Information About ERSPAN
The Cisco NX-OS system supports the Encapsulated Remote Switching Port Analyzer (ERSPAN) feature on both source and destination ports. ERSPAN transports mirrored traffic over an IP network. The traffic is encapsulated at the source router and is transferred across the network. The packet is decapsulated at the destination router and then sent to the destination interface.
ERSPAN consists of an ERSPAN source session, routable ERSPAN generic routing encapsulation (GRE)-encapsulated traffic, and an ERSPAN destination session. You can separately configure ERSPAN source sessions and destination sessions on different switches.
ERSPAN Source Sessions
An ERSPAN source session is defined by the following:
-
A session ID.
-
A list of source ports, source VLANs, or source VSANs to be monitored by the session.
-
An ERSPAN flow ID.
-
Optional attributes related to the GRE envelope such as IP TOS and TTL.
-
Destination IP address.
-
Virtual Routing and Forwarding tables.
ERSPAN source sessions do not copy ERSPAN GRE-encapsulated traffic from source ports. Each ERSPAN source session can have ports, VLANs, or VSANs as sources. However, there are some limitations. For more information, see Guidelines and Limitations for ERSPAN.
The following figure shows an example ERSPAN configuration.
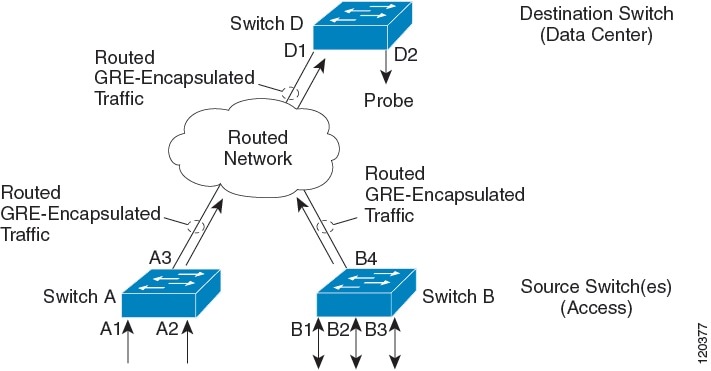
Monitored Traffic
By default, ERSPAN monitors all traffic, including multicast and bridge protocol data unit (BPDU) frames.
The direction of the traffic that ERSPAN monitors depends on the source, as follows:
-
For a source port, the ERSPAN can monitor ingress, egress, or both ingress and egress traffic.
-
For a source VLAN or source VSAN, the ERSPAN can monitor only ingress traffic.
ERSPAN Types
Cisco NX-OS Release 6.1 and later releases support ERSPAN Type II (default) and Type III. All previous Cisco NX-OS releases support only ERSPAN Type II.
ERSPAN Type III supports all of the ERSPAN Type II features and functionality and adds these enhancements:
-
Provides timestamp information in the ERSPAN Type III header that can be used to calculate packet latency among edge, aggregate, and core switches.
-
Identifies possible traffic sources using the ERSPAN Type III header fields.
-
Provides the ability to configure timestamp granularity to determine how the clock manager synchronizes the ERSPAN timers.
-
Beginning with Cisco NX-OS Release 7.1(1)N1(1), ERSPAN Type III provides configurable switch IDs that can be used to identify traffic flows across multiple switches.
| Attribute | Type II | Type III |
|---|---|---|
| Timestamp | NA | Timestamp provided. |
| Platform-specific info | NA | Platform-specific info is required for Nexus 5500, Nexus 5600 and Nexus 6000 platforms. |
| Source Port Identification at Termination Switch | Limited identification. | Detailed identification. Provision of switch IDs. |
ERSPAN Sources
-
Ethernet ports and port channels.
-
VLANs—When a VLAN is specified as an ERSPAN source, all supported interfaces in the VLAN are ERSPAN sources.
-
A port configured as a source port cannot also be configured as a destination port.
-
ERSPAN does not monitor any packets that are generated by the supervisor, regardless of their source.
Truncated ERSPAN
Truncated ERSPAN can be used to reduce the amount of fabric or network bandwidth used in sending ERSPAN packets.
The default is no truncation so switches or routers receiving large ERSPAN packets might drop these oversized packets.
 Note |
Do not enable the truncated ERSPAN feature if the destination ERSPAN router is a Cisco Nexus 6001 or Cisco Nexus 6004 switch because the Cisco Nexus 6000 Series switch drops these truncated packets. |
High Availability
The ERSPAN feature supports stateless and stateful restarts. After a reboot or supervisor switchover, the running configuration is applied.
 Feedback
Feedback