The following attributes in the access-request packet are supported in this release.
-
USER-NAME
Description: String value encoded as per RFC 2865.
-
5G call: GPSI value is used, with stripped-off "msisdn-"
-
4G call: MSISDN value is used, with stripped-off "msisdn-"

Note |
PAP, CHAP, and MSCHAP authentication methods are not supported in this release.
|
-
PASSWORD
Description: Encrypted string value encoded as per RFC 2865.
For both 5G and 4G calls, selected RADIUS server's "secret" is set as user-password.
-
CALLING-STATION-ID
Description: String value encoded as per RFC 2865.
5G call: GPSI value is used, with stripped of "msisdn-"
4G call: MSISDN value is used, with stripped of "msisdn-"
-
CALLED-STATION-ID
Description: String value encoded as per RFC 2865.
For both 5G and 4G calls, DNN value is set as called-station-id.
-
NAS-IP-ADDRESS
Description: IPv4 address value encoded as per RFC 2865.
For both 5G and 4G calls, user-configured RADIUS Client interface-type's VIP-IP is used.
-
NAS-IDENTIFIER
Description: String value encoded as per RFC 2865.
For both 5G and 4G calls, user-configured nas-identifier attribute value is used.
-
SERVICE-TYPE
Description: 4-byte Octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, "FRAMED (2)" value is set.
-
FRAMED-PROTOCOL
Description: 4-byte Octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, "GPRS-PDP-CONTEXT (7)" value is set.
-
NAS-PORT-TYPE
Description: 4-byte Octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, "WIRELESS-OTHER (18)" value is set.
-
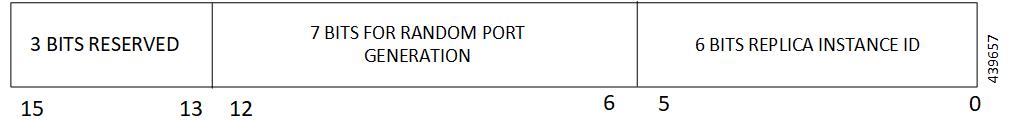
NAS-PORT
Description: 4-byte Octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, the base value of respective instance is used. That is:
0x40 00 00 00 is set for replica-0
0x40 00 00 01 is set for replica-1
-
3GPP-IMSI
Description: String value encoded as per 3GPP TS 29.061.
5G call: SUPI value is used.
4G call: IMSI value is used.
-
3GPP-CHARGING-ID
Description: 4-byte octet (int) value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, charging-ID is set.
-
3GPP-PDP-TYPE
Description: 4-byte octet (int) value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, pdp-type is set as follows:
-
0 = IPv4
-
2 = IPv6
-
3 = IPv4v6
-
3GPP-CHARGING-GATEWAY-ADDR
Description: 4-byte octet (IPv4-address) value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, charging gateway address is set.
-
3GPP-GPRS-NEG-QOS-PROFILE
Description: Octets (special encoding) value encoded as per 3GPP TS 29.061 and 29.274.
For 5G call, the values from default-qos profile of the system are used and the encoding is performed as follows:
Table 3. Non-GBR case
| 1-2 |
<Release indicator>- = "15" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-9 |
UL Session-AMBR length (UTF-8 encoded) |
| 10-m |
UL Session-AMBR (UTF-8 encoded) |
| (m+1) - (m+2) |
DL Session-AMBR length (UTF-8 encoded) |
| (m+3) – n |
DL Session-AMBR (UTF-8 encoded) |
Table 4. GBR case
| 1-2 |
<Release indicator> = "15" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-9 |
UL MFBR length (UTF-8 encoded) |
| 10-m |
UL MFBR (UTF-8 encoded) |
| (m+1)-(m+2) |
DL MFBR length (UTF-8 encoded) |
| (m+3)-n |
DL MFBR (UTF-8 encoded) |
| (n+1)-(n+2) |
UL GFBR length (UTF-8 encoded) |
| (n+3)-o |
UL GFBR (UTF-8 encoded) |
| (o+1) – (o+2) |
UL GFBR length (UTF-8 encoded) |
| (o+3) - p |
DL GFBR (UTF-8 encoded) |
For 4G call, the values from the default-qos profile of the system are used and the encoding is performed as follows:
Table 5. Non-GBR case
| 1-2 |
<Release indicator>- = "08" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-11 |
UL Session-AMBR (UTF-8 encoded) |
| 12-15 |
DL Session-AMBR (UTF-8 encoded) |
Table 6. GBR case
| 1-2 |
<Release indicator> = "08" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-11 |
UL MBR (UTF-8 encoded) |
| 12-15 |
DL MBR (UTF-8 encoded) |
| 16-19 |
UL GBR (UTF-8 encoded) |
| 20-23 |
DL GBR (UTF-8 encoded) |
-
3GPP-SGSN-ADDRESS
Description: 4-byte octet (IPv4-address) value encoded as per 3GPP TS 29.061.
