-
Cisco MDS 9000 Family Configuration Guide, Release 1.3 (from Release 1.3(1) through Release 1.3(6))
-
New and Changed Information
-
Index
-
Preface
-
Product Overview
-
Before You Begin
-
Obtaining and Installing Licenses
-
Initial Configuration
-
Configuring High Availability
-
Software Images
-
Managing Modules
-
Managing System Hardware
-
Configuring and Managing VSANs
-
Configuring Interfaces
-
Configuring Trunking
-
Configuring PortChannels\r\n
-
Configuring and Managing Zones
-
Configuring Inter-VSAN Routing
-
Managing FLOGI, Name Server, FDMI, and RSCN Databases
-
Configuring Switch Security
-
Configuring Fabric Security
-
Configuring Port Security
-
Configuring Fibre Channel Routing Services and Protocols
-
Configuring IP Services
-
Configuring FICON
-
Configuring IP Storage
-
Configuring Call Home
-
Configuring Domain Parameters
-
Configuring Traffic Management
-
Configuring System Message Logging
-
Discovering SCSI Targets
-
Monitoring Network Traffic Using SPAN
-
Advanced Features and Concepts
-
Configuring Fabric Configuration Servers
-
Monitoring System Processes and Logs
-
Table Of Contents
Configuring the Management Interface
Configuring the Default Gateway
Configuring the Default Network
IP-ACL Configuration Guidelines
Adding filters to an Existing IP-ACL
Removing Entries from an Existing IP-ACL
IP-ACL Configuration Verification
Configuring an IP Address in a VSAN
Displaying IP Interface Information
Creating or Removing a Virtual Router
Adding an IP Address for a Virtual Router
Setting Priority for the Virtual Router
Setting the Time Interval for the Advertisement Packet
Preempting the Master Virtual Router
Configuring Authentication for the Virtual Router
Setting the Priority Based on Interface State
Displaying DNS Host Information
Configuring IP Services
Cisco MDS 9000 Family switches can route IP traffic between Ethernet and Fibre Channel interfaces. The IP static routing feature is used to route traffic between VSANs. To do so, each VSAN must be in a different IP subnetwork. Each Cisco MDS 9000 Family switch provides the following services for network management systems (NMS):
•
IP forwarding on the out-of-band Ethernet interface (mgmt0) on the front panel of the supervisor modules.
•
IP forwarding or in-band Fibre Channel interface using the IP over Fibre Channel (IPFC) function—IPFC specifies how IP frames can be transported over Fibre Channel using encapsulation techniques. IP frames are encapsulated into Fibre Channel frames so NMS information can cross the Fibre Channel network without using an overlay Ethernet network.
•
IP routing (default routing and static routing)—If your configuration does not need an external router, you can configure a default route using static routing.
Switches are compliant with RFC 2338 standards for Virtual Router Redundancy Protocol (VRRP) features. VRRP is a restartable application that provides a redundant, alternate path to the gateway switch.
This chapter includes the following sections:
•
Configuring the Management Interface
•
Configuring the Default Gateway
•
Configuring the Default Network
•
Displaying IP Interface Information
Traffic Management Services
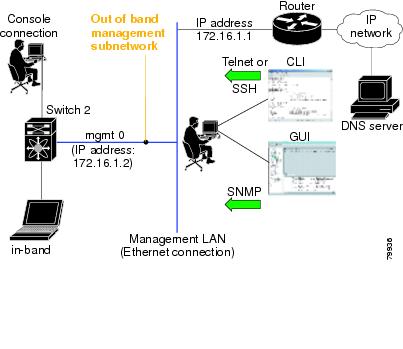
In-band options are compliant with and use the RFC 2625 standards. An NMS host running IP protocol over a FC interface can access the switch using the IPFC functionality. If the NMS does not have a Fibre Channel HBA, in-band management can still be performed using one of the switches as an access point to the fabric (see Figure 20-1).
