- Preface
- New and Changed Information
- Configuring Layer 2 Interfaces
- Configuring Layer 3 Interfaces
- Configuring Port Channels
- Configuring IP Tunnels
- Configuring VXLANs
- Configuring VXLAN BGP EVPN
- Configuring VXLAN OAM
- Configuring VXLAN Multihoming
- IPv6 Across a VXLAN EVPN Fabric
- Configuring Virtual Port Channels
- Configuring Q-in-Q VLAN Tunnels
- Index
- Network Address Translation Overview
- Information About Static NAT
- Dynamic NAT Overview
- Timeout Mechanisms
- NAT Inside and Outside Addresses
- Pool Support for Dynamic NAT
- Static and Dynamic Twice NAT Overview
- Licensing Requirements for Static NAT
- Guidelines and Limitations for Static NAT
- Restrictions for Dynamic NAT
- Guidelines and Limitations for Dynamic Twice NAT
- Configuring Static NAT
- Enabling Static NAT
- Configuring Static NAT on an Interface
- Enabling Static NAT for an Inside Source Address
- Enabling Static NAT for an Outside Source Address
- Configuring Static PAT for an Inside Source Address
- Configuring Static PAT for an Outside Source Address
- Configuring Static Twice NAT
- Configuration Example for Static NAT and PAT
- Example: Configuring Static Twice NAT
- Verifying the Static NAT Configuration
- Configuring Dynamic NAT
- Configuring Dynamic Translation and Translation Timeouts
- Configuring Dynamic NAT Pool
- Configuring Source Lists
- Configuring Dynamic Twice NAT for an Inside Source Address
- Configuring Dynamic Twice NAT for an Outside Source Address
- Clearing Dynamic NAT Translations
- Verifying Dynamic NAT Configuration
- Example: Configuring Dynamic Translation and Translation Timeouts
- Information About VRF Aware NAT
- Configuring VRF Aware NAT
Configuring Static and Dynamic NAT Translation
- Network Address Translation Overview
- Information About Static NAT
- Dynamic NAT Overview
- Timeout Mechanisms
- NAT Inside and Outside Addresses
- Pool Support for Dynamic NAT
- Static and Dynamic Twice NAT Overview
- Licensing Requirements for Static NAT
- Guidelines and Limitations for Static NAT
- Restrictions for Dynamic NAT
- Guidelines and Limitations for Dynamic Twice NAT
- Configuring Static NAT
- Configuring Dynamic NAT
- Information About VRF Aware NAT
- Configuring VRF Aware NAT
Network Address Translation Overview
Network Address Translation (NAT) enables private IP internetworks that use nonregistered IP addresses to connect to the Internet. NAT operates on a device, usually connecting two networks, and translates private (not globally unique) IP addresses in the internal network into legal IP addresses before packets are forwarded to another network. You can configure NAT to advertise only one IP address for the entire network to the outside world. This ability provides additional security, effectively hiding the entire internal network behind one IP address.
A device configured with NAT has at least one interface to the inside network and one to the outside network. In a typical environment, NAT is configured at the exit router between a stub domain and a backbone. When a packet leaves the domain, NAT translates the locally significant source IP address into a globally unique IP address. When a packet enters the domain, NAT translates the globally unique destination IP address into a local IP address. If more than one exit point exists, NAT configured at each point must have the same translation table.
Beginning Cisco NX-OS Release 7.0(3)I7(2), NAT is supported only on Cisco Nexus 3500 Series switches.
NAT is described in RFC 1631.
Information About Static NAT
Static Network Address Translation (NAT) allows the user to configure one-to-one translations of the inside local addresses to the outside global addresses. It allows both IP addresses and port number translations from the inside to the outside traffic and the outside to the inside traffic. The Cisco Nexus device supports Hitless NAT, which means that you can add or remove a NAT translation in the NAT configuration without affecting the existing NAT traffic flows.
Static NAT creates a fixed translation of private addresses to public addresses. Because static NAT assigns addresses on a one-to-one basis, you need an equal number of public addresses as private addresses. Because the public address is the same for each consecutive connection with static NAT, and a persistent translation rule exists, static NAT enables hosts on the destination network to initiate traffic to a translated host if an access list exists that allows it .
With dynamic NAT and Port Address Translation (PAT), each host uses a different address or port for each subsequent translation. The main difference between dynamic NAT and static NAT is that static NAT allows a remote host to initiate a connection to a translated host if an access list exists that allows it, while dynamic NAT does not.
The figure shows a typical static NAT scenario. The translation is always active so both translated and remote hosts can originate connections, and the mapped address is statically assigned by the static command.
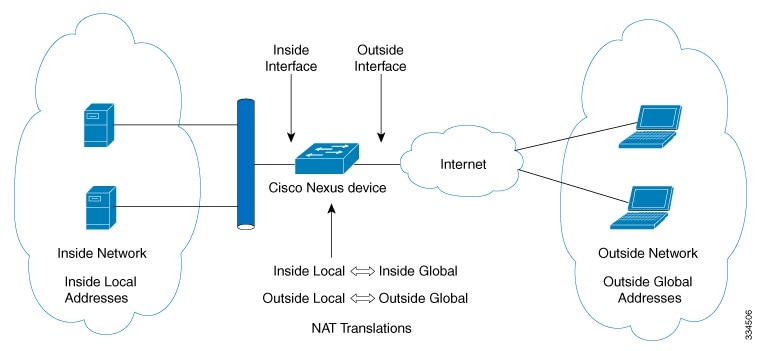
NAT inside interface—The Layer 3 interface that faces the private network.
NAT outside interface—The Layer 3 interface that faces the public network.
Local address—Any address that appears on the inside (private) portion of the network.
