- Preface
- Overview
- Using the Command-Line Interface
- Configuring the Switch Alarms
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS Configuration Engine
- Clustering Switches
- Administering the Switch
- Configuring PTP
- Configuring PROFINET
- Configuring SDM Templates
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring SGT Exchange Protocol over TCP (SXP) and Layer 3 Transport
- Configuring Interface Characteristics
- Configuring Smartports Macros
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLAN
- Configuring Private VLANs
- Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Resilient Ethernet Protocol
- Configuring Flex Links and the MAC Address-Table Move Update Feature
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring Port-Based Traffic Control
- Configuring SPAN and RSPAN
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring CDP
- Configuring UDLD
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Embedded Event Manager
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring EtherChannels and Link-State Tracking
- Configuring IP Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring IPv6 ACLs
- Configuring IPv6 MLD Snooping
- Configuring HSRP and VRRP
- Configuring Cisco IOS IP SLAs Operations
- Configuring Enhanced Object Tracking
- Configuring Web Cache Services By Using WCCP
- Configuring Fallback Bridging
- Troubleshooting
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 15.2(2)E
- Index
- Understanding SNMP
- Configuring SNMP
- Default SNMP Configuration
- SNMP Configuration Guidelines
- Disabling the SNMP Agent
- Configuring Community Strings
- Configuring SNMP Groups and Users
- Configuring SNMP Notifications
- Setting the CPU Threshold Notification Types and Values
- Setting the Agent Contact and Location Information
- Limiting TFTP Servers Used Through SNMP
- SNMP Examples
- Displaying SNMP Status
Configuring SNMP
This chapter describes how to configure the Simple Network Management Protocol (SNMP) on the IE 3000 switch.

Note For complete syntax and usage information for the commands used in this chapter, see the command reference for this release and the Cisco IOS Network Management Command Reference, Release 12.4.
Understanding SNMP
SNMP is an application-layer protocol that provides a message format for communication between managers and agents. The SNMP system consists of an SNMP manager, an SNMP agent, and a MIB. The SNMP manager can be part of a network management system (NMS) such as CiscoWorks. The agent and MIB reside on the switch. To configure SNMP on the switch, you define the relationship between the manager and the agent.
The SNMP agent contains MIB variables whose values the SNMP manager can request or change. A manager can get a value from an agent or store a value into the agent. The agent gathers data from the MIB, the repository for information about device parameters and network data. The agent can also respond to a manager’s requests to get or set data.
An agent can send unsolicited traps to the manager. Traps are messages alerting the SNMP manager to a condition on the network. Traps can mean improper user authentication, restarts, link status (up or down), MAC address tracking, closing of a TCP connection, loss of connection to a neighbor, or other significant events.
These sections contain this conceptual information:
- SNMP Versions
- SNMP Manager Functions
- SNMP Agent Functions
- SNMP Community Strings
- Using SNMP to Access MIB Variables
- SNMP Notifications
- SNMP ifIndex MIB Object Values
- SNMP Support for DOM MIB
SNMP Versions
This software release supports these SNMP versions:
- SNMPv1—The Simple Network Management Protocol, a Full Internet Standard, defined in RFC 1157.
- SNMPv2C replaces the Party-based Administrative and Security Framework of SNMPv2Classic with the community-string-based Administrative Framework of SNMPv2C while retaining the bulk retrieval and improved error handling of SNMPv2Classic. It has these features:
–![]() SNMPv2—Version 2 of the Simple Network Management Protocol, a Draft Internet Standard, defined in RFCs 1902 through 1907.
SNMPv2—Version 2 of the Simple Network Management Protocol, a Draft Internet Standard, defined in RFCs 1902 through 1907.
–![]() SNMPv2C—The community-string-based Administrative Framework for SNMPv2, an Experimental Internet Protocol defined in RFC 1901.
SNMPv2C—The community-string-based Administrative Framework for SNMPv2, an Experimental Internet Protocol defined in RFC 1901.
- SNMPv3—Version 3 of the SNMP is an interoperable standards-based protocol defined in RFCs 2273 to 2275. SNMPv3 provides secure access to devices by authenticating and encrypting packets over the network and includes these security features:
–![]() Message integrity—ensuring that a packet was not tampered with in transit
Message integrity—ensuring that a packet was not tampered with in transit
–![]() Authentication—determining that the message is from a valid source
Authentication—determining that the message is from a valid source
–![]() Encryption—mixing the contents of a package to prevent it from being read by an unauthorized source.
