- Concepts
Authentication and Federated Identity
Revised: May 13, 2015
OL-15762-03

|
We prepared this material with specific expectations of you.
|

Note This material pertains to multiple releases of Cisco DMS.
Concepts
- Overview
- Glossary
- Understand the Requirement to Authenticate Users
- Decide Which Authentication Method to Use
- LDAP and Active Directory Concepts
- Federated Identity and Single Sign-on (SSO) Concepts
- Migration Between Authentication Methods
Overview
User authentication features of DMS-Admin help you to:
- NEW IN CISCO DMS 5.2.0 — Authenticate all user sessions. We now we prevent you from disabling mandatory authentication, even though we allowed this in Cisco DMS 5.1.x and prior releases.
- Choose and configure an authentication method.
- Import user account settings from an Active Directory server.
- NEW IN CISCO DMS 5.2.1 — Synchronize user groups from an Active Directory server.
- NEW IN CISCO DMS 5.2.3 — Use federation services with a SAML 2.0-compliant IdP to support SP-initiated “single sign-on” login authentication in your network (following an initial synchronization to a Microsoft Active Directory Server that populates the DMM user database).

Note We support your use of one — and only one — IdP server with Cisco DMS 5.2.3.
Glossary
Timesaver Go to terms that start with... [ A | C | D | F | I | L | O | R | S | U | X ].
|
Microsoft implementation of LDAP. A central authentication server and user store.
|
|
|
A domain-straddling combination of Active Directory trees within an organization that operates multiple Internet domains. Thus, the forest at “Amalgamated Example, LLC” might straddle all trees across example
.com
, example
.net
, and example
.org
.
Or, to use Cisco as a real-world case-study, one forest could straddle
cisco.com
and
webex.com
, among others.
Note This Cisco DMS release does not support Active Directory forests. |
|
|
Note NEW IN CISCO DMS 5.2.3 — This release is more strict than any prior release in its enforcement of proper LDAP syntax. Now, when you specify the administrator DN, you must use proper syntax, which conforms exactly to LDIF grammar. When you use poor syntax here for the first time while your DMM appliance runs DMS 5.2.3, we show you, the administrator, this error message: “Invalid username or password.” But if you used and validated poor syntax here before upgrading to Cisco DMS 5.2.3, we do not repeat the validation process. Therefore — even though we do not show an error message to anyone — LDAP users simply cannot log in . Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Otherwise, validation fails. |
|
|
The process to verify if a directory service entity has correctly claimed its own identity.
|
|
certification authority
. Authority that issues and manages security credentials and public keys, which any directory service entity relies upon to encrypt and decrypt messages exchanged with any other directory service entity. As part of a public key infrastructure (PKI), a CA checks with a registration authority (RA) to verify information that certificate requestors provide. After the RA verifies requestor information, the CA can then issue a certificate.
|
|
|
common name
. An attribute-value pair that names one directory service entity but indicates nothing about its context or position in a hierarchy. For example, you might see
cn=administrator
. But
cn=administrator
is so commonplace in theory that it might possibly recur many times in an Active Directory forest, while referring to more than just one directory service entity. An absence of context means that you cannot know which device, site, realm, user group, or other entity type requires the implied “administration” or understand why such “administration” should occur.
Therefore, use of a standalone CN is limited in the LDIF grammar. Absent any context, a standalone CN is only ever useful as an RDN.
Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Otherwise, validation fails. |
|
|
domain component
. An attribute to designate one constituent part of a
fully-qualified domain name
(FQDN). Suppose for example that you manage a server whose FQDN is
americas.example.com
. In this case, you would link together three DC attribute-value pairs:
DC=Americas,DC=example,dc=com.
Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Otherwise, validation fails. |
|
|
Uniquely encrypted digital representation of one directory service entity, whether physical or logical. This trustworthy representation certifies that the entity is not an imposter when it sends or receives data through a secured channel. The CA normally issues the certificate upon request by the entity or its representative. The requestor is then held accountable as the “certificate holder.” To establish and retain credibility, a certificate must conform to requirements set forth in International Organization for Standardization (ISO) standard X.509. Most commonly, a digital certificate includes the following.
|
|
|
Any single, named unit at any level within a nested hierarchy of named units, relative to a network. An entity’s essence depends upon its context. This context, in turn, depends upon interactions between at least two service providers — one apiece for the naming service and the directory service — in your network. Theoretically, an entity might represent any tangible thing or logical construct.
