- Preface
- Overview
- Installing the Cisco VSG and the Cisco VNMC-Quick Start
- Installing Cisco VNMC
- Installing the Cisco VSG
- Registering Devices With the Cisco VNMC
- Installing the Cisco VSG on a Cisco Cloud Services Platform Virtual Services Appliance
- Upgrading the Cisco VSG and the Cisco VNMC
- Examples of Cisco VNMC OVA Template Deployment and Cisco VNMC ISO Installations
- Index
Installing the Cisco VSG and the Cisco VNMC-Quick Start
This chapter contains the following sections:
- Information About Installing the Cisco VNMC and the Cisco VSG
- Task 1: Installing the Cisco VNMC from an OVA Template
- Task 2: On the Cisco VNMC, Setting Up VM-Mgr for vCenter Connectivity
- Task 3: On the VSM, Configuring the Cisco VNMC Policy Agent
- Task 4: On the VSM, Preparing Cisco VSG Port Profiles
- Task 5: Installing the Cisco VSG from an OVA Template
- Task 6: On the Cisco VSG and Cisco VNMC, Verifying the VNM Policy-Agent Status
- Task 7: On the Cisco VNMC, Configuring a Tenant, Security Profile, and Compute Firewall
- Task 8: On the Cisco VNMC, Assigning the Cisco VSG to the Compute Firewall
- Task 9: On the Cisco VNMC, Configuring a Permit-All Rule
- Task 10: On the Cisco VSG, Verifying the Permit-All Rule
- Task 11: Enabling Logging
- Task12: Enabling the Traffic VM Port-Profile for Firewall Protection and Verifying the Communication Between the VSM, VEM, and VSG
- Task13: Sending Traffic Flow and on the Cisco VSG Verifying Statistics and Logs
Information About Installing the Cisco VNMC and the Cisco VSG
This chapter describes how to install and set up a basic working configuration of the Cisco VNMC and Cisco VSG. The example in this chapter uses the OVF template method to install the OVA files of the software. The steps assume that the Cisco Nexus 1000V Series switch is operational, and endpoint VMs are already installed.
Cisco VSG and Cisco VNMC Installation Planning Checklists
Planning the arrangement and architecture of your network and equipment is essential for a successful operation of the Cisco VNMC and Cisco VSG.
- Basic Hardware and Software Requirements
- VLAN Configuration Requirements
- Required Cisco VNMC and Cisco VSG Information
- Tasks and Prerequisites Checklist
- Host Requirements
- Obtaining the Cisco VNMC and the Cisco VSG Software
Basic Hardware and Software Requirements
The following table lists the basic hardware and software requirements for Cisco VSG and Cisco VNMC installation.
- x86 Intel or AMD server with 64-bit processor listed in the VMware compatibility matrix
- Intel VT enabled in the BIOS
- VMware ESX 4.1, 5.0, or 5.1
- ESX or ESXi platform that runs VMware software release 4.1. or 5.0 with a minimum of 4-GB physical RAM for the Cisco VSG and similar for the Cisco VNMC or 6 GB for both.
- VMware vSphere Hypervisor
- VMware vCenter 5.0 (4.1 VMware supports only 4.1 host)
- 1 processor
- CPU speed of 1.5 Ghz
- Datastore with at least 25-GB disk space available on shared NFS/SAN storage when the Cisco VNMC is deployed in an HA cluster
- Internet Explorer 8.0 or Mozilla Firefox 3.6.x on Windows
- Flash 10.0 or 10.1
- Cisco VSG software available for download at http://www.cisco.com/en/US/products/ps13095/index.html
- Cisco VNMC software available for download at http://www.cisco.com/en/US/products/ps11213/index.html
VLAN Configuration Requirements
Follow these VLAN requirements top prepare the Cisco Nexus 1000V Series switch for further installation processes:
- You must have two VLANs that are configured on the Cisco Nexus 1000V Series switch uplink ports: the service VLAN and an HA VLAN (the VLAN does not need to be the system VLAN).
- You must have two port profiles that are configured on the Cisco Nexus 1000V Series switch: one port profile for the service VLAN and one port profile for the HA VLAN (you will be configuring the Cisco VSG IP address on the Cisco VSG so that the Cisco Nexus 1000V Series switch can communicate with it)
Required Cisco VNMC and Cisco VSG Information
The following information can be used later during the Cisco VNMC and Cisco VSG installation.
| Type | Your Information | ||
|---|---|---|---|
Cisco VSG name—Unique within the inventory folder and up to 80 characters |
|||
Hostname—Where the Cisco VSG will be installed in the inventory folder |
|||
Datastore name—Where the VM files will be stored |
|||
Cisco VSG management IP address |
|||
VSM management IP address |
|||
Cisco VNMC instance IP address |
|||
Mode for installing the Cisco VSG |
|||
Cisco VSG VLAN number |
|||
Cisco VSG port profile name
|
|||
HA pair ID (HA domain ID) |
|||
Cisco VSG admin password |
|||
Cisco VNMC admin password |
|||
Cisco VSM admin password |
|||
Shared secret password (Cisco VNMC, Cisco VSG policy agent, Cisco VSM policy agent) |
Tasks and Prerequisites Checklist
Tasks |
Prerequisites | ||||
|---|---|---|---|---|---|
| Task 1: Installing the Cisco VNMC from an OVA Template |
|
||||
| Task 2: On the Cisco VNMC, Setting Up VM-Mgr for vCenter Connectivity |
|
||||
| Task 3: On the VSM, Configuring the Cisco VNMC Policy Agent |
|
||||
| Task 4: On the VSM, Preparing Cisco VSG Port Profiles |
|
||||
| Task 5: Installing the Cisco VSG from an OVA Template |
|
||||
| Task 6: On the Cisco VSG and Cisco VNMC, Verifying the VNM Policy-Agent Status | — | ||||
| Task 7: On the Cisco VNMC, Configuring a Tenant, Security Profile, and Compute Firewall |
|
||||
| Task 8: On the Cisco VNMC, Assigning the Cisco VSG to the Compute Firewall | — | ||||
| Task 9: On the Cisco VNMC, Configuring a Permit-All Rule | — | ||||
| Task 10: On the Cisco VSG, Verifying the Permit-All Rule | — | ||||
| Task 11: Enabling Logging | — | ||||
| Task12: Enabling the Traffic VM Port-Profile for Firewall Protection and Verifying the Communication Between the VSM, VEM, and VSG |
|
||||
| Task13: Sending Traffic Flow and on the Cisco VSG Verifying Statistics and Logs | — |
Host Requirements
Obtaining the Cisco VNMC and the Cisco VSG Software
The Cisco VSG software is available for download at the following URL:
http://www.cisco.com/en/US/products/ps13095/index.htmlThe Cisco VNMC software is available for download at the following URL:
http://www.cisco.com/en/US/products/ps11213/index.htmlTask 1: Installing the Cisco VNMC from an OVA Template
Know the following:
- The Cisco VNMC OVA image is available in the vCenter.
- Know the IP/subnet mask/gateway information for the Cisco VNMC.
- Know the admin password, shared_secret, hostname that you want to use.
- Know the DNS server and domain name information.
-
Know the management port-profile name for the Virtual Machine (VM) (management).

Note
The management port profile is the same port profile that is used for the Virtual Supervisor Module (VSM). The port profile is configured in the VSM and is used for the Cisco VNMC management interface.
- The host has 2-GB RAM and 25-GB available hard-disk space.
- A shared secret password is available (this password enables communication between the Cisco VNMC, VSM, and Cisco VSG).
