- Preface
- Overview
- Using the Command-Line Interface
- Configuring the Switch Alarms
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS Configuration Engine
- Clustering Switches
- Administering the Switch
- Configuring PTP
- Configuring PROFINET
- Configuring SDM Templates
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring SGT Exchange Protocol over TCP (SXP) and Layer 3 Transport
- Configuring Interface Characteristics
- Configuring Smartports Macros
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLAN
- Configuring Private VLANs
- Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Resilient Ethernet Protocol
- Configuring Flex Links and the MAC Address-Table Move Update Feature
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring Port-Based Traffic Control
- Configuring SPAN and RSPAN
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring CDP
- Configuring UDLD
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Embedded Event Manager
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring EtherChannels and Link-State Tracking
- Configuring IP Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring IPv6 ACLs
- Configuring IPv6 MLD Snooping
- Configuring HSRP and VRRP
- Configuring Cisco IOS IP SLAs Operations
- Configuring Enhanced Object Tracking
- Configuring Web Cache Services By Using WCCP
- Configuring Fallback Bridging
- Troubleshooting
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 15.2(2)E
- Index
Software Configuration Guide, Cisco IOS Release 15.2(2)E (Industrial Ethernet 3000 Switch)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- May 15, 2014
Chapter: Configuring Embedded Event Manager
Configuring Embedded Event Manager
Embedded Event Manager (EEM) is a distributed and customized approach to event detection and recovery within a Cisco IOS device. EEM offers the ability to monitor events and take informational, corrective, or any other EEM action when the monitored events occur or when a threshold is reached. An EEM policy defines an event and the actions to be taken when that event occurs.
This chapter tells how to use EEM and how to configure it on the IE3000 switch. For complete syntax and usage information for the commands used in this chapter, see the switch command reference for this release and the Cisco IOS Network Management Command Reference . For the complete EEM document set, see these documents in the Cisco IOS Network Management Configuration Guide:
http://www.cisco.com/en/US/docs/ios/netmgmt/configuration/guide/nm_eem_overview.html
http://www.cisco.com/en/US/docs/ios/netmgmt/configuration/guide/nm_eem_policy_cli.html
http://www.cisco.com/en/US/docs/ios/netmgmt/configuration/guide/nm_eem_policy_tcl.html

Note This feature is supported only on switches running the IP services image.
Understanding Embedded Event Manager
EEM monitors key system events and then acts on them through a set policy. This policy is a programmed script that you can use to customize a script to invoke an action based on a given set of events occurring. The script generates actions such as generating custom syslog or Simple Network Management Protocol (SNMP) traps, invoking CLI commands, forcing a failover, and so forth. The event management capabilities of EEM are useful because not all event management can be managed from the switch and because some problems compromise communication between the switch and the external network management device. Network availability is improved if automatic recovery actions are performed without rebooting the switch.
Figure 37-1 shows the relationship between the EEM server, the core event publishers (event detectors), and the event subscribers (policies). The event publishers screen events and publish them when there is a match on an event specification that is provided by the event subscriber. Event detectors notify the EEM server when an event occurs. The EEM policies then implement recovery based on the current state of the system and the actions specified in the policy for the given event.
Figure 37-1 Embedded Event Manager Core Event Detectors
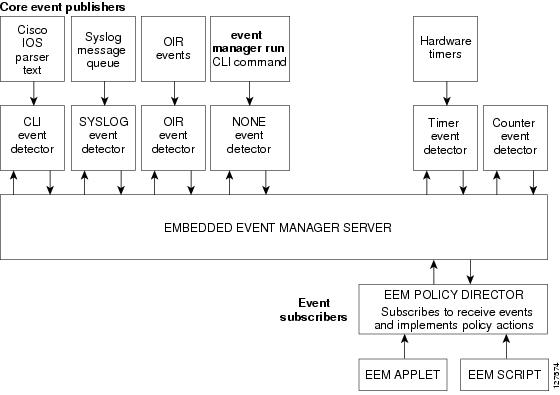
See the EEM Configuration for Cisco Integrated Services Router Platforms Guide for examples of EEM deployment.
- Event Detectors
- Embedded Event Manager Actions
- Embedded Event Manager Policies
- Embedded Event Manager Environment Variables
Event Detectors
EEM software programs known as event detectors determine when an EEM event occurs. Event detectors are separate systems that provide an interface between the agent being monitored, for example SNMP, and the EEM policies where an action can be implemented.
- Application-specific event detector—Allows any EEM policy to publish an event.
- IOS CLI event detector—Generates policies based on the commands entered through the CLI.
- Counter event detector—Publishes an event when a named counter crosses a specified threshold.
- Interface counter event detector— Publishes an event when a generic Cisco IOS interface counter for a specified interface crosses a defined threshold. A threshold can be specified as an absolute value or an incremental value. For example, if the incremental value is set to 50 an event would be published when the interface counter increases by 50.
This detector also publishes an event about an interface based on the rate of change for the entry and exit values.
- None event detector—Publishes an event when the event manager run CLI command executes an EEM policy. EEM schedules and runs policies on the basis on an event specification within the policy itself. An EEM policy must be manually identified and registered before the event manager run command executes.
- Online insertion and removal event detector—Publishes an event when a hardware insertion or removal (OIR) event occurs.
- Resource threshold event detector—Generates policies based on global platform values and thresholds. Includes resources such as CPU utilization and remaining buffer capacity.