Encryption—mixing the contents of a package to prevent it from being read by an unauthorized source.

Note To select encryption, enter the priv keyword. This keyword is available only when the cryptographic (encrypted) software image is installed.
Both SNMPv1 and SNMPv2C use a community-based form of security. The community of managers able to access the agent’s MIB is defined by an IP address access control list and password.
SNMPv2C includes a bulk retrieval mechanism and more detailed error message reporting to management stations. The bulk retrieval mechanism retrieves tables and large quantities of information, minimizing the number of round-trips required. The SNMPv2C improved error-handling includes expanded error codes that distinguish different kinds of error conditions; these conditions are reported through a single error code in SNMPv1. Error return codes in SNMPv2C report the error type.
SNMPv3 provides for both security models and security levels. A security model is an authentication strategy set up for a user and the group within which the user resides. A security level is the permitted level of security within a security model. A combination of the security level and the security model determine which security mechanism is used when handling an SNMP packet. Available security models are SNMPv1, SNMPv2C, and SNMPv3.
Table 36-1 identifies the characteristics of the different combinations of security models and levels.
You must configure the SNMP agent to use the SNMP version supported by the management station. Because an agent can communicate with multiple managers, you can configure the software to support communications using SNMPv1, SNMPv2C, or SNMPv3.
SNMP Manager Functions
The SNMP manager uses information in the MIB to perform the operations described in Table 36-2 .
Retrieves a value from a variable within a table.1 |
|
get-bulk-request2 |
Retrieves large blocks of data, such as multiple rows in a table, that would otherwise require the transmission of many small blocks of data. |
Replies to a get-request, get-next-request, and set-request sent by an NMS. |
|
An unsolicited message sent by an SNMP agent to an SNMP manager when some event has occurred. |
|
1.With this operation, an SNMP manager does not need to know the exact variable name. A sequential search is performed to find the needed variable from within a table. |
SNMP Agent Functions
The SNMP agent responds to SNMP manager requests as follows:
- Get a MIB variable—The SNMP agent begins this function in response to a request from the NMS. The agent retrieves the value of the requested MIB variable and responds to the NMS with that value.
- Set a MIB variable—The SNMP agent begins this function in response to a message from the NMS. The SNMP agent changes the value of the MIB variable to the value requested by the NMS.
The SNMP agent also sends unsolicited trap messages to notify an NMS that a significant event has occurred on the agent. Examples of trap conditions include, but are not limited to, when a port or module goes up or down, when spanning-tree topology changes occur, and when authentication failures occur.
SNMP Community Strings
SNMP community strings authenticate access to MIB objects and function as embedded passwords. In order for the NMS to access the switch, the community string definitions on the NMS must match at least one of the three community string definitions on the switch.
A community string can have one of these attributes:
- Read-only (RO)—Gives read access to authorized management stations to all objects in the MIB except the community strings, but does not allow write access
- Read-write (RW)—Gives read and write access to authorized management stations to all objects in the MIB, but does not allow access to the community strings
- When a cluster is created, the command switch manages the exchange of messages among member switches and the SNMP application. The Network Assistant software appends the member switch number ( @esN , where N is the switch number) to the first configured RW and RO community strings on the command switch and propagates them to the member switches. For more information, see Chapter 6, “Clustering Switches” and see Getting Started with Cisco Network Assistant , available on Cisco.com.
Using SNMP to Access MIB Variables
An example of an NMS is the CiscoWorks network management software. CiscoWorks 2000 software uses the switch MIB variables to set device variables and to poll devices on the network for specific information. The results of a poll can be displayed as a graph and analyzed to troubleshoot internetworking problems, increase network performance, verify the configuration of devices, monitor traffic loads, and more.
As shown in Figure 36-1, the SNMP agent gathers data from the MIB. The agent can send traps, or notification of certain events, to the SNMP manager, which receives and processes the traps. Traps alert the SNMP manager to a condition on the network such as improper user authentication, restarts, link status (up or down), MAC address tracking, and so forth. The SNMP agent also responds to MIB-related queries sent by the SNMP manager in get-request , get-next-request , and set-request format.