1. Choose the host on which to deploy the Cisco VNMC VM.
2. Choose .
3. In the Source window, do the following:
4. In the OVF Template Details window, review the details of the Cisco VNMC template and click Next.
5. In the End User License Agreement window, do the following:
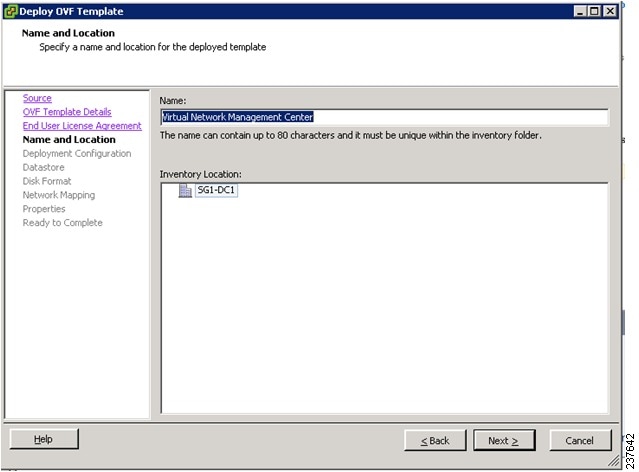
6. In the Name and Location window, do the following:
7. In the Deployment Configuration window, do the following:
8. In the Datastore window, choose the datastore for the VM and click Next.
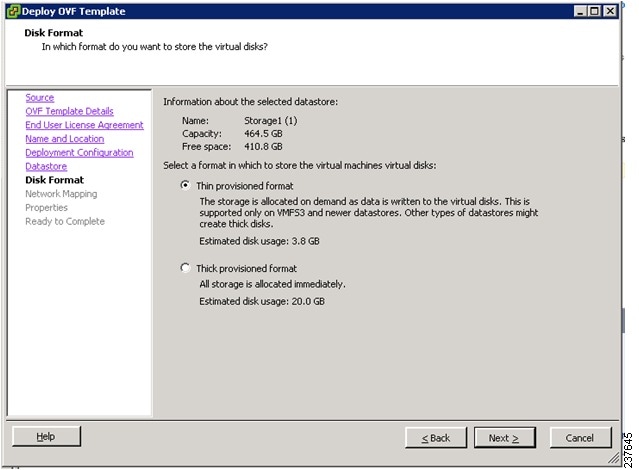
9. In the Disk Format window, do the following:
10. In the Network Mapping window, do the following:
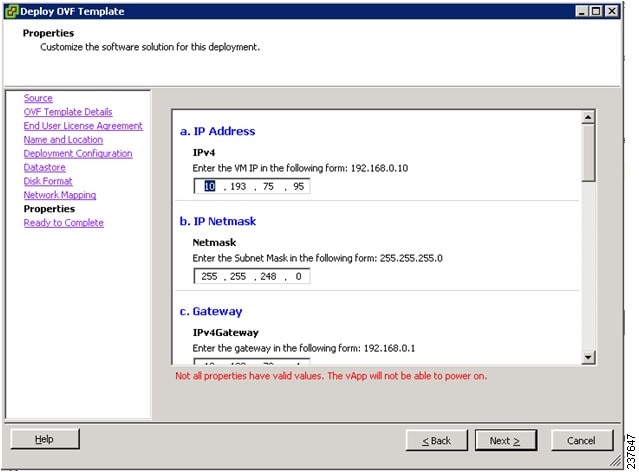
11. In the Properties window, do the following:
12. Click Next.
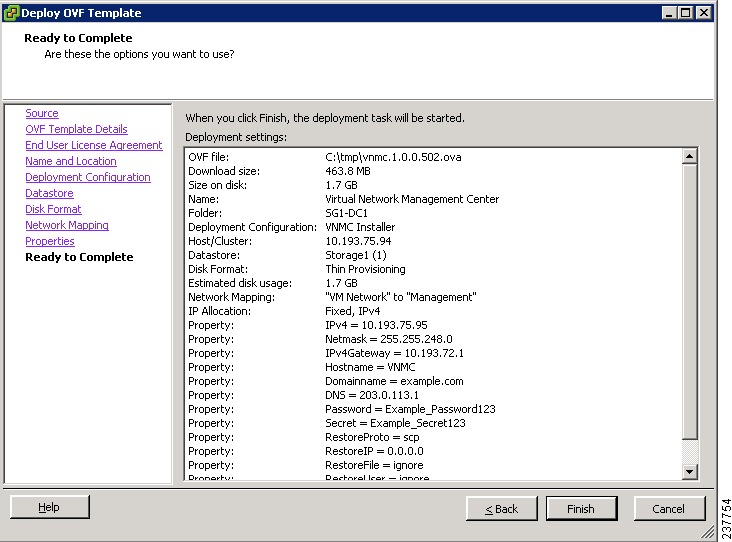
13. In the Ready to Complete window, review the deployment settings information and click Finish.
14. Click Close.
15. Power on the Cisco VSG VM.
DETAILED STEPS
Task 2: On the Cisco VNMC, Setting Up VM-Mgr for vCenter Connectivity
Perform the following tasks in the same order as listed below to set up the VM-manager for vCenter connectivity:
- Downloading the vCenter Extension File from the Cisco VNMC
- Registering the vCenter Extension Plugin in the vCenter
- Configuring the vCenter in VM-Manager in the Cisco VNMC
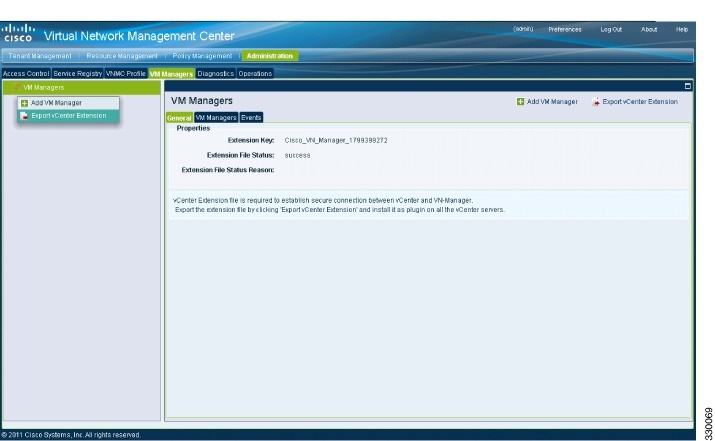
Downloading the vCenter Extension File from the Cisco VNMC
Make sure that you know the following:
1. To access the Cisco VNMC from your client machine, open Internet Explorer and access https://vnmc-ip/ (https://xxx.xxx.xxx.xxx).
2. In the Website Security Certificate window, choose Continue to this website.
3. In the Cisco VNMC Access window, do the following:
4. In the VNMC Main window, choose
5. In the Cisco Virtual Network Management Center VM Managers window, do the following:
DETAILED STEPS
| Step 1 |
To access the Cisco VNMC from your client machine, open Internet Explorer and access https://vnmc-ip/ (https://xxx.xxx.xxx.xxx). The Website Security Certificate window opens. |
| Step 2 | In the Website Security Certificate window, choose Continue to this website. |
| Step 3 |
In the Cisco VNMC Access window, do the following:
|
| Step 4 |
In the VNMC Main window, choose The VM Managers window opens. |
| Step 5 | In the Cisco Virtual Network Management Center VM Managers window, do the following: |
What to Do Next
Go to Registering the vCenter Extension Plugin in the vCenter.