Global address—Any address that appears on the outside (public) portion of the network.
Legitimate IP address—An address that is assigned by the Network Information Center (NIC) or service provider.
Inside local address—The IP address assigned to a host on the inside network. This address does not need to be a legitimate IP address.
Outside local address—The IP address of an outside host as it appears to the inside network. It does not have to be a legitimate address, because it is allocated from an address space that can be routed on the inside network.
Inside global address—A legitimate IP address that represents one or more inside local IP addresses to the outside world.
Outside global address—The IP address that the host owner assigns to a host on the outside network. The address is a legitimate address that is allocated from an address or network space that can be routed.
Dynamic NAT Overview
Dynamic Network Address Translation (NAT) translates a group of real IP addresses into mapped IP addresses that are routable on a destination network. Dynamic NAT establishes a one-to-one mapping between unregistered and registered IP addresses; however, the mapping can vary depending on the registered IP address that is avkailable at the time of communication.
A dynamic NAT configuration automatically creates a firewall between your internal network and outside networks or the Internet. Dynamic NAT allows only connections that originate inside the stub domain—a device on an external network cannot connect to devices in your network, unless your device has initiated the contact.
Dynamic NAT translations do not exist in the NAT translation table until a device receives traffic that requires translation. Dynamic translations are cleared or timed out when not in use to make space for new entries. Usually, NAT translation entries are cleared when the ternary content addressable memory (TCAM) entries are limited. The default minimum timeout for dynamic NAT translations is 30 minutes. The minimum value of the sampling-timeout in the ip nat translation sampling-timeout command is 120 seconds. However it is recommended to configure the ip nat translation sampling-timeout value to 15 minutes or higher.
Dynamic NAT supports Port Address Translation (PAT) and access control lists (ACLs). PAT, also known as overloading, is a form of dynamic NAT that maps multiple unregistered IP addresses to a single registered IP address by using different ports. Your NAT configuration can have multiple dynamic NAT translations with same or different ACLs. However, for a given ACL, only one interface can be specified.
Timeout Mechanisms
After dynamic NAT translations are created, they must be cleared when not in use so that newer translations can be created, especially because the number of TCAM entries is limited. syn-timeout and finrst-timeout is supported only on Cisco Nexus 3500 Series switches. The following NAT translation timeout timers are supported on the switch:
-
syn-timeout—Timeout value for TCP data packets that send the SYN request, but do not receive a SYN-ACK reply.
The timeout value ranges from 1 second to 172800 seconds. The default value is 60 seconds.

Note
syn-timeout is not supported on Cisco 3100 Series switches.
-
finrst-timeout—Timeout value for the flow entries when a connection is terminated by receiving RST or FIN packets. Use the same keyword to configure the behavior for both RST and FIN packets. -
If an RST packet is received after the connection is established, SYN-->SYN-ACK-->RST, the flows are expired after the configured timeout value.
-
If a FIN packet is received after the connection is established, SYN-->SYN-ACK-->FIN, the finrst timer starts.
-
If a FIN-ACK is received from the other side, the translation entry is cleared immediately, else it clears after the timeout value completes. 
Note
If dynamic pool-based configuration is used and a FIN-ACK is received, the translation entry is not cleared.
finrst-timeout is not supported on Cisco 3100 Series switches.
The timeout value ranges from 1 second to 172800 seconds. The default value is 60 seconds.
-
-
tcp-timeout—Timeout value for TCP translations for which connections have been established after a three-way handshake (SYN, SYN-ACK, ACK). If no active flow occurs after the connection has been established, the translations expire as per the configured timeout value. This timeout value starts after the sampling timeout value completes.
The timeout value ranges from 60 seconds to 172800 seconds, including the sampling-timeout.
-
udp-timeout—Timeout value for all NAT UDP packets.
The timeout value ranges from 60 seconds to 172800 seconds, including the sampling-timeout.
-
timeout—Timeout value for dynamic NAT translations.
The timeout value ranges from 60 seconds to 172800 seconds, including the sampling-timeout.
-
sampling-timeout—Time after which the device checks for dynamic translation activity.
The timeout value ranges from 120 seconds to 172800 seconds.

Note
sampling-timeout is not supported on Cisco 3100 Series switches.
The tcp-timeout, udp-timeout, and the timeout value timers are triggered after the timeout configured for the ip nat translation sampling-timeout command expires.
The SYN, FIN and RST timers are not used for dynamic pool-based NAT.
 Note | All the above timers will take additional time (01 to 30 seconds) to expire. This additional time is to randomize the timer expiry events for performance and optimization. |
NAT Inside and Outside Addresses
NAT inside refers to networks owned by an organization that must be translated. When NAT is configured, hosts within this network will have addresses in one space (known as the local address space) that will appear to those outside the network as being in another space (known as the global address space).
Similarly, NAT outside refers to those networks to which the stub network connects. They are not generally under the control of the organization. Hosts in outside networks can be subject to translation and can have local and global addresses.
Local address—A local IP address that appears on the inside of a network.
Global address—A global IP address that appears on the outside of a network.
Inside local address—The IP address that is assigned to a host on the inside network. The address is probably not a legitimate IP address assigned by the Internet Network Information Center (InterNIC) or a service provider.
Inside global address—A legitimate IP address (assigned by InterNIC or a service provider) that represents one or more inside local IP addresses to the outside world.
Outside local address—The IP address of an outside host as it appears to the inside network. The address is not necessarily legitimate; it was allocated from the address space that is routable on the inside.
Outside global address—The IP address that is assigned to a host on the outside network by the owner of the host. The address was allocated from a globally routable address or a network space.
