The following section provides a full description of each attribute. The majority of the attribute values are common for the
ISE and 3GPP dictionaries. The values are included especially in the attribute description section for the attributes with
different attribute values for ISE and 3GPP dictionary:
-
USER-NAME
Description: String value encoded as per RFC 2865.
-
5G call: GPSI value is used, with stripped-off "msisdn-"
-
4G call: MSISDN value is used, with stripped-off "msisdn-"
-
The attribute value for 3GPP dictionary is imsi@apn.

Note
|
PAP, CHAP, and MSCHAP authentication methods are not supported in releases prior to 2020.02.x.
In release 2020.02.x and beyond, the PAP, CHAP, and MSCHAP authentication methods are supported.
|
-
PASSWORD
Description: Encrypted string value encoded as per RFC 2865.
For both 5G and 4G calls, selected RADIUS server's "secret" is set as user-password.
-
CALLING-STATION-ID
Description: String value encoded as per RFC 2865.
5G call: GPSI value is used, with stripped of "msisdn-"
4G call: MSISDN value is used, with stripped of "msisdn-"
-
CALLED-STATION-ID
Description: String value encoded as per RFC 2865.
For both 5G and 4G calls, DNN value is set as called-station-id.
-
NAS-IP-ADDRESS
Description: IPv4 address value encoded as per RFC 2865.
For both 5G and 4G calls, user-configured RADIUS Client interface-type's VIP-IP is used.
-
NAS-IDENTIFIER
Description: String value encoded as per RFC 2865.
For both 5G and 4G calls, user-configured nas-identifier attribute value is used.
-
SERVICE-TYPE
Description: 4-byte octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, "FRAMED (2)" value is set.
-
FRAMED-PROTOCOL
Description: 4-byte octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, "GPRS-PDP-CONTEXT (7)" value is set.
-
NAS-PORT-TYPE
Description: 4-byte octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, "WIRELESS-OTHER (18)" value is set.
-
NAS-PORT
Description: 4-byte octet (int) value encoded as per RFC 2865.
For both 5G and 4G calls, the base value of respective instance is used. That is:
0x4000... 0x407F is set for replica-0
0x4080... 0x40FF is set for replica-1
-
3GPP-IMSI
Description: String value encoded as per 3GPP TS 29.061.
5G call: SUPI value is used.
4G call: IMSI value is used.
-
3GPP-CHARGING-ID
Description: 4-byte octet (int) value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, charging-ID is set.
-
3GPP-PDP-TYPE
Description: 4-byte octet (int) value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, pdp-type is set as follows:
-
0 = IPv4
-
2 = IPv6
-
3 = IPv4v6
-
3GPP-CHARGING-GATEWAY-ADDR
Description: 4-byte octet (IPv4-address) value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, charging gateway address is set.
-
3GPP-GPRS-NEG-QOS-PROFILE
Description: Octets (special encoding) value encoded as per 3GPP TS 29.061 and 29.274.
For 5G call, the values from default-qos profile of the system are used and the encoding is performed as follows:
Table 6. Non-GBR case
| 1-2 |
<Release indicator>- = "15" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-9 |
UL Session-AMBR length (UTF-8 encoded) |
| 10-m |
UL Session-AMBR (UTF-8 encoded) |
| (m+1) - (m+2) |
DL Session-AMBR length (UTF-8 encoded) |
| (m+3) – n |
DL Session-AMBR (UTF-8 encoded) |
Table 7. GBR case
| 1-2 |
<Release indicator> = "15" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-9 |
UL MFBR length (UTF-8 encoded) |
| 10-m |
UL MFBR (UTF-8 encoded) |
| (m+1)-(m+2) |
DL MFBR length (UTF-8 encoded) |
| (m+3)-n |
DL MFBR (UTF-8 encoded) |
| (n+1)-(n+2) |
UL GFBR length (UTF-8 encoded) |
| (n+3)-o |
UL GFBR (UTF-8 encoded) |
| (o+1) – (o+2) |
UL GFBR length (UTF-8 encoded) |
| (o+3) - p |
DL GFBR (UTF-8 encoded) |
For 4G call, the values from the default-qos profile of the system are used and the encoding is performed as follows:
Table 8. Non-GBR case
| 1-2 |
<Release indicator>- = "08" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-11 |
UL Session-AMBR (UTF-8 encoded) |
| 12-15 |
DL Session-AMBR (UTF-8 encoded) |
Table 9. GBR case
| 1-2 |
<Release indicator> = "08" (UTF-8 encoded) |
| 3 |
"-" (UTF-8 encoded) |
| 4-5 |
ARP (UTF-8 encoded) |
| 6-7 |
5QI (UTF-8 encoded) |
| 8-11 |
UL MBR (UTF-8 encoded) |
| 12-15 |
DL MBR (UTF-8 encoded) |
| 16-19 |
UL GBR (UTF-8 encoded) |
| 20-23 |
DL GBR (UTF-8 encoded) |
-
3GPP-SGSN-ADDRESS
Description: 4-byte octet (IPv4-address) value encoded as per 3GPP TS 29.061.