Registering the vCenter Extension Plugin in the vCenter
This task is completed within your client desktop vSphere client directory
See Downloading the vCenter Extension File from the Cisco VNMC.
1. From vSphere client, log in to vCenter.
2. In the Vsphere Client window, choose .
3. Right-click in an empty space, and choose New Plug-in from the drop-down list.
4. In the Register Plug-in window, do the following:
5. On the Register Plug-in progress indicator, click OK after the successful registration message appears.
6. Click Close.
DETAILED STEPS
| Step 1 |
From vSphere client, log in to vCenter.
The vSphere Client Directory window opens. |
| Step 2 | In the Vsphere Client window, choose . |
| Step 3 |
Right-click in an empty space, and choose New Plug-in from the drop-down list. The Register Plug-in window that contains the vSphere client and vCenter directory for managing plug-ins opens. 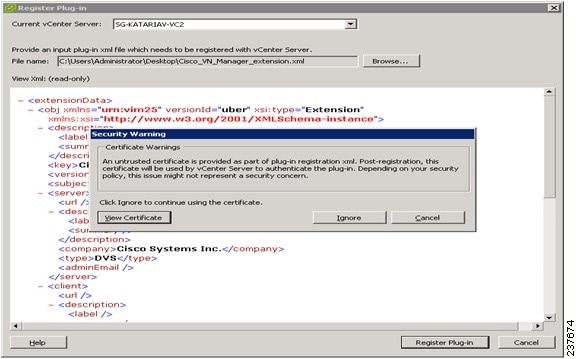
|
| Step 4 | In the Register Plug-in window, do the following: |
| Step 5 | On the Register Plug-in progress indicator, click OK after the successful registration message appears. |
| Step 6 | Click Close. |
What to Do Next
Go to Configuring the vCenter in VM-Manager in the Cisco VNMC.
Configuring the vCenter in VM-Manager in the Cisco VNMC
See Task 2: On the Cisco VNMC, Setting Up VM-Mgr for vCenter Connectivity.
1. Go to the Cisco VNMC and click .
2. In the Cisco Virtual Network Management Center window, click the VM Manager tab.
3. In the left pane, choose .
4. In the Add VM Manager dialog box do the following:
5. Click OK.
DETAILED STEPS
| Step 1 | Go to the Cisco VNMC and click . | ||
| Step 2 | In the Cisco Virtual Network Management Center window, click the VM Manager tab. | ||
| Step 3 | In the left pane, choose . | ||
| Step 4 | In the Add VM Manager dialog box do the following: | ||
| Step 5 |
Click OK.
|
Task 3: On the VSM, Configuring the Cisco VNMC Policy Agent
Once the Cisco VNMC is installed, you must register the VSM with the Cisco VNMC policy.
Make sure that you know the following:
-
The Cisco VNMC policy-agent image is available on the VSM (for example, vnmc-vsmpa.2.1.1b.bin)

Note
The string vsmpa must appear in the image name as highlighted.
- The IP address of the Cisco VNMC
- The shared secret password you defined during the Cisco VNMC installation
-
That IP connectivity between the VSM and the Cisco VNMC is working

Note
If you upgrade your VSM, you must also copy the latest Cisco VSM policy agent image. This image is available in the Cisco VNMC image bundle to boot from a flash drive and to complete registration with the Cisco VNMC.
1. On the VSM, enter the following commands:
2. Check the status of the VNM policy agent configuration to verify that you have installed the Cisco VNMC correctly and it is reachable by entering the show vnm-pa status command. This example shows that the Cisco VNMC is reachable and the installation is correct:
DETAILED STEPS
| Step 1 |
On the VSM, enter the following commands: vsm# configure terminal vsm(config)# vnm-policy-agent vsm(config-vnm-policy-agent)# registration-ip 10.193.75.95 vsm(config-vnm-policy-agent)# shared-secret Example_Secret123 vsm(config-vnm-policy-agent)# policy-agent-image vnmc-vsmpa.2.1.1b.bin vsm(config-vnm-policy-agent)# exit vsm(config)# copy running-config startup-config vsm(config)# exit |
| Step 2 |
Check the status of the VNM policy agent configuration to verify that you have installed the Cisco VNMC correctly and it is reachable by entering the show vnm-pa status command. This example shows that the Cisco VNMC is reachable and the installation is correct: vsm# show vnm-pa status VNM Policy-Agent status is - Installed Successfully. Version 2.1(1b)-vsm vsm The VSM is now registered with the Cisco VNMC. |
This example shows that the Cisco VNMC is unreachable or an incorrect IP is configured:
vsm# show vnm-pa status VNM Policy-Agent status is - Installation Failure VNMC not reachable. vsm#
This example shows that the VNM policy-agent is not configured or installed:
vsm# show vnm-pa status VNM Policy-Agent status is - Not Installed
Task 4: On the VSM, Preparing Cisco VSG Port Profiles
To prepare Cisco VSG port profiles, you must create the VLANs and use the VLANs in the Cisco VSG data port profile and the Cisco VSG-ha port profile.
Make sure that you know the following:
1. On the VSM, create the VLANs by first entering global configuration mode using the following command:
2. Enter the following configuration commands:
3. Press Ctrl-Z to exit.
4. Create a Cisco VSG data port profile and a Cisco VSG-ha port profile by first enabling the Cisco VSG data port-profile configuration mode. Use the configure command to enter global configuration mode.
5. Enter the following configuration commands:
6. Press Ctrl-Z to end the session.
7. Enable the Cisco VSG-ha port profile configuration mode.
8. Enter the following configuration commands:
9. Add the VLANs created for the Cisco VSG data and Cisco VSG-ha interfaces as part of the allowed VLANs into the uplink port profile. Use the configure command to enter global configuration mode.
10. Enter the following configuration commands:
11. Press Ctrl-Z to end the session.
DETAILED STEPS
| Step 1 |
On the VSM, create the VLANs by first entering global configuration mode using the following command: vsm# configure |
| Step 2 |
Enter the following configuration commands: vsm(config)# vlan 100 vsm(config-vlan)# no shutdown vsm(config-vlan)# exit vsm(config)# vlan 200 vsm(config-vlan)# no shutdown vsm(config-vlan)# exit vsm(config)# exit vsm# configure vsm(config)# copy running-config startup-config vsm(config)# exit |
| Step 3 | Press Ctrl-Z to exit. |
| Step 4 |
Create a Cisco VSG data port profile and a Cisco VSG-ha port profile by first enabling the Cisco VSG data port-profile configuration mode. Use the configure command to enter global configuration mode. vsm# configure |
| Step 5 |
Enter the following configuration commands: vsm(config)# port-profile VSG-Data vsm(config-port-prof)# vmware port-group vsm(config-port-prof)# switchport mode access vsm(config-port-prof)# switchport access vlan 100 vsm(config-port-prof)# no shutdown vsm(config-port-prof)# state enabled vsm(config-port-prof)# exit vsm(config)# vsm(config)# copy running-config startup-config vsm(config)# exit |
| Step 6 | Press Ctrl-Z to end the session. |
| Step 7 |
Enable the Cisco VSG-ha port profile configuration mode. vsm# configure |
| Step 8 |
Enter the following configuration commands: vsm(config)# port-profile VSG-HA vsm(config-port-prof)# vmware port-group vsm(config-port-prof)# switchport mode access vsm(config-port-prof)# switchport access vlan 200 vsm(config-port-prof)# no shutdown vsm(config-port-prof)# state enabled vsm(config-port-prof)# exit vsm(config)# copy running-config startup-config vsm(config)# exit |
| Step 9 |
Add the VLANs created for the Cisco VSG data and Cisco VSG-ha interfaces as part of the allowed VLANs into the uplink port profile. Use the configure command to enter global configuration mode. vsm# configure |
| Step 10 |
Enter the following configuration commands: vsm(config)# port-profile type ethernet uplink vsm(config-port-prof)# switchport trunk allowed vlan add 100, 200 vsm(config-port-prof)# exit vsm(config)# |
| Step 11 | Press Ctrl-Z to end the session. |
Task 5: Installing the Cisco VSG from an OVA Template
Make sure that you know the following:
- The Cisco VSG OVA image is available in the vCenter.