Pool Support for Dynamic NAT
Dynamic NAT allows the configuration of a pool of global addresses that can be used to dynamically allocate a global address from the pool for every new translation. The addresses are returned to the pool after the session ages out or is closed. This allows for a more efficient use of addresses based on requirements.
Support for PAT includes the use of the global address pool. This further optimizes IP address utilization. PAT exhausts one IP address at a time with the use of port numbers. If no port is available from the appropriate group and more than one IP address is configured, PAT moves to the next IP address and tries to allocate the original source port again. This process continues until PAT runs out of available ports and IP addresses.
With dynamic NAT and PAT, each host uses a different address or port for each subsequent translation. The main difference between dynamic NAT and static NAT is that static NAT allows a remote host to initiate a connection to a translated host if an access list exists that allows it, while dynamic NAT does not.
Static and Dynamic Twice NAT Overview
When both the source IP address and the destination IP address are translated as a single packet that goes through a Network Address Translation (NAT) device, it is referred to as twice NAT. Twice NAT is supported for static and dynamic translations.
Twice NAT allows you to configure two NAT translations (one inside and one outside) as part of a group of translations. These translations can be applied to a single packet as it flows through a NAT device. When you add two translations as part of a group, both the individual translations and the combined translation take effect.
A NAT inside translation modifies the source IP address and port number when a packet flows from inside to outside. It modifies the destination IP address and port number when the packet returns from outside to inside. NAT outside translation modifies the source IP address and port number when the packet flows from outside to inside, and it modifies the destination IP address and port number when the packet returns from inside to outside.
Without twice NAT, only one of the translation rules is applied on a packet, either the source IP address and port number or the destination IP address and port number.
Static NAT translations that belong to the same group are considered for twice NAT configuration. If a static configuration does not have a configured group ID, the twice NAT configuration will not work. All inside and outside NAT translations that belong to a single group that is identified by the group ID are paired to form twice NAT translations.
Dynamic twice NAT translations dynamically select the source IP address and port number information from pre-defined ip nat pool or interface overload configurations. Packet filtration is done by configuring ACLs, and traffic must originate from the dynamic NAT translation rule direction such that source translation is done by using dynamic NAT rules.
Dynamic twice NAT allows you to configure two NAT translations (one inside and one outside) as part of a group of translations. One translation must be dynamic and other translation must be static. When these two translations are part of a group of translations, both the translations can be applied on a single packet as it goes through the NAT device either from inside to outside or from outside to inside.
Licensing Requirements for Static NAT
|
Product |
License Requirement |
|---|---|
|
Cisco NX-OS |
Guidelines and Limitations for Static NAT
Static NAT has the following configuration guidelines and limitations:
-
Beginning Cisco NX-OS Release 7.0(3)I7(3) NAT is supported on Cisco Nexus 31108PC-V, Cisco Nexus 31108TC-V, Cisco Nexus 3132Q-V, Cisco Nexus 3132Q/3132Q-X, Cisco Nexus 3164Q, Cisco Nexus 3172PQ, Cisco Nexus 3172TQ, Cisco Nexus 31128PQ switches. However NAT is not supported on Cisco Nexus 3048 and Cisco Nexus 3064 switches.
-
Beginning Cisco NX-OS Release 7.0(3)I7(2) static NAT is supported only on Cisco Nexus 3500 Series switches.
-
NAT supports up to 1024 translations which include both static and dynamic NAT.
-
The Cisco Nexus device supports NAT on the following interface types:
-
NAT is supported for IPv4 Unicast only.
-
The Cisco Nexus device does not support the following:
-
Application layer translation. Layer 4 and other embedded IPs are not translated, including FTP, ICMP failures, IPSec, and HTTPs.
-
NAT and VLAN Access Control Lists (VACLs) that are configured on an interface at the same time.
-
PAT translation of fragmented IP packets.
-
NAT translation on software forwarded packets. For example, packets with IP-options are not NAT translated.
-
-
Egress ACLs are applied to the original packets and not the NAT translated packets.
-
HSRP and VRRP are not supported on a NAT interface.
-
Warp mode latency performance is not supported on packets coming from the outside to the inside domain.
-
If an IP address is used for Static NAT or PAT translations, it cannot be used for any other purpose. For example, it cannot be assigned to an interface.
-
For Static NAT, the outside global IP address should be different from the outside interface IP address.
-
If the translated IP is part of the outside interface subnet, then use the ip local-proxy-arp command on the NAT outside interface.
-
Twice NAT is not supported. (Twice NAT is a variation of NAT in that both the source and destination addresses are modified by NAT as a datagram crosses address domains (inside to outside or outside to inside.)
-
NAT statistics are not available.
-
When configuring a large number of translations (more than 100), it is faster to configure the translations before configuring the NAT interfaces.
Restrictions for Dynamic NAT
The following restrictions apply to dynamic Network Address Translation (NAT):
-
Beginning Cisco NX-OS Release 7.0(3)I7(2) dynamic NAT is supported only on Cisco Nexus 3500 Series switches.
-
Fragmented packets are not supported.
-
Application layer gateway (ALG) translations are not supported. ALG, also known as application-level gateway, is an application that translates IP address information inside the payload of an application packet.
-
NAT and VLAN Access Control Lists (VACLs) are not supported together on an interface. You can configure either NAT or VACLs on an interface.
-
Egress ACLs are not applied to translated packets.
-
MIBs are not supported.
-
Cisco Data Center Network Manager (DCNM) is not supported.
-
Dynamic NAT on traffic coming from outside domains is not supported.
-
Dynamic NAT translations are not synchronized with active and standby devices.
-
Stateful NAT is not supported. However, NAT and Hot Standby Router Protocol (HSRP) can coexist.