For 5G call, the AMF address is set.
For 4G call, the S-GW address is set.
-
3GPP-GGSN-ADDRESS
Description: 4-byte octet (IPv4-address) value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, the SMF-Service IP is set.
For 3GPP dictionary, PGW control IP address as sent in CSRsp.
-
3GPP-IMSI-MCC-MNC
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, SUPIs MCC and MNC values are set.
For 4G call, IMSIs MCC and MNC values are set.
MCC is first 3 bytes, MNC is next 2 or 3 bytes.
If MCC value is any of the following, then MNC will be of 3 bytes, else MNC will be of 2 bytes.
300 302 310 311 312 313 316 334 338 342 344 346 348 354 356 358 360 365 376 405 708 722 732
-
3GPP-GGSN-MCC-MNC
Description: String value encoded as per 3GPP TS 29.061.
For both 5G and 4G calls, configured MCC and MNC value of SMF is used.
MCC is first 3 bytes, and MNC is next 2 or 3 bytes.
-
3GPP-SGSN-MCC-MNC
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, AMFs MCC and MNC values are set.
For 4G call, SGWs MCC and MNC values are set.
MCC is first 3 bytes, and MNC is next 2 or 3 bytes.
-
3GPP-NSAPI
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, QFI value from the defaultQos profile is set.
For 4G call, EPS bearer ID is set.
-
3GPP-SELECTION-MODE
Description: String value encoded as per 3GPP TS 29.061.
For both 4G and 5G calls, the value is set to "0".
For 3GPP dictionary, the selection mode value is received in CSReq.
-
3GPP-CHARGING-CHARACTERISTICS
Description: String value encoded as per 3GPP TS 29.061.
For both 4G and 5G calls, generic charging character is set.
-
3GPP-IMEISV
Description: String value encoded as per 3GPP TS 29.061.
For 5G call, PEI value is set.
For 4G call, IMEI value is set.
-
3GPP-RAT-TYPE
Description: 1-byte octet encoded as per 3GPP TS 29.061.
For 5G call, value "NR (51)" is set.
For 4G call, value "EUTRAN (6)" is set.
For WLAN call, value "WLAN (3)" is set.
-
3GPP-USER-LOCATION
Description: Special octet value encoded as per 3GPP TS 29.061.
For 5G call, the following encoding logic is used:
|
1
|
Location-Type
Only TAI = 136
Only NCGI = 135
Both TAI + NCGI =137
|
|
2-7
|
TAI-Encoding (if present)
|
| 8-15 |
NCGI-Encoding (if present)
|
TAI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4-6 |
TAC value |
NCGI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4 |
SPARE |
NCI |
| 5-8 |
NR Cell Identifier (NCI) |
For 4G call, the following encoding logic is used:
| 1 |
Location-Type |
| Only TAI = 128 |
| Only ECGI = 129 |
| Both TAI + ECGI =130 |
| 2-6 |
TAI-Encoding (if present) |
| 7-13 |
ECGI-Encoding (if present) |
TAI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4-5 |
TAC value |
ECGI Encoding header:
| 1 |
MCC digit 2 |
MCC digit 1 |
| 2 |
MNC digit 3 |
MCC digit 3 |
| 3 |
MNC digit 2 |
MNC digit 1 |
| 4 |
Spare |
ECI |
| 5-7 |
EUTRAN Cell Identifier (ECI) |
-
3GPP-MS-TIMEZONE
Description: Special octet value encoded as per 3GPP TS 29.061.
