Configure Private Resources
Perform these steps to create the private resources in your organization.
Procedure
|
Step 1 |
In Cisco Security Cloud Control, click . The Secure Access product menu appears in the left navigation bar. |
|
Step 2 |
Click . |
|
Step 3 |
Click +Add. |
|
Step 4 |
Provide a meaningful name for the resource in the Define a Private Resource section. |
|
Step 5 |
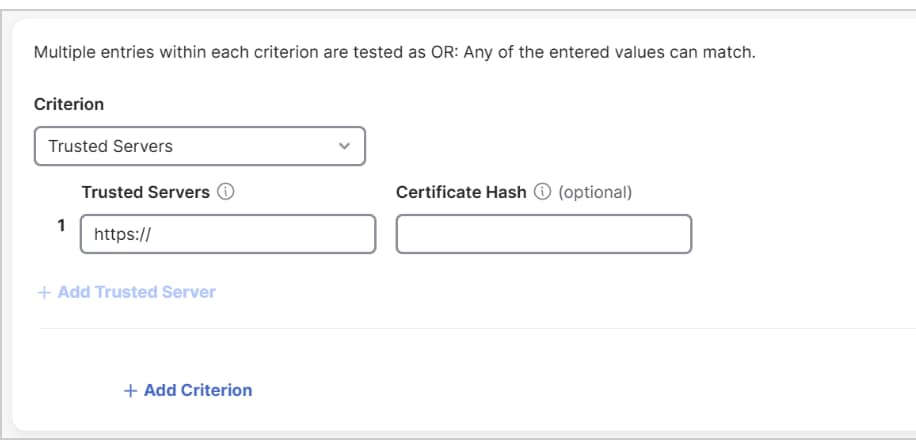
