Understanding the Device Inventory
Security Manager maintains an inventory of the devices that it manages. The inventory includes the information required to locate and log into the device, so that your policies can be deployed to the devices. The following topics describe some general concepts related to the device inventory:
Understanding the Device View
The Device View button opens the Devices page, from which you can add and delete devices from the Security Manager inventory and manage device policies, properties, and interfaces centrally.
This is a device-centric view in which you can see all devices that you are managing and you can select specific devices to view their properties and define their settings and policies. You can define security policies locally on specific devices. You can then share those policies to make them globally available to be assigned to other devices.
The Devices page contains two panes. The left pane contains two elements: the Device selector, located in the top left pane, and the Policy selector, located in the bottom left pane. The right pane is the main content area. The following illustration shows the Devices page.
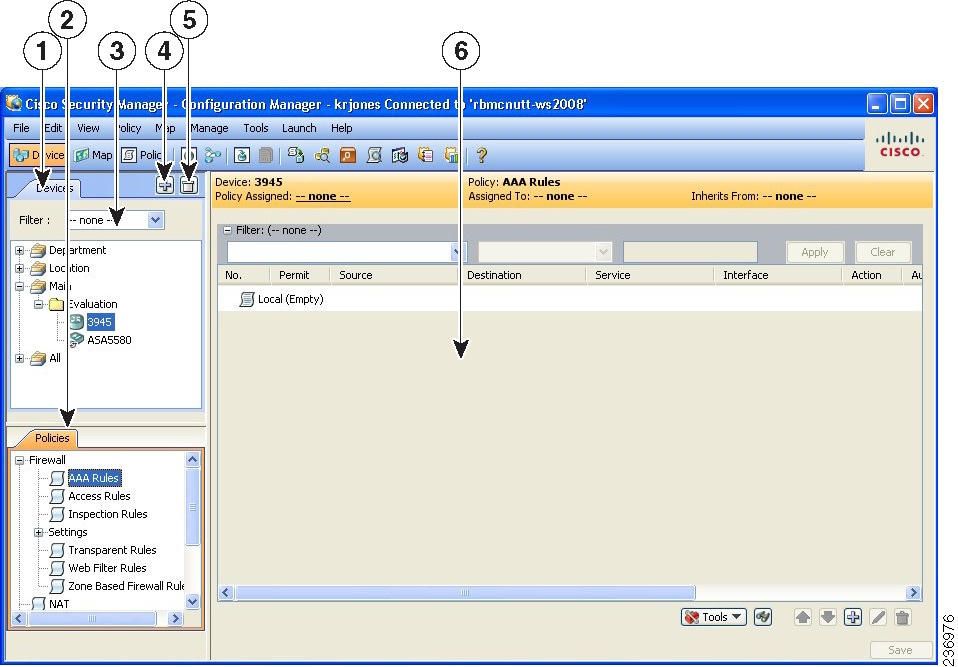
Device selector (1, 3, 4, 5)—Contains the following:
-
Add and Delete buttons (4, 5)—Enables you to add and delete devices from the Security Manager inventory.
-
Filter field (3)—Enables you to display a subset of devices based on the filtering criteria you define. For details, see Filtering Items in Selectors.
-
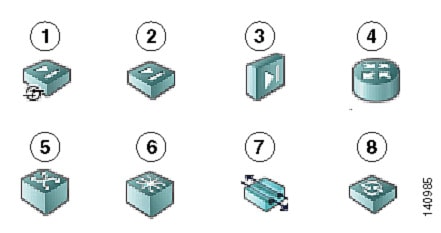
Device tree—Lists the device groups and devices that exist in the system. Each device type is represented by an icon. For information about the icons, see Figure 3-2.
If you hover the mouse pointer over a device, detailed information about the device appears in a popup window. The information is a summary of the device properties (see Device Properties: General Page).
