- Preface
- Overview
- Adding and Deleting Mobility Services Engines and Licenses
- Synchronizing Mobility Services Engines
- Configuring High Availability
- MSE Delivery Modes
- Configuring and Viewing System Properties
- Mobile Concierge Services
- Managing Users and Groups
- Configuring Event Notifications
- Context-Aware Service Planning and Verification
- Working with Maps
- Monitoring the System and Services
- Performing Maintenance Operations
- MSE System and Appliance Hardening Guidelines
- Index
Monitoring the System and Services
This chapter describes how to monitor the Cisco Mobility Services Engine by configuring and viewing alarms, events, and logs and how to generate reports on system use and element counts (tags, clients, rogue clients, interferers, and access points). This chapter also describes how to use the Prime Infrastructure to monitor clients (wired and wireless), tags, chokepoints, and Wi-Fi TDOA receivers.
- Working with Alarms
- Working with Events
- Working with Logs
- Generating Reports
- Generating MSE Analytics Reports
- Creating a Device Utilization Report
- Managing OUI
- Monitoring Wireless Clients
- Client Support on the MSE
- Configuring Buildings
- Monitoring Tags
- Monitoring Geo-Location
- Monitoring Chokepoints
- Monitoring Wi-Fi TDOA Receivers
- Ekahau Site Survey Integration
- AirMagnet Survey and Planner Integration
- Monitoring Wired Clients
- Monitoring Wired Switches
- Monitoring Interferers
- Clustering of Monitor Mode APs Using MSE
Working with Alarms
This section describes how to view, assign, and clear alarms on a Mobility Services Engine using the Prime Infrastructure. It also describes how to define alarm notifications (all, critical, major, minor, warning) and how to e-mail those alarm notifications.
- Guidelines and Limitations
- Viewing Alarms
- Monitoring Cisco Adaptive wIPS Alarm Details
- Assigning and Unassigning Alarms
- Deleting and Clearing Alarms
- E-mailing Alarm Notifications
Guidelines and Limitations
Once the severity is cleared, the alarm is deleted from the Prime Infrastructure after 30 days.
Viewing Alarms
To view Mobility Services Engine alarms, follow these steps:
| Step 1 | Choose Monitor > Alarms. | ||
| Step 2 | Click the Advanced Search link in the navigation bar. A configurable search dialog box for alarms appears. | ||
| Step 3 | Choose Alarms from the Search Category drop-down list. | ||
| Step 4 | Choose the severity of alarms from the Severity drop-down list. The options are All Severities, Critical, Major, Minor, Warning, or Clear. | ||
| Step 5 | Choose Mobility Service from the Alarm Category drop-down list. | ||
| Step 6 | Choose the Condition from the Condition combo box. Alternatively, you can enter the condition in the Condition text box. | ||
| Step 7 | From the Time Period
drop-down list, choose the time frame for which you want to review alarms.
The options range from minutes (5, 15, and 30) to hours (1 and 8) to days (1 and 7). To display all, choose Any time. | ||
| Step 8 | Select the Acknowledged State check box to exclude the acknowledged alarms and their count in the Alarm Summary page. | ||
| Step 9 | Select the Assigned State check box to exclude the assigned alarms and their count in the Alarm Summary page. | ||
| Step 10 | From the Items per page drop-down list, choose the number of alarms to display in each page. | ||
| Step 11 | To save the search criteria
for later use, select the
Save Search check box and
enter a name for the search.
| ||
| Step 12 | Click
Go. The alarms summary
dialog box appears with search results.
| ||
| Step 13 | Repeat Step 2 to Step 12 to see Context-Aware Service notifications for the Mobility Services Engine. Enter Context Aware Notifications as the alarm category in Step 5. |
Monitoring Cisco Adaptive wIPS Alarm Details
-
General
Properties—The general information might vary depending on the type of alarm.
For example, some alarm details might include location and switch port tracing
information. The following table describes the general parameters associated
with the MSE Alarm and wIPS Traps condition.
- Detected By wIPS AP—The access point that detected the alarm.
- wIPS AP IP Address—The IP address of the wIPS access point.
- Owner—Name of person to which this alarm is assigned or left blank.
- Acknowledged—Displays whether or not the alarm is acknowledged by the user.
- Category—For wIPS, the alarm category is Security.
- Created—Month, day, year, hour, minute, second, AM or PM that the alarm was created.
- Modified—Month, day, year, hout, minute, second, AM or PM that the alarm was last modified.
- Generated By—Indicates how the alarm event was generated (either NMS or from a trap). NMS (Network Management System - Prime Infrastructure—Generated through polling. Prime Infrastructure periodically polls the Cisco WLCs and generates events. Prime Infrastructure generates events when the traps are disabled or when the traps are lost for those events. in this case, "Generated by" NMS. Trap—Generated by the controller. Prime Infrastructure process these traps and raises corresponding events for them. In this case, "Generated by" is controller.
- Severity—Level of severity including critical, major, minor, warning, and clear.
- Last Disappeared—The date and time that the potential attack last disappeared.
- Channel—The channel on which the potential attack occurred.
- Attacker Client/AP MAC—The MAC address of the client or access point that initiated the attack.
- Attacker Client/AP IP Address—The IP address of the client or access point that initiated the attack.
- Target Client/AP IP Address—The IP address of the client or access point targeted by the attacker.
- Controller IP Address—The IP address of the controller to which the access point is associated.
- MSE—The IP address of the associated Mobility Services Engine.
- Controller MAC address—The MAC address of the controller to which the access point is associated.
- wIPS access point MAC address
- Forensic File
- Event History—Takes you to the Monitoring Alarms page to view all events for this alarm.
- Annotations—Enter any new notes in this text box and click Add to update the alarm. Notes appear in the "Annotations" display area.
- Messages—Displays the alarm name.
- Description—Displays the consolidated information about the alarm.
- Mitigation Status—Displays what mitigation action was initiated against the attack.
-
Audit
Report—Click to view config audit alarm details. This report is only available
for Config Audit alarms.
Configuration
audit alarms are generated when audit discrepancies are enforced on config
groups.

Note
If enforcement fails, a critical alarm is generated on the config group. If enforcement succeeds, a minor alarm is generated on the config group. The alarms have links to the audit report where you can view a list of discrepancies for each controller.
