For initial login, use admin as the default user name, and Admin123# as the default password. Immediately after the initial login, the system prompts you to change the default password. You
must set a strong password as per the on-screen instructions to proceed with the application. All other operations are blocked
until default password is changed. API returns 401 unauthorized error if the default password is not reset.
If wan-br or wan2-br have not obtained IP addresses through DHCP, the zero touch deployment is
terminated. To manually apply the IP configurations answer 'y' and the system proceeds
with DHCP assignment on wan-br until the configurations are changed. For DHCP assignment
to continue to request IP address for PnP flow on both WAN interfaces answer 'n'.
You must adhere to the following rules to create a strong password:
-
Must contain at least one upper case and one lower case letter.
-
Must contain at least one number and one special character (# _ - * ?).
-
Must contain seven characters or greater. Length should be between 7 and 128 characters.
You can change the default password in three ways:
-
Using the Cisco Enterprise NFVIS portal.
-
Using the CLI (When you first log into Cisco Enterprise NFVIS through SSH, the system will prompt you to change the password).
-
Using PnP (for details, see the Cisco Network Plug-n-Play Support).
-
Using console (After the initial login using the default password, you are prompted to change the default password).
NFVIS Version: 3.10.0-9
Copyright (c) 2015-2018 by Cisco Systems, Inc.
Cisco, Cisco Systems, and Cisco Systems logo are registered trademarks of Cisco
Systems, Inc. and/or its affiliates in the U.S. and certain other countries.
The copyrights to certain works contained in this software are owned by other
third parties and used and distributed under third party license agreements.
Certain components of this software are licensed under the GNU GPL 2.0, GPL 3.0,
LGPL 2.1, LGPL 3.0 and AGPL 3.0.
nfvis login: console (automatic login)
login:
login:
login:
login:
login: admin
Cisco Network Function Virtualization Infrastructure Software (NFVIS)
NFVIS Version: 3.10.0-9
Copyright (c) 2015-2018 by Cisco Systems, Inc.
Cisco, Cisco Systems, and Cisco Systems logo are registered trademarks of Cisco
Systems, Inc. and/or its affiliates in the U.S. and certain other countries.
The copyrights to certain works contained in this software are owned by other
third parties and used and distributed under third party license agreements.
Certain components of this software are licensed under the GNU GPL 2.0, GPL 3.0,
LGPL 2.1, LGPL 3.0 and AGPL 3.0.
admin@localhost's password:
admin connected from ::1 using ssh on nfvis
nfvis# show version
NFVIS Version: 3.12.3
Copyright (c) 2015-2020 by Cisco Systems, Inc.
Cisco, Cisco Systems, and Cisco Systems logo are registered trademarks of Cisco
Systems, Inc. and/or its affiliates in the U.S. and certain other countries.
The copyrights to certain works contained in this software are owned by other
third parties and used and distributed under third party license agreements.
Certain components of this software are licensed under the GNU GPL 2.0, GPL 3.0,
LGPL 2.1, LGPL 3.0 and AGPL 3.0.
login: admin
NFVIS service is OK
Warning: Permanently added 'localhost' (RSA) to the list of known hosts.
admin@localhost's password:
Cisco Network Function Virtualization Infrastructure Software (NFVIS)
NFVIS Version: 3.12.3-RC8
Copyright (c) 2015-2020 by Cisco Systems, Inc.
Cisco, Cisco Systems, and Cisco Systems logo are registered trademarks of Cisco
Systems, Inc. and/or its affiliates in the U.S. and certain other countries.
The copyrights to certain works contained in this software are owned by other
third parties and used and distributed under third party license agreements.
Certain components of this software are licensed under the GNU GPL 2.0, GPL 3.0,
LGPL 2.1, LGPL 3.0 and AGPL 3.0.
admin connected from ::1 using ssh on nfvis
admin logged with default credentials
Setting admin password will disable zero touch deployment behaviors.
Do you wish to proceed? [y or n]y
Please provide a password which satisfies the following criteria:
1.At least one lowercase character
2.At least one uppercase character
3.At least one number
4.At least one special character from # _ - * ?
5.Length should be between 7 and 128 characters
Please reset the password :
Please reenter the password :
Resetting admin password
New admin password is set
nfvis#
System message at 2020-01-08 03:10:10...
Commit performed by system via system using system.
nfvis#