|
|
|
distinguished name
. A sequence of attributes that help a CA to distinguish a particular directory service entity uniquely for authentication. Distinct identity in this case arises from a text string of comma-delimited attribute-value pairs. Each attribute-value pair conveys one informational detail about the entity or its context. The comma-delimited string
is
the actual DN. It consists of the entity’s own CN, followed by at least one OU, and then concludes with at least one DC. For example:
Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Otherwise, validation fails.
Thus, each DN represents more than merely one isolated element. A DN also associates the element to its specific context within the Active Directory user base that your IdP depends upon.
Note A DN can change over the lifespan of its corresponding entity. For example, when you move entries in a tree, you might introduce new OU attributes or deprecate old ones that are elements of a DN. However, you can assign to any entity a reliable and unambiguous identity that persists beyond such changes to its context. To accomplish this, merely include a universally unique identifier (UUID) among the entity’s set of operational attributes. |
|
NEW IN CISCO DMS 5.2.3 —
identity provider
. One SAML 2.0-compliant server (synchronized to at least one Active Directory user base), that authenticates user session requests upon demand for SPs in one network subdomain. Furthermore, an IdP normalizes data from a variety of directory servers (user stores).
Users send their login credentials to an IdP over HTTPS, so the IdP can authenticate them to whichever SPs they are authorized to use. As an example, consider how an organization could use three IdPs.
Note Only a well known CA can issue the digital certificate for your IdP. Otherwise, you cannot use SSL, HTTPS, or LDAPS in Federation mode and, thus, all user credentials are passed in the clear. 
|
||
|
Note Before you try to configure SSL encryption and before you let anyone log in with SSL, you MUST: 
|
||
|
LDAP Data Interchange Format
. A strict grammar that SPs and IdPs use to classify and designate named elements and levels in Active Directory.
|
|
NEW IN CISCO DMS 5.2.3 —
SAML 2.0-compliant identity and access management server platform written in Java. OpenAM is open source software available under the Common Development and Distribution (CDDL) license. OpenAM is derived from and replaces OpenSSO Enterprise, which also used CDDL licensing. See
http://www.forgerock.com/openam.html
.
|
|
|
organizational unit
. An LDIF classification type for a logical container within a hierarchical system. In LDIF grammar, the main function of an OU value is to distinguish among superficially identical CNs that might otherwise be conflated. For example:
Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Otherwise, validation fails. |
|
relative distinguished name
. The CN for a directory service entity, as used exclusively (and still without any explicit context) by the one IdP that has synchronized this entity against an Active Directory user base. When an IdP encounters any RDN attribute in an LDIF reference, the IdP expects implicitly that its SAML 2.0-synchronized federation is the only possible context for the CN. It expects this because an IdP cannot authenticate — and logically should never encounter — a directory service entity whose RDN is meaningful to any other federation.
|
|
NEW IN CISCO DMS 5.2.3 —
A SAML 2.0-compliant architecture for federated identity-based authentication and authorization.
|
|
|
NEW IN CISCO DMS 5.2.3 —
single sign on
. (And sometimes
“single sign
off
.
”
) The main user-facing benefit of federation mode is that SPs begin — and end, in some implementations — user sessions on behalf of their entire federation. SSO is a convenience for users, who can log in only once per day as their work takes them between multiple servers that are related but independent. Furthermore, SSO is a convenience to IT staff, who spend less time on user support, password fatigue, compliance audits, and so on.
|
|
Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Otherwise, validation fails. |
|
|
Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Otherwise, validation fails. |
|
|
A user filter limits the scope of an agreement to import filtered records from an Active Directory user base.
Note An LDAP expression must never include a space immediately to either side of a “=” sign. Similarly, it must never include a space immediately to either side of an “objectClass” attribute. Nor can a group name include any spaces. Otherwise, validation fails. |
|
A standard for public key infrastructure. X.509 specifies, among other things, standard formats for public key certificates and a certification path validation algorithm. |
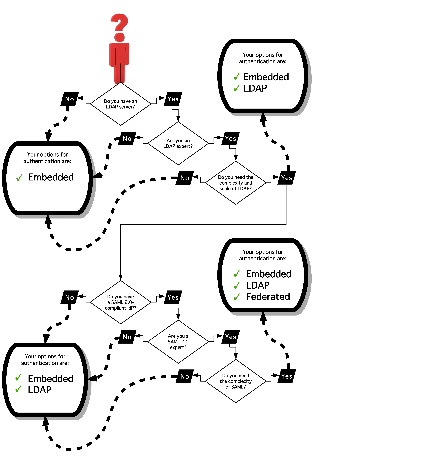
Understand the Requirement to Authenticate Users
Although Cisco DMS always authenticates users, we support three authentication methods.