-
When creating a new translation on a Cisco Nexus 3548 Series switch, the flow is software forwarded until the translation is programmed in the hardware, which might take a few seconds. During this period, there is no translation entry for the inside global address. Therefore, returning traffic is dropped. To overcome this limitation, create a loopback interface and give it an IP address that belongs to the NAT pool.
Guidelines and Limitations for Dynamic Twice NAT
See the following guidelines for configuring dynamic twice NAT:
-
Beginning Cisco NX-OS Release 7.0(3)I7(2) dynamic twice NAT is supported only on Cisco Nexus 3500 Series switches.
-
In dynamic twice NAT, if dynamic NAT flows are not created before creating static NAT flows, dynamic twice NAT flows are not created correctly.
-
When an empty ACL is created, the default rule of permit ip any any is configured. The NAT-ACL does not match further ACL entries if the first ACL is blank.
-
The maximum number of supported ICMP translations or flow entries is 176 for an optimal utilization of the TCAM space.
-
NAT is ECMP aware and it supports a maximum of 24 ECMP paths.
Configuring Static NAT
Enabling Static NAT
Configuring Static NAT on an Interface
This example shows how to configure an interface with static NAT from the inside:
switch# configure terminal switch(config)# interface ethernet 1/4 switch(config-if)# ip nat inside
Enabling Static NAT for an Inside Source Address
For inside source translation, the traffic flows from inside interface to the outside interface. NAT translates the inside local IP address to the inside global IP address. On the return traffic, the destination inside global IP address gets translated back to the inside local IP address.
 Note | When the Cisco Nexus device is configured to translate an inside source IP address (Src:ip1) to an outside source IP address (newSrc:ip2), the Cisco Nexus device implicitly adds a translation for an outside destination IP address (Dst: ip2) to an inside destination IP address (newDst: ip1). |
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# ip nat inside source static local-ip-address global-ip-address [group group-id] | Configures static NAT to translate the inside global address to the inside local address or to translate the opposite (the inside local traffic to the inside global traffic). |
| Step 3 | switch(config)# copy running-config startup-config | (Optional)
Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example shows how to configure static NAT for an inside source address:
switch# configure terminal switch(config)# ip nat inside source static 1.1.1.1 5.5.5.5 switch(config)# copy running-config startup-config
Enabling Static NAT for an Outside Source Address
For outside source translation, the traffic flows from the outside interface to the inside interface. NAT translates the outside global IP address to the outside local IP address. On the return traffic, the destination outside local IP address gets translated back to outside global IP address.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# ip nat outside source static global-ip-address local-ip-address [group group-id] [add-route] |
Configures static NAT to translate the outside global address to the outside local address or to translate the opposite (the outside local traffic to the outside global traffic). |
| Step 3 | switch(config)# copy running-config startup-config | (Optional)
Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example show how to configure static NAT for an outside source address:
switch# configure terminal switch(config)# ip nat outside source static 2.2.2.2 6.6.6.6 switch(config)# copy running-config startup-config
Configuring Static PAT for an Inside Source Address
You can map services to specific inside hosts using Port Address Translation (PAT).
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# ip nat inside source static {inside-local-address outside-local-address | {tcp| udp} inside-local-address {local-tcp-port | local-udp-port} inside-global-address {global-tcp-port | global-udp-port}} | Maps static NAT to an inside local port to an inside global port. |
| Step 3 | switch(config)# copy running-config startup-config | (Optional)
Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example shows how to map UDP services to a specific inside source address and UDP port:
switch# configure terminal switch(config)# ip nat inside source static udp 20.1.9.2 63 35.48.35.48 130 switch(config)# copy running-config startup-config
Configuring Static PAT for an Outside Source Address
You can map services to specific outside hosts using Port Address Translation (PAT).
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# ip nat outside source static {outside-global-address outside-local-address | {tcp | udp} outside-global-address {global-tcp-port | global-udp-port} outside-local-address {global-tcp-port | global-udp-port}} | Maps static NAT to an outside global port to an outside local port. |
| Step 3 | switch(config)# copy running-config startup-config | (Optional)
Saves the change persistently through reboots and restarts by copying the running configuration to the startup configuration. |
This example shows how to map TCP services to a specific outside source address and TCP port:
switch# configure terminal switch(config)# ip nat outside source static tcp 20.1.9.2 63 35.48.35.48 130 switch(config)# copy running-config startup-config
Configuring Static Twice NAT
All translations within the same group are considered for creating static twice Network Address Translation (NAT) rules.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | enable
Example: switch> enable |
|
| Step 2 | configure terminal
Example: switch# configure terminal |
Enters privileged EXEC mode. |
| Step 3 | ip
nat
inside
source
static
inside-local-ip-address
inside-global-ip-address
[group
group-id]
Example: switch(config)# ip nat inside source static 10.1.1.1 192.168.34.4 group 4 |
|
| Step 4 | ip
nat
outside
source
static
outside-global-ip-address
outside-local-ip-address
[group
group-id] [add-route]
Example: switch(config)# ip nat outside source static 209.165.201.1 10.3.2.42 group 4 add-route |
|
| Step 5 | interface
type
number
Example: switch(config)# interface ethernet 1/2 |