Figure 20-1 Management Access to Switches
Configuring the Management Interface
On director class switches, a single IP address is used to manage the switch. The active supervisor module's management (mgmt0) interface uses this IP address. The mgmt0 interface on the standby supervisor module remains in an inactive state and cannot be accessed until a switchover happens. After a switchover, the mgmt0 interface on the standby supervisor module becomes active and assumes the same IP address as the previously-active supervisor module.
The management interface on the switch allows multiple simultaneous Telnet or SNMP sessions. You can remotely configure the switch through the management interface, but first you must configure some IP parameters (IP address, subnet mask) so that the switch is reachable. You can manually configure the management interface from the CLI.
Note
Before you begin to configure the management interface manually, obtain the switch's IP address and IP subnet mask. Also make sure the console cable is connected to the console port.
To configure the mgmt0 Ethernet interface, follow these steps:
Configuring the Default Gateway
Use the IP default-gateway command to configure the IP address for a switch's default gateway. This IP address should be configured along with the IP static routing commands (IP default-network, destination prefix, and destination mask, and next hop address).
Tip
If you configure the static route IP forwarding and the default-network details, these IP addresses will be used regardless of the default-gateway being enabled or disabled. If these IP addresses are configured but not available, the switch will fall back to using the default gateway IP address, if you have configured it. Be sure to configure IP addresses for all entries in the switch (see the "Initial Setup Routine" section).
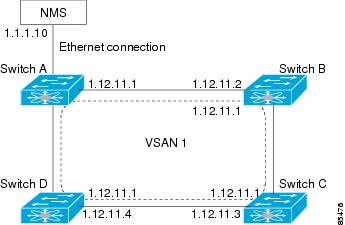
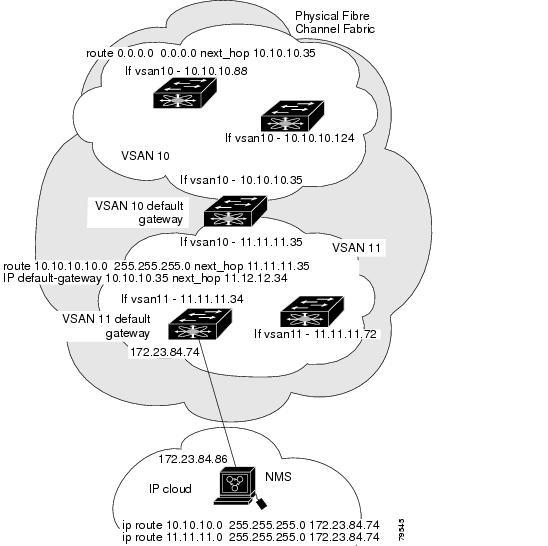
When the Ethernet interface is configured, the switch should point to the gateway router for the IP network. The host accesses the gateway using a gateway switch. This gateway switch is configured as the default gateway. The other switches in the fabric that are connected to the same VSAN as the gateway switch can also be connected through the gateway switch. Every interface connected to this VSAN should be configured with the VSAN IP address of the gateway switch (see Figure 20-2).
Figure 20-2 Overlay VSAN Functionality
In Figure 20-2, switch A has the IP address 1.12.11.1, switch B has the IP address 1.12.11.2, switch C has the IP address 1.12.11.3, and switch D has the IP address 1.12.11.4. Switch A is the gateway switch with the Ethernet connection. The NMS uses the IP address 1.1.1.10 to connect to the gateway switch. Frames forwarded to any switch in the overlaid VSAN 1 are routed through the gateway switch. Configuring the gateway switch's IP address, 1.12.11.1, in the other switches enable the gateway switch to forward the frame to the intended destination. Similarly, if a non-gateway switch in the VSAN forwards a frame to the Ethernet world, the frame is routed through the gateway switch.
When forwarding is disabled (default), IP frames are not sent from one interface to another. In these cases, the software performs local IP routing between two switches using the in-band option for Fibre Channel traffic and the mgmt0 option for Ethernet traffic.
When a VSAN is created, a VSAN interface is not created automatically. You need to specifically create the interface (see the "Configuring VSAN Interfaces" section).
To configure default gateways, follow these steps:
Step 1
Enters configuration mode.