- Embedded authentication is completely native to Cisco DMS. It does not depend on any external servers.
- LDAP authentication causes Cisco DMS products to rely on one — and only one — Microsoft Active Directory server and a Microsoft Internet Information Server (IIS). Thus, setup and operation with this method are more complex than with embedded authentication.
- NEW IN CISCO DMS 5.2.3 — Federation mode — also known as single sign-on (SSO) causes Cisco DMS products to rely on a SAML 2.0-compliant IdP in combination with a Microsoft Active Directory server and IIS. Thus, setup and operation with this method are more complex than with LDAP authentication.

Note You must choose one of these methods. The method that you use determines which login screen your users will see.

Tip • After a user session times out, we prompt the affected user to log in twice.
- An unresponsive Active Directory server can hang a login prompt for 20 minutes without any error message.
|
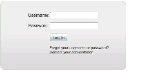
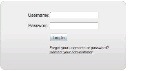
FEDERATION (SSO) MODE 1
|
||
|---|---|---|
|
|
IdP-specific login screen ( NEW IN CISCO DMS 5.2.3 ) 
|
LDAP is Highly Complex

Plan Ahead
- Install and configure Active Directory and Internet Information Services (IIS) before you try to configure LDAP authentication mode or federation mode in DMS-Admin.

Tip We support IIS 6 on Windows Server 2003.
- Pair your DMM appliance and your Show and Share appliance in AAI before you configure Cisco DMS to use LDAP authentication. Otherwise, video tutorials for Show and Share are not loaded onto your Show and Share appliance.
- Make sure that you have generated or imported certificates as necessary and activated SSL on the Active Directory server before you try to configure SSL encryption.
Synchronization (Replication) Overview
When you choose LDAP authentication or SSO authentication, user account data originates from your Active Directory server. However, Cisco DMS does not synchronize (replicate) this data automatically, in real time. Instead, we cache it. Therefore, you must resynchronize user account data when you think it is appropriate to do so. You can:

Note Features of Digital Signs and Show and Share Administration help you to manage user access privileges and permissions for Cisco DMS.
DMS-Admin synchronizes all user accounts in the Active Directory “user base” that your filter specifies, except users whose accounts are disabled on your Active Directory server.
Synchronization Types
We support four types of Active Directory synchronization in LDAP mode or federation mode.
Runs a one-time synchronization for a new filter that you never synchronized previously. |
Runs an incremental, fast update to find and make up for any differences between user accounts that match your Active Directory filter and your local copy of those user accounts. |
Overwrites your local copy of user accounts that correspond to your Active Directory filter with new copies of those user accounts. In addition, deletes your local copy of each user account that has been deleted from Active Directory since the last time that you ran a synchronization. |
Deletes your local copy of user accounts that correspond to a defined Active Directory filter and deletes the entry for that filter from DMS-Admin. |
Understand Synchronization of a DMM Group to an LDAP Filter

|

|
|

|
||
- In most cases, you can associate one LDAP filter apiece to one DMM user group. Likewise, in most cases, you can associate one DMM user group apiece to one LDAP filter. The Digital Signs user group is an exception to both of these principles. It is built-in to Cisco DMS.
- After you associate a DMM user group to an LDAP filter, you cannot use features on the Users tab to delete the DMM user group until after you delete the LDAP filter. However, even when you delete an LDAP filter, there is no requirement to delete its associated DMM user group. Furthermore, there is no way for you to delete the Digital Signs user group. It is built-in to Cisco DMS.
Understand Manual Synchronization
Manual synchronization mode requires you to choose Administration > Settings > Authentication > Synchronize Users > LDAP Bookmarks during all future synchronizations. Afterward, you must click Update.