Configures an interface and enters interface configuration mode. |
| Step 6 | ip
address
ip-address
mask
Example: switch(config-if)# ip address 10.2.4.1 255.255.255.0 |
Sets a primary IP address for an interface. |
| Step 7 | ip
nat
inside
Example: switch(config-if)# ip nat inside |
Connects the interface to an inside network, which is subject to NAT. |
| Step 8 | exit
Example: switch(config-if)# exit |
Exits interface configuration mode and returns to global configuration mode. |
| Step 9 | interface
type
number
Example: switch(config)# interface ethernet 1/1 |
Configures an interface and enters interface configuration mode. |
| Step 10 | ip
address
ip-address
mask
Example: switch(config-if)# ip address 10.5.7.9 255.255.255.0 |
Sets a primary IP address for an interface. |
| Step 11 | ip
nat
outside
Example: switch(config-if)# ip nat outside |
Connects the interface to an outside network, which is subject to NAT. |
| Step 12 | end
Example: switch(config-if)# end |
Exits interface configuration mode and returns to privileged EXEC mode. |
Configuration Example for Static NAT and PAT
This example shows the configuration for static NAT:
ip nat inside source static 103.1.1.1 11.3.1.1 ip nat inside source static 139.1.1.1 11.39.1.1 ip nat inside source static 141.1.1.1 11.41.1.1 ip nat inside source static 149.1.1.1 95.1.1.1 ip nat inside source static 149.2.1.1 96.1.1.1 ip nat outside source static 95.3.1.1 95.4.1.1 ip nat outside source static 96.3.1.1 96.4.1.1 ip nat outside source static 102.1.2.1 51.1.2.1 ip nat outside source static 104.1.1.1 51.3.1.1 ip nat outside source static 140.1.1.1 51.40.1.1
ip nat inside source static tcp 10.11.1.1 1 210.11.1.1 101 ip nat inside source static tcp 10.11.1.1 2 210.11.1.1 201 ip nat inside source static tcp 10.11.1.1 3 210.11.1.1 301 ip nat inside source static tcp 10.11.1.1 4 210.11.1.1 401 ip nat inside source static tcp 10.11.1.1 5 210.11.1.1 501 ip nat inside source static tcp 10.11.1.1 6 210.11.1.1 601 ip nat inside source static tcp 10.11.1.1 7 210.11.1.1 701 ip nat inside source static tcp 10.11.1.1 8 210.11.1.1 801 ip nat inside source static tcp 10.11.1.1 9 210.11.1.1 901 ip nat inside source static tcp 10.11.1.1 10 210.11.1.1 1001 ip nat inside source static tcp 10.11.1.1 11 210.11.1.1 1101 ip nat inside source static tcp 10.11.1.1 12 210.11.1.1 1201
Example: Configuring Static Twice NAT
The following example shows how to configure the inside source and outside source static twice NAT configurations:
Switch> enable Switch# configure terminal Switch(config)# ip nat inside source static 10.1.1.1 192.168.34.4 group 4 Switch(config)# ip nat outside source static 209.165.201.1 10.3.2.42 group 4 Switch(config)# interface ethernet 1/2 Switch(config-if)# ip address 10.2.4.1 255.255.255.0 Switch(config-if)# ip nat inside switch(config-if)# exit switch(config)# interface ethernet 1/1 switch(config-if)# ip address 10.5.7.9 255.255.255.0 switch(config-if)# ip nat outside Switch(config-if)# end
Verifying the Static NAT Configuration
To display the static NAT configuration, perform this task:
| Command or Action | Purpose |
|---|
This example shows how to display the static NAT configuration:
switch# sh ip nat translations
Pro Inside global Inside local Outside local Outside global
--- --- --- 51.3.1.1 104.1.1.1
--- --- --- 95.4.1.1 95.3.1.1
--- --- --- 96.4.1.1 96.3.1.1
--- --- --- 51.40.1.1 140.1.1.1
--- --- --- 51.42.1.1 142.1.2.1
--- --- --- 51.1.2.1 102.1.2.1
--- 11.1.1.1 101.1.1.1 --- ---
--- 11.3.1.1 103.1.1.1 --- ---
--- 11.39.1.1 139.1.1.1 --- ---
--- 11.41.1.1 141.1.1.1 --- ---
--- 95.1.1.1 149.1.1.1 --- ---
--- 96.1.1.1 149.2.1.1 --- ---
130.1.1.1:590 30.1.1.100:5000 --- ---
130.2.1.1:590 30.2.1.100:5000 --- ---
130.3.1.1:590 30.3.1.100:5000 --- ---
130.4.1.1:590 30.4.1.100:5000 --- ---
130.1.1.1:591 30.1.1.101:5000 --- ---
Configuring Dynamic NAT
Configuring Dynamic Translation and Translation Timeouts
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | enable
Example: Switch> enable |
|
| Step 2 | configure terminal
Example: Switch# configure terminal |
Enters global configuration mode. |
| Step 3 | ip access-list
access-list-name
Example: Switch(config)# ip access-list acl1 |
Defines an access list and enters access-list configuration mode. |
| Step 4 | permit
protocol source source-wildcard
any
Example: Switch(config-acl)# permit ip 10.111.11.0/24 any |
Sets conditions in an IP access list that permit traffic matching the conditions. |
| Step 5 | deny
protocol source source-wildcard
any
Example: Switch(config-acl)# deny udp 10.111.11.100/32 any |
Sets conditions in an IP access list that deny packets from entering a network. The deny rule is treated as a permit rule, and the packets matching the criteria mentioned in the deny rule are forwarded without NAT translation. |
| Step 6 | exit
Example: Switch(config-acl)# exit |
Exits access-list configuration mode and returns to global configuration mode. |
| Step 7 | ip
nat
inside
source
list
access-list-name
interface
type
number
overload
Example: Switch(config)# ip nat inside source list acl1 interface ethernet 1/1 overload |
Establishes dynamic source translation by specifying the access list defined in Step 3. |
| Step 8 | interface
type
number
Example: Switch(config)# interface ethernet 1/4 |
Configures an interface and enters interface configuration mode. |
| Step 9 | ip
address
ip-address
mask
Example: Switch(config-if)# ip address 10.111.11.39 255.255.255.0 |
Sets a primary IP address for the interface. |
| Step 10 | ip
nat
inside
Example: Switch(config-if)# ip nat inside |
Connects the interface to an inside network, which is subject to NAT. |
| Step 11 | exit
Example: Switch(config-if)# exit |
Exits interface configuration mode and returns to global configuration mode. |
| Step 12 | interface
type
number
Example: Switch(config)# interface ethernet 1/1 |
Configures an interface and enters interface configuration mode. |
| Step 13 | ip
address
ip-address
mask
Example: Switch(config-if)# ip address 172.16.232.182 255.255.255.240 |
Sets a primary IP address for an interface. |
| Step 14 | ip
nat
outside
Example: Switch(config-if)# ip nat outside |
Connects the interface to an outside network. |
| Step 15 | exit
Example: Switch(config-if)# exit |