To define how Secure Access can communicate with the resource, provide the network address or the fully qualified domain name (FQDN) of the resource. 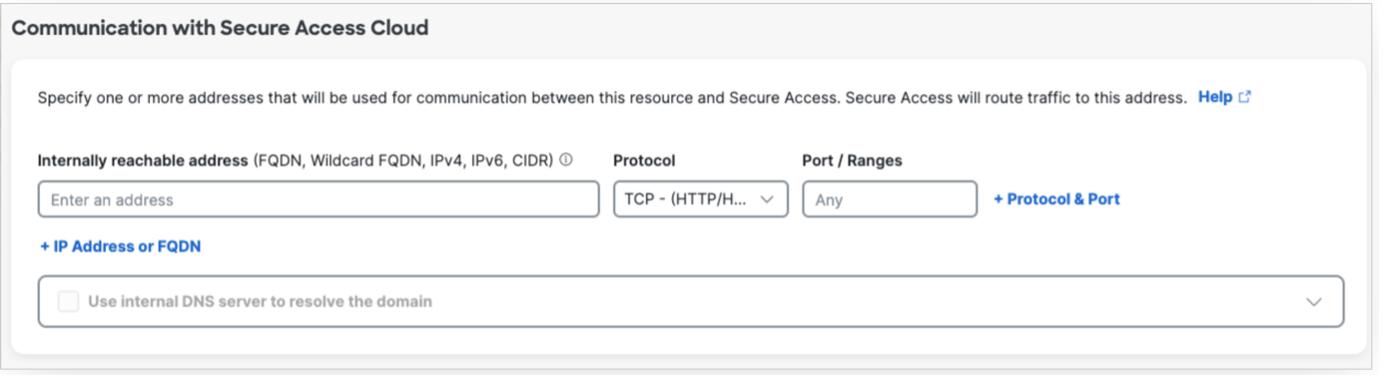 |
|
Step 6 |
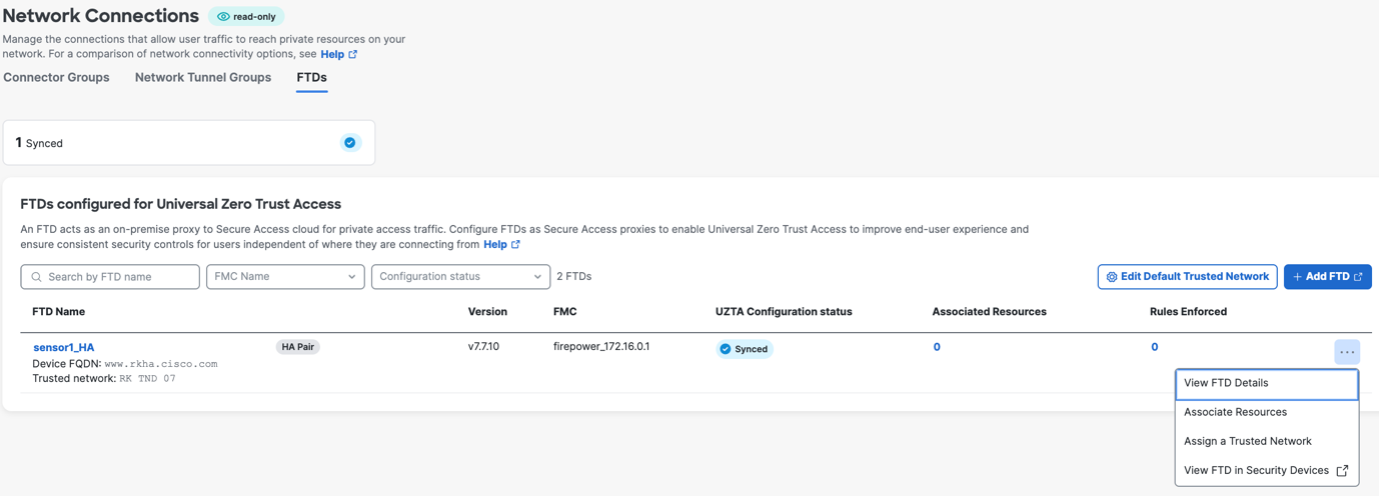