- Cisco VSG-Data and Cisco VSG-ha port profiles are created on the VSM.
-
The management port profile (management)

Note
The management port profile is the same port profile that is used for the VSM. The port profile is configured in the VSM and is used for the Cisco VNMC management interface.
- The Cisco VSG-Data port profile: VSG-Data
- The Cisco VSG-ha port profile: VSG-ha
- The HA ID
- The IP/subnet mask/gateway information for the Cisco VSG
- The admin password
- 2-GB RAM and 3-GB hard disk space are available
- The Cisco VNMC IP address
- The shared secret password
- The IP connectivity between Cisco VSG and Cisco VNMC is okay.
- The Cisco VSG VNM-PA image name (vnmc-vsgpa.2.1.1b.bin) is available.
1. Choose the host on which to deploy the Cisco VSG VM.
2. Choose .
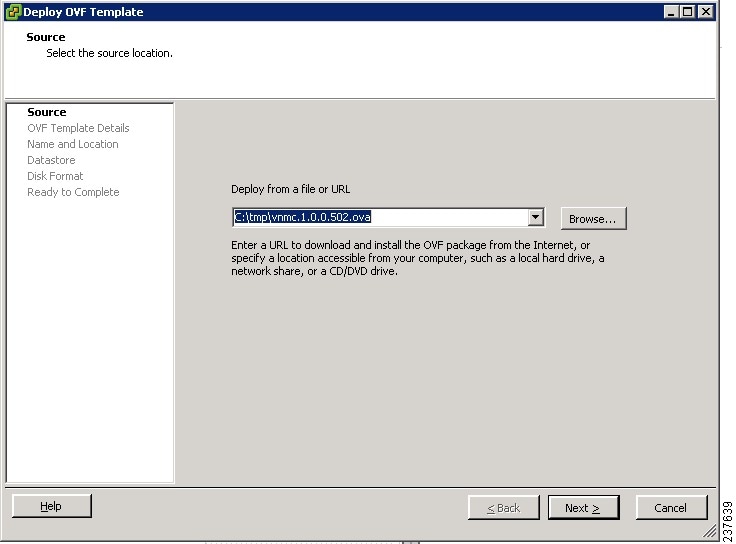
3. In the Deploy OVF Template—Source window, do the following:
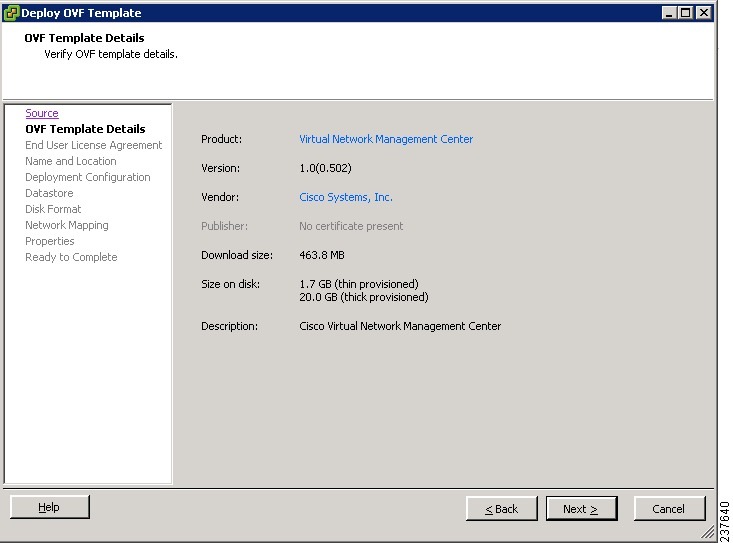
4. In the Deploy OVF Template—OVF Template Details window, review the product information including the size of the file and the VM disk.
5. Click Next.
6. In the Deploy OVF Template—End User License Agreement window, do the following:
7. In the Deploy OVF Template—Name and Location window, do the following:
8. In the Deploy OVF Template—Deployment Configuration window, do the following:
9. In the Deploy OVF Template—Datastore window, choose the data store for the VM and click Next. The Disk Format window opens.
10. In the Deploy OVF Template—Disk Format window, do the following:
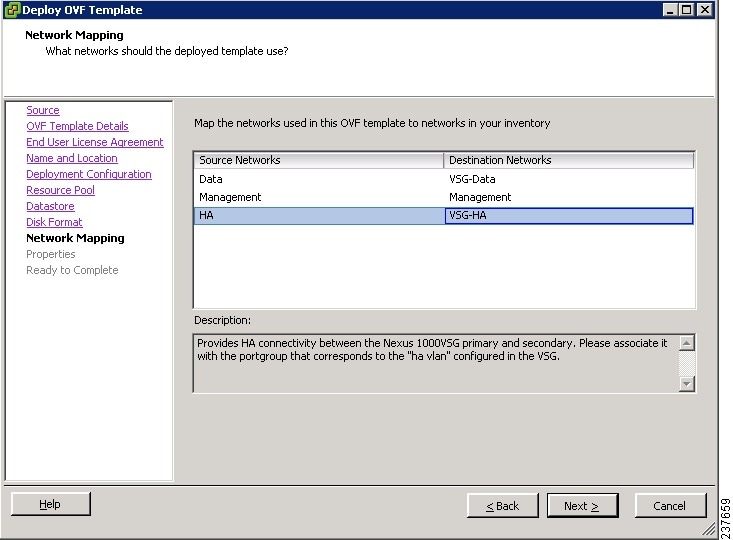
11. In the Deploy OVF Template—Network Mapping window, do the following:
12. In the Deploy OVF Template—Properties window, do the following:
13. Click Next. The Ready to Complete window opens.
14. In the Ready to Complete window, review the deployment settings information .
15. Click Finish. The Deploying Nexus 1000VSG dialog box opens.
16. Wait and click Close after the progress indicator shows that the deployment is completed successfully.
17. From your virtual machines, do one of the following:
18. In the Virtual Machine Properties window, do the following:
19. Power on the Cisco VSG VM.
DETAILED STEPS
| Step 1 | Choose the host on which to deploy the Cisco VSG VM. | ||
| Step 2 | Choose . | ||
| Step 3 | In the Deploy OVF Template—Source window, do the following: | ||
| Step 4 | In the Deploy OVF Template—OVF Template Details window, review the product information including the size of the file and the VM disk. | ||
| Step 5 | Click Next. | ||
| Step 6 | In the Deploy OVF Template—End User License Agreement window, do the following: | ||
| Step 7 |
In the Deploy OVF Template—Name and Location window, do the following:
|
||
| Step 8 | In the Deploy OVF Template—Deployment Configuration window, do the following: | ||
| Step 9 |
In the Deploy OVF Template—Datastore window, choose the data store for the VM and click Next. The Disk Format window opens. The storage can be local or shared remote such as the network file storage (NFS) or the storage area network (SAN).
