Document Flow
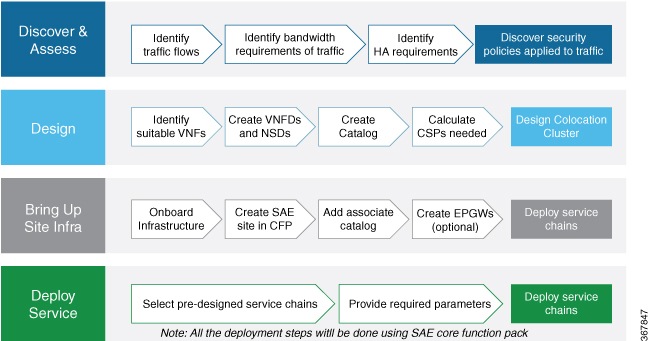
The document is structured according to the stages an enterprise would go through when they decide to deploy SAE. Typically, enterprises would go through the following milestones in their SAE journey.
-
Assess and analyze existing infrastructure and traffic flows
-
Design services based on existing patterns so that they can be instantiated as required
-
Deploy hardware and compute requirements based on your service requirements and design
-
Deploy service chains

 Feedback
Feedback