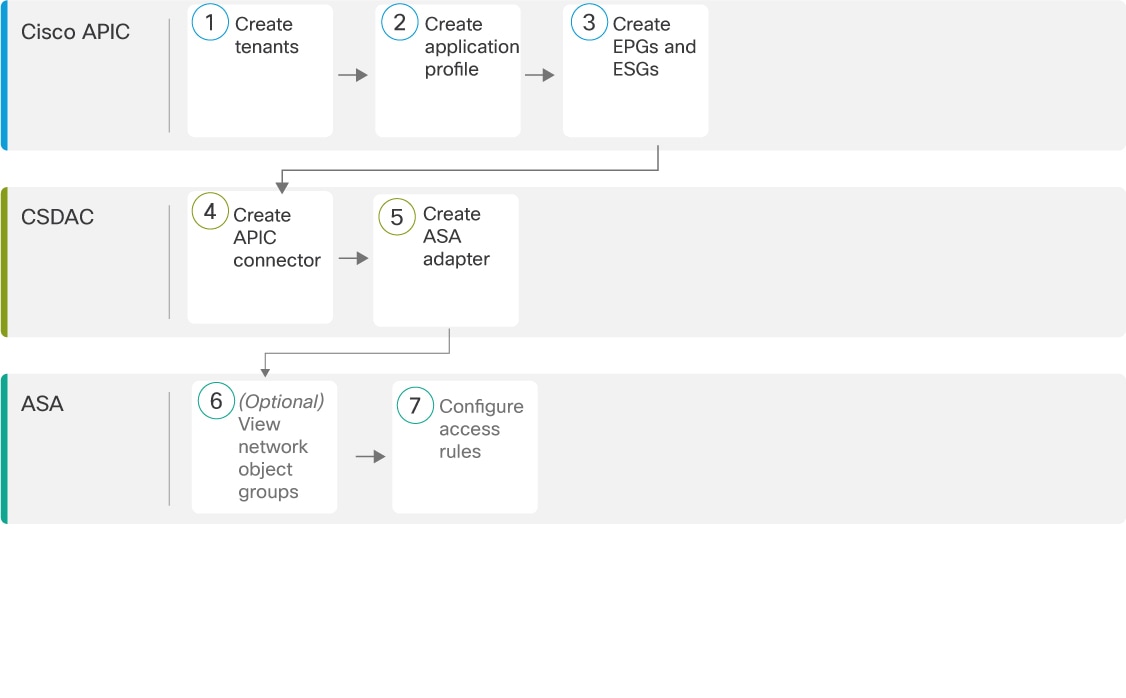
About the Cisco APIC integration with ASA
The dynamic attributes connector enables you to send Cisco APIC dynamic endpoint group (EPG) and endpoint security group (ESG) data from Cisco APIC tenants to . The following figure shows how this works at a high level.
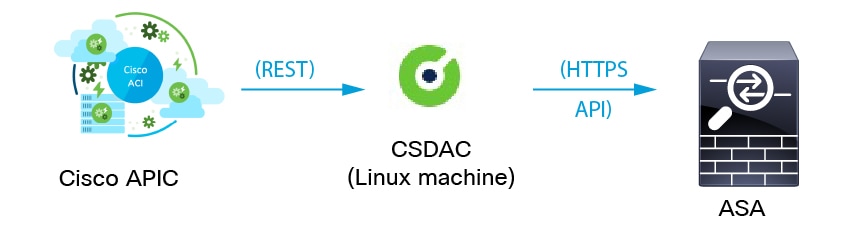
Cisco APIC defines endpoint groups (EPGs) and endpoint security groups (ESGs) that have network object groups. Create a connector in the dynamic attributes connector that pulls that data from Cisco APIC tenants to ASA on which you can use those objects in access control rules. An ASA adapter pushes network object groups in the configured security context.
(You have the option to specify the tenants from which retrieve EPG and ESG objects when you set up the ASA adapter in the dynamic attributes connector. The Cisco APIC user determines which tenants data can be pulled from.)
You can optionally create an empty network object in the ASA CLI under which to create additional network objects sent from Cisco APIC. For more information, see Access Control Lists.