Note Manual synchronization mode deletes your schedule for automatic synchronizations.
Understand Automatic Synchronization
Automatic synchronization mode automates and schedules incremental updates to user accounts that match Active Directory filters that you defined in DMS-Admin. When you use automatic synchronization mode, new fields and elements become available to you. These help you to configure the settings for automatic synchronization.

Tip See the “Understand Synchronization of a DMM Group to an LDAP Filter” section.
Guidelines for Synchronization
We recommend that you synchronize your LDAP bookmarks periodically. Synchronization ensures that user and group membership associations are current and correct.
The Initial option is CPU-intensive for your DMM appliance and might lower performance temporarily. We recommend that you use it during off-peak hours only. |
|
We recommend that you use the Update option whenever:
|
|
Note The Overwrite option is CPU-intensive for your DMM appliance and might lower its performance temporarily. We recommend that you use this option during off-peak hours only.
|
|

Caution The Delete option is destructive by design. We advise that you use it sparingly and with great caution. Among other effects, your deletion of an LDAP bookmark can affect user access to videos in Show and Share.
Note Typically, the deletion process takes about 1 minute to finish. However, when there are more than 50,000 users in the Active Directory database, this process might run in the background and take about 30 minutes to finish. In this case, the user interface in DMS-Admin can show that a bookmark was deleted even though the actual process has not finished. If you observe this behavior, simply allow 30 minutes for the operation to finish. |
Understand LDAP Attributes
Ordinarily, DMS-Admin will not import any user account from your Active Directory server when the value in it is blank for any of these attributes:
- Login User Name — This required value always must be unique.
- First Name — This required value might be identical for multiple users.
- Last Name — This required value might also be identical for multiple users.
However, you can import and synchronize all of the Active Directory user accounts that match your filters. You can do this even when some of the user accounts are incomplete because one or more of their attributes have blank values.
To prevent these undefined attributes from blocking the import of the user accounts they are meant to describe, you can enter generic values for most attributes in the Values to Use by Default column. DMS-Admin takes the generic values that you enter, and then inserts them automatically where they are needed.

Tip Nonetheless, you cannot enter a default value for the Login User Name attribute. Usernames are unique.
Guidelines for LDAP Filters
- Use “OU” values to impose rough limits on a filter
- Use “memberOf” values to pinpoint a filter more precisely
- Use “objectClass” values to match all user records
Use “OU” values to impose rough limits on a filter
- Never use a filter that defines the user base at the domain level. For example, this filter is not acceptable.
Use “memberOf” values to pinpoint a filter more precisely
- But what if you did not want to include any members of Milpitas or Sunnyvale? If your Active Directory server considered these cities (organizational units) to be subsets of San José, how could you exclude their members? To do so, you would use the
attribute. It stops LDAP from matching records at any lower level than the one you name explicitly. In this scenario for example, you would use
to match only the direct members of the “SanJose” OU.
Password Concepts