 Note |
Beginning from version 4.8, Security Manager displays the updated version information of a device that has been upgraded using Auto Update Server (AUS). To enable this feature you must configure Security Manager details in the AUS user interface. If you hover the mouse over a device, the following message appears if AUS has successfully updated the device version: |
"State Description: Version update is successfully completed by Auto Update Server. Check if any other configuration changes are required in Security Manager."
|
1 |
Adaptive Security Appliances (ASA) |
5 |
Catalyst Switch |
|
2 |
PIX Firewall |
6 |
Catalyst 7600 Series Router |
|
3 |
Catalyst security Services Modules: Firewall Services Module (FWSM) and ASA-SM |
7 |
VPN 3000 Concentrator |
|
4 |
Cisco IOS Router |
8 |
Intrusion Prevention System (IPS) |
-
Shortcut menu options—When you right-click a device or device group, you get a menu of commands related to that device or group. These commands are shortcuts to commands available in the regular menus.
Policy selector (2)—Contains the following:
-
Policy groups—Lists the policy groups that are supported on the selected device type. The policy groups that are displayed are dependent on four factors:
-
The type of device selected in the Device selector.
-
The operating system running on the device.
-
The target operating system version selected for determining which commands will be available for generated configurations.
-
Whether the device contains supported service modules.
-
For more information about policies, see Understanding Policies
-
Shortcut menu options—When you right-click a policy, you get a menu of commands related to that policy. These commands are shortcuts to commands available in the regular menus.
Contents pane (6)—The main content area.
The information displayed in this area depends on the device you select from the Device selector and the option you select from the Policy selector.
Understanding Device Names and What Is Considered a Device
Besides managing traditional devices, you can use Security Manager to manage virtual devices that you can define on some types of security devices. These virtual devices are treated as separate devices in the device inventory, and they appear as separate entries in the device selectors. Because these virtual devices actually reside on a host physical device, many actions, such as deployment, will have to include the host device as well as the virtual device.
All physical devices appear in the device selectors. In addition, these are the types of virtual devices that appear in the device selectors:
-
Security Contexts—You can define security contexts on PIX Firewall, FWSM, and ASA devices. Security contexts act as virtual firewalls. By default, security contexts appear in the device selectors using this naming convention: host-display-name_context-name , where host-display-name is the display name of the device on which the context is defined, and context-name is the name of the security context. For example, the admin security context on the device named firewall12 would be called firewall12_admin.
 Tip |
You can control whether the display name is added to the context name using the Prepend Device Name when Generating Security Context Names property on the Discovery settings page (see Discovery Page). However, if you do not add the display name, it is very difficult to determine the hosting device for a context, and the context names are not sorted with the host device (they do not appear in a folder attached to the host device). If you do not add the display name, Security Manager adds a numeric suffix to the context name if more than one context of the same name is added to the inventory (for example, admin_01, admin_02), and these numbers are not related to the host device. |
-
Virtual Sensors—You can define virtual sensors on IPS devices. Virtual sensors appear in device selectors using the host-display-name_virtual-sensor-name naming convention, and there is not a discovery setting to control this convention.
 Tip |
You can always change the display name for a virtual sensor, security context, or other type of device in the device’s properties. |
Besides the naming conventions for virtual devices, you also need to understand the relationship between various types of device names:
-
Display name—The display name is simply the name that appears within Security Manager in device selectors. This name does not have to be related to any name actually defined on the device. When you add devices to the inventory, a display name is suggested based on the DNS name or IP address you enter, but you can use whatever naming convention you want to use.
-
DNS name—The DNS name you define for a device must be resolvable by the DNS server configured for the Security Manager server.
-
IP address—The IP address you define for a device should be the management IP address for the device.
-
Hostname—When you discover a device, the hostname property that is shown in the device properties is taken from the device’s configuration. If you add devices using configuration files, and a file does not contain a hostname command, the initial hostname is the name of the configuration file.
However, the hostname device property is not updated if you change the hostname on the device. There is a Hostname policy in the device platform policy area, and it is this Hostname policy that determines the hostname that is defined on the device.