- Event History—Opens the MSE Alarm Events page to view events for this alarm. When there are multiple alarm pages, the page numbers appear at the top of the page with a scroll arrow on each side. Use these scroll arrows to view additional alarms.
- Rogue Clients—If the failure object is a rogue access point, information about rogue clients is displayed.
- Map Location—Displays the map location for the alarm.
- Related Alarm List—Lists all the alarms related to a particular attack. This shows what consolidation rule was used to consolidate the alarms.
Assigning and Unassigning Alarms
Deleting and Clearing Alarms
If you delete an alarm, the Prime Infrastructure removes it from its database. If you clear an alarm, it remains in the Prime Infrastructure database, but in the Clear state. You should clear an alarm when the condition that caused it no longer exists.
To delete or clear an alarm from a Mobility Services Engine, follow these steps:
E-mailing Alarm Notifications
The Prime Infrastructure lets you send alarm notifications to a specific e-mail address. Sending notifications through e-mail enables you to take prompt action when needed.
You can choose the alarm severity types (critical, major, minor, and warning) to have e-mailed to you.
| Step 1 | Choose Monitor > Alarms. | ||
| Step 2 | Select the alarms by selecting their corresponding check boxes.
Click
Email Notification
From the Select a command
drop-down list, choose
Email Notification. Click
Go. The Email
Notification page appears.
| ||
| Step 3 | Select the
Enabled check box next to
the Mobility Service.
| ||
| Step 4 | Click the Mobility Service link. The page for configuring the alarm severity types that are reported for the Mobility Services Engine appears. | ||
| Step 5 | Select the check box next to all the alarm severity types for which you want e-mail notifications sent. | ||
| Step 6 | In the To text box, enter the e-mail address or addresses to which you want the e-mail notifications sent. Separate e-mail addresses by commas. | ||
| Step 7 | Click
OKSave.
You are returned to the Alarms > Notification page. The changes to the reported alarm severity levels and the recipient e-mail address for e-mail notifications are displayed. |
Working with Events
You can use Prime Infrastructure to view the Mobility Services Engine and location notification events. You can search and display events based on their severity (critical, major, minor, warning, clear, and info) and their category.
This section contains Displaying location notification events procedure.
Displaying Location Notification Events
To display location notification events, follow these steps:
| Step 1 | Choose Monitor > Events. | ||
| Step 2 | In the Events page, you can perform the following:
| ||
| Step 3 | If Prime Infrastructure finds events that match the search criteria, it shows a list of these events.
|
Working with Logs
This section describes how to configure logging options and how to download log files.
Guidelines and Limitations
Configuring Logging Options
You can use Prime Infrastructure to specify the logging level and types of messages to log.
| Step 1 | Choose Services > Mobility ServicesMobility Services Engines. | ||
| Step 2 | Click the name of the MSE that you want to configure. | ||
| Step 3 | From the System menu, choose Logs. The logging options for the selected MSE appear. | ||
| Step 4 | Choose the appropriate
options from the Logging Level drop-down list.
There are four logging options: Off, Error, Information, and Trace. All log records with a log level of Error or above are logged to a new error log file locserver-error-%u-%g.log. This is an additional log file maintained along with the location server locserver-%u-%g.log log file. The error log file consists of logs of Error level along with their context information. The contextual information consists of 25 log records prior to the error. You can maintain up to 10 error log files. The maximum size allowed for each log file is 10 MB.
| ||
| Step 5 | Select the Enable check box next to each element listed in that section to begin logging of its events. | ||
| Step 6 | Select the
Enable check box under
Advanced Parameters to enable advanced debugging. By default, this option is
disabled.
| ||
| Step 7 | To download log files from the server, click Download Logs. For more information, see the Downloading Log Files, page 10-9. | ||
| Step 8 | In the Log File group box, enter the following: | ||
| Step 9 | In the MAC Address Based
Logging page, do the following:
| ||
| Step 10 | Click Save to apply your changes. |
MAC address-based Logging
This feature allows you to create log files that are specific to an entity whose MAC address is specified. The log files are created in the locserver directory under the following path:
/opt/mse/logs/locserver
A maximum of 5 MAC addresses can be logged at a time. The log file format for MAC address aa:bb:cc:dd:ee:ff is:
macaddress-debug-aa-bb-cc-dd-ee-ff.log
You can create a maximum of two log files for a MAC address. The two log files may consist of one main and one back up or rollover log file.
The minimum size of a MAC log file is 10 MB. The maximum size allowed is 20 MB per MAC address. The MAC log files which are not updated for more than 24 hours are pruned.
Downloading Log Files
If you need to analyze Mobility Services Engine log files, you can use Prime Infrastructure to download them to your system. The Prime Infrastructure downloads a .zip file containing the log files.
To download a .zip file containing the log files, follow these steps:
| Step 1 | Choose Services > Mobility Services. |
| Step 2 | Click the name of the Mobility Services Engine to view its status. |
| Step 3 | From the left sidebar menu, choose Logs. |
| Step 4 | Click Download Logs. |
| Step 5 | Follow the instructions in the File Download dialog box to view the file or save the .zip file to your system. |
Generating Reports
In the Prime Infrastructure, you can generate various kinds of reports. This section explains how to generate Context Aware reports using the Prime Infrastructure Report Launch Pad. By default, reports are stored on the Prime Infrastructure server.
Once you define the report criteria, you can save the reports for future diagnostic use and run them on either an ad hoc or scheduled basis.
You can define the following criteria for the reports:
Report Launch Pad
The report launch pad provides access to all the Prime Infrastructure reports from a single page. In this page, you can view current reports, open specific types of reports, create and save new reports, and manage scheduled runs. You can access the ContextAware reports section in the Report Launch Pad to generate ContextAware reports.
 Tip | Hover your mouse cursor over the tool tip next to the report type to view more report details. |
- Creating and Running a New Report
- Managing Current Reports
- Managing Scheduled Run Results
- Managing Saved Reports
Creating and Running a New Report
To create and run a new report, follow these steps:
| Step 1 | Choose
Reports
>
Report Launch
Pad.
