Before attempting to
upgrade to any software image, follow these guidelines:
-
Schedule the upgrade when your network is stable and steady.
-
Avoid any power interruption, which could corrupt the software image, during the installation procedure.
-
On devices with dual supervisor modules, both supervisor modules must have connections on the console ports to maintain connectivity
when switchovers occur during a software upgrade. See the Hardware Installation Guide for your specific chassis.
-
Perform the installation on the active supervisor module, not the standby supervisor module.
-
The compressed image of Cisco Nexus 3000-series is hardware dependent and can only be used on the same device that it got
compressed or downloaded from CCO. Do not use the Nexus 3000-series compressed image on Nexus 9000-series
-
The following limitation applies to all Cisco Nexus 9200, 9300, and 9300-EX platform switches:
A non-disruptive ISSU from Cisco NX-OS Release 7.0(3)I7(8) or 7.0(3)I7(9) to Cisco NX-OS Release 9.3(1) or 9.3(2) with NAT
enabled is not supported. NAT must be disabled prior to the upgrade.
-
If you are upgrading from any release to Cisco NX-OS Release 7.0(3)I7(6), 7.0(3)I7(7), or 7.0(3)I7(8) through LXC mode, it
is disruptive.
-
Performing a non-disruptive upgrade from Cisco NX-OS Release 7.0(3)I7(1) to 7.0(3)I7(3) (or a subsequent 7.x release) might
un-configure the PBR policy. Possible workarounds are:
-
Disruptive upgrade
-
Remove all PBR policy configurations before a non-disruptive ISSU from Cisco NX-OS Release 7.0(3)I7(1) to 7.0(3)I7(3) (or
a subsequent 7.x release). Perform the ISSU and re-apply the PBR configurations.
-
Perform the ISSU from Cisco NX-OS Release 7.0(3)I7(1) to 7.0(3)I7(3) (or a subsequent 7.x release) and reload the switch.
-
When performing a PoAP upgrade from Cisco NX-OS Release 6.0(2)A8(11) to Cisco NX-OS Release 7.0(3)I7(8), the provisioning
fails if the software image is not compacted. The PoAP script does not support SCP compact in 6.0(2)A8(11), so a non-compacted
image is copied instead, and this causes a bios upgrade failure.
To address this issue, use a pre-compacted image for PoAP from 6.0(2)A8(11). Perform a copy scp: urlbootflash: destination-file-system
compact to the switch, then copy it back to the PoAP server. Start the provisioning. PoAP should pick-up the already compacted image
and the provisioning should be successful.
-
When upgrading from Cisco NX-OS Release 7.0(3)I6(1) or 7.0(3)I7(1) to Cisco NX-OS Release 7.0(3)I7(2) (or a subsequent 7.x
release), if the Cisco Nexus 9000 Series switches are running vPC and they are connected to an IOS-based switch via Layer
2 vPC, there is a likelihood that the Layer 2 port channel on the IOS side will become error disabled. The workaround is to
disable the spanning-tree etherchannel guard misconfig command on the IOS switch before starting the upgrade process. Once both the Cisco Nexus 9000 Series switches are upgraded,
you can re-enable the command.
-
If you are upgrading from Cisco NX-OS Release 7.0(3)I5(2) to Cisco NX-OS Release 7.0(3)I6(1) (or a subsequent 7.x release)
using the install all command, BIOS will not be upgraded. When the upgrade to Cisco NX-OS Release 7.0(3)I6(1) (or a subsequent 7.x release) is
complete, use the install all command again to complete the BIOS upgrade, if applicable.
-
An upgrade performed via the install all command for Cisco NX-OS Release 7.0(3)I2(2b) to Release 7.0(3)I6(2) (or a subsequent 7.x release) might result in the VLANs
being unable to be added to the existing FEX HIF trunk ports. To recover from this, the following steps should be performed
after all FEXs have come online and the HIFs are operationally up:
-
Enter the copy run bootflash:fex_config_restore.cfg command at the prompt.
-
Enter the copy bootflash:fex_config_restore.cfg running-config echo-commands command at the prompt.
-
In Cisco NX-OS Release 7.0(3)I6(1) and earlier, performing an ASCII replay or running the copy file run command on a FEX HIF configuration requires manually reapplying the FEX configuration after the FEX comes back up.
-
When upgrading to Cisco NX-OS Release to 7.0(3)I7(1) (or a subsequent 7.x release) from 7.0(3)I2(x) or before and running
EVPN VXLAN configuration, an intermediate upgrade to 7.0(3)I4(x) or 7.0(3)I5(x) or 7.0(3)I6(x) is required.
-
When upgrading to Cisco NX-OS Release 7.0(3)I7(1) (or a subsequent 7.x release) running EVPN VXLAN and redistributing BGP
EVPN into OSPF, match the route-type internal under the relevant route-map configured.