Understanding Device Credentials
Security Manager requires credentials for logging in to devices. You can provide device credentials in two ways:
-
When you add a device manually or from network discovery. For more information, see these topics:
-
By editing the device properties. For more information, see Viewing or Changing Device Properties.
You can provide the following device credentials:
-
Primary Credentials—The username and password for logging into the device using SSH or Telnet. This information is required for device communication.
-
HTTP Credentials—Some devices allow HTTP or HTTPS connections, and some devices (such as IPS devices) require it. By default, Security Manager uses the primary credentials for HTTP/HTTPS access, but you can configure unique HTTP/HTTPS credentials.
-
RX-Boot Mode—(Optional) Some Cisco routers are designed to run from flash memory where they boot only from the first file in flash. This means that you must run an image other than the one in flash to upgrade the flash image. That image is a reduced command-set image referred to as RX-Boot (a ROM-based image).
-
SNMP Credentials—(Optional) The Simple Network Management Protocol (SNMP) facilitates the exchange of management information between network devices. SNMP enables network administrators to manage network performance, find and solve network problems, and plan for network growth.
 Note |
PIX/ASA/FWSM devices require that user names be at least four characters. Passwords can be three to 32 characters; we recommend that passwords be at least eight characters. For ASA devices running the software version 9.6(1) or later, you can enter a password up to 127 characters. |
Rather than using device-based credentials, you can configure Security Manager to use the credentials you use when you log into Security Manager. You can then use the AAA server’s accounting facilities to track configuration changes by user. Using user login credentials is suitable only if your environment is configured according to these standards:
-
You use TACACS+ or RADIUS for change auditing. User-login credentials will be reflected in these accounting records. If you use device credentials, all changes made through Security Manager will come from the same account, regardless of which user made the change.
-
User accounts are configured in the AAA server, and they have appropriate device-level access to perform configuration changes.
-
You configure Security Manager and the managed devices to use the AAA server for authorization. For information on configuring Security Manager to use AAA, see the Installation Guide for Cisco Security Manager .
-
You do not use one-time passwords.
If your network setup supports using user-login credentials, you can configure Security Manager to use them by selecting . Select Device Communication from the table of contents, and select Security Manager User Login Credentials in the Connect to Device Using field. The default is to use device credentials for all device access.
Related Topics
Understanding Device Properties
You define device properties when you add devices to Security Manager. Device properties are general information about the device, credentials, the group the device is assigned to, and policy overrides. You must provide some device property information, such as device identity and primary credentials, when you add the device, but you can add or edit the properties from the Device Properties dialog box.
To view the device properties, do one of the following in the Device selector:
-
Double-click a device.
-
Right-click a device and select Device Properties.
-
Select a device and select .
The Device Properties dialog box has two panes. The left pane contains a table of contents with these items:
-
General—Contains general information about the device, such as device identity, the operating system running on the device, and device communication settings.
-
Credentials—Contains device primary credentials (username, password, and enable password), SNMP credentials, Rx-Boot Mode credentials, and HTTP credentials.
-
Device Groups—Contains the groups to which the device is assigned.
-
Cluster Information—Contains detailed informatio for the cluster group, if any.
-
Policy Object Overrides—Contains global settings of certain types of reusable policy objects that you can override for this device.
When you select an item in the table of contents, the corresponding information is displayed in the right pane.
Notes
-
Security Manager does not assume that the DNS hostname that appears on the Device Properties page is the same as the hostname that you configured on the device.
-
When you add a device to Security Manager, you must enter either the management IP address or the DNS hostname. Because it is not possible to determine the management interface and, therefore, the management IP address when you discover from a configuration file, the hostname in the configuration file is used as the DNS hostname. If the hostname is missing in the CLI of the configuration file, the configuration filename is used as the DNS hostname.
-
When you discover a device from the network, the DNS hostname in the Device Properties page is not updated with the hostname configured on the device. Therefore, if you want to specify the DNS hostname for the device, you must specify it manually when you add the device to Security Manager or on the Device Properties page.
For more information about device properties, see Viewing or Changing Device Properties.

 Feedback
Feedback