|
||
| Step 10 |
In the Deploy OVF Template—Disk Format window, do the following:
|
||
| Step 11 |
In the Deploy OVF Template—Network Mapping window, do the following:
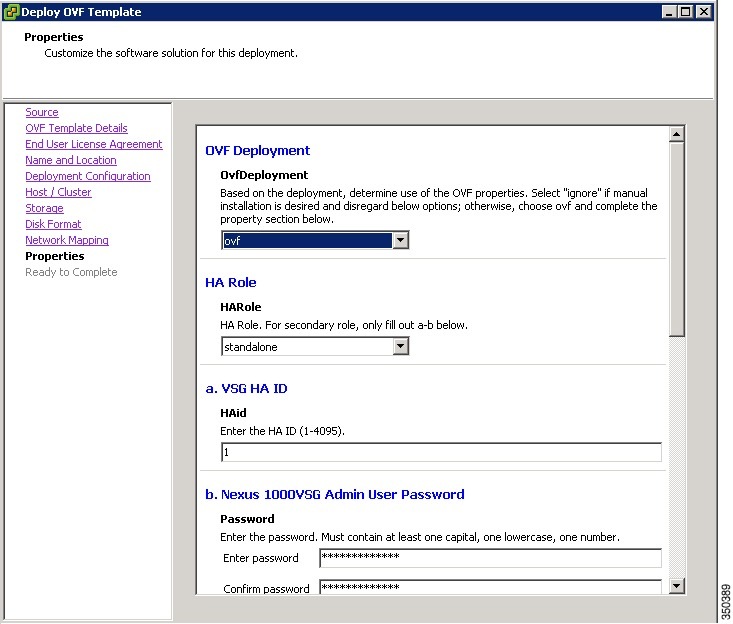
|
||
| Step 12 |
In the Deploy OVF Template—Properties window, do the following:
|
||
| Step 13 | Click Next. The Ready to Complete window opens. | ||
| Step 14 |
In the Ready to Complete window, review the deployment settings information .
|
||
| Step 15 |
Click Finish. The Deploying Nexus 1000VSG dialog box opens. The progress bar in the Deploying Nexus 1000VSG dialog box shows how much of the deployment task is completed before the Cisco VNMC is deployed. |
||
| Step 16 | Wait and click Close after the progress indicator shows that the deployment is completed successfully. | ||
| Step 17 |
From your virtual machines, do one of the following:
|
||
| Step 18 |
In the Virtual Machine Properties window, do the following:
Choosing 2 CPUs results in a higher performance. |
||
| Step 19 | Power on the Cisco VSG VM. |
Task 6: On the Cisco VSG and Cisco VNMC, Verifying the VNM Policy-Agent Status
You can use the show vnm-pa status command to verify the VNM policy-agent status (which can indicate that you have installed the policy-agent successfully).
1. Log in to the Cisco VSG.
2. Check the status of VNM-PA configuration by entering the following command:
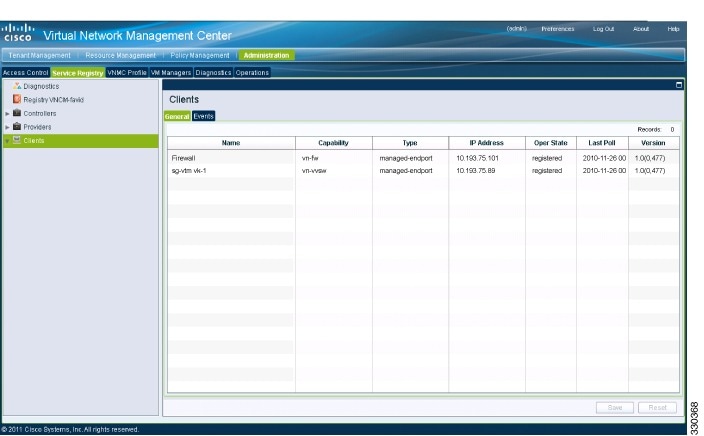
3. Log in to the Cisco VNMC. The VNMC Administration on Service Registry window opens.
4. Choose .
5. In the Client pane of the VNMC Administration Service Registry window, verify that the Cisco VSG and VSM information is listed.
DETAILED STEPS
| Step 1 | Log in to the Cisco VSG. |
| Step 2 |
Check the status of VNM-PA configuration by entering the following command: vsg# show vnm-pa status VNM Policy-Agent status is - Installed Successfully. Version 2.0(1a)-vsg vsg# |
| Step 3 |
Log in to the Cisco VNMC. The VNMC Administration on Service Registry window opens.
|
| Step 4 | Choose . |
| Step 5 | In the Client pane of the VNMC Administration Service Registry window, verify that the Cisco VSG and VSM information is listed. |
Task 7: On the Cisco VNMC, Configuring a Tenant, Security Profile, and Compute Firewall
Now that you have the Cisco VNMC and the Cisco VSG successfully installed with the basic configurations (completed through the OVA File Template wizard), you should configure some of the basic security profiles and policies.
This task includes the following subtasks:
Make sure that you know the following:
1. For Cisco VNMC access, from your client machine, open Internet Explorer and access https://vnmc-ip/ (https://xxx.xxx.xxx.xxx).
2. In the Website Security Certification window, click Continue to this website.
3. In the Cisco VNMC Access window, log in to the Cisco VNMC:
4. In the Cisco VNMC main window, choose to check the Cisco VSG and VSM registration in the Cisco VNMC.
DETAILED STEPS
| Step 1 | For Cisco VNMC access, from your client machine, open Internet Explorer and access https://vnmc-ip/ (https://xxx.xxx.xxx.xxx). |
| Step 2 | In the Website Security Certification window, click Continue to this website. |
| Step 3 | In the Cisco VNMC Access window, log in to the Cisco VNMC: |
| Step 4 |
In the Cisco VNMC main window, choose to check the Cisco VSG and VSM registration in the Cisco VNMC. The Clients pane lists the Cisco VSG and VSM information. |
What to Do Next
Configuring a Tenant on the Cisco VNMC
Tenants are entities (businesses, agencies, institutions, and so on) whose data and processes are hosted on VMs on the virtual data center. To provide firewall security for each tenant, the tenant must first be configured in the Cisco VNMC.
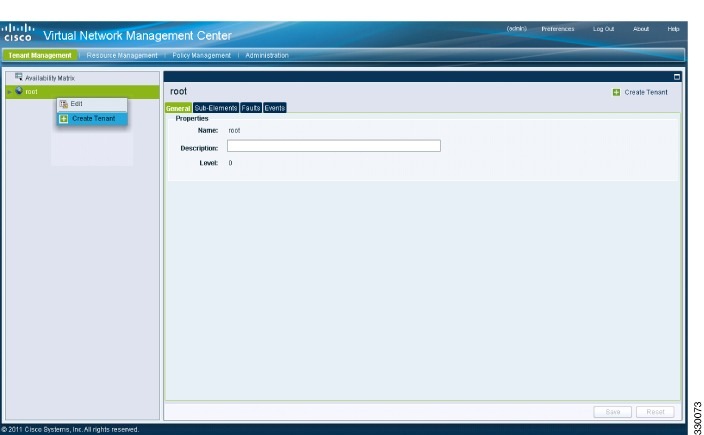
1. From the Cisco VNMC toolbar, click the Tenant Management tab.
2. In the Navigation pane directory tree, right-click on root, and from the drop-down list, choose Create Tenant.
3. In the root pane, click the General tab and do the following:
4. Click OK.
DETAILED STEPS
| Step 1 |
From the Cisco VNMC toolbar, click the Tenant Management tab.
|
| Step 2 | In the Navigation pane directory tree, right-click on root, and from the drop-down list, choose Create Tenant. |
| Step 3 | In the root pane, click the General tab and do the following: |
| Step 4 |
Click OK. Notice that the tenant you just created is listed in the left-side pane under root. |
What to Do Next
Configuring a Security Profile on the Cisco VNMC
You can configure a security profile on the Cisco VNMC.