-
When redistributing static routes, Cisco NX-OS requires the default-information originate command to successfully redistribute the default static route starting in 7.0(3)I7(6).
-
Before enabling the FHS on the interface, we recommend that you carve the ifacl TCAM region on Cisco Nexus 9300 and 9500 platform
switches. If you carved the ifacl TCAM region in a previous release, you must reload the system after upgrading to Cisco NX-OS
Release 7.0(3)I7(1) (or a subsequent 7.x release). Uploading the system will create the required match qualifiers for the
FHS TCAM region, ifacl.
-
Before enabling the FHS, we recommend that you carve the ing-redirect TCAM region on Cisco Nexus 9200 and 9300-EX platform
switches. If you carved the ing-redirect TCAM region in a previous release, you must reload the system after upgrading to
Cisco NX-OS Release 7.0(3)I7(1) (or a subsequent 7.x release). Uploading the system will create the required match qualifiers
for the FHS TCAM region, ing-redirect.
-
An error occurs when you try to perform an ISSU if you changed the reserved VLAN without entering the copy running-config save-config and reload commands.
-
On enhanced ISSUs from Cisco NX-OS Release 7.0(3)I5(1) or 7.0(3)I5(2) to Cisco NX-OS Release 7.0(3)I6(1) (or a subsequent
7.x release), ISSU completes, but you must reload the switch for tunnel enhancements to work. ToR ISSU does not require a
reload.
-
During an ISSU, there is a drop for all traffic to and from 100 Mb ports 65-66 on the Cisco Nexus 92304QC switch.
-
The install all command is the recommended method for software upgrades and downgrades because it performs configuration compatibility checks
and BIOS upgrades automatically. In contrast, changing the boot variables and reloading the device bypasses these checks and
the BIOS upgrade and therefore it is not recommended.
-
An enhanced ISSU can be performed only from a Cisco NX-OS Release 7.0(3)I5(1) to a later image. The upgrade will be disruptive.
-
Upgrading from Cisco NX-OS Release 7.0(3)I1(2), Release 7.0(3)I1(3), or Release 7.0(3)I1(3a) requires installing a patch for
Cisco Nexus 9500 platform switches only. For more information on the upgrade patch, see Upgrade Patch Instructions.
-
When upgrading to Cisco NX-OS Release 7.0(3)I2(1) (or a subsequent 7.x release), Guest Shell automatically upgrades from 1.0
to 2.0. In the process, the contents of the guest shell 1.0 root filesystem are lost. To keep from losing important content,
copy any needed files to /bootflash or an off-box location before upgrading to Cisco NX-OS Release 7.0(3)I2(1) (or a subsequent
7.x release).
-
While performing an ISSU, VRRP and VRRPv3 displays the following messages:
-
If VRRPv3 is enabled:
2015 Dec 29 20:41:44 MDP-N9K-6 %$ VDC-1 %$ %USER-0-SYSTEM_MSG: ISSU ERROR:
Service "vrrpv3" has sent the following message: Feature vrrpv3 is configured. User can
change vrrpv3 timers to 120 seconds or fine tune these timers based on upgrade time on all
Vrrp Peers to avoid Vrrp State transitions. – sysmgr
-
If VRRP is enabled:
2015 Dec 29 20:45:10 MDP-N9K-6 %$ VDC-1 %$ %USER-0-SYSTEM_MSG: ISSU ERROR:
Service "vrrp-eng" has sent the following message: Feature vrrp is configured. User can
change vrrp timers to 120 seconds or fine tune these timers based on upgrade time on all
Vrrp Peers to avoid Vrrp State transitions. – sysmgr
-
Guest Shell is disabled during an ISSU and reactivated after the upgrade. Any application running in the Guest Shell will
be affected.
-
If you have ITD probes configured, you need to disable the ITD service (using the shutdown command) before upgrading to Cisco NX-OS Release 7.0(3)I3(1) (or a subsequent 7.x release). After the upgrade, enter the
feature sla sender command to enable IP SLA for ITD probes and then the no shutdown command to re-enable the ITD service. (If you upgrade without shutting down the service, you can enter the feature sla sender command after the upgrade.)
-
For Cisco Nexus 9500 platform switches with -R line cards, you must perform a write erase and reload the device to upgrade
from any release prior to Cisco NX-OS Release 7.0(3)F3(4). To upgrade from Cisco NX-OS Release 7.0(3)F3(4) or any later release,
we recommend that you use the install all command, although we also support changing the boot variables and reloading the device.
-
Detect a bad software image before performing an ISSU upgrade from an old release to a new release by checking the md5sum
after downloading the new image (with seg6).
