, azurefunction, or googlecloud_function. |
Yes |
| Gateway |
A gateway/proxy that can be a system/appliance or software service, such as a network router or application gateway. |
Yes |
| Group |
A defined, generic group of Entities. This could represent a group of Resources, Users, Workloads, DataRepositories, etc. |
Yes |
| Host |
A compute instance that itself owns a whole network stack and serves as an environment for workloads. Typically, it runs an operating system. The exact host type is described in the _type property of the Entity. The UUID of the host should be captured in the _id property of the Entity. |
Yes |
| HostAgent |
A software agent or sensor that runs on a host/endpoint. |
Yes |
| Image |
A system image. For example, an AWS AMI (Amazon Machine Image). |
No |
| Incident |
An operational or security incident. |
Yes |
| Internet |
The Internet node in the graph. There should be only one Internet node. |
No |
| IpAddress |
A re-assignable IpAddress resource entity. Do not create an entity for an IP Address configured on a Host. Use this only if the IP Address is a reusable resource, such as an Elastic IP Address object in AWS. |
No |
| Key |
An ssh-key, access-key, api-key/token, pgp-key, etc. |
Yes |
| Logs |
A specific repository or destination containing application, network, or system logs. |
Yes |
| Module |
A software or hardware module. Such as an npmmodule or javalibrary. |
Yes |
| Network |
A network, such as an aws-vpc, aws-subnet, or cisco-meraki-vlan. |
Yes |
| NetworkEndpoint |
A network endpoint for connecting to or accessing network resources. For example, NFS mount targets or VPN endpoints. |
Yes |
| NetworkInterface |
A re-assignable software-defined network interface resource entity. Do not create an entity for a network interface configured on a Host. Use this only if the network interface is a reusable resource, such as an Elastic Network Interface object in AWS. |
No |
| Organization |
An organization, such as a company (e.g., JupiterOne) or a business unit (e.g., HR). An organization can be internal or external. Note that there is a more specific Vendor class. |
Yes |
| PR |
A pull request. |
No |
| PasswordPolicy |
A password policy is a specific Ruleset. It is separately defined because of its pervasive usage across digital environments and the well-known properties (such as length and complexity) unique to a password policy. |
Yes |
| Person |
An entity that represents an actual person, such as an employee of an organization. |
Yes |
| Policy |
A written policy documentation. |
Yes |
| Procedure |
A written procedure and control documentation. A Procedure typically IMPLEMENTS a parent Policy. An actual Control further IMPLEMENTS a Procedure. |
Yes |
| Process |
A compute process -- i.e., an instance of a computer program/software application that is being executed by one or many threads. This is NOT a program-level operational process (i.e., a Procedure). |
Yes |
| Product |
A product developed by the organization, such as a software product. |
Yes |
| Program |
A program. For example, a bug bounty/vuln disclosure program. |
Yes |
| Project |
A software development project. Can be used for other generic projects as well but the defined properties are geared toward software development projects. |
Yes |
| Queue |
A scheduling queue of computing processes or devices. |
Yes |
| Record |
A DNS record; or an official record (e.g., Risk); or a written document (e.g., Policy/Procedure); or a reference (e.g., Vulnerability/Weakness). The exact record type is captured in the _type property of the Entity. |
No |
| Repository |
A repository that contains resources. For example, a Docker container registry repository hosting Docker container images. |
Yes |
| Requirement |
An individual requirement for security, compliance, regulation, or design. |
Yes |
| Resource |
A generic assignable resource. A resource is typically nonfunctional by itself unless used by or attached to a host or workload. |
Yes |
| Review |
A review record. |
Yes |
| Risk |
An object that represents an identified Risk as the result of an Assessment. The collection of Risk objects in JupiterOne makes up the Risk Register. A Control may have a MITIGATES relationship to a Risk. |
Yes |
| Root |
The root node in the graph. There should be only one Root node per organization account. |
Yes |
| Rule |
An operational or configuration compliance rule, often part of a Ruleset. |
Yes |
| Ruleset |
An operational or configuration compliance ruleset with rules that govern (or enforce, evaluate, monitor) a security control or IT system. |
Yes |
| Scanner |
A system vulnerability, application code, or network infrastructure scanner. |
Yes |
| Section |
An object to represent a section such as a compliance section. |
Yes |
| Service |
A service provided by a vendor. |
Yes |
| Site |
The physical location of an organization. A Person (i.e., employee) would typically have a relationship to a Site (i.e., located at or workat). Also used as the abstract reference to AWS Regions. |
Yes |
| Standard |
An object to represent a standard such as a compliance or technical standard. |
Yes |
| Subscription |
A subscription to a service or channel. |
Yes |
| Task |
A computational task. Examples include AWS Batch Job, ECS Task, etc. |
Yes |
| Team |
A team consists of multiple member Person entities. For example, the Development team or the Security team. |
Yes |
| ThreatIntel |
Threat intelligence captures information collected from vulnerability risk analysis by those with substantive expertise and access to all-source information. Threat intelligence helps a security professional determine the risk of a vulnerability finding to their organization. |
Yes |
| Training |
A training module, such as security awareness training or secure development training. |
Yes |
| User |
A user account/login to access certain systems and/or services. Examples include okta-user, aws-iam-user, ssh-user, local-user (on a host), etc. |
Yes |
| UserGroup |
A user group, typically associated with some type of access control, such as a group in Okta or in Office365. If a UserGroup has an access policy attached, all member Users of the UserGroup would inherit the policy. |
Yes |
| Vault |
A collection of secrets such as a key ring. |
Yes |
| Vendor |
An external organization that is a vendor or service provider. |
Yes |
| Vulnerability |
A security vulnerability (application or system or infrastructure). A single vulnerability may relate to multiple findings and impact multiple resources. The IMPACTS relationship between the Vulnerability and the resource entity that was impacted serves as the record of the finding. The IMPACTS relationship carries properties such as 'identifiedOn', 'remediatedOn', 'remediationDueOn', 'issueLink', etc. |
Yes |
| Weakness |
A security weakness. |
Yes |
| Workload |
A virtual compute instance. It could be an aws-ec2-instance, a docker-container, an aws-lambda-function, an application-process, or a vmware-instance. The exact workload type is described in the _type property of the Entity. |
Yes |
| [System Mapped Entities] |
Entities with _source='system-mapper'. |
No |
| [System Internal Entities] |
Entities with _source='system-internal'. |
No |
| [Custom Created Entities] |
Entities created with a custom-defined _class or _type. |
Yes |