The reports are listed by category in the main section of the page and on the left sidebar menu. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 2 | Find the
appropriate report in the main section of the Report Launch Pad.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 3 | Click New. The Report Details page appears. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 4 | In the Report
Details page, enter the following Settings parameters:
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 5 | If you plan to
run this report at a later time or as a recurring report, enter the Schedule
parameters. The Schedule parameters allow you to control when and how often the
report runs.
The Create Custom Report page allows you to customize the report results. For the more information on the customizable reports, see Cisco Prime Infrastructure User Guide. The following table specifies which reports are customizable, which have multiple sub-reports, and which report views are available. In future releases, all reports are customizable.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 6 | Click
Customize
to open a separate Create Custom Report page.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 7 | When all
report parameters have been set, choose one of the following:
|
Managing Current Reports
If a report has been saved for a specific report type, you can access the current reports from the Report Launch Pad.
When a new chokepoint is created, it is available in all the virtual domains. After placing it on a floor, it is updated so that it is available in the same virtual domain as that of a floor. When a chokepoint is removed from a floor, it will be available in all the virtual domains again.
To access current or saved reports from the Report Launch Pad, follow these steps:
| Step 1 | Choose Reports > Report Launch Pad |
| Step 2 | Choose the specific report from the left sidebar menu or from the main section of the Report Launch Pad. The Report Launch Pad page displays a list of current reports for this report type. To view a list of saved reports, choose Reports > Saved Reports. |
Managing Scheduled Run Results
 Note | The list of scheduled runs can be sorted by report category, report type, and time frame. |
Sorting Scheduled Run Results
You can use the Show drop-down list to sort the Scheduled Run Results by category, type, and time frame:
- Report Category—Choose the appropriate report category from the drop-down list or choose All.
- Report Type—Choose the appropriate report type from the drop-down list or choose All. The report Type selections change depending on the selected report category.
- From/To—Type the report start (From) and end (To) dates in the text boxes, or click the calendar icons to select the start and end dates.
- Report Generation method—Choose the appropriate report generation method from the drop-down list. The possible methods are Scheduled, On-demand Export, and On-demand Email.
Click Go to sort this list. Only reports that match your criteria appear.
Viewing or Editing Scheduled Run Details
| Step 1 | Choose Report > Scheduled Run Results. |
| Step 2 | Click the Report Title link for the appropriate report to open the Report Details page. |
| Step 3 | In this page, you can view or edit the details for the scheduled run. |
| Step 4 | When all scheduled run parameters have been edited (if necessary), select from the following: |
- Save—Click Save to save this schedule run without immediately running the report. The report automatically runs at the scheduled time.
- Save and Run—Click Save and Run to save this scheduled run and to immediately run the report.
- Cancel—Click Cancel to return to the previous page without running nor saving this report.
- Delete—Click Delete to delete the current saved report.
Managing Saved Reports
In the Saved Reports page, you can create and manage saved reports. To open this page in the Prime Infrastructure, choose Reports > Saved Reports.
 Note | The list of saved reports can be sorted by report category, report type, and scheduled status (enabled, disabled, or expired). |
The Saved Reports page shows the following information:
- Report Title—Identifies the user-assigned report name. Click the report title to view the details for this report.
- Report Type—Identifies the specific report type.
- Scheduled—Indicates whether this report is enabled or disabled.
- Next Schedule On—Indicates the date and time of the next scheduled run for this report.
- Last Run—Indicates the date and time of the most recent scheduled run for this report.
- Download—Click the Download icon to open or save a .csv file of the report results.
- Run Now—Click the Run Now icon to immediately run the current report.
Sorting Saved Reports
You can use the Show drop-down lists to sort the Saved Reports list by category, type, and scheduled status.
- Report Category—Choose the appropriate report category from the drop-down list or choose All.
- Report Type—Choose the appropriate report type from the drop-down list or choose All. The Report Type selections change depending on the selected report category.
- Scheduled—Choose All, Enabled, Disabled, or Expired to sort the Saved Reports list by scheduled status.
Figure 1. Sorting Saved Reports 
Click Go to sort this list. Only reports that match your criteria appear.
Viewing or Editing Saved Report Details
| Step 1 | Choose Report > Saved Reports. |
| Step 2 | Click the Report Title link for the appropriate report to open the Report Details page. |
| Step 3 | In the Report Details page, you can view or edit the details for the saved report. |
| Step 4 | When all report parameters have been edited, choose one of the following:
|
Generating MSE Analytics Reports
MSE analytics reports are generated based on location history data. This section lists and describes the various MSE analytics reports that you can generate through the Prime Infrastructure Report Launch Pad.
To generate an MSE analytics report, click New next to a type.
Click a report type to view currently saved reports. In this page, you can enable, disable, delete, or run currently saved reports.
This section describes the MSE Analytics report that you can create and contains the following topics:
- Associated vs. Probing Clients by Selected Zone
- Client Location
- Client Location Density
- Device Count by Zone
- Device Dwell Time by Zone
- Guest Location Density
- Location Notifications by Zone
- Mobile MAC Statistics
- Rogue AP Location Density
- Rogue Client Location Density
- Tag Location Tracking
Associated vs. Probing Clients by Selected Zone
This report provides counts for associated vs. probing clients in the selected time period on a selected zone. The first part of the report shows the count in a time series chart and the other part shows the distribution of the clients on the floor.
This section contains the following topics:
Client Location
This report shows historical location information of a wireless client detected by an MSE.
 Note | The Client Location report is not filtered in the non-root virtual domain. |
This section contains the following topics:
Configuring a Client Location History Report
The client location history report results are available only in the root domain. To configure a client location history report, follow these steps:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report By—By default, Client MAC Address is selected.
- Report Criteria—Click Edit and enter a valid MAC address as the filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or click Close to return to the previous page.
Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters. See the Managing Saved Reports for more information on scheduling a report.
Customize Report Form
The Customize Report form allows you to customize the report results. See the Managing Saved Reports for more information on customizing report results.
 Note | Fixed columns appear in blue font and cannot be moved to the available columns. |
Client Location Results
The results of the Client Location History report contain the following information:
- Last Located—The time when the client was located.
- Client Location—The position of the client at the located time.
- MSE—The name of the MSE that located this client.
- User—The username of the client.
- Detecting Cisco WLCs—The IP address of the detecting controller.
- 802.11 State—The state of 802.11. It can be either Probing or Associated.
- IP Address—The IP address of the client.