Step 2
switch(config)# ip default-gateway 1.12.11.1switch(config)#Configures the IP address for the default gateway (1.12.11.1).
Use the show ip route command to verify that the IP address for the default gateway is configured.
Configuring the Default Network
Unlike the ip default-gateway command, use the ip default-network command when IP routing is enabled on the switch. If you assign the IP default network address, the switch considers routes to that network as the last resort. If the IP default network address is not available, the switch uses the IP default gateway address. For every network configured with the IP default network address, the switch flags that route as a candidate default route, if the route is available.
Tip
If you configure the static route IP forwarding and the default network details, these IP addresses will be used regardless of the default gateway being enabled or disabled. If these IP address are configured and not available, the switch will fall back to using the default gateway IP address, if you have configured it. Be sure to configure IP addresses for all entries in the switch (see the "Initial Setup Routine" section).
To configure default networks, follow these steps:
Use the show ip route command to verify if the IP address for the default gateway is configured.
IP Access Control Lists
IP Access control Lists (IP-ACLs) provide basic network security to all switches in the Cisco MDS 9000 Family. IP-ACLs restrict IP-related traffic based on the configured IP filters. A filter contains the rules to match an IP packet, and if the packet matches, the rule also stipulates if the packet should be permitted or denied.
Each switch in the Cisco MDS 9000 Family can have a maximum of 64 IP-ACLs, each IP-ACL can have a maximum of 256 filters.
IP-ACL Configuration Guidelines
Follow these guidelines when configuring IP-ACLs in any switch or director in the Cisco MDS 9000 Family:
•
You can apply IP-ACLs to VSAN interfaces and the management interface.
•
Configure the order of conditions accurately. As the IP-ACL filters are sequentially applied to the IP flows, only the first match determines the action taken. Subsequent matches are not considered. Be sure to configure the most important condition first. If no conditions match, the software drops the packet.
Filter Contents
An IP filter contains rules for matching an IP packet based on the protocol, address, port, ICMP type, and type of service (TOS).
Protocol Information
The protocol information is required in each filter. It identifies the name or number of an IP protocol. You can specify the IP protocol in one of two ways:
•
Specify an integer ranging from 0 to 255. This number represents the IP protocol.
•
Specify the name of a protocol including, but not restricted to, Internet Protocol (IP, keyword ip), Transmission Control Protocol (TCP, keyword tcp), User Datagram Protocol (UDP, keyword udp), and Internet Control Message Protocol (ICMP, keyword icmp).
Address Information
The address information is required in each filter. It identifies the following details:
•
Source: the address of the network or host from which the packet is being sent.
•
Source-wildcard: the wildcard bits applied to the source.
•
Destination: the number of the network or host to which the packet is being sent.
•
Destination-wildcard: the wildcard bits applied to the destination.
Specify the source and source-wildcard or the destination and destination-wildcard in one of two ways:
•
Using the 32-bit quantity in four-part, dotted decimal format (10.1.1.2/0.0.0.0 is the same as host 10.1.1.2).
–
Each wildcard bit set to zero indicates that the corresponding bit position in the packet's ip address must exactly match the bit value in the corresponding bit position in the source.
–
Each wildcard bit set to one indicates that both a zero bit and a one bit in the corresponding position of the packet's ip address will be considered a match to this access list entry. Place ones in the bit positions you want to ignore. For example, 0.0.255.255 to require an exact match of only the first 16 bits of the source. Wildcard bits set to one do not need to be contiguous in the source-wildcard. For example, a source-wildcard of 0.255.0.64 would be valid.
•
Using the any option as an abbreviation for a source and source-wildcard or destination and destination-wildcard (0.0.0.0/255.255.255.255)
Port Information
The port information is optional. To compare the source and destination ports, use the eq (equal) option, the gt (greater than) option, the lt (less than) option, or the range (range of ports) option. You can specify the port information in one of two ways:
•
Specify the number of the port. Port number range from 0 to 65535. Table 20-1 displays the port numbers recognized by the Cisco SAN-OS software for associated TCP and UDP ports.