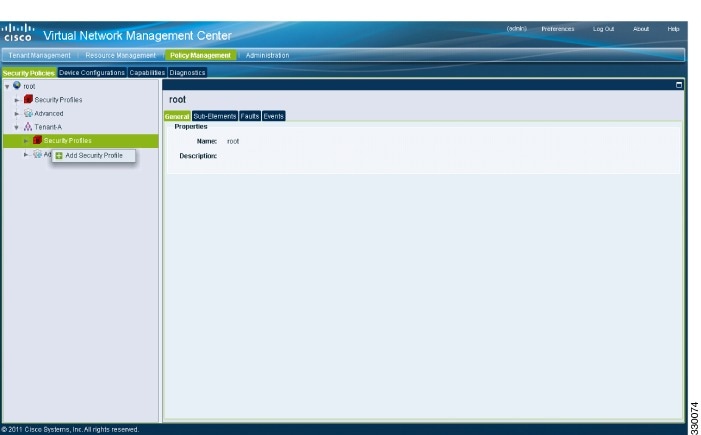
1. Click the Policy Management tab in the Cisco VNMC toolbar. The Policy Management window opens.
2. In the Policy Management Security Policies window, from the directory path, choose .
3. Right click in an empty space and choose Add Security Profile from the drop-down list.
4. In the Add Security Profile dialog box, do the following:
5. Click OK
DETAILED STEPS
| Step 1 |
Click the Policy Management tab in the Cisco VNMC toolbar. The Policy Management window opens.
|
| Step 2 | In the Policy Management Security Policies window, from the directory path, choose . |
| Step 3 |
Right click in an empty space and choose Add Security Profile from the drop-down list. The Add Security Profile dialog box opens. 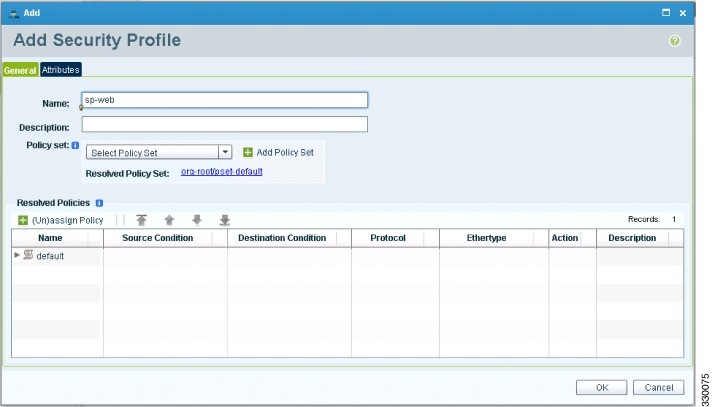
|
| Step 4 | In the Add Security Profile dialog box, do the following: |
| Step 5 | Click OK |
What to Do Next
Configuring a Compute Firewall on the Cisco VNMC
The compute firewall is a logical virtual entity that contains the device profile that you can bind (assign) to a Cisco VSG VM. The device policy in the device profile is then pushed from the Cisco VNMC to the Cisco VSG. Once this is complete, the compute firewall is in the applied configuration state on the Cisco VNMC.
1. From the Cisco VNMC, choose .
2. On the left-pane directory tree, choose .
3. From the drop-down list, choose Add Compute Firewall. The Add Compute Firewall dialog box opens.
4. In the Add Compute Firewall dialog box, do the following:
5. Click OK.
DETAILED STEPS
| Step 1 |
From the Cisco VNMC, choose . The Firewall Profiles window opens. 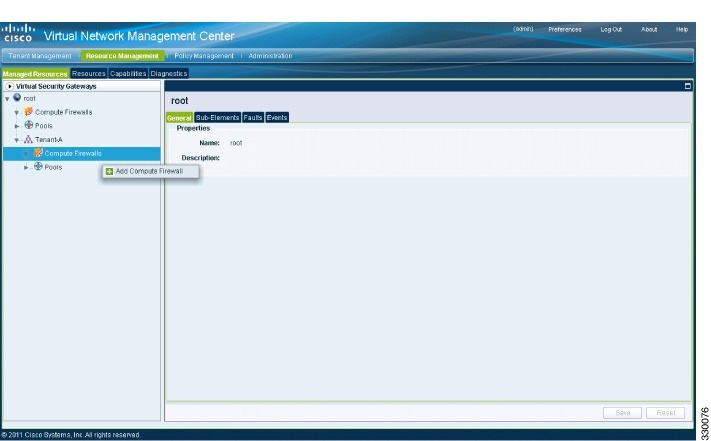
|
| Step 2 | On the left-pane directory tree, choose . |
| Step 3 |
From the drop-down list, choose Add Compute Firewall. The Add Compute Firewall dialog box opens.
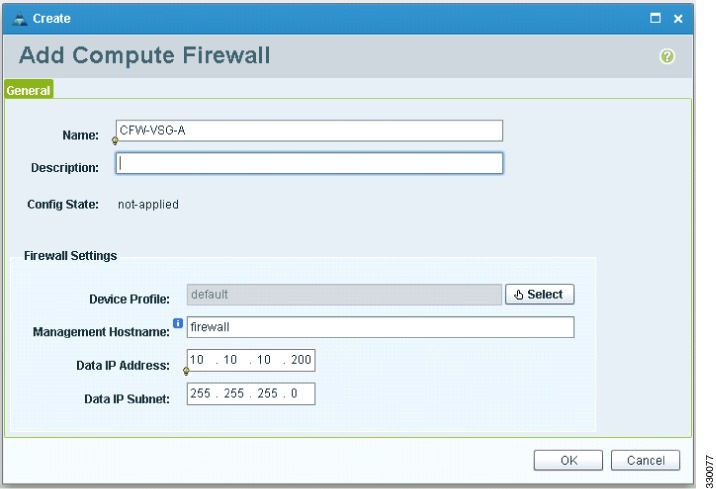
|
| Step 4 | In the Add Compute Firewall dialog box, do the following: |
| Step 5 |
Click OK. The new Compute Firewall pane displays with the information that you provided. |
Task 8: On the Cisco VNMC, Assigning the Cisco VSG to the Compute Firewall
The compute firewall is a logical virtual entity that contains the device profile that can be later bound to the device for communication with the Cisco VNMC and VSM.
1. Choose .The Deploy OVF Template window opens.
2. In the Deploy OVF Template window, choose .
3. Right-click in the Compute Firewalls pane and choose Assign VSG from the drop-down list.
4. From the Name drop-down list, choose the Cisco VSG IP address.
5. Click OK.
DETAILED STEPS
| Step 1 | Choose .The Deploy OVF Template window opens. | ||
| Step 2 |
In the Deploy OVF Template window, choose .