- AP MAC Address—The MAC address of the associated access point.
- Authenticated—Whether authenticated or not. This can be either Yes or No.
- SSID—The SSID used by the client.
- Protocol—The protocol used to retrieve the information from the client.
 Note | The location field in this report is a hyperlink, and clicking the hyperlink shows the location of the client in the floor map at the located time. If the previous and current client location calculation is greater than 20 feet which is a configurable parameter, then the location history report is updated. This calculation is done every 30 to 120 seconds depending on the client. |
Client Location Density
This report shows wireless clients and their locations detected by the MSEs based on your filtering criteria.
This section contains the following topics:
Configuring a Client Location Density Report
The client location history report results are available only in the root domain. To configure a Client Location History report, follow these steps:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report By
- Report Criteria—The report criteria differ based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or click Close to return to the previous page.
- Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters.
Customize Report Form
The Customize Report form allows you to customize the report results.
 Note | Fixed columns appear in blue font and cannot be moved to the available columns. |
Client Location Density Results
The results of the Client Location Density report contain the following information:
- Last Located—The time when the client was last located during the selected Report Time criteria.
- MAC Address—The MAC address of the client.
- Client Location—The position of the client at the located time.
- MSE—The name of the MSE that located the client.
- User—The username of the client.
- Detecting Cisco WLCs—The IP address of the detecting controller.
- 802.11 State—The state of 802.11. It can be Probing or Associated.
- IP Address—The IP address of the client.
- SSID—The SSID used by the client.
-
Protocol—The
protocol used to retrieve the information from the client.

Note
The location field in this report is a hyperlink, and clicking that hyperlink shows the location of the client in the floor map at the located time.
Device Count by Zone
This report provides the count of devices detected by an MSE in the selected zone.
This sections contains the following topics:
Configuring a Device Dwell by Zone Report
This section describes how to configure a Device Dwell Count Time by Zone report and contains the following topics:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report By
- Report Criteria—The report criteria differ based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or click Close to return to the previous page.
- Device Type
- Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last see. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters.
Customize Report Form
The Customize Report form allows you to customize the report results.
 Note | Fixed columns appear in blue font and cannot be moved to the Available columns. |
Device Count by Zone Results
The results of the Device Count by Zone report contain the following information:
Device Dwell Time by Zone
This report provides the Dwell Time Report for a device detected by an MSE.
Configuring a Device Dwell by Zone Report
This section describes how to configure a Device Dwell Count Time by Zone report and contains the following topics:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report By
- Report Criteria—The report criteria differ based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or click Close to return to the previous page.
- Device Type
- Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last see. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters.
Customize Report Form
The Customize Report form allows you to customize the report results.
 Note | Fixed columns appear in blue font and cannot be moved to the Available columns. |
Device Count by Zone Results
The results of the Device Count by Zone report contain the following information:
Guest Location Density
This report shows guest clients and their locations detected by the MSEs based on your filtering criteria.
Configuring Guest Location Density
This section contains the following topics:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report by
- Report Criteria—The report criteria differs based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or Close to return to the previous page.
- Reporting Period
- Select the radio button and a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen. The times are in the UTC time zone.
- Schedule If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters. See the Managing Saved Reports for more information.
- Customize Report Form The Customize Report form allows you to customize the report results. See the Managing Saved Reports for more information on scheduling a report.
Guest Location Density Results
The results of the Guest Location Tracking report contains the following information:
- Last Located—The time when the guest client was last located during the selected Report Time criteria.
- Guest Username—The login name of the guest client user.
- MAC Address—The MAC address of the guest client.
- Guest Location—The position of the guest client at the located time.
- MSE—The name of the MSE that located this guest client.
- Detecting Controllers—The IP address of the detecting controller.
- IP Address—The IP address of the guest client.
- AP MAC Address—The MAC address of the access point to which the guest client is associated.
- SSID—The SSID used by the guest client.
- Protocol—The protocol used to retrieve the information from the guest client.

NoteThe location field in this report is a hyperlink and clicking that hyperlink shows the location of the guest in the floor map at the located time.
Location Notifications by Zone
This report shows Context-Aware notifications generated by MSEs.
This section contains the following topics:
Configuring a Location Notification Report
This section describes how to configure a Rogue Client Location Tracking report.
- Report Title—If you plan to save this report, enter a report name.
- Report by
- Report Criteria—The report criteria differs based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or Close to return to the previous page.
- Reporting Period
- Select the radio button and a period of time from the drop-down list. Or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters. See the Managing Saved Reports for more information on scheduling a report.
Customize Report Form
The Customize Report form allows you to customize the report results. See the Managing Saved Reports for more information on customizing report results.
 Note | Fixed columns appear in blue font and cannot be moved to the Available columns. |
Location Notification Results
The results of Location Notification report contains the following information:
- Last Seen—The date and time when the device was last located.
- MAC Address—The MAC address of the device.
- Device Type—The type of the device.
- Asset Name—The name of the asset.
- Asset Group—The name of the asset group.
- Asset Category—The name of the asset category.
- Map Location—The map location where the device was located.
- serverName—The name of the server that sends the ContextAware notifications.
Mobile MAC Statistics
This report shows the most active mobile Mac statistics based on click count by MSAP servers or by venues.
Configuring Mobile MAC Statistics
This section describes how to configure a Mobile MAC Statistics report and contains the following topics:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report By
- Report Criteria—The report criteria differs based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or Close to return to the previous page.
- Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the calendar icon to choose a date. Select the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters. See the Managing Saved Reports for more information on scheduling a report.
Customize Report Form
The Customize Report form allows you to customize the report results. See the Managing Saved Reports for more information on customizing report results.
 Note | Fixed columns appear in blue font and cannot be moved to the Available columns. |
Mobile MAC Tracking Results
The results of the Mobile MAC Statistics report contain the following information:
 Note | The location field in this report is a hyperlink and clicking that hyperlink shows the location of the rogue AP in the floor map at the located time. |
Rogue AP Location Density
This report shows Rogue APs and their locations detected by the MSEs based on your filtering criteria.
This section contains the following topics:
Configuring Rogue AP Location Density
This section describes how to configure a rogue AP location density report and contains the following topics:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report By
- Report Criteria—The report criteria differs based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or Close to return to the previous page.