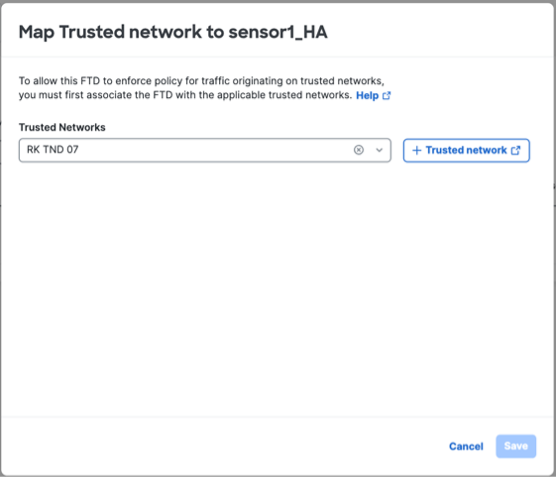
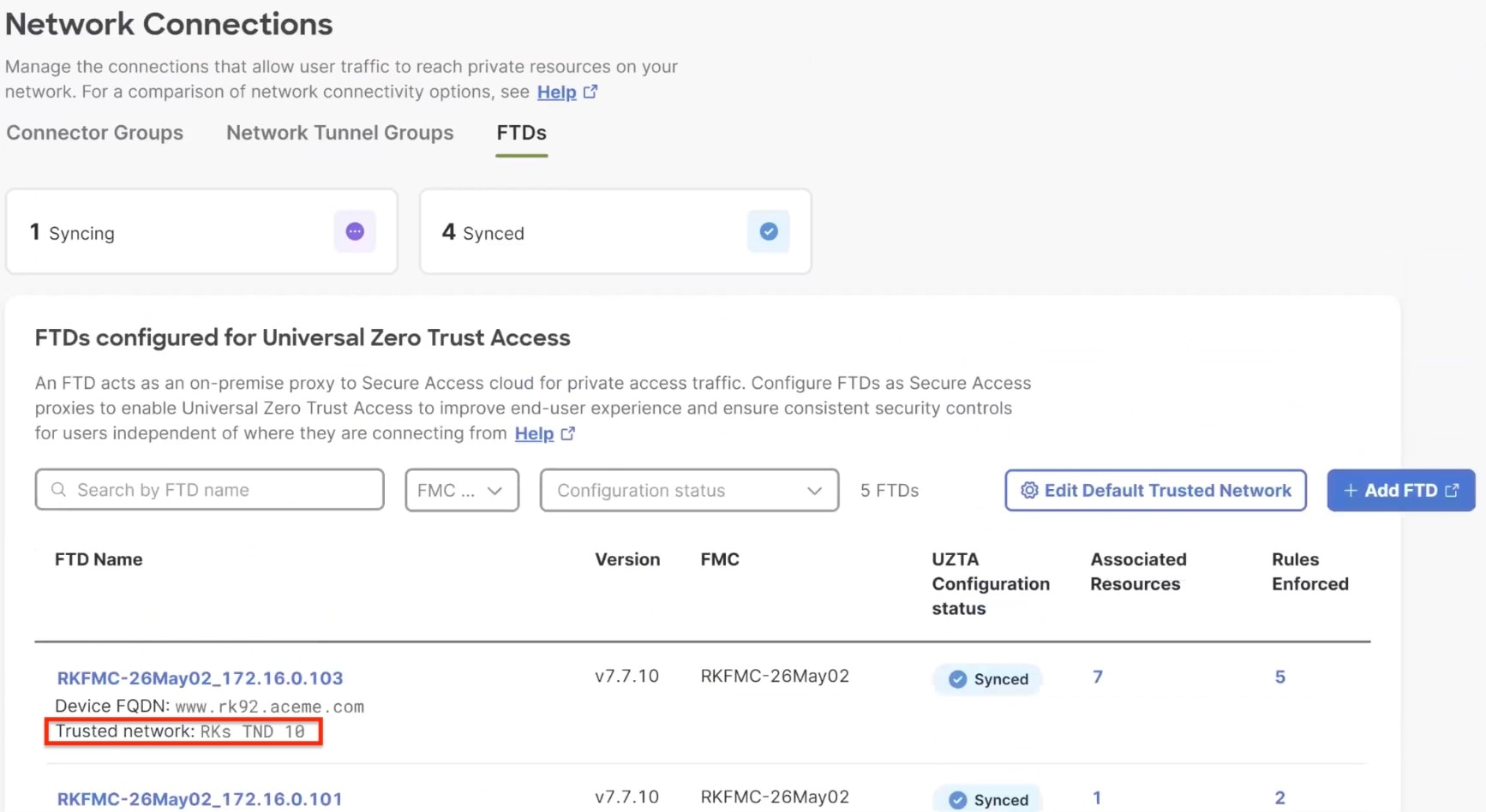
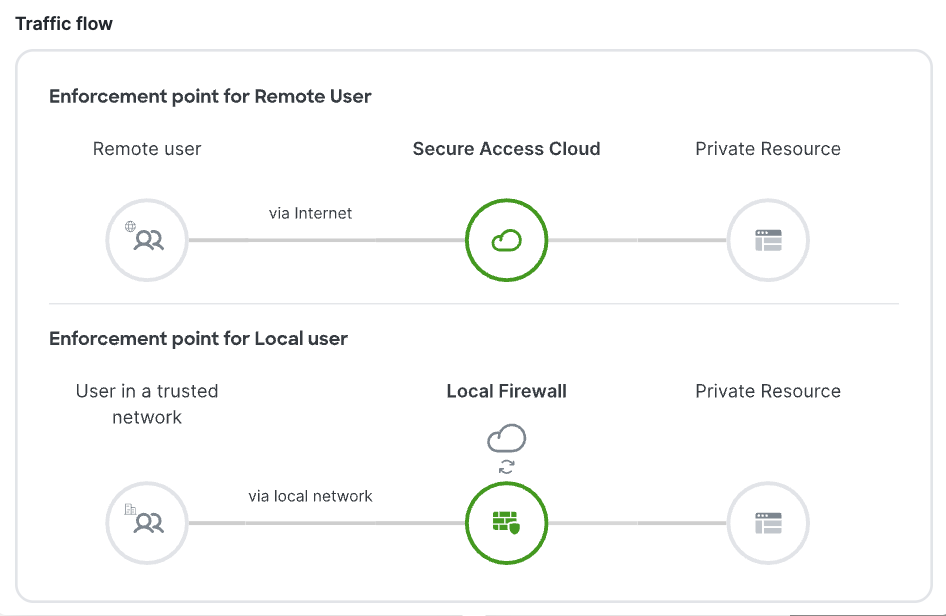
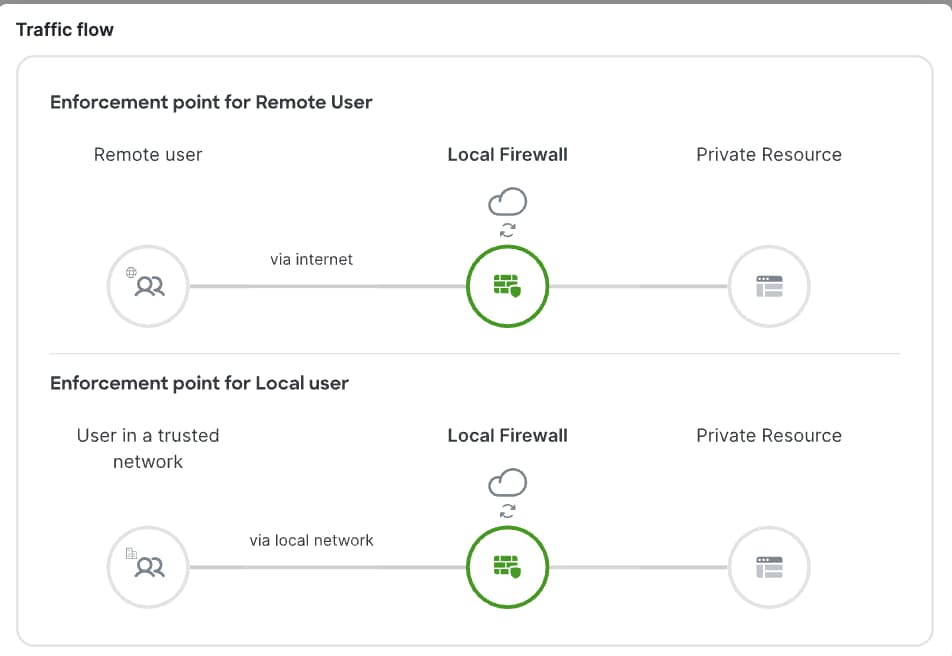
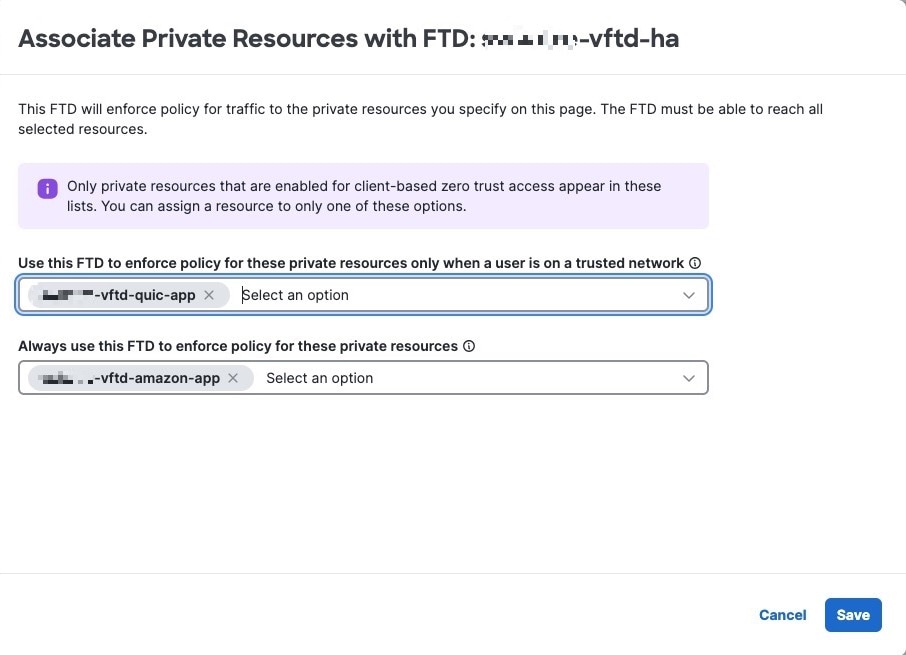