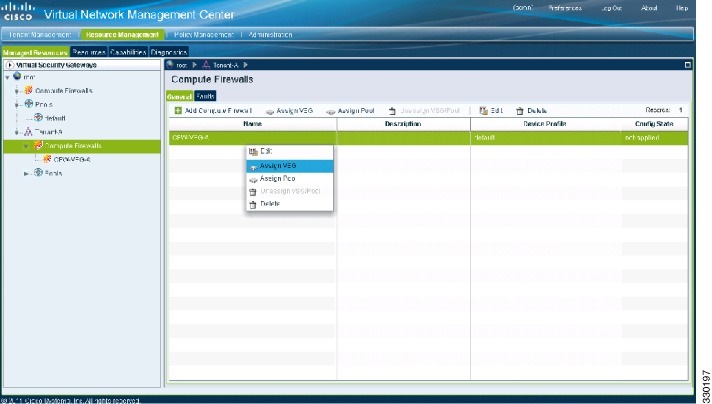
|
||
| Step 3 |
Right-click in the Compute Firewalls pane and choose Assign VSG from the drop-down list. The Assign VSG dialog box opens. 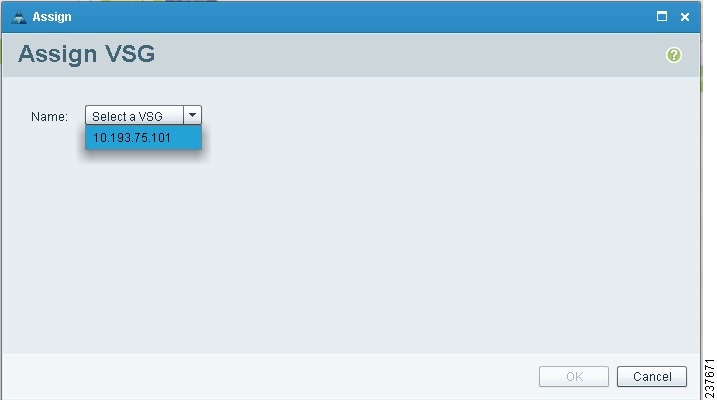
|
||
| Step 4 | From the Name drop-down list, choose the Cisco VSG IP address. | ||
| Step 5 |
Click OK.
|
Task 9: On the Cisco VNMC, Configuring a Permit-All Rule
You can configure a permit-all rule in the Cisco VNMC.
1. Log in to the Cisco VSG.
2. Choose . The Cisco VNMC Policy Management Security Policies window opens.
3. In the Cisco VNMC Policy Management Security Policies, window do the following:
4. Click Add Policy. The Add Policy dialog box opens.
5. In the Add Policy dialog box, do the following:
6. In the Add Rule dialog box, do the following:
7. In the Add Policy dialog box, click OK.
8. In the Add Policy Set dialog box, click OK.
9. In the Security Profile window, click Save.
DETAILED STEPS
| Step 1 | Log in to the Cisco VSG. |
| Step 2 |
Choose . The Cisco VNMC Policy Management Security Policies window opens.
|
| Step 3 | In the Cisco VNMC Policy Management Security Policies, window do the following: |
| Step 4 |
Click Add Policy. The Add Policy dialog box opens.
|
| Step 5 | In the Add Policy dialog box, do the following: |
| Step 6 |
In the Add Rule dialog box, do the following:
|
| Step 7 |
In the Add Policy dialog box, click OK. The newly created policy is displayed in the Assigned field. |
| Step 8 | In the Add Policy Set dialog box, click OK. |
| Step 9 | In the Security Profile window, click Save. |
Task 10: On the Cisco VSG, Verifying the Permit-All Rule
You can verify the rule presence in the Cisco VSG, by using the Cisco VSG CLI and the show commands.
vsg# show running-config | begin security security-profile SP_web@root/Tenant-A policy PS_web@root/Tenant-A custom-attribute vnsporg "root/tenant-a" security-profile default@root policy default@root custom-attribute vnsporg "root" rule Pol_web/permit-all@root/Tenant-A cond-match-criteria: match-all action permit action log rule default/default-rule@root cond-match-criteria: match-all action drop Policy PS_web@root/Tenant-A rule Pol_web/permit-all@root/Tenant-A order 101 Policy default@root rule default/default-rule@root order 2
Task 11: Enabling Logging
To enable logging follow these procedures:
Enabling Logging level 6 for Policy-Engine Logging
Logging enables you to see what traffic is going through your monitored virtual machine. This logging is helpful for verifying that you have a proper configuration and to help in troubleshooting. You can enable Logging Level 6 for policy-engine logging in a monitor session.
1. Log in to the Cisco VNMC.
2. Choose .
3. In the Device Configuration window, do the following:
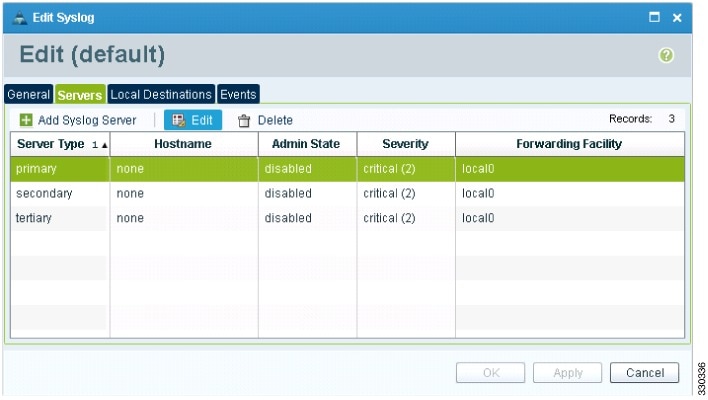
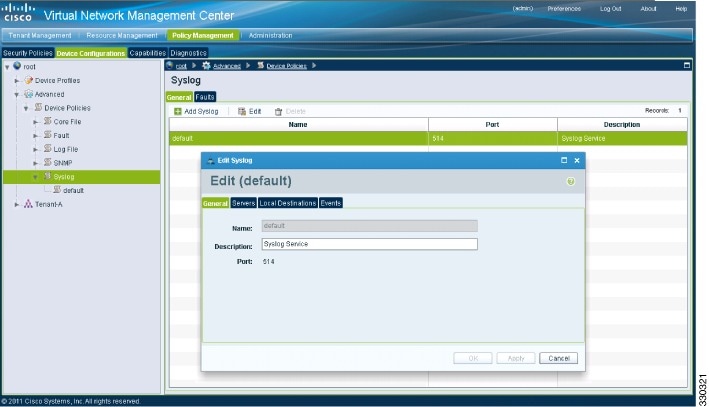
4. In the Edit Syslog dialog box, do the following:
5. In the Edit (Primary) Syslog Server dialog box, do the following:
6. Click OK.
DETAILED STEPS
| Step 1 | Log in to the Cisco VNMC. |
| Step 2 | Choose . |
| Step 3 |
In the Device Configuration window, do the following:
|
| Step 4 |
In the Edit Syslog dialog box, do the following:
|
| Step 5 | In the Edit (Primary) Syslog Server dialog box, do the following: |
| Step 6 | Click OK. |
What to Do Next
Enabling Global Policy-Engine Logging
Logging enables you to see what traffic is going through your monitored VM. This logging is helpful for verifying that you have a proper configuration and to help in troubleshooting.
1. Log in to the Cisco VNMC.
2. In the Virtual Network Management Control window, choose . The default Device Profile window opens.
3. In the default window, do the following:
4. Click Save.
DETAILED STEPS
| Step 1 |
Log in to the Cisco VNMC.
