Autonomic Networking
Autonomic networking makes network devices intelligent by introducing self-management concepts that simplify network management for network operators.
Prerequisites for Autonomic Networking
- The Autonomic Networking Infrastructure feature supports only Ethernet ports and IPv6 addresses.
- All interfaces are up by default to exchange adjacency discovery messages if there is no startup configuration in the corresponding device.
- The Autonomic Control Plane is automatically built between two adjacent devices supporting the autonomic networking infrastructure. The Ethernet interfaces on both devices need to be up, and the device should either be unconfigured (greenfield rollout) or have autonomic networking configured explicitly.
- The Autonomic Control Plane can also be automatically built between two adjacent devices if there is an intervening nonautonomic layer 2 cloud such as a Metro ethernet service. This is achieved by the Channel Discovery protocol on the autonomic devices. This protocol probes for working VLAN encapsulations.
- To build the ACP across intervening nonautonomic L3 devices, you should explicitly configure a tunnel between the autonomic devices and enable autonomic adjacency discovery on this tunnel.
- Autonomic Registrar, commonly known as registrar, is required for the Autonomic Networking Infrastructure feature to work. At least one device in the network must be configured as a registrar to enroll new devices into the autonomic domain.
- In a network where all the required devices are already enrolled into the autonomic domain, a registrar is not required.
- Each registrar supports only one autonomic domain. The registrar is needed only when new autonomic devices join the domain.
- To contact the registrar for enrolment to the autonomic domain, all new devices must have L2 reachability to at least one device that is already enrolled to the domain. If there is no L2 reachability, user needs to configure the tunnel between the devices and configure autonomic adjacency discovery on them.
- A device can be enrolled only into one autonomic domain. Two devices enrolled into different domains will not build the autonomic control plane between each other.
- Autonomic intent can be configured only on the registrar and from there it is propagated to all the devices in the domain.
- For Zero Touch Bootstrap to take place, there must be no startup-config file present and the config-register must remain default which is 0x2102.
Restrictions for Autonomic Networking
-
Autonomic networking supports only unique device identifier (UDI) -based devices.
-
Autonomic networking and Zero Touch Provisioning (ZTP) are different zero touch solutions. We recommended that you do not test or use autonomic networking and ZTP at the same time.
-
All the devices in an autonomic network should be contiguously autonomic. If there is no continuity, manual configuration is required to configure a tunnel through a nonautonomic network.
-
In Cisco IOS XE Denali 16.3.1 Release, Cisco Catalyst 3850 and Cisco Catalyst 3650 switches support only untagged probes and channel.
-
Devices running Cisco IOS XE Denali 16.3.x Release and later are not compatible with devices running releases earlier than IOS XE 3.18 or 15.6(01)T. To facilitate interwork between these devices, autonomic adjacency discovery should be configured on the interfaces.
-
When autonomic networking is enabled, you must not disable IPv6 unicast routing manually.
-
The autonomic Registrar functionality is not supported in Cisco Catalyst 3850 and Cisco Catalyst 3650 switches.
Information About Autonomic Networking
Overview of Autonomic Networking
The aim of autonomic networking is to create self-managing networks to overcome the rapidly growing complexity of the Internet and other networks to enable them to grow further. In a self-managing autonomic system, network management takes on a new role where, instead of controlling the network elements individually and directly, the administrator can define network-wide policies and rules to guide the self-management process.
The following figure provides a high-level architecture of an autonomic network.
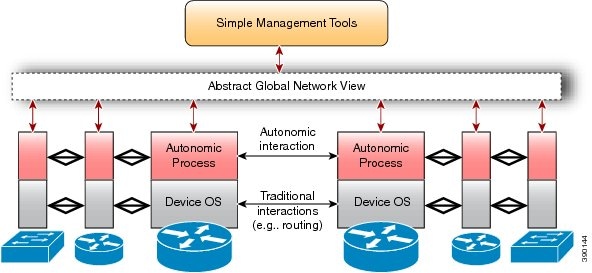
Autonomic networking is controlled by a separate software entity running on top of traditional operating systems that include networking components, such as IP, Open Shortest Path First (OSPF), and so forth. Traditional networking components are unchanged and unaware of the presence of the autonomic process. The autonomic components use normal interfaces that are exposed by the traditional networking components and interact with different devices in the network. The autonomic components securely cooperate to add more intelligence to devices so that the devices in an autonomic network can autonomically configure, manage, protect, and heal themselves with minimal operator intervention. They can also securely consolidate their operations to present a simplified and abstracted view of the network to the operator.
Autonomic Networking Infrastructure
The Autonomic Networking Infrastructure feature simplifies the network bootstrap functionality by removing the need for any kind of prestaging, thereby allowing devices to join a domain securely, after which devices can be configured. The goal of the Autonomic Networking Infrastructure feature is to make new and unconfigured devices reachable by an operator or network management system, securely. This is carried as described here:
- A device is defined and configured as the registrar. This registrar is the first autonomic domain device.
- This step is optional. The network administrator collects a list of legitimate device identifiers of the devices to be added to the network. This list controls the devices that are added to the autonomic domain. Devices are identified by their unique device identifier (UDI). The list is compiled as a simple text file, one UDI per line. This step is optional because, in the absence of a whitelist, all the devices are allowed to join the domain. A whitelist is an approved list of entities that is provided a particular privilege, service, mobility, access, or recognition. Whitelisting means to grant access.
- (Optional) The whitelist of known devices is uploaded to the registrar as part of its configuration.
- Any new autonomic device that is directly connected to the registrar, or another enrolled domain device, will automatically receive a domain certificate from the registrar.
