Scenario B: Traffic Monitoring With NetFlow and sFlow
In this particular situation, the enterprise has implemented network traffic monitoring protocols such as NetFlow or sFlow.
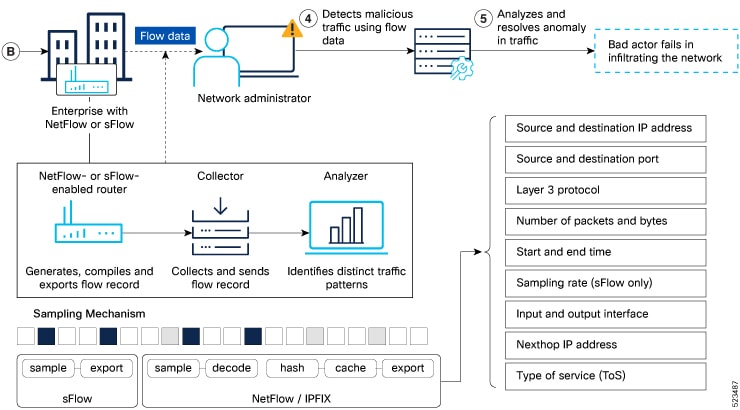
Here is a high-level outline of the network's response to the attack:
-
Flow data collection—Routers enabled with NetFlow or sFlow capture and retain flow records of transmitted traffic. These records store essential metadata related to the traffic's journey, including source and destination domains, the count and volume of inbound and outbound packets, timestamps and so on. The recorded flow records are then sent to a designated collector.
-
Data analysis—Utilize a NetFlow or sFlow analyzer or security monitoring tool to process and analyze the collected data. The tool can identify patterns and anomalies that may indicate a security threat, such as unusual traffic patterns, unexpected communication between hosts, or a high volume of traffic from suspicious sources.
-
Threat detection—The analyzer applies algorithms and rules to detect potential threats based on the analyzed data. It can compare network traffic with predefined security policies. If a potential threat is detected, the analyzer generates an alert. This alert can be sent to the network administrator for further investigation.
-
Prompt investigation and responsive action—Upon receiving the alert, the network administrator can investigate the identified threat. They can analyze additional logs, inspect packet captures, or perform other security measures to gather more information about the threat. Once the threat is confirmed, appropriate actions can be taken to mitigate the impact by blocking the malicious IP addresses and isolating affected hosts to prevent further harm.
By leveraging NetFlow and sFlow for threat identification, you can proactively detect and respond to security threats, enhancing the overall network security posture. It allows for early threat detection, and faster incident response, ultimately reducing the risk of a successful attack.
 Feedback
Feedback