•
Specify the name of a TCP or UDP port as follows:
–
TCP port names can only be used when filtering TCP.
–
UDP port names can only be used when filtering UDP.
ICMP Information
IP packets can be filtered based on the following optional ICMP conditions:
•
The icmp-type: ICMP message type. The type is a number from 0 to 255.
•
The icmp-code: ICMP message code. The code is a number from 0 to 255.
Table 20-2 displays the value for each ICMP type.
Table 20-2 ICMP Type Value
echo
8
echo-reply
0
destination unreachable
3
traceroute
30
time exceeded
11
1 ICMP redirect packets are always rejected.
TOS Information
IP packets can be filtered based on the following optional TOS conditions:
•
The TOS level, as specified by a number from 0 to 15
•
The TOS name: max-reliability, max-throughput, min-delay, min-monetary-cost, and normal
IP-ACL -Creation
Traffic coming into the switch is compared to IP-ACL filters based on the order that the filters occur in the switch. New filters are added to the end of the IP-ACL. The switch keeps looking until it has a match. If no matches are found when the switch reaches the end of the filter, the traffic is denied. For this reason, you should have the frequently hit filters at the top of the filter. There is an implied deny for traffic that is not permitted. A single-entry IP-ACL with only one deny entry has the effect of denying all traffic.
To configure an IP-ACL, you must complete the following tasks:
1.
Create an IP-ACL by specifying a filter name and one or more access condition(s). Filters require the source and destination address to match a condition. Use optional keywords to configure finer granularity.
2.
Apply the access filter to specified interfaces.
To create an IP-ACL, follow these steps:
To define an IP-ACL that permits a specified network, follow these steps:
To use the operand and port options, follow these steps:
Adding filters to an Existing IP-ACL
After you create an IP-ACL, you place subsequent additions at the end of the IP-ACL. You cannot insert filters in the middle of an IP-ACL. Each configured entry is automatically added to the end of a IP-ACL.
To add entries to an existing IP-ACL, follow these steps:
Removing Entries from an Existing IP-ACL
To remove configured entries from an IP-ACL, follow these steps:
Reading the IP-ACL Log Dump
Use the log-deny option at the end of an filter condition to log information about packets that match dropped entries. The log output displays the ACL number, permit or deny status, and port information.
For the input ACL, the log displays the raw MAC information. The keyword "MAC=" does not refer to showing an Ethernet MAC frame with MAC address information. It refers to the Layer 2 MAC-layer information dumped to the log. For the output ACL, the raw Layer 2 information is not logged.
The following is example of an input ACL log dump.
Jul 17 20:38:44 excal-2%KERN-7-SYSTEM_MSG:%IPACL-7-DENY:IN=vsan1 OUT= MAC=10:00:00:05:30:00:47:df:10:00:00:05:30:00:8a:1f:aa:aa:03:00:00:00:08:00:45:00:00:54:00 :00:40:00:40:01:0e:86:0b:0b:0b:0c:0b:0b:0b:02:08:00:ff:9c:01:15:05:00:6f:09:17:3f:80:02:01 :00:08:09:0a:0b:0c:0d:0e:0f:10:11:12:13:14:15:16:17:18:19:1a:1b:1c:1d:1e:1f:20:21:22:23:24 :25:26:27:28:29:2a:2b SRC=11.11.11.12 DST=11.11.11.2 LEN=84 TOS=0x00 PREC=0x00 TTL=64 ID=0 DF PROTO=ICMP TYPE=8 CODE=0 ID=277 SEQ=1280The following example is an output ACL log dump.
Jul 17 20:38:44 excal-2%KERN-7-SYSTEM_MSG:%IPACL-7-DENY:IN= OUT=vsan1 SRC=11.11.11.2 DST=11.11.11.12 LEN=84 TOS=0x00 PREC=0x00 TTL=255 ID=38095 PROTO=ICMP TYPE=0 CODE=0 ID=277 SEQ=1280
IP-ACL Interface Application
You can define IP-ACLs without applying them. However, the IP-ACLs will have no effect until they are applied to the switch's interface.