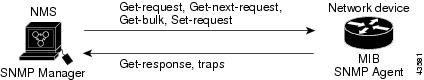
SNMP Notifications
SNMP allows the switch to send notifications to SNMP managers when particular events occur. SNMP notifications can be sent as traps or inform requests. In command syntax, unless there is an option in the command to select either traps or informs, the keyword traps refers to either traps or informs, or both. Use the snmp-server host command to specify whether to send SNMP notifications as traps or informs.

Note SNMPv1 does not support informs.
Traps are unreliable because the receiver does not send an acknowledgment when it receives a trap, and the sender cannot determine if the trap was received. When an SNMP manager receives an inform request, it acknowledges the message with an SNMP response protocol data unit (PDU). If the sender does not receive a response, the inform request can be sent again. Because they can be re-sent, informs are more likely than traps to reach their intended destination.
The characteristics that make informs more reliable than traps also consume more resources in the switch and in the network. Unlike a trap, which is discarded as soon as it is sent, an inform request is held in memory until a response is received or the request times out. Traps are sent only once, but an inform might be re-sent or retried several times. The retries increase traffic and contribute to a higher overhead on the network. Therefore, traps and informs require a trade-off between reliability and resources. If it is important that the SNMP manager receive every notification, use inform requests. If traffic on the network or memory in the switch is a concern and notification is not required, use traps.
SNMP ifIndex MIB Object Values
In an NMS, the IF-MIB generates and assigns an interface index (ifIndex) object value that is a unique number greater than zero to identify a physical or a logical interface. When the switch reboots or the switch software is upgraded, the switch uses this same value for the interface. For example, if the switch assigns a port 2 an ifIndex value of 10003, this value is the same after the switch reboots.
The switch uses one of the values in Table 36-3 to assign an ifIndex value to an interface:

Note The switch might not use sequential values within a range.
SNMP Support for DOM MIB
The Digital Optical Monitoring (DOM) MIB for SFP optical transceivers allows you to monitor real-time operating parameters. Each DOM-capable optical transceiver has five sensors that are configured to monitor operational parameters such as temperature, voltage, laser bias current, and optical Tx and Rx power on a specific interface.
Each sensor has four thresholds: high alarm, high warning, low warning, and low alarm. The DOM MIB, with the support of an SNMP agent, reads the sensor data and evaluates each threshold for every 10 minutes and sends a trap only when the sensor value violates the default threshold value. The trap is sent every 10 minutes until the sensor value is within the acceptable range.
For each sensor, an entry exists in the entPhysicalTable (ENTITY-MIB). These entries are created when an SFP is inserted in the switch. For each sensor-operating parameter placed in the entPhysicalTable, one entry is created in the entSensorValueTable in the CISCO-ENTITY-SENSOR-MIB. The CISCO-ENTIY-SENSOR-MIB provides information on a set of managed objects representing physical entities in the entPhysicalTable with entPhysicalClass set to sensor.
- Support for SFP optical interfaces
- Inline power measurement capability at installation
- Layer1 status information to support network monitoring
- Ability to enable dedicated Layer 1 fault analysis
The real-time DOM parameters can be monitored using the command line interface (CLI) or SNMP interface.

Note This feature is only available when a DOM-capable transceiver is present and configured for monitoring. The frequency at which the sensor information is refreshed depends on default values configured in the transceiver SEEPROM.
Use the show interfaces transceivers privileged EXEC command to display the physical properties of a small form-factor pluggable (SFP) module interface. The calibration properties includes high and low numbers and any alarm and warning threshold information for Digital Optical Monitoring(DoM)-capable transceiver installed in the switch.
This example shows the interface operating status against the threshold values.
Configuring SNMP
- Default SNMP Configuration
- SNMP Configuration Guidelines
- Disabling the SNMP Agent
- Configuring Community Strings
- Configuring SNMP Groups and Users
- Configuring SNMP Notifications
- Setting the CPU Threshold Notification Types and Values
- Setting the Agent Contact and Location Information
- Limiting TFTP Servers Used Through SNMP
- SNMP Examples
Default SNMP Configuration
Table 36-4 shows the default SNMP configuration.
