Before enabling ECDSA on the solution components—CVP, Cisco Finesse, Cloud Connect, Cisco Unified Intelligence Center, Voice
Browser, IDS, and ECE—the administrator must ensure that the solution component’s ECDSA certificate is exported and installed
on the other component’s certificate store for the interface to become active.
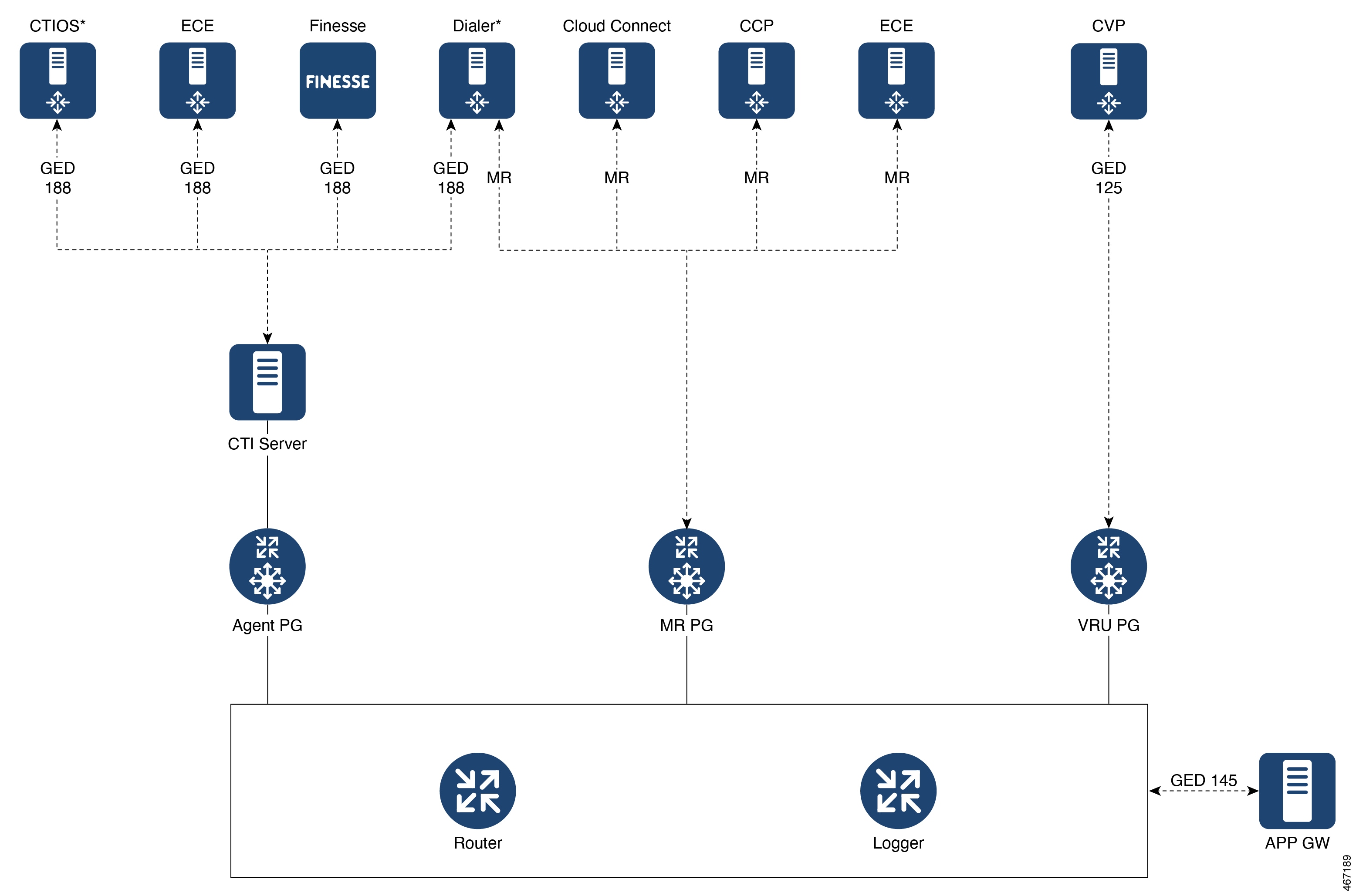
For example, before enabling ECDSA on the CTI Server, the CTI Server's ECDSA certificate has to be copied and installed on
Cisco Finesse, ECE, and Dialer. Before enabling ECDSA on Cisco Finesse, the Cisco Finesse ECDSA certificate has to be copied
and installed on the CTI server. This is required for 2-way authentication which is enabled by default on the CTI Server-to-Finesse
interface.
The administrator can enable ECDSA individually on each solution component, after the
certificate exchange is completed. The administrator has the option to enable ECDSA on
different solution components across multiple maintenance windows.

Note
|
A component operates on ECDSA only if the server is configured to use ECDSA.
|
For details about which components act as servers in various use cases, refer to the
table Server-Client Matrix for Secured Connections at Manage Secured PII in Transit.
Considerations for enabling ECDSA
Before enabling ECDSA, the administrator should be aware of the following:
-
After enabling or disabling ECDSA, the changes will take effect only after
you reboot the system.
-
In a one-way trust on the TLS interface, the component acting as client must
have the server ECDSA certificate in its store.
-
In a two-way trust on the TLS interface, both the client and the server
components should have the peer ECDSA certificate in their store.
-
Ensure to have mutual ECDSA certificates that are installed on high availability enabled components for seamless failover
in secured mode.
-
ECDSA can be enabled in any order on the solution components that support it.
However, it is recommended to enable it first on the server component.
-
If you want to enable CA-signed ECDSA certificate for a specific channel, the entire certificate chain must be enabled for
ECDSA.
-
If Cisco Finesse is enabled for ECDSA and Cisco Finesse IP Phone Agent (IPPA) is used in your deployment, you must ensure
that Cisco Unified Communications Manager is also enabled for ECDSA so that the Cisco Finesse IPPA phones can establish a
secure channel with both Cisco Finesse and Cisco Unified Communications Manager. To enable ECDSA in Cisco Unified Communications
Manager, see Security Guide for Cisco Unified Communications Manager at https://www.cisco.com/c/en/us/support/unified-communications/unified-communications-manager-callmanager/products-maintenance-guides-list.html.
-
Servers that are enabled with the ECDSA mode use ECDSA certificate and ciphers. Client with either RSA or ECDSA certificate
can connect to the server. For more information, refer to the table Server-Client Matrix at Manage Secured PII in Transit.
By default, self-signed ECDSA certificate exists in each solution component except where it is specified as not available
(for example, CVP). The self-signed certificate can be overridden with CA certificate if necessary.
RSA certificates will be used as the default cryptography algorithm. ECDSA can be
enabled or disabled as and when required.

 Feedback
Feedback