Tip
Apply the IP-ACL on the interface closest to the source of the traffic.
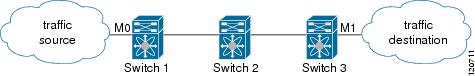
When you are trying to block traffic from source to destination, you can apply an inbound IP-ACL to M0 on Switch 1 instead of an outbound filter to M1 on Switch 3 (see Figure 20-3).
Figure 20-3 Denying Traffic on the Inbound Interface
The access-group option controls access to an interface. Each interface can only be associated with one access filter per direction. The ingress direction can have a different ACL than the egress direction. The access group becomes active on creation.
Tip
Create all conditions in an access filter before creating the access group that uses this filter.
CautionIf you create an access group before an access-filter, all packets in that interface are dropped because the access filter is empty.
The terms in, out, source, and destination are used as referenced by the switch.
•
In—Traffic that is arriving on the interface and which will go through the switch; the source would be where it's been and the destination is where it's going (on the other side of the router).
Tip
The access-group configuration for the ingress traffic applies to both local and remote traffic.
•
Out—Traffic that has already been through the switch and is leaving the interface; the source would be where it's been (on the other side of the router) and the destination is where it's going.
Tip
The access-group configuration for the egress traffic applies only to local traffic.
To create an access group, follow these steps:
IP-ACL Configuration Verification
Use the show ip access-list command to view the contents of configured access filters. Each access filter can have several conditions.
Example 20-1 Displays Configured IP-ACLs
switch# show ip access-list usageAccess List Name/Number Filters IF Status Creation Time-------------------------------- ------- ---- --------- -------------abc 3 7 active Tue Jun 24 17:51:40 2003x1 3 1 active Tue Jun 24 18:32:25 2003x3 0 1 not-ready Tue Jun 24 18:32:28 2003Example 20-2 Displays a Summary of the Specified IP-ACL
switch# show ip access-list abcip access-list abc permit tcp any any (0 matches)ip access-list abc permit udp any any (0 matches)ip access-list abc permit icmp any any (0 matches)ip access-list abc permit ip 10.1.1.0 0.0.0.255 (2 matches)ip access-list abc permit ip 10.3.70.0 0.0.0.255 (7 matches)IP-ACL Counter Cleanup
Use the clear command to clear the counters for a specified IP-ACL entry.
Note
You cannot use this command to clear the counters for each individual filter.
switch# clear ip access-list counters abcConfiguring IPFC
Once the VSAN interface is created, you can specify the IP address for that VSAN using the ip address command.
Configuring an IP Address in a VSAN
To configure a VSAN interface and an IP address for that interface, follow these steps:
Enabling IP Routing
By default, the IP routing feature is disabled in all switches. To enable the IP routing feature, follow these steps:
Configuring IP Static Routes
Static routing is a mechanism to configure IP routes on the switch. You can configure more than one static route.
To configure a static route, follow these steps:
If your configuration does not need an external router, you can use static routing.
If a VSAN has multiple exit points, configure static routes to direct traffic to the appropriate gateway switch. IP routing is disabled by default on any gateway switch between the out-of-band management interface and the default VSAN, or between directly connected VSANs.
Displaying and Clearing ARPs
Address Resolution Protocol (ARP) entries in Cisco MDS 9000 Family switches can be displayed (show arp), deleted (no arp), or cleared (clear arp-cache). The ARP feature is enabled on all switches.
•
Use the show arp command to display the ARP table.
switch# show arp Protocol Address Age (min) Hardware Addr Type InterfaceInternet 171.1.1.1 0 0006.5bec.699c ARPA mgmt0Internet 172.2.0.1 4 0000.0c07.ac01 ARPA mgmt0•
Use the no arp command in configuration mode to remove an ARP entry from the ARP table.
switch(config)# no arp 172.2.0.1switch(config)#•
Use the clear arp command to delete all entries from the ARP table. The ARP table is empty by default.
switch# clear arp-cacheswitch#Displaying IP Interface Information
Use the following show commands to view configured IP interface information (see Examples 20-3 to 20-6).