Under Endpoint Connection Methods, choose . This selection allows endpoints with Secure Client to communicate with Secure Access. 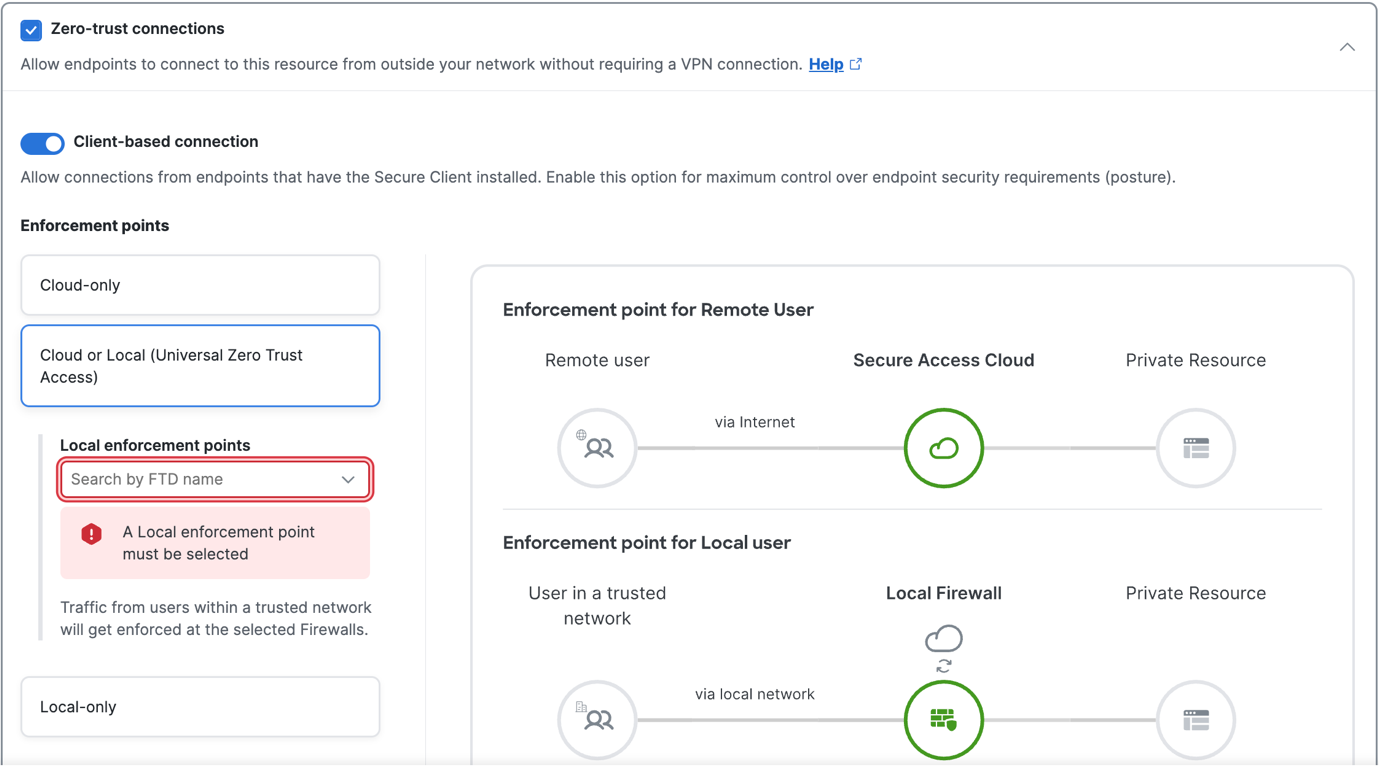 Depending on how you want to enforce traffic flow, choose an appropriate enforcement point.