-
When upgrading from Cisco Nexus 94xx, 95xx, and 96xx line cards to Cisco Nexus 9732C-EX line cards and their fabric modules,
upgrade the Cisco NX-OS software before inserting the line cards and fabric modules. Failure to do so can cause a diagnostic
failure on the line card and no TCAM space to be allocated. You must use the write_erase command followed by the reload command.
-
If you upgrade from a Cisco NX-OS release that supports the CoPP feature to a Cisco NX-OS release that supports the CoPP feature
with additional classes for new protocols, you must either run the setup utility using the setup command or use the copp profile command for the new CoPP classes to be available. For more information on these commands, see the "Configuring Control Plane
Policing" chapter in the Cisco Nexus 9000 Series NX-OS Security Configuration Guide.
-
For secure POAP, ensure that DHCP snooping is enabled and set firewall rules to block unintended or malicious DHCP servers.
For more information on POAP, see the Cisco Nexus 9000 Series Fundamentals Configuration Guide.
-
When you upgrade from an earlier release to a Cisco NX-OS release that supports switch profiles [beginning with Cisco NX-OS
Release 7.0(3)I2(1)], you have the option to move some of the running-configuration commands to a switch profile. For more
information, see the Cisco Nexus 9000 Series NX-OS System Management Configuration Guide.
-
By default, the software upgrade process is disruptive.
-
OpenFlow and LACP fast timer rate configurations are not supported for Non-Disruptive ISSU.
-
Guest Shell is disabled during an ISSU and reactivated after the upgrade.
-
ISSU supports only default hold timers for BGP peers.
-
During an ISSU on a Cisco Nexus 3164Q, 31128PQ, or 9300 platform switch, all First-Hop Redundancy Protocols (FHRPs) will cause
the other peer to become active if the node undergoing the ISSU is active.
-
Make sure that both vPC peers are in the same mode (regular mode or enhanced mode) before performing a nondisruptive upgrade.

Note
|
vPC peering between an enhanced ISSU mode (boot mode lxc) configured switch and a non-enhanced ISSU mode switch is not supported.
|
-
During an ISSU, the software reload process on the first vPC device locks its vPC peer device by using CFS messaging over
the vPC communications channel. Only one device at a time is upgraded. When the first device completes its upgrade, it unlocks
its peer device. The second device then performs the upgrade process, locking the first device as it does so. During the upgrade,
the two vPC devices temporarily run different releases of Cisco NX-OS; however, the system functions correctly because of
its backward compatibility support.
-
ISSU is not supported when onePK is enabled. You can run the show feature | include onep command to verify that this feature is disabled before performing an ISSU or enhanced ISSU.
-
For Cisco Nexus 9500 platform switches with PTP enabled, we do not support non-disruptive ISSUs to Cisco NX-OS Release 7.0(3)I7(x)
from any earlier release. This issue is resolved in Cisco NX-OS Release 7.0(3)I7(1), so these switches support non-disruptive
ISSUs with PTP enabled from 7.0(3)I7(1) onwards.
-
On performing a non-disruptive ISSU from Cisco NX-OS Release 7.0(3)I6(1) to any higher version, a traffic loss might occur
based on the number of VLANs configured. To avoid traffic loss, it is recommended to increase the routing protocol's graceful
restart timer to higher value. The recommended value of the graceful restart timer is 600 seconds. You can further increase
or decrease this value based on the scale of the configuration.
-
ISSUs are supported for the following:
-
From a major release to any associated maintenance release. For example, you can perform an ISSU from Cisco NX-OS Release
7.0(3)I6(1) to any future Cisco NX-OS Release 7.0(3)I6(x) release, where x is any maintenance release of the respective major release.
-
From the last two maintenance releases to the next two major releases. For example, you can perform an ISSU from Cisco NX-OS
Release 7.0(3)I4(5) or 7.0(3)I4(6) to Cisco NX-OS Release 7.0(3)I5(2) or to 7.0(3)I6(1).
-
From an earlier maintenance release to the next two major releases. For example, you can perform an ISSU from Cisco NX-OS
Release 7.0(3)I4(3) to Cisco NX-OS Release 7.0(3)I4(4) or 7.0(3)I4(5). However, to upgrade from Cisco NX-OS Release 7.0(3)I4(3)
to 7.0(3)I6(1), you must perform two ISSUs, one from 7.0(3)I4(3) to 7.0(3)I4(4) or 4(5) and one from 7.0(3)I4(4) or 4(5) to
7.0(3)I6(1).