Timezone string (for example: -07:00+1) is encoded as two-byte value as mentioned in the following table.
| 1 |
TIMEZONE
The first byte timezone is encoded as per 3GPP 29.061, 3GPP 29.274, 3GPP 24.008, and 3GPP 23.040 (section 9.2.3.11).
|
| 2 |
DAYLIGHT SAVING 0, or +1 or +2
The second byte daylight consists of two bits used (00-0, 01-+1, 10-+2, 11 – Unused).
|
-
3GPP-NEGOTIATED-DSCP
Description: 1-byte octet encoded as per 3GPP TS 29.061
For both 5G and 4G calls, DSCP configuration from DNN qos-profile configuration is used.
Sub -> DNN profile -> QosProfile -> DSCPMap -> Qi5 value check -> ARP priority check
-
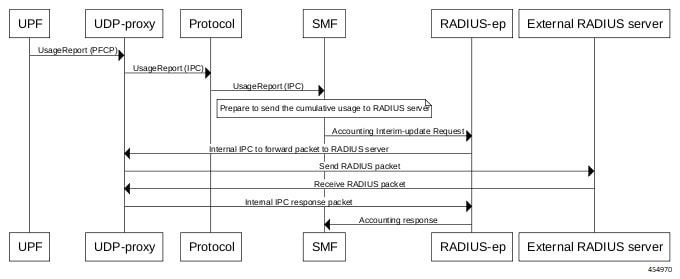
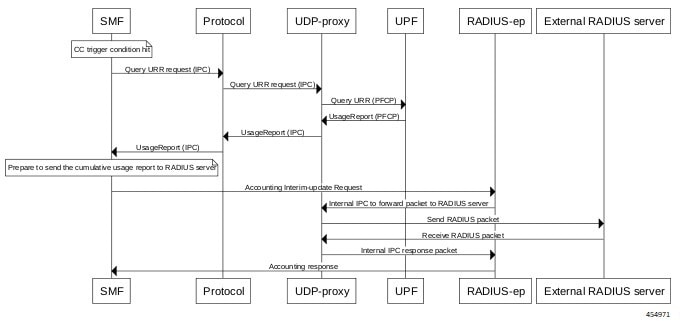
Acct-Status-Type
Description: Enum value encoded as per RFC 2866. The value of this attribute can be one of the following:
-
1 - Start
-
2 - Stop
-
3 - Interim Update
-
Acct-Delay-Time
Description: Integer value encoded as per RFC 2866. This attribute represents the amount of time client is trying to send the accounting
record.
-
Acct-Input-Octets
Description: Integer value encoded as per RFC 2866. This attribute represents the amount of bytes received. This attribute contains 4
bytes.
The SMF wraps values when the number crosses the maximum value.
-
Acct-Output-Octets
Description: Integer value encoded as per RFC 2866. This attribute represents the amount of bytes transmitted. This attribute contains
4 bytes.
The SMF wraps values when the number crosses the maximum value.
-
Acct-Input-Packets
Description: Integer value encoded as per RFC 2866. This attribute represents the amount of packets received. This attribute contains
4 bytes.
The SMF wraps values when the number crosses the maximum value.
-
Acct-Output-Packets
Description: Integer value encoded as per RFC 2866. This attribute represents the amount of packets transmitted. This attribute contains
4 bytes.
The SMF wraps values when the number crosses the maximum value.
-
Acct-Input-Gigawords
Description: Integer value encoded as per RFC 2869. This attribute indicates how many times the Acct-Input-Octets counter has wrapped
around 2^32 over the course of this service being provided. This value is incremented whenever Acct-Input-Octets is wrapped.
-
Acct-Output-Gigawords
Description: Integer value encoded as per RFC 2869. This attribute indicates how many times the Acct-Output-Octets counter has wrapped
around 2^32 over the course of this service being provided. This value is incremented whenever Acct-Output-Octets is wrapped.