Example 20-3 Displays the VSAN Interface
switch# show interface vsan1vsan1 is up, line protocol is upWWPN is 10:00:00:05:30:00:59:1f, FCID is 0x9c0100Internet address is 10.1.1.1/24MTU 1500 bytes, BW 1000000 Kbit0 packets input, 0 bytes, 0 errors, 0 multicast0 packets output, 0 bytes, 0 errors, 0 dropped
Note
You can see the output for this command only if you have previously configured a virtual network interface (see the "Configuring an IP Address in a VSAN" section).
Example 20-4 Displays the Connected and Static Route Details
switch# show ip route Codes: C - connected, S - static Default gateway is 172.22.95.1 C 172.22.95.0/24 is directly connected, mgmt0 C 10.1.1.0/24 is directly connected, vsan1Example 20-5 Displays Configured Routes
switch# show ip route configuredDestination Gateway Mask Metric Interfacedefault 172.22.95.1 0.0.0.0 0 mgmt010.1.1.0 0.0.0.0 255.255.255.0 0 vsan1172.22.95.0 0.0.0.0 255.255.255.0 0 mgmt0Example 20-6 Displays the IP Routing Status
switch# show ip routingip routing is disabledConfiguring Overlay VSANs
VSANs enable deployment of larger SANs by overlaying multiple logical SANs, each running its own instance of fabric services, on a single large physical network. This partitioning of fabric services reduces network instability by containing fabric reconfiguration and error conditions within an individual VSAN. VSANs also provide the same isolation between individual VSANs as physically separated SANs. Traffic cannot cross VSAN boundaries and devices may not reside in more than one VSAN. Because each VSAN runs separate instances of fabric services, each VSAN has its own zone server and can be zoned in exactly the same way as SANs without VSAN capability.
To configure an overlay VSAN, follow these steps:
Step 1
Add the VSAN to the VSAN database on all switch in the fabric.
Step 2
Create a VSAN interface for the VSAN on all switches in the fabric. Any VSAN interface belonging to the VSAN has an IP address in the same subnet. Create a route to the IPFC cloud on the IP side
Step 3
Configure a default route on every switch in the Fibre Channel fabric pointing to the switch that provides NMS access.
Step 4
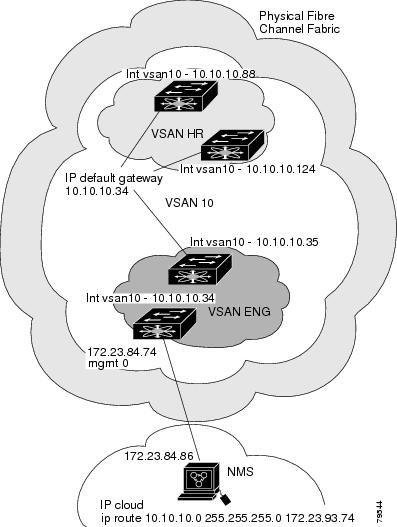
Configure default gateway (route) and the IP address on switches that point to the NMS (see Figure 20-4).
Figure 20-4 Overlay VSAN Configuration Example
The following procedure configures an overlay VSAN in one switch. This procedure must be repeated for each switch in the fabric.
To configure an overlay VSAN in one switch (using the example in Figure 20-4), follow these steps:
To configure the NMS station displayed in Figure 20-4, follow this step:
Note
To configure the management interface displayed in Figure 20-4, set the default gateway to an IP address on the Ethernet network.
Configuring Multiple VSANs
More than one VSAN can be used to segment the management network in multiple subnets. An active interface must be present on the switch for the VSAN interface to be enabled.
To configure multiple VSANs, follow these steps:
Step 1
Add the VSAN to the VSAN database on any switch in the fabric.
Step 2
Create a VSAN interface for the appropriate VSAN on any switch in the fabric.
Step 3
Assign an IP address on every VSAN interface on the same subnet as the corresponding VSAN.
Step 4
Define the multiple static route on the Fibre Channel switches and the IP cloud (see Figure 20-5).