Exits interface configuration mode and returns to global configuration mode. |
| Step 16 | ip
nat
translation
tcp-timeout
seconds
Example: Switch(config)# ip nat translation tcp-timeout 50000 |
|
| Step 17 | ip
nat
translation
max-entries
number-of-entries
Example: Switch(config)# ip nat translation max-entries 300 |
Specifies the maximum number of dynamic NAT translations. The number of entries can be between 1 and 1023. |
| Step 18 | ip
nat
translation
udp-timeout
seconds
Example: Switch(config)# ip nat translation udp-timeout 45000 |
|
| Step 19 | ip
nat
translation
timeout
seconds
Example: switch(config)# ip nat translation timeout 13000 |
Specifies the timeout value for dynamic NAT translations. |
| Step 20 | end
Example: Switch(config)# end |
Exits global configuration mode and returns to privileged EXEC mode. |
Configuring Dynamic NAT Pool
You can create a NAT pool by either defining the range of IP addresses in a single ip nat pool command or by using the ip nat pool and address commands
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# feature nat |
Enables the NAT feature on the device. |
| Step 3 | switch(config)# ip nat pool pool-name [startip endip] {prefix prefix-length | netmask network-mask} |
Creates a NAT pool with a range of global IP addresses. The IP addresses are filtered by using either a prefix length or a network mask. |
| Step 4 | switch(config-ipnat-pool)# address startip endip | (Optional)
Specifies the range of global IP addresses if they were not specified during creation of the pool. |
| Step 5 | switch(config)#
no ip nat
pool
pool-name
| (Optional)
Deletes the specified NAT pool. |
This example shows how to create a NAT pool with a prefix length:
switch# configure terminal switch(config)# ip nat pool pool1 30.1.1.1 30.1.1.2 prefix-length 24 switch(config)#
This example shows how to create a NAT pool with a network mask:
switch# configure terminal switch(config)# ip nat pool pool5 20.1.1.1 20.1.1.5 netmask 255.0.255.0 switch(config)#
This example shows how to create a NAT pool and define the range of global IP addresses using the ip nat pool and address commands:
switch# configure terminal switch(config)# ip nat pool pool7 netmask 255.255.0.0 switch(config-ipnat-pool)# address 40.1.1.1 40.1.1.5 switch(config-ipnat-pool)#
This example shows how to delete a NAT pool:
switch# configure terminal switch(config)# no ip nat pool pool4 switch(config)#
Configuring Source Lists
You can configure a source list of IP addresses for the inside interface and the outside interface.
Ensure that you configure a pool before configuring the source list for the pool.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch# ip nat inside source list list-name pool pool-name [overload] | (Optional)
Creates a NAT inside source list with pool with or without overloading. |
| Step 3 | switch# ip nat outside source list list-name pool pool-name [add-route] | (Optional)
Creates a NAT outside source list with pool without overloading. |
This example shows how to create a NAT inside source list with pool without overloading:
switch# configure terminal switch(config)# ip nat inside source list list1 pool pool1 switch(config)#
This example shows how to create a NAT inside source list with pool with overloading:
switch# configure terminal switch(config)# ip nat inside source list list2 pool pool2 overload switch(config)#
This example shows how to create a NAT outside source list with pool without overloading:
switch# configure terminal switch(config)# ip nat outside source list list3 pool pool3 switch(config)#
Configuring Dynamic Twice NAT for an Inside Source Address
For an inside source address translation, the traffic flows from the inside interface to the outside interface. You can configure dynamic twice NAT for an inside source address.
Ensure that you enable NAT on the switch.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# ip nat outside source static outside-global-ip-address outside-local-ip-address | [tcp | udp] outside-global-ip-address outside-global-port outside-local-ip-address outside-local-port [group group-id] [add-route] [dynamic] |
Configures static NAT to translate an outside global address to an inside local address or to translate inside local traffic to inside global traffic. The group keyword determines the group to which a translation belongs. |
| Step 3 | switch(config)# ip nat inside source list access-list-name [interface type slot/port overload | pool pool-name ] [group group-id] [dynamic] ] |
Establishes dynamic source translation by creating a NAT inside source list with pool with or without overloading. The group keyword determines the group to which a translation belongs. |
| Step 4 | switch(config)# ip nat pool pool-name [startip endip] {prefix prefix-length | netmask network-mask} |
Creates a NAT pool with a range of global IP addresses. The IP addresses are filtered by using either a prefix length or a network mask. |
| Step 5 | switch(config)# interface type slot/port |
Configures an interface and enters interface configuration mode. |
| Step 6 | switch(config-if)# ip nat outside |
Connects the interface to an outside network. |
| Step 7 | switch(config-if)# exit |
Exits interface configuration mode and returns to global configuration mode. |
| Step 8 | switch(config)# interface type slot/port |
Configures an interface and enters interface configuration mode. |
| Step 9 | switch(config-if)# ip nat inside |
Connects the interface to an inside network, which is subject to NAT. |
This example shows how to configure dynamic twice NAT for an inside source address:
switch# configure terminal Enter configuration commands, one per line. End with CNTL/Z. switch(config)# ip nat outside source static 2.2.2.2 4.4.4.4 group 20 dynamic switch(config)# ip nat inside source list acl_1 pool pool_1 overload group 20 dynamic switch(config)# ip nat pool pool_1 3.3.3.3 3.3.3.10 prefix-length 24 switch(config)# interface Ethernet1/8 switch(config-if)# ip nat outside switch(config-if)# exit switch(config)# interface Ethernet1/15 switch(config-if)# ip nat inside
Configuring Dynamic Twice NAT for an Outside Source Address
For an outside source address translation, the traffic flows from the outside interface to the inside interface. You can configure dynamic twice NAT for an outside source address.