- Device Type
- Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters. See the Managing Saved Reports for more information on scheduling a report.
Customize Report Form
The Customize Report form allows you to customize the report results. See the Managing Saved Reports for more information on customizing report results.
 Note | Fixed columns appear in blue font and cannot be moved to the Available columns. |
Rogue Client Location Density
This report shows rogue client location density detected by the MSEs based on your filtering criteria.
Configuring Rogue Client Location Density
This section describes how to configure a Rogue Client Location Density and contains the following topics:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report by
- Report Criteria—The report criteria differs based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or Close to return to the previous page.
- Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Reporting Period
- Select the radio button and choose a period of time from the drop-down list. or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the Calendar icon to choose a date. Choose the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters. See the Managing Saved Reports for more information on scheduling a report.
Customize Report Form
The Customize Report form allows you to customize the report results. See the Managing Saved Reports for more information on customizing report results.
 Note | Fixed columns appear in blue font and cannot be moved to the available columns. |
Rogue Client Location Tracking Results
The results of Rogue Client Location Tracking report contains the following information:
- Last Located—The time when the rogue client was last located during the selected Report Time criteria.
- MAC Address—The MAC address of the rogue client.
- Rogue Client Location—Position of the rogue client at the located time.
- MSE—Name of the MSE that located this rogue client.
- Rogue AP—The rogue access point to which the rogue client is associated with.
- Detecting Cisco WLCs—The IP address of the detecting controller.
-
State—State of the Rogue
client.

Note
The location field in this report is a hyperlink and clicking that hyperlink shows the location of the rogue client in the floor map at the located time.
Tag Location Tracking
This report shows the location tracking of a tag detected by an MSE.
This section contains the following topics:
Configuring Tag Location Tracking
This section describes procedures to configure a Tag Location Tracking report and contains the following topics:
Settings
- Report Title—If you plan to save this report, enter a report name.
- Report by
- Report Criteria—The report criteria differs based on the Report By option selected. Click Edit and select the required filter criteria.

NoteIn the Report Criteria page, click Select to confirm your filter criteria or Close to return to the previous page.
- Reporting Period
- Select the radio button and a period of time from the drop-down list. Or
- Select the From radio button and enter the From and To dates and times. You can type a date in the text box, or click the calendar icon to choose a date. Select the hours and minutes from the drop-down lists.

NoteThe reporting period is based on the alarm last seen time. The times are in the UTC time zone.
Schedule
If you plan to run this report at a later time or as a recurring report, enter the scheduling parameters. See the Managing Saved Reports for more information on scheduling a report.
Customize Report Form
The Customize Report form allows you to customize the report results. See the Managing Saved Reports for more information on customizing report results.
 Note | Fixed columns appear in blue font and cannot be moved to the Available columns. |
Tag Location Tracking Results
The results of the Tag Location Tracking report contain the following information:
- Last Located—The time when the tag was last located during the selected Report Time criteria.
- Tag Location—The position of the tag at the located time.
- MSE—The name of the MSE that located this tag.
- Detecting Controller—The IP address of the detecting controller.
- Vendor—The name of the tag vendor.
- Battery Status—The status of the battery of that tag.
 Note | The location field in this report is a hyperlink and clicking that hyperlink shows the location of the tag in the floor map at the located time. |
Creating a Device Utilization Report
To create a device utilization report for the Mobility Services Engine, follow these steps:
| Step 1 | Choose Reports > Report Launch Pad. | ||||
| Step 2 | Choose Device > Utilization. | ||||
| Step 3 | Click New. The Utilization Report Details page appears. | ||||
| Step 4 | In the Reports Details page,
enter the following Settings parameters:
| ||||
| Step 5 | In the Schedule group box, select the Enable Schedule check box. | ||||
| Step 6 | Choose the report format (CSV or PDF) from the Export Report drop-down list. | ||||
| Step 7 | Select either
File or
Email
as the destination of the report.
| ||||
| Step 8 | Enter a start date (MM:DD:YYYY), or click the Calendar icon to select a date. | ||||
| Step 9 | Specify a start time using the hour and minute drop-down lists. | ||||
| Step 10 | Select the
Recurrence radio button to determine how often you want to
run the report. The possible values follow:
| ||||
| Step 11 | When finished
with
Step 1 to
Step 10, do one of
the following:
If the report is scheduled, it is shown as enabled and the next scheduled run date is noted. If the report has run and is not scheduled to run again, it is shown as expired. If the report has run and is scheduled to run again, it is shown as disabled. | ||||
| Step 12 | To enable, disable, or delete a report, select the check box next to the report title, and click the appropriate option. |
Viewing Saved Utilization Reports
Viewing Scheduled Utilization Runs
To review the status for a scheduled report, follow these steps:
Managing OUI
The Prime Infrastructure relies on the IEEE Organizational Unique Identifier (OUI) database to identify the client vendor name mapping. Prime Infrastructure stores vendor OUI mappings in an XML file named vendorMacs.xml. With the OUI update, you can perform the following:
Adding a New Vendor OUI Mapping
The User Defined OUI List page displays a list of vendor OUI mappings that you created. This page allows you to add a new vendor OUI mapping, delete an OUI entry, and update the vendor name for an OUI that is existing in the vendorMacs.xml file.
When you add an OUI, Prime Infrastructure verifies the vendorMacs.xml file to see if the OUI exists. If the OUI exists, Prime Infrastructure updates the vendor name for the OUI. If the OUI does not exists, Prime Infrastructure adds a new OUI entry to the vendor OUI mapping.
To add a new vendor OUI mapping, follow these steps:
| Step 1 | Choose Administration > System Settings. |
| Step 2 | From the left sidebar menu, choose User Defined OUI. The User Defined OUI page appears. |
| Step 3 | From the Select a Command drop-down list, choose Add OUI Entries, and Click Go. |
| Step 4 | In the OUI field, enter a valid OUI. The format is aa:bb:cc. |
| Step 5 | Click Check to verify if the OUI exists in the vendor OUI mapping. |
| Step 6 | In the Name field, enter the display name of the vendor for the OUI. |
| Step 7 | Select the Change Vendor Name check box to update the display name of the vendor, if the OUI exists in the vendor OUI mapping. |
| Step 8 | Click OK. |
| Step 9 | After adding new OUIs, you must restart the Prime Infrastructure server to make changes into effect. You can use the following commands to shut down and restart the Prime Infrastructure server. |
Uploading an Updated Vendor OUI Mapping File
You can download and save the vendorMacs.xml file posted on cisco.com to a local directory using the same filename, vendorMacs.xml. You can then, upload the file to Prime Infrastructure. Prime Infrastructure replaces the existing vendorMacs.xml file with the updated file and refreshes the vendor OUI mapping. However, it does not override the new vendor OUI mapping or the vendor name update that you made.