Note NEW IN CISCO DMS 5.2.3 — User passwords in Cisco DMS are no longer case-sensitive.
Understand the Effects of a Changed Password in Active Directory
After you change a user password on your Active Directory server, there is no requirement to resynchronize the affected user account in DMS-Admin.
Understand the Effects of a Blank Password in Active Directory
- Even though it is possible in Active Directory to use a blank value for a password, Cisco DMS does not allow it.
- When you choose LDAP authentication, any user whose Active Directory password is blank is prevented from logging in to any component of Cisco DMS.
- Access is enabled or restored after the password is populated on the Active Directory server.
Understand Authentication Property Sheets for LDAP
The Authentication page contains four tabbed property sheets.
Embedded, LDAP, or ( NEW IN CISCO DMS 5.2.3 ) SSO Select Mode is by default the only active tab. Your choices on the Select Mode property sheet determine whether you have access to the other three property sheets. |
||
LDAP or ( NEW IN CISCO DMS 5.2.3 ) SSO Your choices on the Define Filter property sheet help you to configure and add a new agreement. |
||
LDAP or ( NEW IN CISCO DMS 5.2.3 ) SSO Your choices on the Synchronize Users property sheet help you to submit a new agreement. |
||
IdP Requirements
NEW IN CISCO DMS 5.2.3 — To use federation (SSO) mode in Cisco DMS, you must have access to an IdP that meets our requirements. Your IdP must:
– Web Browser SSO Profile
Configuration Workflow to Activate Federation (SSO) Mode
1. Configure and set up an Active Directory server.
2. Configure and set up a SAML 2.0-compliant IdP.

Note When you use a “fresh install” of Cisco DMS 5.2.3 (as opposed to an upgrade), your DMM appliance is configured to use embedded authentication mode by default. But when you upgrade a DMM server that was already configured for an earlier Cisco DMS release, it might use either embedded mode or LDAP mode.
3. Obtain a digital certificate from a trusted CA and install it on your IdP.
4. Use DMS-Admin to configure Cisco DMS for federation mode.
5. Export SAML 2.0-compliant metadata from your DMM server and import it into your IdP.
6. Export SAML 2.0-compliant metadata from your IdP and import it into your DMM server.
7. Configure Active Directory exactly as you would in LDAP mode.
8. Click Update to save your work, and then advance to the Synchronize Users property sheet.
9. Synchronize DMM with your Active Directory server to populate the DMM user database.

Note You MUST configure at least one LDAP bookmark.
10. Synchronize users exactly as you would in LDAP mode.

Note Whenever you change any setting or value on your IdP or any of your SPs, you must reestablish their pairing to restore mutual trust among them.
SSO Scenario 1 — Trusted + Valid + Authorized
|
1. A web browser requests access to a protected resource on an SP. 
Your federation will not approve or deny this request until it knows more. |
|
|
2. The SP asks its IdP if the browser is currently authenticated to any valid user account in the CoT. |
|
|
3. The IdP verifies that: |
|
|
4. The IdP acts on the SP’s behalf and redirects the browser immediately to the protected resource. |
SSO Scenario 2 — Trusted + Valid + NOT Authorized
|
1. A web browser requests access to a protected resource on an SP. 
Your federation will not approve or deny this request until it knows more. |
|
|
2. The SP asks its IdP if the browser is currently authenticated to any valid user account in the CoT. |
|
|
3. The IdP verifies that: |
|
|
4. The IdP redirects the browser to the SP , where an HTTP 403 Forbidden message states that the user is not authorized to access the protected resource. |
SSO Scenario 3 — Nothing Known
|
1. A web browser requests access to a protected resource on an SP. 
Your federation will not approve or deny this request until it knows more. |
|
|
2. The SP asks its IdP if the browser is currently authenticated to any valid user account in the CoT. |
|
|
3. The IdP reports that: |
|
|
4. The SP redirects the browser automatically to an HTTPS login prompt on the IdP, where one of the following occurs.
|
Understand Migration (from Either LDAP or SSO) to Embedded
When you migrate from LDAP or federation mode to embedded authentication mode, you must explicitly choose whether to keep local copies of the:
- User accounts that were associated to LDAP filters.
- Groups and policies that were associated to LDAP filters.

Note • Unless you choose explicitly to keep the local copy of a user, a group, or a policy, we discard the local copy.
The result varies according to the combination of your choices.
|
|||
|
6.This security feature protects your network and user data. If anyone gains unauthorized access to the exported file and tries to use it, Active Directory rejects the invalid passwords. |
 Embedded Mode
Embedded Mode LDAP Mode
LDAP Mode Federation Mode
Federation Mode
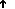
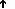
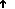












 Feedback
Feedback