-
Acct-Session-Id
Description: String value encoded as per RFC 2866. This attribute represents the unique accounting ID of subscriber. The accounting ID
is unique to make it easy to match start and stop records in a log file. The start and stop records for a given session MUST
have the same Acct-Session-Id. An Accounting-Request packet MUST have an Acct-Session-Id.
An Access-Request packet MAY have an Acct-Session-Id; if it does, then the NAS MUST use the same Acct-Session-Id in the Accounting-Request
packets for that session. The Acct-Session-Id contains UTF-8 encoded 10646 characters.
-
Acct-Session-Time
Description: Integer value encoded as per RFC 2866. This attribute represents the amount of time the subscriber is active.
-
Framed-MTU
Description: This attribute indicates the Maximum Transmission Unit to be configured for the user, when it is not negotiated by some
other means (such as PPP). The default value is 1500.
It MAY be used in Access-Accept packets. It MAY be used in an Access-Request packet as a hint by the NAS to the server that
it would prefer that value, but the server is not required to honour the hint.
-
Acct-Terminate-cause
Description: Enum value encoded as per RFC 2866. This attribute represents the reason for termination of subscriber.
-
FRAMED-IP
The IPv4 address value decoded as per RFC 2865.
For both 4G and 5G calls, the received value is set as the IPv4 address for the subscriber.
-
FRAMED-IPv6-PREFIX
The IPv6 Prefix + Length value decoded as per RFC 3162.
For both 4G and 5G calls, the received value is set as the IPv6 prefix for the subscriber.

Important
|
If the received prefix-length is !=64, the SMF overrides to 64.
|
-
IDLE-TIMEOUT
The 4-byte octet (integer) value encoded as per RFC 2865. This attribute is supported in the inbound RADIUS packet.
For both 4G and 5G calls, the received value is used as the maximum number of consecutive seconds of idle time that the user
is permitted before being disconnected by the NAS.
-
SESSION-TIMEOUT
The 4-byte octet (integer) value encoded as per RFC 2865. This attribute is supported in the inbound RADIUS packet.
For both 4G and 5G calls, the received value is used as the maximum number of seconds that the user is allowed to remain connected
by the NAS.
-
3GPP-Negotiated-QoS-Profile
-
Access-request
For ISE or default dictionary: ARP PCI and ARP PVI were sent out incorrectly and did not match value received in CSReq. Also
APN AMBR was sent out in bps instead of Kbps.
For 3GPP dictionary: ARP PCI and ARP PVI values are fixed and in sync with what is received in CSReq. Also APN AMBR is sent
out in Kbps.
-
Accounting-request
For ISE or default dictionary: ARP PCI and ARP PVI were sent out incorrectly and did not match value received in CSReq/Gx
CCA-I. Also APN AMBR was sent out in bps instead of Kbps.
-
For 3GPP dictionary: ARP PCI and ARP PVI values are fixed and in sync with what is received in CSReq/Gx-CCA-I. Also APN AMBR
is sent out in Kbps.
-
3GPP-IMEI-SV
-
Access-request
For ISE or default dictionary: For 16 bit IMEI: imeisv-1122334455667788 and for 15 bit imei: 112233445566778.
For 3GPP dictionary: For 16 bit IMEI: 1122334455667788 and for 15 bit IMEI: 112233445566778.
-
Accounting-request
For ISE or default dictionary: For 16 bit IMEI: imeisv-1122334455667788 and for 15 bit IMEI: 112233445566778.
-
For 3GPP dictionary: For 16 bit IMEI: 1122334455667788 and for 15 bit IMEI: 112233445566778.
-
3GPP-UE-Location
-
Access-request
For ISE or default dictionary: ECI value is going as 0.
For 3GPP dictionary: the value is received in CSReq.
-
Accounting-request
For ISE or default dictionary: For 16 bit IMEI: imeisv-1122334455667788 and for 15 bit IMEI: 112233445566778.
-
For 3GPP dictionary: For 16 bit IMEI: 1122334455667788 and for 15 bit IMEI: 112233445566778 .

 Feedback
Feedback