To upload the updated vendor OUI mapping file, follow these steps:
Monitoring Wireless Clients
This section describes about monitoring wireless clients and contains the following topics:
Monitoring Wireless Clients Using Maps
On a Prime Infrastructure map, you can view the name of the access point that the client is associated with, the IP Address, Asset information, Authentication, SSID, 802.11 protocol, and when the location information was last updated for the client. Hover mouse cursor over the client icon on the map to display this information.
You can also view the client details page, that provides statistics (such as client association, client RSSI, and client SNR), packets transmitted and received values, events, and security information for that client.
To determine the location status of a client on a map and view its client details page using maps, follow these steps:
| Step 1 | Choose Monitor > Site Maps. | ||||
| Step 2 | Choose the building and floor on which the mobility services engine and its clients are located. | ||||
| Step 3 | Select the Clients check box in the Floor Settings left sidebar menu if it is not already selected. Do not click Save Settings unless you want to save changes made to the floor settings across all maps. 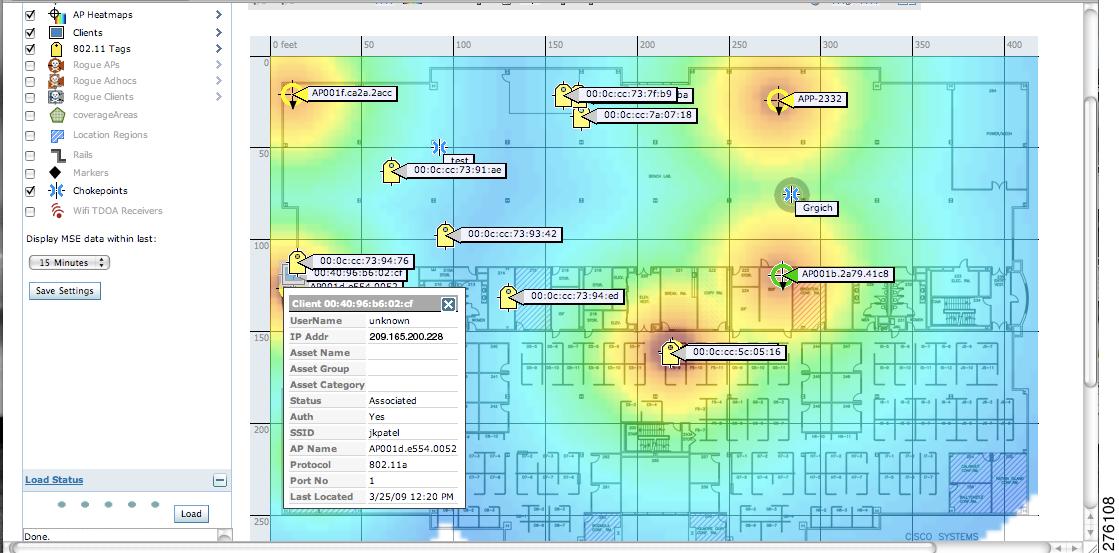
| ||||
| Step 4 | Hover mouse cursor over a client icon (blue square) and a summary of its configuration appears in a pop-up dialog box.
| ||||
| Step 5 | Click the Client icon to see client details. 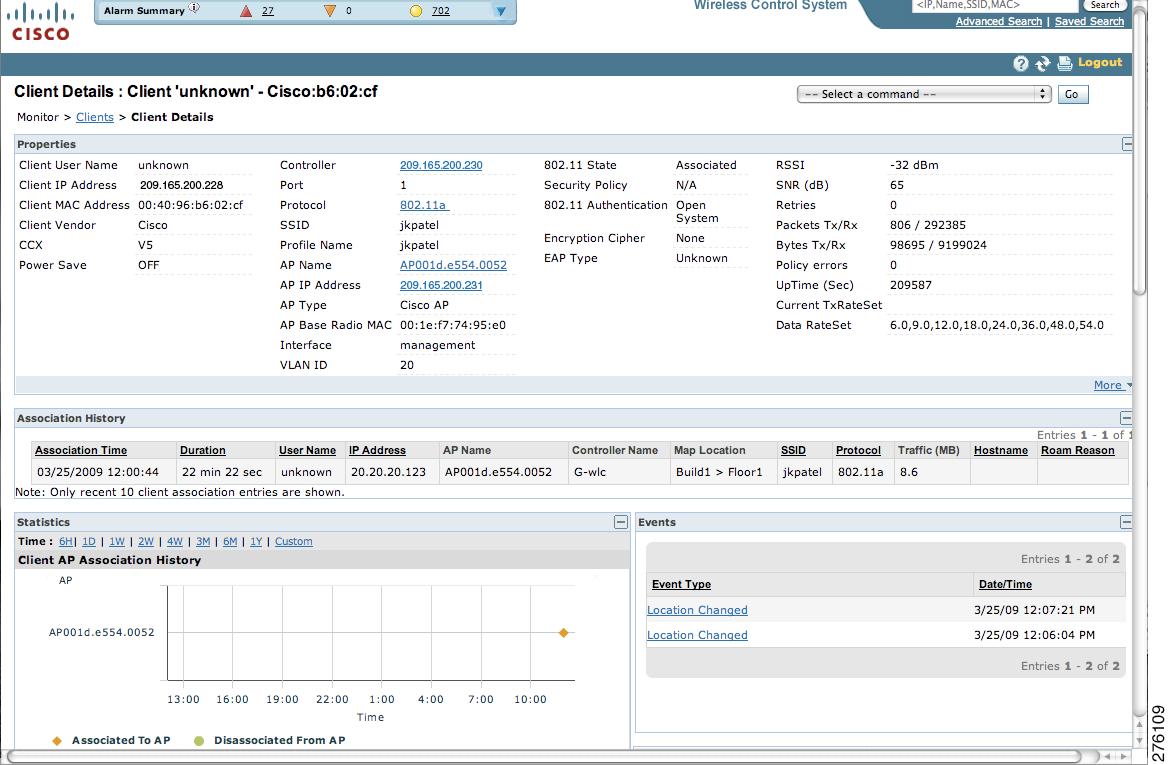 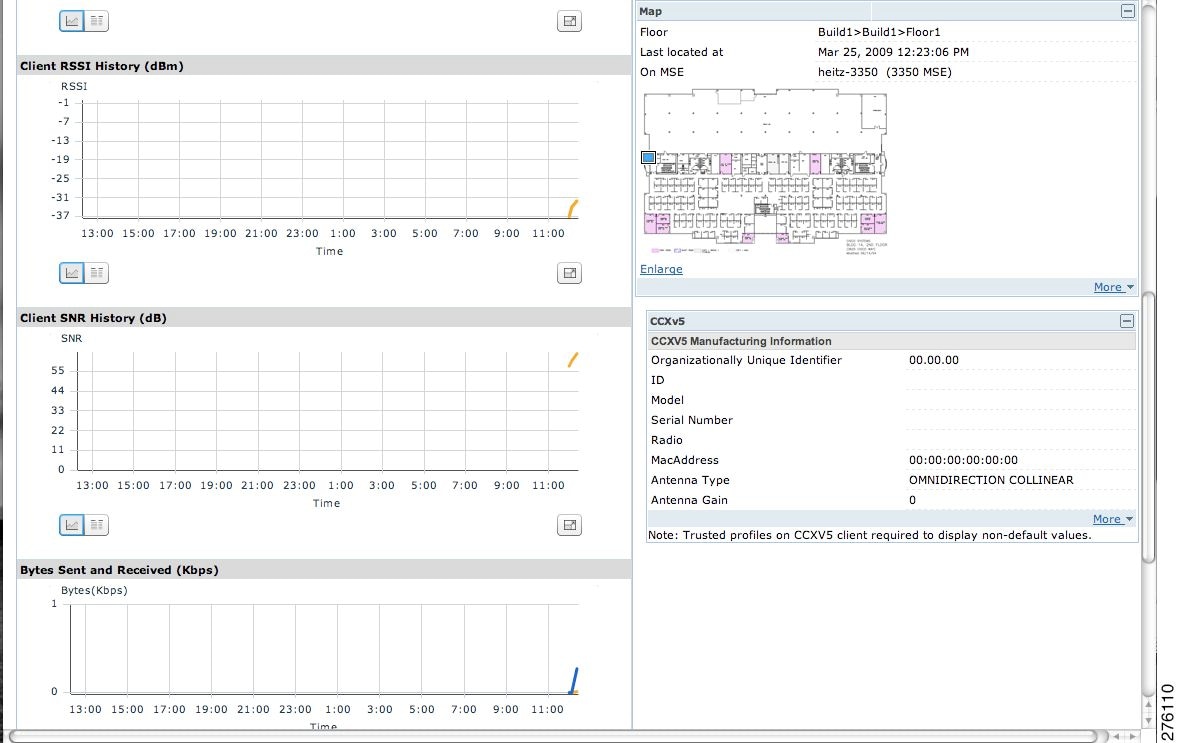 | ||||
| Step 6 | Click the More link to configure asset information for the client. |
Monitoring Wireless Clients Using Search
To view client information, follow these steps:
| Step 1 | Choose Monitor > Clients. The Clients summary page appears. | ||
| Step 2 | From the Show drop-down list, choose Clients Detected by MSEs. Click Go. A summary of all clients detected by mobility services engines and location appliances managed by Prime Infrastructure is displayed (see Figure 11-6). The clients detected by MSE is a union of wired and wireless clients. Location information is stored only for wireless clients in MSE but not for wired clients. Hence, in order to filter clients by virtual domain, switch ports must be assigned to floors in the given virtual domain in order to view the wired clients, otherwise only wireless clients are listed here.
|
Client Support on the MSE
You can use the Prime Infrastructure Advanced Search feature to narrow the client list based on specific categories and filters. You can also filter the current list using the Show drop-down list.