Ensure that you enable NAT on the switch.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# ip nat inside source static inside-local-ip-address inside-global-ip-address | [tcp | udp] inside-local-ip-address local-port inside-global-ip-address global-port [group group-id] [dynamic] |
Configures static NAT to translate an inside global address to an inside local address or to translate inside local traffic to inside global traffic. The group keyword determines the group to which a translation belongs. |
| Step 3 | switch(config)# ip nat outside source list access-list-name [interface type slot/port pool pool-name ] [group group-id] [add-route] [dynamic] |
Establishes dynamic source translation by creating a NAT outside source list with pool. |
| Step 4 | switch(config)# ip nat pool pool-name [startip endip] {prefix prefix-length | netmask network-mask} |
Creates a NAT pool with a range of global IP addresses. The IP addresses are filtered by using either a prefix length or a network mask. |
| Step 5 | switch(config)# interface type slot/port |
Configures an interface and enters interface configuration mode. |
| Step 6 | switch(config-if)# ip nat outside |
Connects the interface to an outside network. |
| Step 7 | switch(config-if)# exit |
Exits interface configuration mode and returns to global configuration mode. |
| Step 8 | switch(config)# interface type slot/port |
Configures an interface and enters interface configuration mode. |
| Step 9 | switch(config-if)# ip nat inside |
Connects the interface to an inside network, which is subject to NAT. |
This example shows how to configure dynamic twice NAT for an outside source address:
switch# configure terminal Enter configuration commands, one per line. End with CNTL/Z. switch(config)# ip nat inside source static 7.7.7.7 5.5.5.5 group 30 dynamic switch(config)# ip nat outside source list acl_2 pool pool_2 group 30 dynamic switch(config)# ip nat pool pool_2 4.4.4.4 4.4.4.10 prefix-length 24 switch(config)# interface Ethernet1/6 switch(config-if)# ip nat outside switch(config-if)# exit switch(config)# interface Ethernet1/11 switch(config-if)# ip nat inside
Clearing Dynamic NAT Translations
To clear dynamic translations, perform the following task:
| Command | Purpose |
|---|---|
| clear ip nat translation [ all | inside global-ip-address local-ip-address [outside local-ip-address global-ip-address] | outside local-ip-address global-ip-address ] |
Deletes all or specific dynamic NAT translations. |
This example shows how to clear all dynamic translations:
switch# clear ip nat translation all
This example shows how to clear dynamic translations for inside and outside addresses:
switch# clear ip nat translation inside 2.2.2.2 4.4.4.4 outside 5.5.5.5 7.7.7.7
Verifying Dynamic NAT Configuration
To display dynamic NAT configuration, perform the following tasks:
| Command | Purpose |
|---|---|
|
show ip nat translations |
Displays active Network Address Translation (NAT) translations. Displays additional information for each translation table entry, including when an entry was created and used. |
|
show ip nat translations verbose |
Displays active Network Address Translation (NAT) translations including dynamic translations in a more readable format. |
|
show run nat |
Displays NAT configuration. |
This example shows how to display running configuration for NAT:
switch# show run nat
!Command: show running-config nat
!Time: Wed Apr 23 11:17:43 2014
version 6.0(2)A3(1)
feature nat
ip nat inside source list list1 pool pool1
ip nat inside source list list2 pool pool2 overload
ip nat inside source list list7 pool pool7 overload
ip nat outside source list list3 pool pool3
ip nat pool pool1 30.1.1.1 30.1.1.2 prefix-length 24
ip nat pool pool2 10.1.1.1 10.1.1.2 netmask 255.0.255.0
ip nat pool pool3 30.1.1.1 30.1.1.8 prefix-length 24
ip nat pool pool5 20.1.1.1 20.1.1.5 netmask 255.0.255.0
ip nat pool pool7 netmask 255.255.0.0
address 40.1.1.1 40.1.1.5
This example shows how to display active NAT translations:
Inside pool with overload
switch# show ip nat translation Pro Inside global Inside local Outside local Outside global icmp 20.1.1.3:64762 10.1.1.2:133 20.1.1.1:0 20.1.1.1:0 icmp 20.1.1.3:64763 10.1.1.2:134 20.1.1.1:0 20.1.1.1:0
switch# sh ip nat translations verbose
Pro Inside global Inside local Outside local Outside global
any 1.1.1.1 10.1.1.2 --- ---
Flags:0x1 Entry-id:0 State:0x0 Group_id:0 Format(H:M:S) Time-left:0:0:-1
icmp 101.1.0.1:65351 101.0.0.1:0 102.1.0.1:231 102.1.0.1:231
Flags:0x82 Entry-id:101 State:0x3 Group_id:0 VRF: red Format(H:M:S) Time-left:12:0:9
udp 101.1.0.1:65383 101.0.0.1:63 102.1.0.1:63 102.1.0.1:63
Flags:0x82 Entry-id:103 State:0x3 Group_id:0 VRF: red Format(H:M:S) Time-left:12:0:9
tcp 101.1.0.1:64549 101.0.0.1:8809 102.1.0.1:9087 102.1.0.1:9087