Figure 20-5 Multiple VSANs Configuration Example
To configure an overlay VSAN (using the example in Figure 20-5), follow these steps:
Configuring VRRP
Cisco MDS 9000 Family switches are compliant with RFC 2338 standards for Virtual Router Redundancy Protocol (VRRP) features. This section provides details on the VRRP feature.
VRRP Features
VRRP provides a redundant alternative path to the gateway switch, which has connectivity to the NMS. VRRP has the following characteristics and advantages:
•
VRRP is a restartable application.
•
When a VRRP master fails, the VRRP backup takes over within three times the advertisement time.
•
VRRP over Ethernet, VRRP over VSAN, and Fibre Channel functions are implemented as defined in RFC 2338.
•
A virtual router is mapped to each VSAN and Ethernet interface with its unique virtual router IP, virtual router MAC, and VR ID.
•
VR IDs can be reused in multiple VSANs with a different virtual router IP mapping.
•
Up to 255 virtual router groups can be assigned in each VSAN.
•
VRRP security provides three options, including no authentication, simple text authentication, and MD5 authentication.
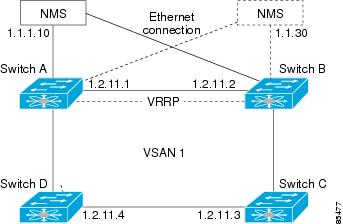
VRRP Functionality
In Figure 20-6, switch A is the VRRP master and switch B is the VRRP backup switch. Both switches have IP address to VRRP mapping configured. The other switches set switch A as the default gateway. If switch A fails, the other switches don't have to change the routing configurations as switch B automatically becomes the master and takes over the function of a gateway.
Figure 20-6 VRRP Functionality
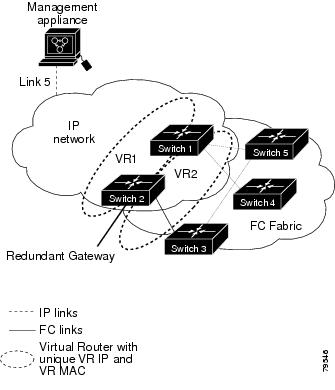
In Figure 20-7, the fabric example has two virtual router groups (VR1 and VR 2) because a virtual router cannot span across different types of interfaces. In both switch 1 and switch 2, the Ethernet interface is in VR 1 and the FC interface is in VR 2. Each virtual router is uniquely identified by the VSAN interface and the VR ID.
Figure 20-7 Redundant Gateway
Creating or Removing a Virtual Router
All VRRP configurations should be replicated across switches in a fabric that runs VRRP.
To create or remove a VR, follow these steps:
Enabling a Virtual Router
By default, a virtual router is always disabled (shutdown). VRRP can be configured only if this state is disabled. Be sure to configure at least one IP address before attempting to enable a VR.
To enable or disable a virtual router, follow these steps:
Step 1
Enables VRRP configuration.
Disables VRRP configuration.
Adding an IP Address for a Virtual Router
One primary IP address and multiple secondary addresses can be configured for a switch. If the configured IP address is the same as the interface IP address, this switch automatically owns the IP address.
To configure an IP address for a virtual router, follow these steps:
Setting Priority for the Virtual Router
The valid range to assign a virtual router priority is 1 to 254 with 1 being the lowest priority and 254 being the highest priority. The default value is 100 for switches with secondary IP addresses and 255 for a switch with the primary IP address.
To set the priority for a virtual router, follow these steps:
Setting the Time Interval for the Advertisement Packet
The valid time range for an advertisement packet is between 1 and 255 seconds with the default being 1 (one) second. If the switch has the primary IP address, this time must be specified.
To set the priority for a virtual router, follow these steps:
Preempting the Master Virtual Router
By default, the preempt option is enabled. An owner with priority 255 cannot be preempted. If two priorities match, the owner with the highest priority preempts the master virtual router.