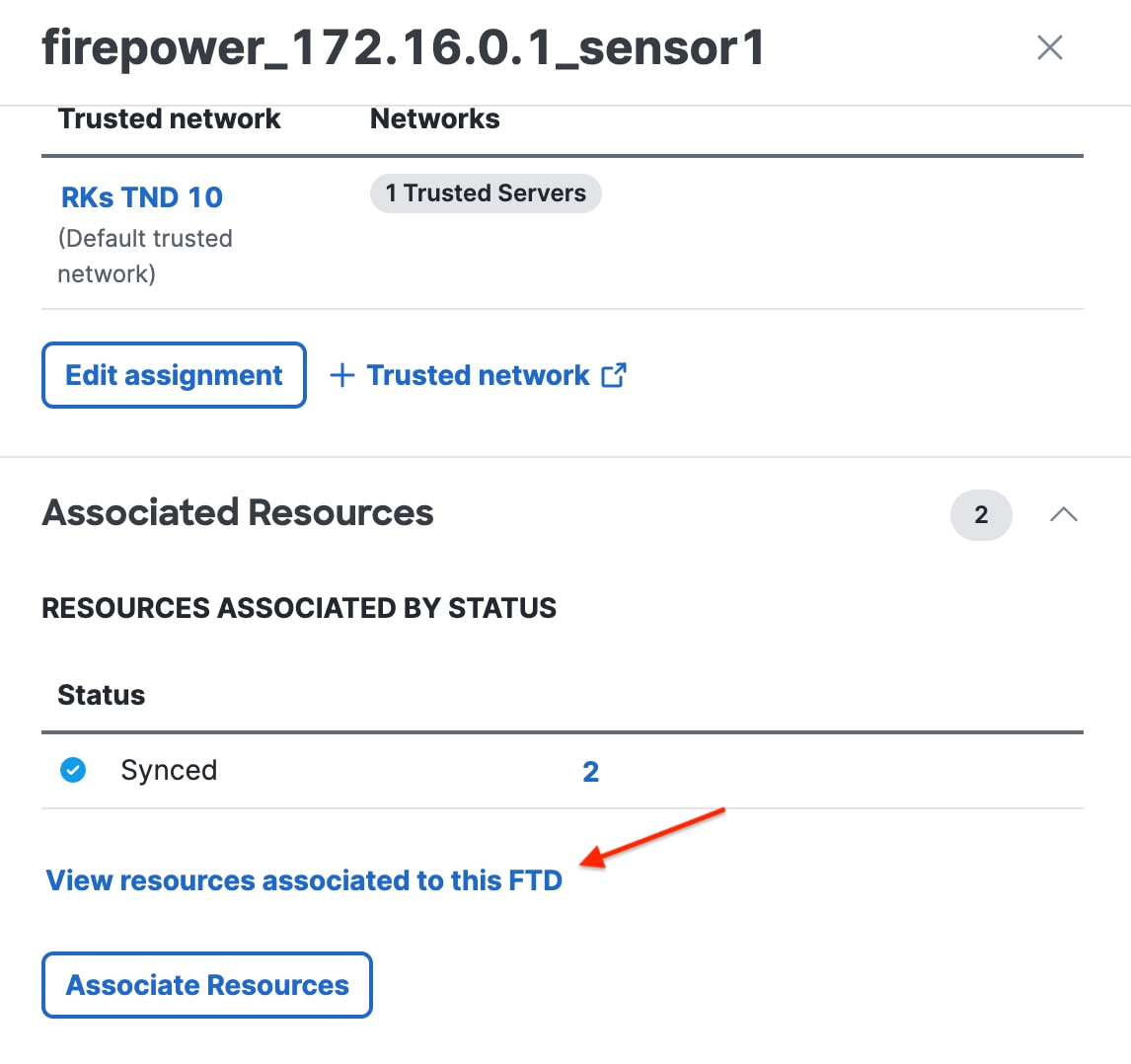
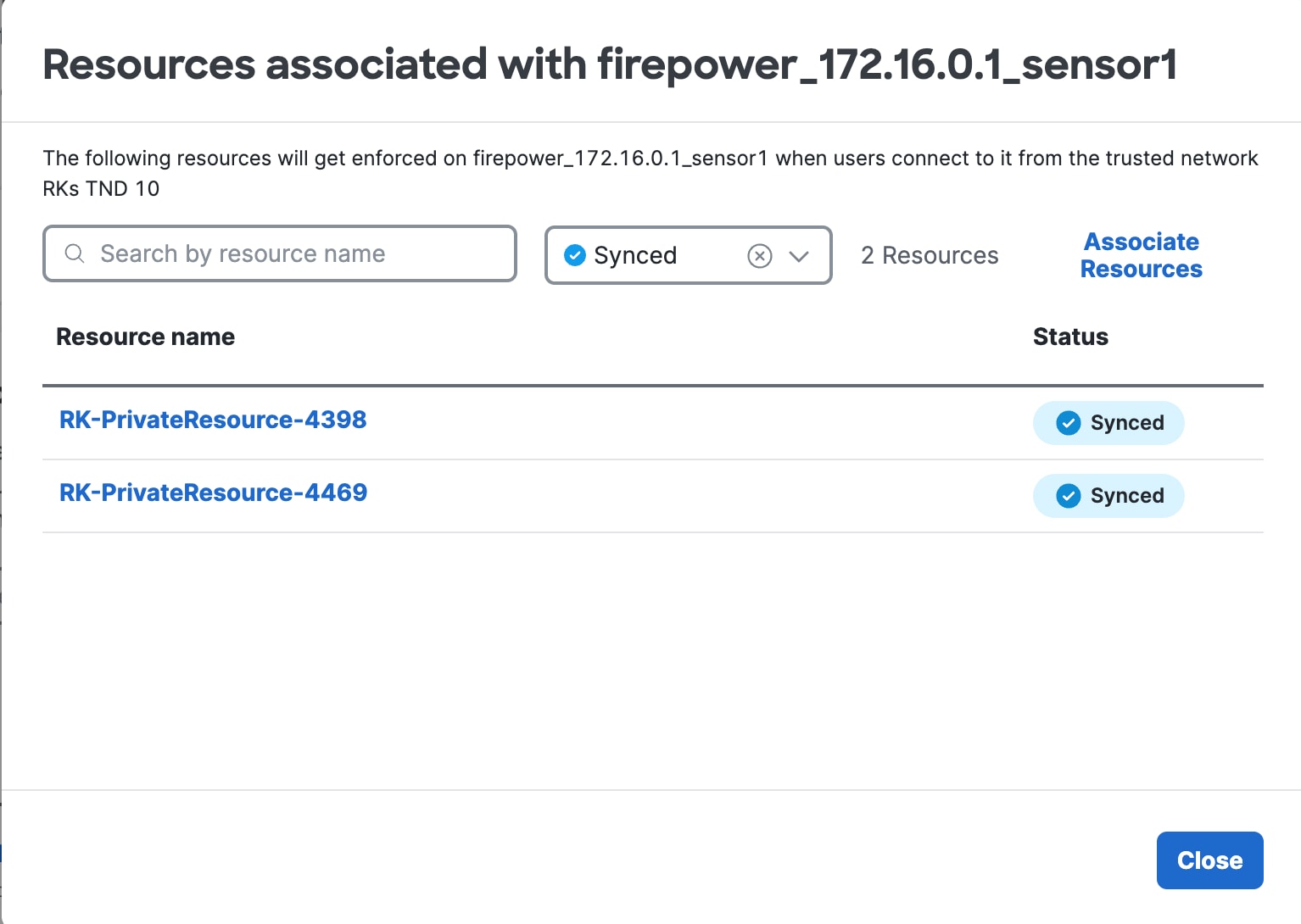
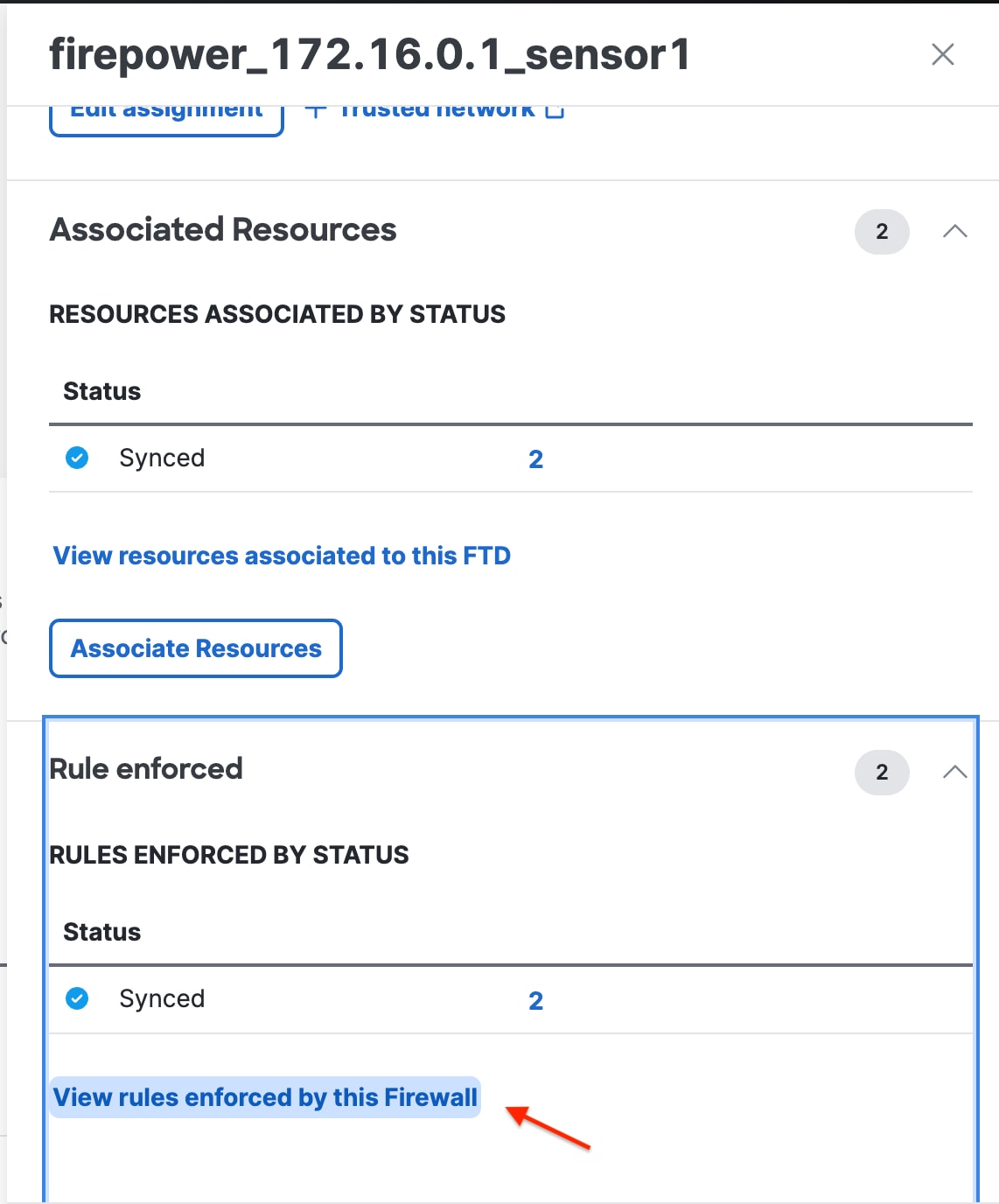
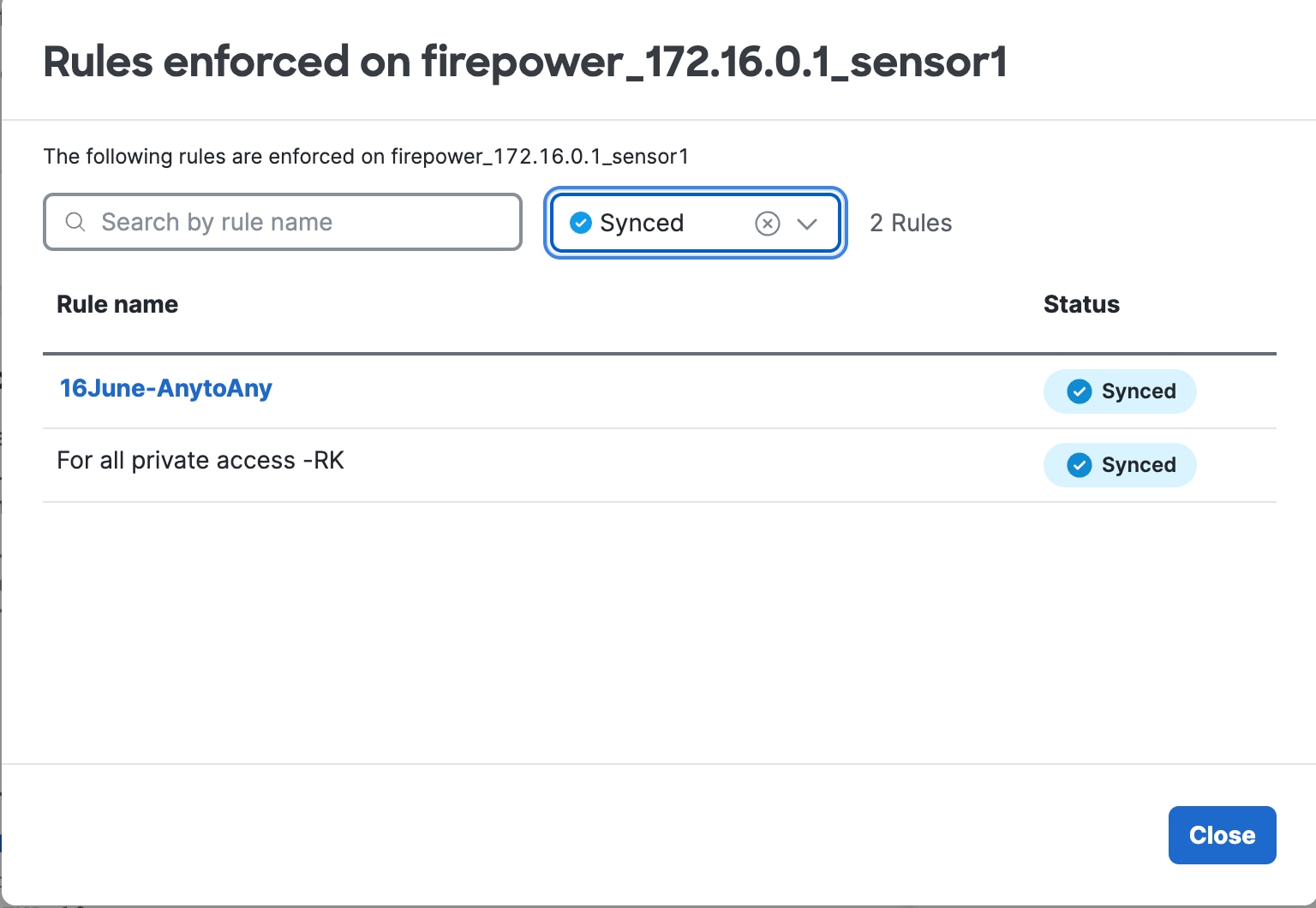
Choose a Threat Defense device from the Local