Note
|
To commit the target configuration to the active (running) configuration, use the
commit command in any configuration mode. Changes made during a
configuration session are inactive until the commit command is entered. By
default, the commit operation is pseudo-atomic, meaning that all changes must
succeed for the entire commit operation to succeed.
|
Connect to the System
Using IPv4
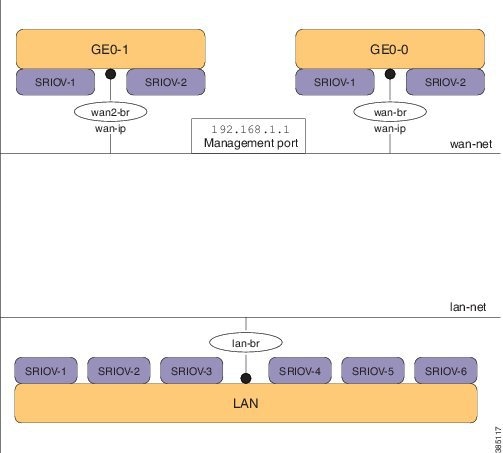
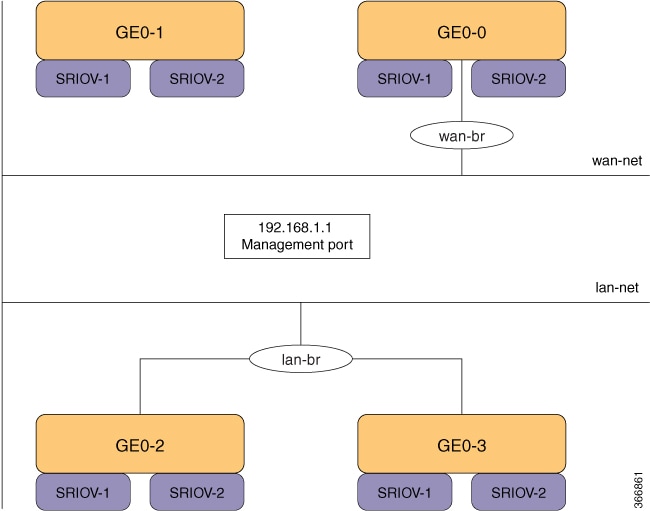
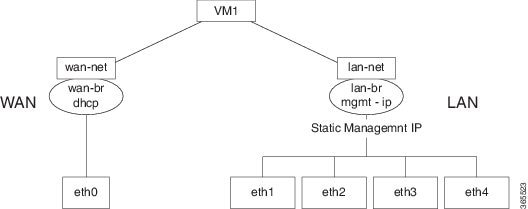
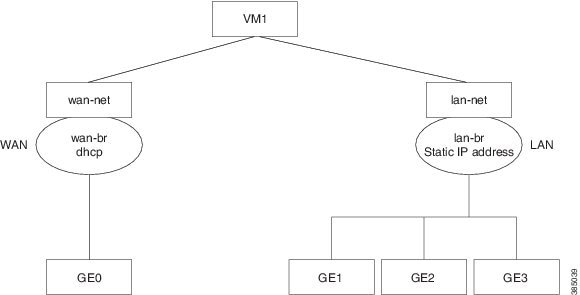
The three interfaces that connect the user to the system are the WAN and WAN2 interfaces and the management interface. By
default, the WAN interface has DHCP configuration and the management interface is configured with a static IP address of 192.168.1.1.
If the system has a DHCP server connected to the WAN interface, the WAN interface is assigned an IP address from this server.
You can use this IP address to connect to the system.
You can connect to the server locally (with an Ethernet cable) using the static management IP address. However, to be able
to use a static IP address to remotely connect to a server, the default gateway needs to be configured first.
You can connect to the system in the following ways:
-
Using the local portal—After the initial login, you are prompted to change the default password.
-
Using the KVM console—After the initial login using the default password, you are prompted to change the default password.
-
Using PnP—After the initial provisioning through PnP, the configuration file pushed by the PNP server must include the new
password for the default user (admin).
Using IPv6
IPv6 can be configured in static, DHCP stateful and Stateless Autoconfiguration (SLAAC) mode. By default, DHCP IPv6 stateful
is configured on the WAN interface. If DHCP stateful is not enabled on the network, the router advertisement (RA) flag decides
which state the network stays in. If the RA shows the Managed (M) flag, then the network stays in DHCP mode, even if there
is no DHCP server in the network. If the RA shows the Other (O) flag, then the network switches from DHCP server to SLAAC
mode.
SLAAC provides IPv6 address and default gateway. Stateless DHCP is enabled in the SLAAC mode.
If the server has DNS and domain configured, then SLAAC also provides those values
via stateless DHCP.
Perform Static Configuration without DHCP