Flags:0x82 Entry-id:102 State:0x1 Group_id:0 VRF: red Format(H:M:S) Time-left:12:0:9
syn:0:1:9 fin-rst:12:0:9
Outside pool without overload
switch# show ip nat translation Pro Inside global Inside local Outside local Outside global any --- --- 177.7.1.1:0 77.7.1.64:0 any --- --- 40.146.1.1:0 40.46.1.64:0 any --- --- 10.4.146.1:0 10.4.46.64:0
switch# show ip nat translations verbose
Pro Inside global Inside local Outside local Outside global
any 1.1.1.1 10.1.1.2 --- ---
Flags:0x1 Entry-id:0 State:0x0 Group_id:0 Format(H:M:S) Time-left:0:0:-1
any 101.1.0.1 101.0.0.1 --- ---
Flags:0x0 Entry-id:92 State:0x3 Group_id:0 VRF: red Format(H:M:S) Time-left:12:0:11
Example: Configuring Dynamic Translation and Translation Timeouts
The following example shows how to configure dynamic overload Network Address Translation (NAT) by specifying an access list:
Switch> enable Switch# configure terminal Switch(config)# ip access-list acl1 Switch(config-acl)# permit ip 10.111.11.0/24 any Switch(config-acl)# deny udp 10.111.11.100/32 any Switch(config-acl)# exit Switch(config)# ip nat inside source list acl1 interface ethernet 1/1 overload Switch(config)# interface ethernet 1/4 Switch(config-if)# ip address 10.111.11.39 255.255.255.0 Switch(config-if)# ip nat inside Switch(config-if)# exit Switch(config)# interface ethernet 1/1 Switch(config-if)# ip address 172.16.232.182 255.255.255.240 Switch(config-if)# ip nat outside Switch(config-if)# exit Switch(config)# ip nat translation tcp-timeout 50000 Switch(config)# ip nat translation max-entries 300 Switch(config)# ip nat translation udp-timeout 45000 Switch(config)# ip nat translation timeout 13000 Switch(config)# end
Information About VRF Aware NAT
VRF aware NAT is supported by static and dynamic NAT configurations. When the traffic is configured to flow from a non-default VRF (inside) to the same non-default VRF (outside), the match-in-vrf option of the IP NAT command must be specified.
When the traffic is configured to flow from a non-default VRF (inside) to a default VRF (outside), the match-in-vrf option of the IP NAT command cannot be specified. A NAT outside configuration is not supported on a non-default VRF interface when the NAT inside is configured on a default VRF interface.
When overlapping addresses are configured across different VRFs for a NAT inside interface, a NAT outside interface should not be the default VRF interface. For example, vrfA and vrfB are configured as NAT inside interfaces with same source subnets and a NAT outside interface is configured as the default VRF. NAT is not supported in a configuration like this because of the ambiguity in routing packets from a NAT outside interface to NAT inside interface.
Configuring VRF Aware NAT
Ensure that you enable NAT on the switch.
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | switch# configure terminal |
Enters global configuration mode. |
| Step 2 | switch(config)# [no] ip nat inside | outside source list ACL_NAME [interface INTERFACE NAME overload ][pool POOL NAME overload ] [group group-id] [dynamic] [ vrf <vrf-name> [match-in-vrf] ] |
Creates or deletes dynamic NAT with VRF specific. The group keyword determines the group to which a translation belongs. |
| Step 3 | switch(config)# [no] ip nat inside | outside source static LOCAL IP GLOBAL IP | [tcp | udp LOCAL IP LOCAL PORT GLOBAL IP GLOBAL PORT ] [group group-id] [dynamic] [ vrf <vrf-name> [match-in-vrf] ] |
Creates or deletes a VRF specific static NAT. The group keyword determines the group to which a translation belongs. |
| Step 4 | switch(config)# interface type slot/port [ vrf <vrf-name ip nat inside | outside |
Enables NAT on a VRF-aware interface. |
See the output of show run nat command.
#show run nat
….
feature nat
ip nat inside source static 1.1.1.1 1.1.1.100 vrf red match-in-vrf
ip nat outside source static 2.2.2.200 2.2.2.2 vrf red match-in-vrf add-route
ip nat inside source list nat-acl-in1 pool pool-in1 vrf red match-in-vrf overload
ip nat outside source list nat-acl-out1 pool pool-out1 vrf red match-in-vrf add-route
interface Ethernet1/3
ip nat outside
interface Ethernet1/5
ip nat inside
N3548#show ip nat translation verbose
Pro Inside global Inside local Outside local Outside global
any 1.1.1.1 10.1.1.2 --- ---
Flags:0x1 Entry-id:0 State:0x0 Group_id:0 Format(H:M:S) Time-left:0:0:-1
icmp 101.1.0.1:65351 101.0.0.1:0 102.1.0.1:231 102.1.0.1:231
Flags:0x82 Entry-id:101 State:0x3 Group_id:0 VRF: red Format(H:M:S) Time-left:12:0:9
udp 101.1.0.1:65383 101.0.0.1:63 102.1.0.1:63 102.1.0.1:63
Flags:0x82 Entry-id:103 State:0x3 Group_id:0 VRF: red Format(H:M:S) Time-left:12:0:9
tcp 101.1.0.1:64549 101.0.0.1:8809 102.1.0.1:9087 102.1.0.1:9087
Flags:0x82 Entry-id:102 State:0x1 Group_id:0 VRF: red Format(H:M:S) Time-left:12:0:9
syn:0:1:9 fin-rst:12:0:9
 Feedback
Feedback