Deploy easily, segment effectively, secure comprehensively
Transform your network with identity-based security that simplifies operations, reduces hardware complexity, and delivers enterprise-grade zero-trust protection across your campus.
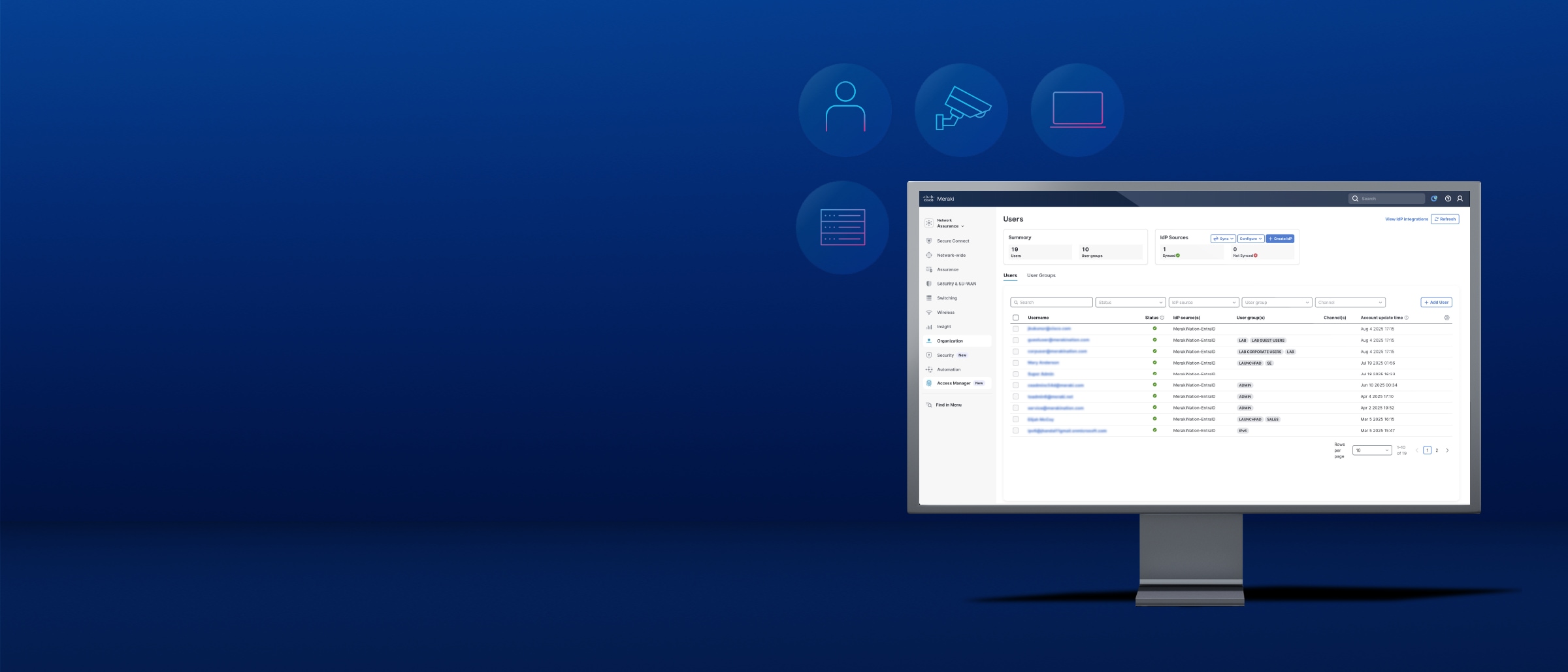
Embed identity into your network
Delivered as software as a service (SaaS) and integrated with the Meraki Dashboard, identity-based access is enforced seamlessly across your existing Meraki network.
Segment and protect everything
Identity-driven segmentation protects users, devices, and things across all supported infrastructure—enforced natively at every point, eliminating bottlenecks and delivering adaptive zero-trust protection.
Extend zero trust from campus to cloud
Meraki Dashboard brings together campus identity, cloud security, and context visibility with Cisco Access Manager, Cisco Secure Access, and Cisco XDR, providing continuous, adaptive zero-trust protection across your network.
At-a-Glance
Quick overview
Get a concise overview of identity-based access control with Meraki Dashboard.
Data sheet
Deeper dive
Get identity-based zero trust security without the appliances, complexity, or overhead of traditional access control solutions.
Resource landing page
One stop for all documents and resources
Access technical documentation, deployment guides, API references, video tutorials, and more—all in one place.
Solution Brief
Limit breach impact with identity-based segmentation
Learn how adaptive segmentation automatically contains compromises and prevents lateral movement—even when attackers have valid credentials.
Seamless integration ecosystem
Native Entra ID integration
Integrate seamlessly with Microsoft Entra ID for unified identity management. Leverage existing user directories without duplication or synchronization.
Unified with Meraki Dashboard
Delivered as pure SaaS within your existing Meraki Dashboard. Manage campus access, cloud security, and threat detection from one unified interface—no separate consoles or logins.
Add value to security solutions
Cisco Security Enterprise Agreement
Instant savings
Experience security software buying flexibility with one easy-to-manage agreement.
Services for security
Let the experts secure your business
Get more from your investments and enable constant vigilance to protect your organization.