- Searching a Wireless Client from the Prime Infrastructure on the MSE by IPv6 Address
- Viewing the Clients Detected by the MSE
Searching a Wireless Client from the Prime Infrastructure on the MSE by IPv6 Address
To search for an MSE-located client using the Prime Infrastructure Advanced Search feature, follow these steps:
| Step 1 | Click Advanced Search located in the top right corner of the Prime Infrastructure UI. | ||
| Step 2 | In the New Search dialog, choose Clients as the search category from the Search Category drop-down list. | ||
| Step 3 | From the Media Type drop-down
list, choose
Wireless Clients.
| ||
| Step 4 | From the Wireless Type drop-down list, choose any of the following types: All, Lightweight, or Autonomous Clients. | ||
| Step 5 | From the Search By drop-down
list, choose
IP Address.
| ||
| Step 6 | From the Clients Detected By
drop-down list, choose
clients detected by MSE.
This shows clients located by Context-Aware Service in the MSE by directly communicating with the Cisco WLCs. | ||
| Step 7 | From the Last detected within drop-down list, choose the time within which the client was detected. | ||
| Step 8 | Enter the client IP address
in the Client IP Address text box. You can enter wither a partial or full IPv6
address.
| ||
| Step 9 | From the Client States drop-down list, choose the client states. The possible values for wireless clients are All States, Idle, Authenticated, Associated, Probing, or Excused. The possible values for wired clients are All States, Authenticated, and Associated. | ||
| Step 10 | From the Posture Status drop-down list, choose the posture status to know if the devices are clean or not. The possible values are All, unknown, Passed, and Failed. | ||
| Step 11 | Select the CCX Compatible check box to search for clients that are compatible with Cisco Client Extensions. The possible values are All Versions, V1, V2, V3, V4, V5, and V6. | ||
| Step 12 | Select the E2E Compatible check box to search for clients that are End to End compatible. The possible values are All Versions, V1, and V2. | ||
| Step 13 | Select the NAC State check box to search for clients identified by a certain Network Admission Control (NAC) state. The possible values are Quarantine, Access, Invalid, and Not Applicable. | ||
| Step 14 | Select the Include Disassociated check box to include clients that are no longer on the network but for which Prime Infrastructure has historical records. | ||
| Step 15 | From the Items per page drop-down list, choose the number of records to be displayed in the search results page. | ||
| Step 16 | Select the Save Search check box to save the selected search option. | ||
| Step 17 | Click
Go.