Note
Sometimes, the Ethernet switch port connected to the IPS port may be isolated due to the spanning tree algorithm converging in the Ethernet switch. This may prevent the master VRRP port from being preempted. To optimize the host port configuration, issue the Cisco IOS set port host command in the Ethernet switch. Refer to the Cisco Systems IOS documentation at the following URL: http://www.cisco.com/univercd/cc/td/doc/product/lan/cat6000/122sy/cmdref/s1.htm#26643
To enable or disable preempting, follow these steps:
Note
The VRRP preempt option is not supported on IP storage Gigabit Ethernet interfaces. However, if the virtual IP address is also the IP address for the interface, then preemption is implicitly applied.
Configuring Authentication for the Virtual Router
VRRP security provides three options, including simple text authentication, MD5 authentication, and no authentication.
•
Simple text authentication uses a unique, 1 to 8 character password that is used by all switches participating in the same virtual router. This password should be different from other security passwords.
•
MD5 authentication uses a unique, 16 character key that is shared by all switches participating in the same virtual router. This secret key is shared by all switches in the same virtual router.
•
No authentication is the default option.
You can configure the key using the authentication option in the VRRP submode and distribute it using the configuration file. The security parameter index (SPI) settings assigned in this option should be unique for each VSAN.
Note
All VRRP configurations must be duplicated
To set an authentication option for a virtual router, follow these steps:
Setting the Priority Based on Interface State
The tracking feature is disabled by default. When you specify the tracking option, the priority of the virtual router is changed based on the state of another interface in the switch. When the tracked interface is down, the priority of the virtual router is changed to a lower priority value. When the tracked interface is up, the priority of the virtual router is restored to its original value. You can track one of two interfaces on a switch in the Cisco MDS 9000 Family: a specified VSAN interface or a management interface.
To track the interface priority for a virtual router, follow these steps:
Displaying VRRP Information
Use the show vrrp vr command to display configured VRRP information (see Examples 20-7 to 20-10).
Example 20-7 Displays VRRP Configured Information
switch# show vrrp vr 7 interface vsan 2 configurationvr id 7 configurationadmin state downpriority 100no authenticationadvertisement-Interval 1preempt yestracking interface vsan1 priority 2protocol IPExample 20-8 Displays VRRP Status Information
switch# show vrrp vr 7 interface vsan 2 statusvr id 7 statusMAC address 00:00:5e:00:01:07Operational state: initExample 20-9 Displays VRRP Statistics
switch# show vrrp vr 7 interface vsan 2 statisticsvr id 7 statisticsBecome master 0Advertisement 0Advertisement Interval Error 0Authentication Failure 0TTL Error 0Priority 0 Received 0Priority 0 Sent 0Invalid Type 0Mismatch Address List 0Invalid Authentication Type 0Mismatch Authentication 0Invalid Packet Length 0Example 20-10 Displays VRRP Cumulative Statistics
switch# show vrrp statisticsInvalid checksum 0Invalid version 0Invalid VR ID 0Clearing VRRP Statistics
Use the clear vrrp command to clear all the software counters for the specified virtual router (see Example 20-11).
Example 20-11 Clears VRRP Information
switch# clear vrrp 7 interface vsan2switch#Configuring DNS Server
The DNS client on the switch communicates with the DNS server to perform the IP address-name server correspondence.
To configure a DNS server, follow these steps:
The DNS server may be dropped after two attempts due to one of the following reasons:
•
The IP address or the switch name is wrongly configured.
•
The DNS server is not reachable due to external reasons (reasons beyond our control).
Note
When accessing a Telnet host, if the DNS server is not reachable (for any reason) the switch login prompt may take a longer time to appear. If so, verify that the DNS server is accurately configured and reachable.
Displaying DNS Host Information
Use the show hosts command to display the DNS configuration (see Example 20-12).
Example 20-12 Displays Configured Host Details
switch# show hostsDefault domain is cisco.com
Domain list: ucsc.edu harvard.edu yale.edu stanford.edu
Name/address lookup uses domain service
Name servers are 15.1.0.1 15.2.0.0
Default Settings
Table 20-3 lists the default settings for IP features.

 Feedback
Feedback