802.1X port-based authentication
The 802.1X port-based authentication is a type of authentication that enables port-based network access control as defined by the IEEE 802.1X standard that
-
operates at the Layer 2 and prevents an unauthorized network device from connecting to a network via LAN ports,
-
uses a client-server model to authenticate a client network device (hereafter referred to as client) before allowing it access to a network, and
-
controls port access, ensuring the port-interface blocks all traffic to and from a client until it is successfully authenticated.
In 802.1X port-based authentication, the client-server model involves a client device requesting network access by communicating with an authentication server, typically a Remote Authentication Dial-In User Service (RADIUS) server. The client sends its credentials, which the server verifies against authorized user databases. Upon successful authentication, the server permits network access, ensuring only authorized devices can connect.
This chapter describes how to configure IEEE 802.1X port-based authentication in Cisco 8000 series routers to prevent unauthorized network devices from gaining access to the network.
Supported protocols for 802.1X port-based authentication
802.1X port-based authentication supports these protocols for secure and reliable network access:
-
EAP —Extensible Authentication Protocol (EAP) is a flexible authentication framework that supports multiple authentication methods, allowing network devices to negotiate the most appropriate protocol for secure communications.
-
EAP-TLS—Extensible Authentication Protocol with Transport Layer Security (EAP-TLS) is an authentication protocol that leverages TLS to provide robust encryption and mutual authentication, ensuring secure and private communication between the client and server during the authentication process.
-
EAPOL—Extensible Authentication Protocol over LAN (EAPOL) is a network protocol used in the IEEE 802.1X standard, facilitating the exchange of EAP packets over wired or wireless LANs, enabling secure port-based network access control.
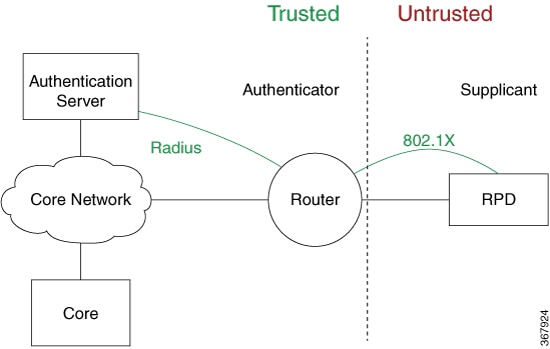
IEEE 802.1X Device Roles
Devices in the network have specific roles in IEEE 802.1X authentication:
-
Authenticator—A router that facilitates authentication for other network devices or clients on the same LAN.
-
Supplicant—A network device or client that seeks authentication from an authenticator on a point-to-point LAN segment.
-
Authentication server—A RADUIS server that verifies client credentials and authorizes network access through the authenticator.
802.1X host modes
The 802.1X host modes table describes the two host modes supported by 802.1X.
For information on how to configure the host modes, refer to Configure 802.1X host-modes.
|
Host modes |
Description |
|---|---|
|
Single-host |
While in this mode, the port allows a single host or client to be authenticated and allows only ingress traffic from the authenticated peer. A security violation is detected if more than one client is present. |
|
Multi-auth |
This is the default host mode. While in this mode, multiple hosts can independently authenticate through the same port and ingress traffic is allowed from all authenticated peers. The router can support up to 20 clients using the 802.1X protocol in multi-authentication mode. |
Prerequisites for 802.1X Port-Based Authentication
Prerequisites for 802.1X port-based authentication are:
-
K9sec RPM is required to enable this feature.
-
Ensure that both RADIUS/EAP-server and supplicant are configured with supported EAP methods when remote authentication is used.
-
If the device is used as a local EAP server, only EAP-TLS method is supported.
-
Ensure that a Certificate Authority (CA) server is configured for the network with a valid certificate.
-
Ensure that the supplicant, authenticator, and CA server are synchronized using Network Time Protocol (NTP). If time is not synchronized on all these devices, certificates may not be validated.

 Feedback
Feedback