For 5G call, the AMF address is set.
For 4G call, the S-GW address is set.
-
3GPP-GGSN-ADDRESS
Description: 4-byte octet (IPv4-address) value encoded as per 3GPP TS 29.061.
For both 5G and 4G call, SMF-Service IP is set.
-
3GPP-IMSI-MCC-MNC
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, SUPIs MCC and MNC values are set.
For 4G call, IMSIs MCC and MNC values are set.
MCC is first 3 bytes, MNC is next 2 or 3 bytes.
If MCC value is any of the following, then MNC will be of 3 bytes, else MNC will be of 2 bytes.
300 302 310 311 312 313 316 334 338 342 344 346 348 354 356 358 360 365 376 405 708 722 732
-
3GPP-GGSN-MCC-MNC
Description: String value encoded as per 3GPP TS 29.061.
For both 5G and 4G call, configured MCC and MNC value of SMF is used.
MCC is first 3 bytes, and MNC is next 2 or 3 bytes.
-
3GPP-SGSN-MCC-MNC
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, AMFs MCC and MNC values are set.
For 4G call, SGWs MCC and MNC values are set.
MCC is first 3 bytes, and MNC is next 2 or 3 bytes.
-
3GPP-NSAPI
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, QFI value from the defaultQos profile is set.
For 4G call, EPS bearer ID is set.
-
3GPP-SELECTION-MODE
Description: String value encoded as per 3GPP TS 29.061.
For both 4G and 5G call, value is set to "0".
-
3GPP-CHARGING-CHARACTERISTICS
Description: String value encoded as per 3GPP TS 29.061.
For both 4G and 5G call, generic charging character is set.
-
3GPP-IMEISV
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, PEI value is set.
For 4G call, IMEI value is set.
-
3GPP-RAT-TYPE
Description: 1-byte octet encoded as per 3GPP TS 29.061.
For 5G call, value "NR (10)" is set.
For 4G call, value "EUTRAN (6)" is set.
-
3GPP-USER-LOCATION
Description: Special encoded octet value encoded as per 3GPP TS 29.061.
For 5G call, the following encoding logic is used:
|
1
|
Location-Type
Only TAI = 136
Only NCGI = 135
Both TAI + NCGI =137
|
|
2-6
|
TAI-Encoding (if present)
|
| 7-14 |
NCGI-Encoding (if present)
|
TAI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4-5 |
TAC value |
NCGI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4 |
SPARE |
NCI |
| 5-8 |
NR Cell Identifier (NCI) |
For 4G call, the following encoding logic is used:
| 1 |
Location-Type |
| Only TAI = 128 |
| Only ECGI = 129 |
| Both TAI + ECGI =130 |
| 2-6 |
TAI-Encoding (if present) |
| 7-13 |
ECGI-Encoding (if present) |
TAI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4-5 |
TAC value |
ECGI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4 |
Spare |
ECI |
| 5-7 |
EUTRAN Cell Identifier (ECI) |
-
3GPP-MS-TIMEZONE
Description: Special encoded octet value encoded as per 3GPP TS 29.061.
Timezone string (for example: -07:00+1) is encoded as two-byte value mentioned below:
First byte timezone – NA
Second byte daylight – two bits used (00-0, 01-+1, 10-+2, 11 – Unused)
| 1 |
TIMEZONE |
| 2 |
DAYLIGHT SAVING 0, or +1 or +2 |
-
3GPP-NEGOTIATED-DSCP
Description: 1-byte octet encoded as per 3GPP TS 29.061
For both 5G and 4G calls, DSCP configuration from DNN qos-profile configuration is used.
Sub -> DNN profile -> QosProfile -> DSCPMap -> Qi5 value check -> ARP priority check

 Feedback
Feedback