- Remote procedure call (RPC) event detector—Invokes EEM policies from outside the switch over an encrypted connecting using Secure Shell (SSH) and uses Simple Object Access Protocol (SOAP) data encoding for exchanging XML-based messages. It also runs EEM policies and then gets the output in a SOAP XML-formatted reply.
- SNMP event detector—Allows a standard SNMP MIB object to be monitored and an event to be generated when
–![]() The object matches specified values or crosses specified thresholds.
The object matches specified values or crosses specified thresholds.
–![]() The SNMP delta value, the difference between the monitored Object Identifier (OID) value at the beginning the period and the actual OID value when the event is published, matches a specified value.
The SNMP delta value, the difference between the monitored Object Identifier (OID) value at the beginning the period and the actual OID value when the event is published, matches a specified value.
- SNMP notification event detector—Intercepts SNMP trap and inform messages received by the switch. The event is generated when an incoming message matches a specified value or crosses a defined threshold.
- Syslog event detector—Allows for screening syslog messages for a regular expression pattern match. The selected messages can be further qualified, requiring that a specific number of occurrences be logged within a specified time. A match on a specified event criteria triggers a configured policy action.
- Timer event detector—Publishes events for
–![]() An absolute-time-of-day timer publishes an event when a specified absolute date and time occurs.
An absolute-time-of-day timer publishes an event when a specified absolute date and time occurs.
–![]() A countdown timer publishes an event when a timer counts down to zero.
A countdown timer publishes an event when a timer counts down to zero.
–![]() A watchdog timer publishes an event when a timer counts down to zero. The timer automatically resets itself to its initial value and starts to count down again.
A watchdog timer publishes an event when a timer counts down to zero. The timer automatically resets itself to its initial value and starts to count down again.
–![]() A CRON timer publishes an event by using a UNIX standard CRON specification to define when the event is to be published. A CRON timer never publishes events more than once per minute.
A CRON timer publishes an event by using a UNIX standard CRON specification to define when the event is to be published. A CRON timer never publishes events more than once per minute.
–![]() CPU utilization for a Cisco IOS process crosses a threshold.
CPU utilization for a Cisco IOS process crosses a threshold.
–![]() Memory utilization for a Cisco IOS process crosses a threshold.
Memory utilization for a Cisco IOS process crosses a threshold.
Two events can be monitored at the same time, and the event publishing criteria requires that one or both events cross their specified thresholds.
Embedded Event Manager Policies
EEM can monitor events and provide information, or take corrective action when the monitored events occur or a threshold is reached. An EEM policy is an entity that defines an event and the actions to be taken when that event occurs.
There are two types of EEM policies: an applet or a script. An applet is a simple policy that is defined within the CLI configuration. It is a concise method for defining event screening criteria and the actions to be taken when that event occurs. Scripts are defined on the networking device by using an ASCII editor. The script, which can be a bytecode (.tbc) and text (.tcl) script, is then copied to the networking device and registered with EEM. You can also register multiple events in a .tcl file.
You use EEM to write and implement your own policies using the EEM policy tool command language (TCL) script.
Cisco enhancements to TCL in the form of keyword extensions facilitate the development of EEM policies. These keywords identify the detected event, the subsequent action, utility information, counter values, and system information.
For complete information on configuring EEM policies and scripts, see the Cisco IOS Network Management Configuration Guide, Release 12.4T.
Embedded Event Manager Environment Variables
EEM uses environment variables in EEM policies. These variables are defined in a EEM policy tool command language (TCL) script by running a CLI command and the event manager environment command.
Defined by the user for a user-defined policy.
Defined by Cisco for a specific sample policy.
Defined by Cisco and can be read-only or read-write. The read-only variables are set by the system before an applet starts to execute. The single read-write variable, _exit_status, allows you to set the exit status for policies triggered from synchronous events.
Cisco-defined environment variables and Cisco system-defined environment variables might apply to one specific event detector or to all event detectors. Environment variables that are user-defined or defined by Cisco in a sample policy are set by using the event manager environment global configuration command. You must defined the variables in the EEM policy before you register the policy.
For information about the environmental variables that EEM supports, see the Cisco IOS Network Management Configuration Guide, Release 12.4T.
Configuring Embedded Event Manager
- Registering and Defining an Embedded Event Manager Applet
- Registering and Defining an Embedded Event Manager TCL Script
For complete information about configuring embedded event manager, see the Cisco IOS Network Management Configuration Guide, Release 12.4T.
Registering and Defining an Embedded Event Manager Applet
Beginning in privileged EXEC mode, perform this task to register an applet with EEM and to define the EEM applet using the event applet and action applet configuration commands.
This example shows the output for EEM when one of the fields specified by an SNMP object ID crosses a defined threshold:
These examples show actions that are taken in response to an EEM event:
Registering and Defining an Embedded Event Manager TCL Script
Beginning in privileged EXEC mode, perform this task to register a TCL script with EEM and to define the TCL script and policy commands.
This example shows the sample output for the show event manager environment command:
This example shows a CRON timer environment variable, which is assigned by the software, to be set to every second minute, every hour of every day:
This example shows the sample EEM policy named tm_cli_cmd.tcl registered as a system policy. The system policies are part of the Cisco IOS image. User-defined TCL scripts must first be copied to flash memory.
 Feedback
Feedback