About the Migration
This chapter discusses how to migrate your configuration and objects from the Cisco ACI Endpoint Update App to the Cisco APIC integration with ASA. Among the reasons to migrate:
-
The Cisco APIC integration with ASA uses the Cisco Secure Dynamic Attributes Connector, which retrieves dynamic objects (that is, network object groups) from Cisco APIC and sends them to ASA.
-
You can add more Cisco APIC-ASA integrations to the dynamic attributes connector at any time.
 Note |
As an alternative to this migration, you can use the Standalone ACI-Endpoint-Update-App. |
To migrate, perform the following tasks:
-
Install the dynamic attributes connector and make sure it, Cisco APIC, and ASA can communicate with each other over the network. The dynamic attributes connector retrieves network object groups from Cisco APIC and pushes them to ASA so all systems must be able to communicate.
See Migration Step 1: Set up the Cisco Secure Dynamic Attributes Connector
-
On Cisco APIC, get the site prefix and update interval from the Cisco ACI Endpoint Update App, disable learning, and choose a user with the appropriate privilege level.
-
On the dynamic attributes connector, create a Cisco APIC connector an ASAadapter.
See Migration Step 3: Configure the Cisco Secure Dynamic Attributes Connector
-
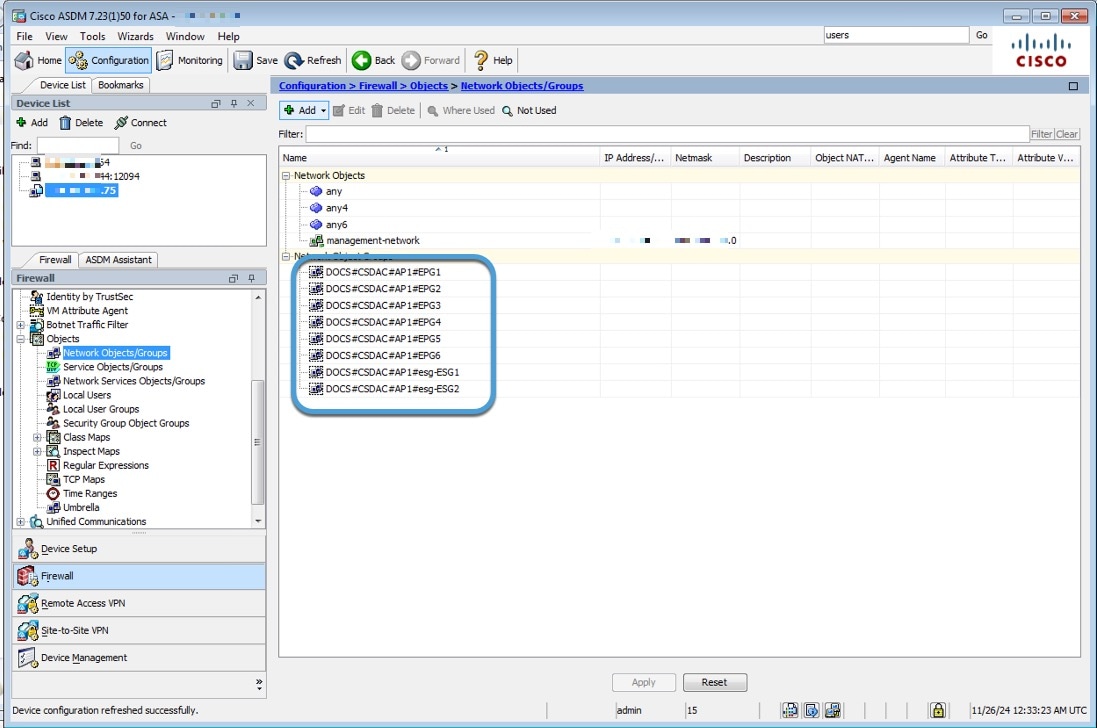
As a final verification step, make sure you see network group objects on the ASA.
See Migration Final Step: Verify Network Object Groups in ASDM
 .
.
 Feedback
Feedback