 Note |
ASDM does not support creating empty network objects at this time. |
Sample configuration
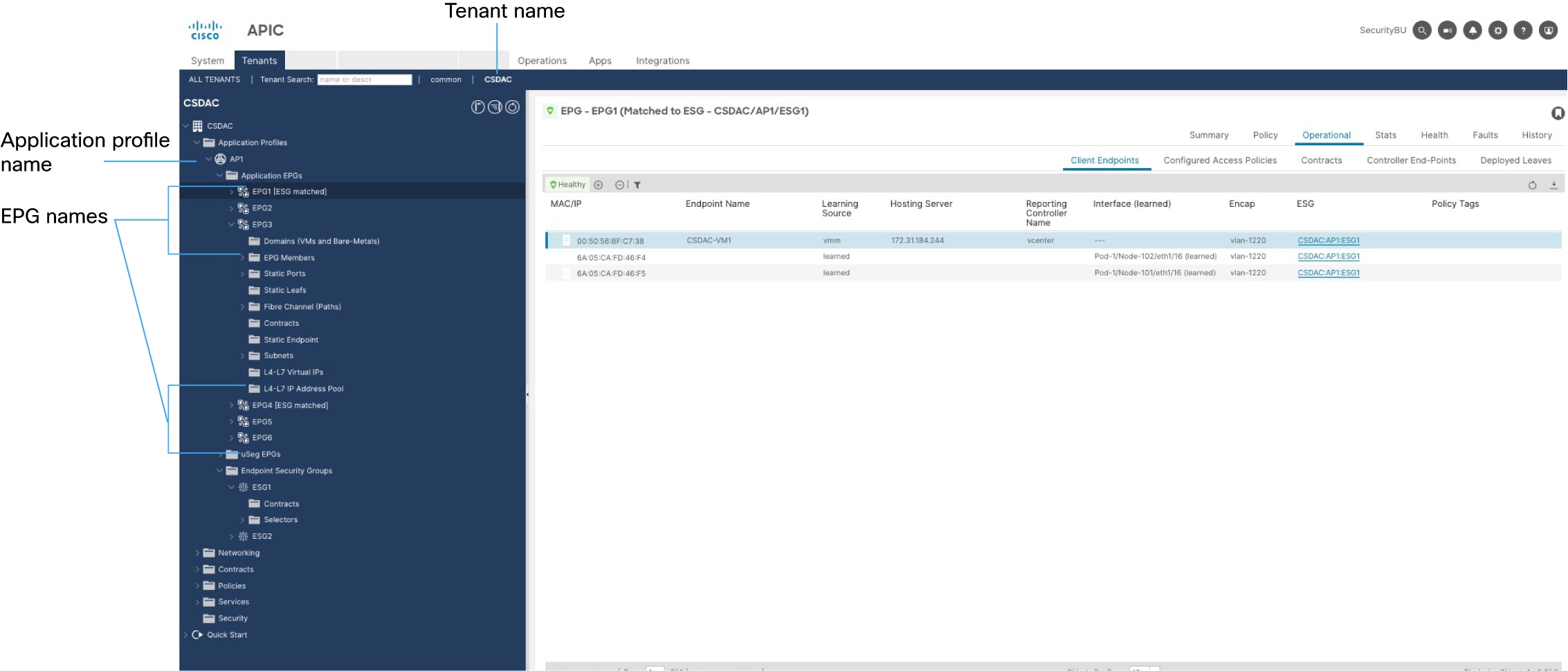
The following sample configuration shows how network object groups are named in ASA based on names in APIC and the APIC connector (not shown).
Network object group names are a concatenation of (in order):
-
Cisco ACI Endpoint Update App Site Prefix value
Cisco APIC tenant name); in this example,
CSDAC. -
Cisco APIC application profile name (in this example,
AP1) -
Cisco APIC EPG name (in this example,
EPG1throughEPG4)
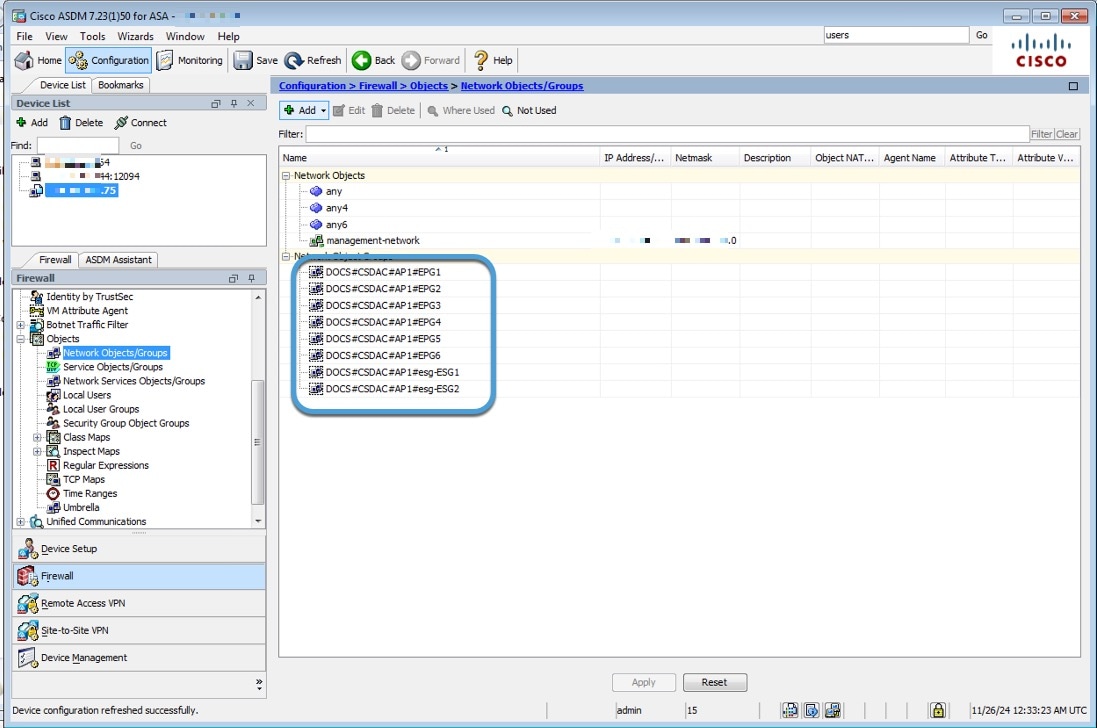
Assuming the connector's Site Prefix is DOCS and the Cisco APIC tenant name the CSDAC user has rights to is CSDAC, network object groups on ASA are named as follows (in ASDM, ):
 Feedback
Feedback