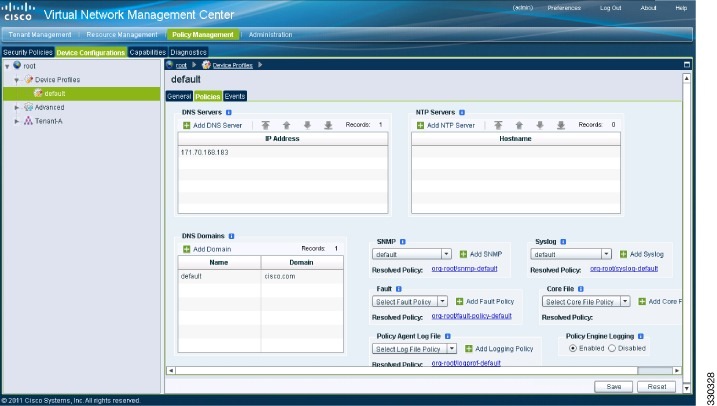
|
| Step 2 | In the Virtual Network Management Control window, choose . The default Device Profile window opens. |
| Step 3 | In the default window, do the following: |
| Step 4 | Click Save. |
Task12: Enabling the Traffic VM Port-Profile for Firewall Protection and Verifying the Communication Between the VSM, VEM, and VSG
This section includes the following topics:
Enabling Traffic VM Port-Profile for Firewall Protection
Verifying the VSM or VEM for Cisco VSG Reachability
Checking the VM Virtual Ethernet Port for Firewall Protection
Make sure that you know the following:
- The server virtual machine that runs with an access port profile (for example, web server)
- The Cisco VSG data IP address (10.10.10.200) and VLAN ID (100)
- The security profile name (for example, sp-web)
- The organization (Org) name (for example, root/Tenant-A)
- The port profile that you would like to edit to enable firewall protection
- That one active port in the port-profile with vPath configuration has been set up
Enabling Traffic VM Port-Profile for Firewall Protection
You can enable a traffic VM port profile for traffic protection.
1. Verify the traffic VM port profile before firewall protection.
DETAILED STEPS
vsm(config)# port-profile type vethernet pp-webserver vmware port-group switchport mode access switchport access vlan 756 no shutdown state enabled Enable firewall protection. VSM(config)# port-profile pp-webserver VSM(config-port-prof)# vservice node vsg1 profile SP_web VSM(config-port-prof)# org root/Tenant-A Verify the traffic VM port profile after firewall protection. VSM(config)# port-profile type vethernet pp-webserver vmware port-group switchport mode access switchport access vlan 756 org root/Tenant-A vservice node vsg1 profile SP_web no shutdown state enabled |
Verifying the VSM or VEM for Cisco VSG Reachability
This example shows how to verify the communication between the VEM and the VSG:
vsm# show vservice brief
--------------------------------------------------------------------------------
License Information
--------------------------------------------------------------------------------
Type In-Use-Lic-Count UnLicensed-Mod
vsg 4
asa 0
--------------------------------------------------------------------------------
Node Information
--------------------------------------------------------------------------------
ID Name Type IP-Address Mode State Module
1 vsg1 vsg 40.40.40.40 l3 Alive 4,5,
--------------------------------------------------------------------------------
Path Information
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Port Information
--------------------------------------------------------------------------------
PortProfile:pp-webserver
Org:root/Tenant-A
Node:vsg1(40.40.40.40) Profile(Id):SP_web(29) Veth Mod VM-Name vNIC IP-Address
23 4 vm1 2 14.14.14.21
A display showing the MAC-ADDR Listing and Up state verifies that the VEM can communicate with the Cisco VSG.
 Note |
In order to see the above status, one active port in the port profile with vPath configuration needs to be up. |
Checking the VM Virtual Ethernet Port for Firewall Protection
This example shows how to verify the VM Virtual Ethernet port for firewall protection:
VSM(config)# show vservice port brief vethernet 23
--------------------------------------------------------------------------------
Port Information
--------------------------------------------------------------------------------
PortProfile:pp-webserver
Org:root/Tenant-A
Node:vsg1(40.40.40.40) Profile(Id):SP_web(29)
Veth Mod VM-Name vNIC IP-Address
23 4 vm1 2 14.14.14.21
 Note |
Make sure that your VNSP ID value is greater than 1. |
Task13: Sending Traffic Flow and on the Cisco VSG Verifying Statistics and Logs
This section includes the following topics:
Sending Traffic Flow
You can send traffic flow through the Cisco VSG to ensure that it is functioning properly.
1. Ensure that you have the VM (Server-VM) that is using the port profile (pp-webserver) configured for firewall protection.
2. In the Virtual Machine Properties window, do the following:
3. Check the policy-engine statistics and log on the Cisco VSG.
DETAILED STEPS
| Step 1 |
Ensure that you have the VM (Server-VM) that is using the port profile (pp-webserver) configured for firewall protection.
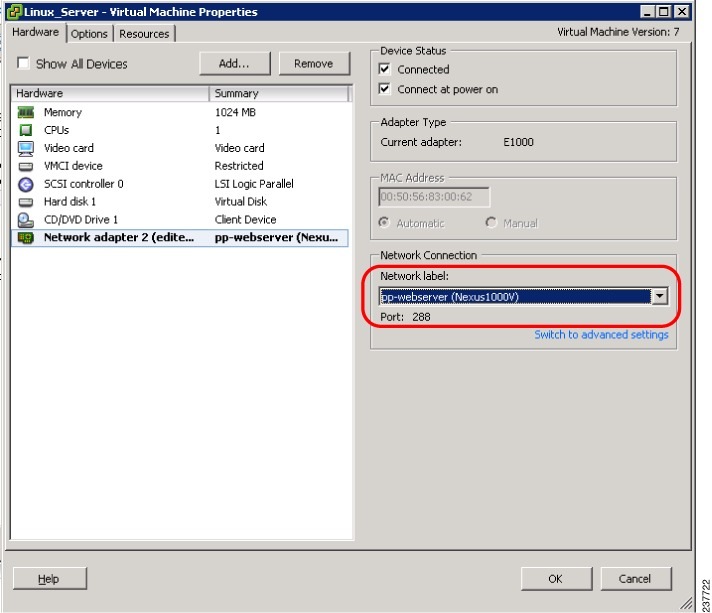
|
| Step 2 |
In the Virtual Machine Properties window, do the following:
[root@]# wget http://172.31.2.92/ --2010-11-28 13:38:40-- http://172.31.2.92/ Connecting to 172.31.2.92:80... connected. HTTP request sent, awaiting response... 200 OK Length: 258 [text/html] Saving to: `index.html' 100%[=======================================================================>] 258 --.-K/s in 0s 2010-11-28 13:38:40 (16.4 MB/s) - `index.html' saved [258/258] [root]# |
| Step 3 | Check the policy-engine statistics and log on the Cisco VSG. |
What to Do Next
Go to Verifying Policy-Engine Statistics and Logs on the Cisco VSG.
Verifying Policy-Engine Statistics and Logs on the Cisco VSG
Log in to the Cisco VSG and check the policy-engine statistics and logs.
This example shows how to check the policy-engine statistics and logs:
vsg# show policy-engine stats Policy Match Stats: default@root : 0 default/default-rule@root : 0 (Drop) NOT_APPLICABLE : 0 (Drop) PS_web@root/Tenant-A : 1 pol_web/permit-all@root/Tenant-A : 1 (Log, Permit) NOT_APPLICABLE : 0 (Drop) vsg# terminal monitor vsg# 2010 Nov 28 05:41:27 firewall %POLICY_ENGINE-6-POLICY_LOOKUP_EVENT: policy=PS_web@root/Tenant-A rule=pol_web/permit-all@root/Tenant-A action=Permit direction=egress src.net.ip-address=172.31.2.91 src.net.port=48278 dst.net.ip-address=172.31.2.92 dst.net.port=80 net.protocol=6 net.ethertype=800
 Feedback
Feedback