Note
|
Starting from NFVIS 3.10.1 release, for ENCS 5400 and ENCS 5100, wan2-br obtains an IP address from DHCP. To configure default
gateway, first use the no bridges bridge wan2-br dhcp command.
|
If you want to disable DHCP and use static configuration, you need to perform the initial configuration by setting the WAN
IP address and/or management IP address, and the default gateway. You can also configure a static IP on a created bridge.
To perform initial configuration on the system without using DHCP:
configure terminal
system settings mgmt ip address 192.168.1.2 255.255.255.0
bridges bridge wan-br ip address 209.165.201.22 255.255.255.0
system settings default-gw 209.165.201.1
commit

Note
|
When an interface is configured with a static IP address, DHCP is automatically disabled on that interface.
|
Now you can either use the management IP or WAN IP to access the portal.
To configure static IPv6 on the WAN interface:
configure terminal
system settings mgmt ipv6 address 2001:DB8:1:1::72/64
bridges bridge wan-br ipv6 address 2001:DB8:1:1::75/64
system settings default-gw-ipv6 2001:DB8:1:1::76
commit

Note
|
When an interface is configured with a static IPv6 address, DHCP IPv6 is automatically disabled on that interface. There are
three options for IPv6 - static, DHCP and SLAAC, out of which only one can be enabled at a time.
Secure overlay is not supported when WAN interface is configured with IPv6.
|
To configure DHCP on the WAN interface:
configure terminal
no system settings default-gw
system settings wan dhcp
commit
exit
hostaction wan-dhcp-renew

Note
|
Starting from NFVIS 3.10.1, you can configure DHCP IPv6 on any bridge. You can only have one DHCP IPv6 bridge or management
interface active at a time. You cannot have DHCP IPv6 and default IPv6 gateway or SLAAC IPv6 configured at the same time.
|
To configure DHCP IPv6 on the WAN interface:
configure terminal
no system settings default-gw-ipv6
system settings wan dhcp-ipv6
commit
exit
hostaction wan-dhcp-renew
Verify Initial Configuration
Use the show system settings-native command to verify initial configuration. Use show bridge-settings and show bridge-settings
bridge_name commands to verify the configuration for any bridge on the system.
Here is an extract from the output of the show system settings-native command when both WAN and management interfaces have a static configuration:
system settings-native mgmt ip-info interface lan-br
system settings-native mgmt ip-info ipv4_address 192.168.1.2
system settings-native mgmt ip-info netmask 255.255.255.0
!
!
!
system settings-native mgmt dhcp disabled
system settings-native wan ip-info interface wan-br
system settings-native wan ip-info ipv4_address 209.165.201.22
system settings-native wan ip-info netmask 255.255.255.0
!
!
!
system settings-native wan dhcp disabled
!
!
system settings-native gateway ipv4_address 209.165.201.1
system settings-native gateway interface wan-br
Here is an extract from the output of the show system settings-native command when the management interface has a DHCP configuration and the WAN interface has a static configuration:
system settings-native mgmt ip-info interface MGMT
system settings-native mgmt ip-info ipv4_address 192.168.1.2
system settings-native mgmt ip-info netmask 255.255.255.0
!
!
!
system settings-native mgmt dhcp enabled
system settings-native wan ip-info interface wan-br
system settings-native wan ip-info ipv4_address 209.165.201.22
system settings-native wan ip-info netmask 255.255.255.0
!
!
!
system settings-native wan dhcp disabled
Here is an extract from the output of the show system settings-native command when the WAN interface has a DHCP configuration and the management interface has a static configuration:
system settings-native mgmt ip-info interface lan-br
system settings-native mgmt ip-info ipv4_address 209.165.201.2
system settings-native mgmt ip-info netmask 255.255.255.0
!
!
!
system settings-native mgmt dhcp disabled
system settings-native wan ip-info interface wan-br
system settings-native wan ip-info ipv4_address 209.165.201.22
system settings-native wan ip-info netmask 255.255.255.0
!
!
!
system settings-native wan dhcp enabled


 Feedback
Feedback