Disabled3. |
|
If no keyword is entered, the default is the noauth (noAuthNoPriv) security level. |
|
|
3.This is the default when the switch starts and the startup configuration does not have any snmp-server global configuration commands. |
SNMP Configuration Guidelines
If the switch starts and the switch startup configuration has at least one snmp-server global configuration command, the SNMP agent is enabled.
An SNMP group is a table that maps SNMP users to SNMP views. An SNMP user is a member of an SNMP group. An SNMP host is the recipient of an SNMP trap operation. An SNMP engine ID is a name for the local or remote SNMP engine.
When configuring SNMP, follow these guidelines:
- When configuring an SNMP group, do not specify a notify view. The snmp-server host global configuration command autogenerates a notify view for the user and then adds it to the group associated with that user. Modifying the group's notify view affects all users associated with that group. See the Cisco IOS Network Management Command Reference for information about when you should configure notify views.
- To configure a remote user, specify the IP address or port number for the remote SNMP agent of the device where the user resides.
- Before you configure remote users for a particular agent, configure the SNMP engine ID, using the snmp-server engineID global configuration with the remote option. The remote agent's SNMP engine ID and user password are used to compute the authentication and privacy digests. If you do not configure the remote engine ID first, the configuration command fails.
- When configuring SNMP informs, you need to configure the SNMP engine ID for the remote agent in the SNMP database before you can send proxy requests or informs to it.
- If a local user is not associated with a remote host, the switch does not send informs for the auth (authNoPriv) and the priv (authPriv) authentication levels.
- Changing the value of the SNMP engine ID has important side effects. A user's password (entered on the command line) is converted to an MD5 or SHA security digest based on the password and the local engine ID. The command-line password is then destroyed, as required by RFC 2274. Because of this deletion, if the value of the engine ID changes, the security digests of SNMPv3 users become invalid, and you need to reconfigure SNMP users by using the snmp-server user username global configuration command. Similar restrictions require the reconfiguration of community strings when the engine ID changes.
Disabling the SNMP Agent
Beginning in privileged EXEC mode, follow these steps to disable the SNMP agent:
The
no snmp-server
global configuration command disables all running versions (Version 1,
Version 2C, and Version 3) on the device. No specific Cisco IOS command exists to enable SNMP. The first
snmp-server
global configuration command that you enter enables all versions of SNMP.
Configuring Community Strings
You use the SNMP community string to define the relationship between the SNMP manager and the agent. The community string acts like a password to permit access to the agent on the switch. Optionally, you can specify one or more of these characteristics associated with the string:
- An access list of IP addresses of the SNMP managers that are permitted to use the community string to gain access to the agent
- A MIB view, which defines the subset of all MIB objects accessible to the given community
- Read and write or read-only permission for the MIB objects accessible to the community
Beginning in privileged EXEC mode, follow these steps to configure a community string on the switch:

Note To disable access for an SNMP community, set the community string for that community to the null string (do not enter a value for the community string).
To remove a specific community string, use the no snmp-server community string global configuration command.
This example shows how to assign the string comaccess to SNMP, to allow read-only access, and to specify that IP access list 4 can use the community string to gain access to the switch SNMP agent:
Configuring SNMP Groups and Users
You can specify an identification name (engine ID) for the local or remote SNMP server engine on the switch. You can configure an SNMP server group that maps SNMP users to SNMP views, and you can add new users to the SNMP group.
Beginning in privileged EXEC mode, follow these steps to configure SNMP on the switch:
Configuring SNMP Notifications
A trap manager is a management station that receives and processes traps. Traps are system alerts that the switch generates when certain events occur. By default, no trap manager is defined, and no traps are sent. Switches running this Cisco IOS release can have an unlimited number of trap managers.

Note Many commands use the word traps in the command syntax. Unless there is an option in the command to select either traps or informs, the keyword traps refers to traps, informs, or both. Use the snmp-server host global configuration command to specify whether to send SNMP notifications as traps or informs.
Table 36-5 describes the supported switch traps (notification types). You can enable any or all of these traps and configure a trap manager to receive them. To enable the sending of SNMP inform notifications, use the snmp-server enable traps global configuration command combined with the snmp-server host host-addr informs global configuration command .

Note Though visible in the command-line help strings, the fru-ctrl, insertion, and removal keywords are not supported.
You can use the snmp-server host global configuration command to a specific host to receive the notification types listed in Table 36-5 .