-
ISSUs are supported on the following platforms:
|
Series
|
Supported Platforms
|
Initial Release That Supports ISSU 1
|
Features Not Supported with ISSU2
|
|
Cisco Nexus 9200
|
Standard and enhanced ISSU: Cisco Nexus 9236C, 9272Q, 92160YC-X, 92300YC, and 92304QC
|
Standard ISSU: 7.0(3)I6(1)
Enhanced ISSU: 7.0(3)I7(3)
|
Segment routing, and Tetration
|
|
Cisco Nexus 9300
|
Standard and enhanced ISSU: Cisco Nexus 9332PQ, 9372PX, 9372PX-E, 9372TX, 9372TX-E, 9396PX, 9396TX, 93120TX, and 93128TX
|
Note
|
ISSU on one of these Cisco Nexus 9300 platform switches is supported when the switch is the spanning tree root. You can use
the show spanning-tree issu-impact command to verify if the switch meets this criteria.
|
|
Standard ISSU: 7.0(3)I3(1)
Enhanced ISSU: 7.0(3)I5(1)
|
Dual-homed FEX, MACsec, and segment routing
|
Note
|
Straight-through FEX is supported on Cisco Nexus 9372PX and 9396PX switches starting with Cisco NX-OS Release 7.0(3)I4(1).
|
|
|
Cisco Nexus 9300-EX
|
Standard and enhanced ISSU: Cisco Nexus 93108TC-EX, 93180LC-EX, and 93180YC-EX
|
Standard ISSU for Cisco Nexus 93108TC-EX and 93180YC-EX: 7.0(3)I6(1)
Standard ISSU for Cisco Nexus 93180LC-EX: 7.0(3)I7(1)
Enhanced ISSU: 7.0(3)I7(3)
|
Straight-through and dual-homed FEX, segment routing, MACsec, and Tetration
|
|
Cisco Nexus 9300-FX
|
Standard ISSU: None
Enhanced ISSU: None
|
|
MACsec |
|
Cisco Nexus 9500
|
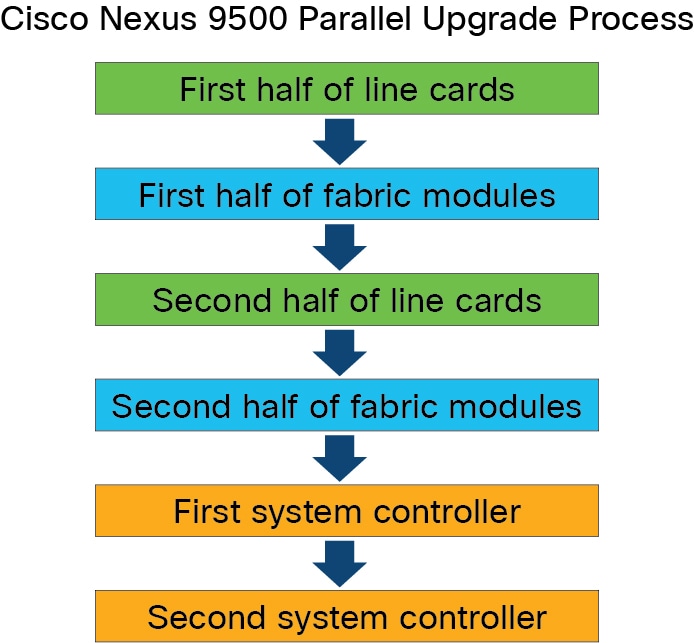
Standard ISSU: Cisco Nexus 9504, 9508, and 9516 with Cisco Nexus 9432PQ, 9464PX, 9464TX, 9536PQ, 9564PX, 9564TX, or 9636PQ
line cards, dual supervisor modules, and a minimum of two system controllers and two fabric modules
|
Note
|
Cisco Nexus 9500 platform switches with -R, -EX, and -FX line cards do not support ISSU.
|
Enhanced ISSU: None
|
Standard ISSU: 7.0(3)I3(1)
|
Dual-homed FEX, segment routing, and VXLAN
|
Note
|
Straight-through FEX is supported on Cisco Nexus 9500 platform switches with a Cisco Nexus 9464PX or 9564PX line card starting
with Cisco NX-OS Release 7.0(3)I4(1).
|
|
|
Cisco Nexus 3000 that run Cisco Nexus 9000 NX-OS software
|
Standard ISSU: Cisco Nexus 3164Q, 31128PQ, 3132Q-V, 31108PC-V, 31108TC-V, 3232C, and 3264Q
Enhanced ISSU: Cisco Nexus 3164Q, 31128PQ, 3132Q-V, 31108PC-V, and 31108TC-V
|
Standard ISSU for Cisco Nexus 3164Q and 31128PQ: 7.0(3)I3(1)
Standard ISSU for Cisco Nexus 3132Q-V, 31108PC-V,31108TC-V, 3232C, and 3264Q: 7.0(3)I6(1)
Enhanced ISSU for Cisco Nexus 3164Q, 31128PQ, 3132Q-V, 31108PC-V, and 31108TC-V: 7.0(3)I5(1)
|
Segment routing, and VXLAN for Cisco Nexus 3164Q and 31128PQ
Segment routing for Cisco Nexus 3232C and 3264Q
|



 Feedback
Feedback