- The autonomic control plane is automatically established across the autonomic domain to make new devices reachable.
The benefits of Autonomic Networking Infrastructure are as follows:
- Autonomic discovery of Layer 2 topology and connectivity by discovering how to reach autonomic neighbors.
- Secure and zero touch identity of new devices by using the device name and domain certificate.
- A virtual autonomic control plane that enables communications between autonomic nodes.
Autonomic behavior is enabled by default on new devices. To enable autonomic behavior on existing devices, use the autonomic command. To disable, use the no form of this command.
The components of autonomic networking are as follows:
- Registrar—A domain-specific registration authority in a given enterprise that validates new devices in the domain, provides them with domain-wide credentials, and makes policy decisions. Policy decisions can include a decision on whether a new device can join a given domain based on a preloaded whitelist. The registrar also has a database of devices that join a given domain and the device details.
- Channel Discovery—Used to discover reachability between autonomic nodes across nonautonomic Layer 2 networks.
- Adjacency Discovery—Used to discover autonomic neighbors. Adjacency discovery is performed on Layer 3. It is also possible to discover autonomic neighbors across pre-established Layer 3 Generic Routed Encapsulation (GRE) tunnels.
New Device Joining the Autonomic Network
The following figure illustrates how a new device joins an autonomic network.
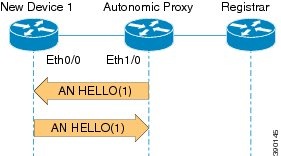
- The new device sends out a hello message to the neighbor. In this case, the neighbor is part of an autonomic network domain.
- The hello message includes the unique device identifier (UDI) of the new device.
- The autonomic device acts as a proxy and allows the new device to join this autonomic network domain. The autonomic network device advertises itself with the domain information to its Layer 3 neighbors.
- On receiving the autonomic network hello message from the neighbor and detecting the UDI information, the new device is validated with the autonomic registrar.
- The new device advertises its domain certificate in its hello message with all neighbors. The neighbor information is exchanged every 10 seconds.
 Note |
If the neighbor information changes, the entry is deleted and neighbor discovery is restarted. In the absence of a domain certificate and devices working with UDI, UDI is exchanged at a 10-second interval. |
Channel Discovery in Autonomic Networking
Channel Discovery occurs automatically on all the interfaces when Autonomic Networking is enabled on the device. Note that autonomic Networking is enabled by default on devices with no configuration (greenfield devices, and assuming they have AN functionality), but will be passive. They will only be able to receive and answer CD probes, which are L2 frames. Only a device with domain certificate or one that is already enrolled to a domain can send out CD probes on all of its Ethernet interfaces that are up. As a result of this, neighbors will be dynamically discovered. The probing will continue over time, so that newly added neighbors are discovered over time.
Adjacency Discovery in Autonomic Networking
After a channel is established, the proxy will send ND Hello messages to the new device, that is the one that is already enrolled in the domain and can act as a proxy for a new device joining the domain. The new device will send AN Hello messages in response back to the proxy. The Hello messages consist of an identification for the new device (UDI). On receiving AN Hello messages from the new device and detecting the UDI information, the AN proxy will send the details to the Autonomic Networking Registrar (ANR) for validating this new device.
Service Discovery in Autonomic Networking
Autonomic networking uses the multicast Domain Name System (mDNS) infrastructure to locate the various services required by the devices in the autonomic networking domain. A few of the services discovered by the network using the mDNS infrastructure are the AAA server, the configuration server, the syslog server, and the autonomic networking registrar. Autonomic networking listens to the mDNS advertisements on all the devices in the domain. From the devices hosting the services, autonomic networking initiates the mDNS advertisements.
Autonomic Control Plane
When a new device in the domain receives a domain certificate, it exchanges the domain certificate in the Hello messages with its neighbors. This creates an autonomic control plane between two autonomic devices of the same domain. There are different types of autonomic control planes that can be created based on the different capabilities of the devices. The autonomic control plane is established by using the following mechanisms:
- Configuring a loopback interface.
- Dynamically assigning an IPv6 address to the loopback interface.
- Configuring autonomic VPN routing and forwarding (VRF).
How to Configure Autonomic Networking
Configuring the Registrar
Procedure
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 |
enable Example: |
|
||
| Step 2 |
configure terminal Example: |
Enters global configuration mode. |
||
| Step 3 |
autonomic Example: |
Enables autonomic networking. |
||
| Step 4 |
autonomic registrar Example: |
Enables a device as a registrar and enters registrar configuration mode.
|
||
| Step 5 |
domain-id domain-name Example: |
|
||
| Step 6 |
device-accept udi Example: |
|
||
| Step 7 |
whitelist filename Example: |
|
||
| Step 8 |
no shut Example: |
|
||
| Step 9 |
exit Example: |
|
||
| Step 10 |
exit Example: |
|
Verifying and Monitoring Autonomic Networking Configuration
Procedure
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable Example: |
|
| Step 2 |
show autonomic device Example: |
|
| Step 3 |
show autonomic neighbors [detail] Example: |
|
| Step 4 |
show autonomic control-plane [detail] Example: |
|
| Step 5 |
show autonomic l2-channels [detail] Example: |
|
| Step 6 |
show autonomic interfaces Example: |
|
| Step 7 |
debug autonomic {Bootstrap | Channel-Discovery | Infra | Intent | Neighbor-Discovery | Registrar | Services } {aaa | all | ntp | events | packets} {info | moderate | severe} |
|
| Step 8 |
clear autonomic {device | neighbor UDI | registrar accepted-device device UDI} |
|
 Feedback
Feedback