enforcement points drop-down list. All devices that share the same FQDN as the selected device act as the enforcement points. |
|
Step 7 |
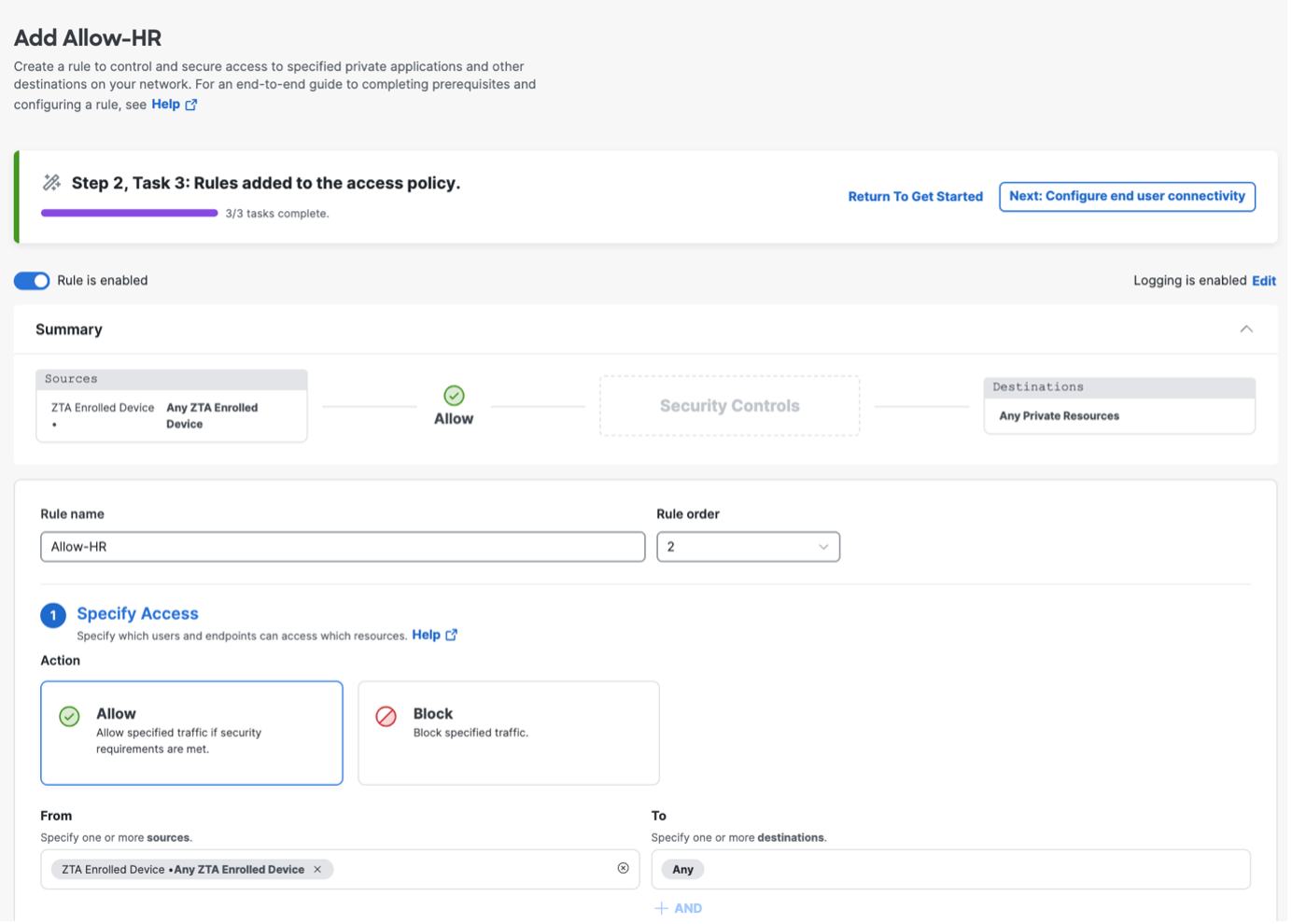
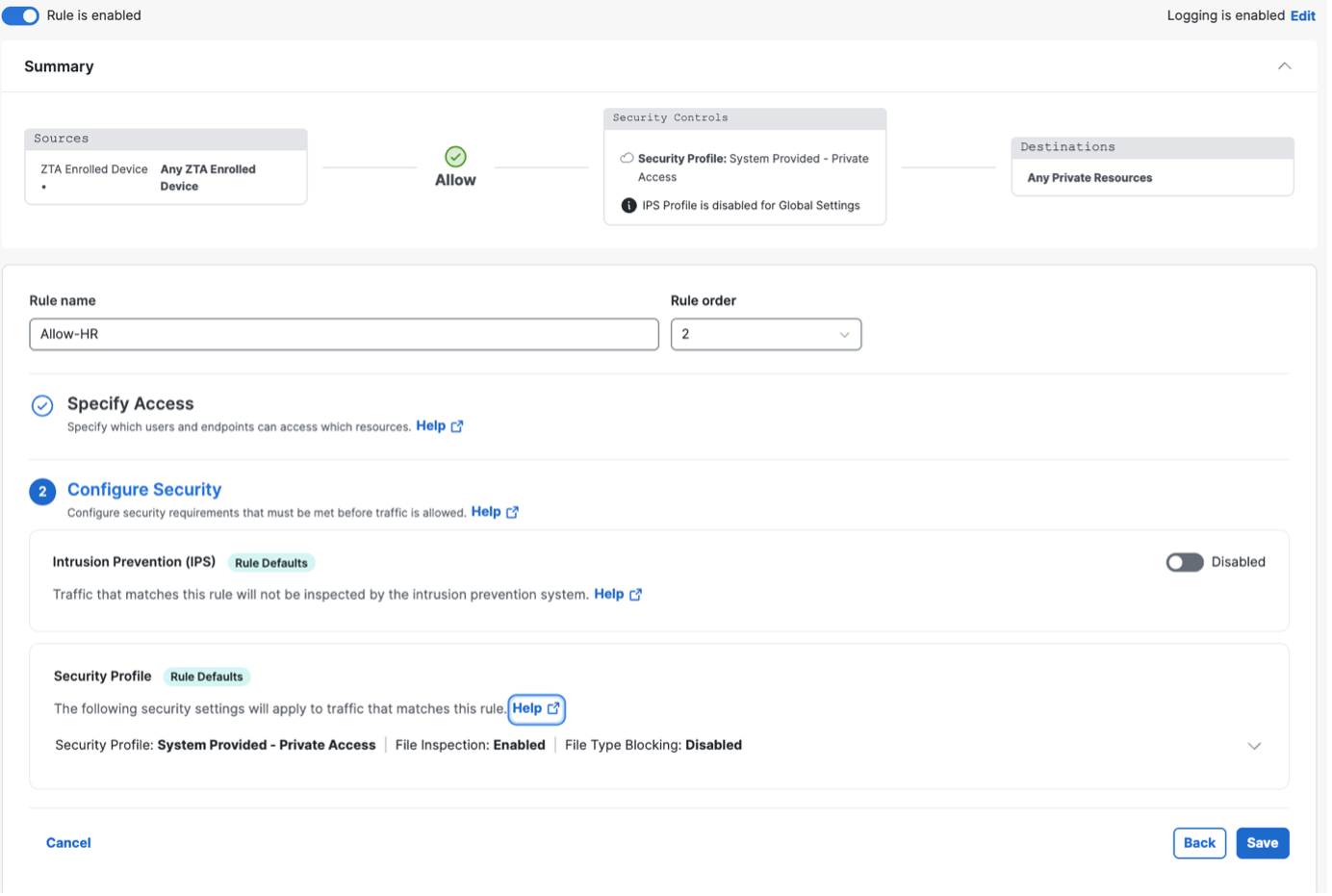
Click Save to save the configuration. Private resources are now added to the network. For more information on managing private resources, refer to Managing Private Resources in the Secure Access documentation. |
 Feedback
Feedback