Beginning in privileged EXEC mode, follow these steps to configure the switch to send traps or informs to a host:
snmp-server user username groupname { remote host [ udp-port port ]} { v1 [ access access-list ] | v2c [ access access-list ] | v3 [ encrypted ] [ access access-list ] [ auth { md5 | sha } auth-password ]} |
Configure an SNMP user to be associated with the remote host created in Step 2. Note You cannot configure a remote user for an address without first configuring the engine ID for the remote host. Otherwise, you receive an error message, and the command is not executed. |
|
snmp-server group groupname { v1 | v2c | v3 { auth | noauth | priv } } [ read readview ] [ write writeview ] [ notify notifyview ] [ access access-list ] |
||
snmp-server host
host-addr
|
Specify the recipient of an SNMP trap operation.
Note The priv keyword is available only when the cryptographic software image is installed.
Note The @ symbol is used for delimiting the context information. Avoid using the @ symbol as part of the SNMP community string when configuring this command.
|
|
Enable the switch to send traps or informs and specify the type of notifications to be sent. For a list of notification types, see Table 36-5, or enter snmp-server enable traps ? To enable multiple types of traps, you must enter a separate snmp-server enable traps command for each trap type. Note When you configure a trap by using the notification type port-security, configure the port security trap first, and then configure the port security trap rate: |
||
(Optional) Specify the source interface, which provides the IP address for the trap message. This command also sets the source IP address for informs. |
||
(Optional) Establish the message queue length for each trap host. The range is 1 to 1000; the default is 10. |
||
(Optional) Define how often to resend trap messages. The range is 1 to 1000; the default is 30 seconds. |
||
|
Note To display SNMPv3 information about auth | noauth | priv mode configuration, you must enter the show snmp user privileged EXEC command. |
||
The snmp-server host command specifies which hosts receive the notifications. The snmp-server enable trap command globally enables the mechanism for the specified notification (for traps and informs). To enable a host to receive an inform, you must configure an snmp-server host informs command for the host and globally enable informs by using the snmp-server enable traps command.
To remove the specified host from receiving traps, use the no snmp-server host host global configuration command. The no snmp-server host command with no keywords disables traps, but not informs, to the host. To disable informs, use the no snmp-server host informs global configuration command. To disable a specific trap type, use the no snmp-server enable traps notification-types global configuration command.
Setting the CPU Threshold Notification Types and Values
Beginning in privileged EXEC mode, follow these steps to set the CPU threshold notification types and values:
Setting the Agent Contact and Location Information
Beginning in privileged EXEC mode, follow these steps to set the system contact and location of the SNMP agent so that these descriptions can be accessed through the configuration file:
Limiting TFTP Servers Used Through SNMP
Beginning in privileged EXEC mode, follow these steps to limit the TFTP servers used for saving and loading configuration files through SNMP to the servers specified in an access list:
SNMP Examples
This example shows how to enable all versions of SNMP. The configuration permits any SNMP manager to access all objects with read-only permissions using the community string public . This configuration does not cause the switch to send any traps.
This example shows how to permit any SNMP manager to access all objects with read-only permission using the community string public . The switch also sends VTP traps to the hosts 192.180.1.111 and 192.180.1.33 using SNMPv1 and to the host 192.180.1.27 using SNMPv2C. The community string public is sent with the traps.
This example shows how to allow read-only access for all objects to members of access list 4 that use the comaccess community string. No other SNMP managers have access to any objects. SNMP Authentication Failure traps are sent by SNMPv2C to the host cisco.com using the community string public .
This example shows how to send Entity MIB traps to the host cisco.com . The community string is restricted. The first line enables the switch to send Entity MIB traps in addition to any traps previously enabled. The second line specifies the destination of these traps and overwrites any previous snmp-server host commands for the host cisco.com .
This example shows how to enable the switch to send all traps to the host myhost.cisco.com using the community string public :
This example shows how to associate a user with a remote host and to send auth (authNoPriv) authentication-level informs when the user enters global configuration mode:
Displaying SNMP Status
To display SNMP input and output statistics, including the number of illegal community string entries, errors, and requested variables, use the show snmp privileged EXEC command. You also can use the other privileged EXEC commands in Table 36-6 to display SNMP information. For information about the fields in the displays, see the Cisco IOS Configuration Fundamentals Command Reference.
 Feedback
Feedback