The Clients and Users page appears with all the clients detected by the MSE. |
Viewing the Clients Detected by the MSE
To view all the clients detected by MSE, follow these steps:
| Step 1 | Choose
Monitor >
Clients and Users to view
both wired and wireless clients information.
The Client and Users page appears. The Clients and Users table
shows a few column by default. If you want to display the additional columns
that are available, click
| ||||||||
| Step 2 | Filter the current list to
choose all the clients that are detected by MSE by choosing
Clients detected by
MSE from the Show
drop-down list.
All the clients detected by MSE including wired and wireless appear. All the clients detected by MSE including wired and wireless appear. The following different parameters are available in the Clients Detected by MSE table:
When you choose a client from the Clients and Users list, the following client details are displayed. Clients are identified using the MAC address.
The Statistics group box contains the following information for the selected client:
This information is presented in interactive graphs. Client IPV6 Addresses The Client IPv6 Address group box contains the following information for the selected client:
The Events group box in the Client Details page displays all events for this client including the event type as well as the date and time of the event: Click View Location History to view the location history details of wired and wireless clients. The following location history information is displayed for a wired or wireless client: |
Configuring Buildings
You can add buildings to the Prime Infrastructure database regardless of whether you have added campus maps to the database. This section describes how to add a building to a campus map or a standalone building (one that is not part of a campus) to the Prime Infrastructure database.
- Adding a Building to a Campus Map
- Viewing a Building
- Editing a Building
- Deleting a Building
- Moving a Building
Adding a Building to a Campus Map
To add a building to a campus map in the Prime Infrastructure database, follow these steps:
| Step 1 | Choose Monitor > Site Maps to display the Maps page. |
| Step 2 | Click the desired campus. The Site Maps > Campus Name page appears. |
| Step 3 | From the Select a command drop-down list, choose New Building, and click Go. |
| Step 4 | In the Campus Name > New Building page, follow these steps to create a virtual building in which to organize related floor plan maps: |
| Step 5 | (Optional) To assign location presence information for the new outdoor area, do the following: |
| Step 6 | Click Save. |
Adding a Standalone Building
To add a standalone building to the Prime Infrastructure database, follow these steps:
| Step 1 | Choose Monitor > Site Maps to display the Maps page. | ||
| Step 2 | From the Select a command drop-down list, choose New Building, and click Go. | ||
| Step 3 | In the Maps > New Building page, follow these steps to create a virtual building in which to organize related floor plan maps: | ||
| Step 4 | (Optional) To assign location presence information for the new building, do the following: | ||
| Step 5 | Click Save.
|
Viewing a Building
To view a current building map, follow these steps:
| Step 1 | Choose Monitor > Site Maps. | ||
| Step 2 | Click the name of the building map to open its details page. The Building View page provides a list of floor maps and map details for each floor.
The map details include the following:
| ||
| Step 3 | The Select a command drop-down list provides the following options:
|
Editing a Building
To edit a current building map, follow these steps:
| Step 1 | Choose Monitor > Site Maps. | ||
| Step 2 | Click the name of the building map to open its details page. | ||
| Step 3 | From the Select a command drop-down list, choose Edit Building. | ||
| Step 4 | Make any necessary changes to Building Name, Contact, Number of Floors, Number of Basements, and Dimensions (feet).
| ||
| Step 5 | Click OK. |
Deleting a Building
To delete a current building map, follow these steps:
| Step 1 | Choose Monitor > Site Maps. | ||
| Step 2 | Select the check box for the building that you want to delete. | ||
| Step 3 | Click Delete at the bottom of the map list (or choose Delete Maps from the Select a command drop-down list, and click Go). | ||
| Step 4 | Click OK to confirm the deletion.
|
Moving a Building
To move a building to a different campus, follow these steps:
| Step 1 | Choose Monitor > Site Maps. |
| Step 2 | Select the check box of the applicable building. |
| Step 3 | From the Select a command drop-down list, choose Move Buildings. |
| Step 4 | Click Go. |
| Step 5 | Choose the Target Campus from the drop-down list. |
| Step 6 | Select the buildings that you want to move. Unselect any buildings that remain in their current location. |
| Step 7 | Click OK. |
Monitoring Tags
You can monitor tag status and location on the Prime Infrastructure maps as well as review tag details in the Monitor > Tags page. You can also use the Advanced Search to monitor tags.
Monitoring Tags Using Maps
On an Prime Infrastructure map, you can view the name of the access point that generated the signal for a tagged asset, its strength of signal, and when the location information was last updated for the asset. Hover your mouse cursor over the tag icon on the map to display this information.
| Step 1 | Choose Monitor > Maps. | ||
| Step 2 | Choose the building and floor on which the mobility services engine and tag are located. | ||
| Step 3 | Select the 802.11 Tags check box in the Floor Settings menu if it is not already selected.
| ||
| Step 4 | Hover your mouse cursor over a tag icon (yellow tag) and a summary of its configuration appears in a Tag dialog box. | ||
| Step 5 | Click the tag icon to see tag details. You can also configure the asset information by entering the required information in the Asset Info group box. | ||
| Step 6 | To see location history for the tag, choose Location History from the Select a command drop-down list. Click Go . |
Monitoring Tags Using Search
You can search for tags by asset type (name, category and group), MAC address, system (Cisco WLC or MSE), and area (floor area and outdoor area).
You can further refine your search using the Advanced Search parameters and save the search criteria for future use. Click Saved Searches to retrieve saved searches.
When you click the MAC address of a tag location in a search results page, the following details appear for the tag:
- Tag vendor
- Cisco WLC to which tag is associated
- Telemetry data (CCX v1-compliant tags only)
- Asset Information (Name, Category, Group)
- Statistics (Bytes and packets received)
- Location (Floor, Last Located, MSE, map)
- Location Notification (Absence, Containment, Distance, All)
- Emergency Data (CCX v1-compliant tags only)
| Step 1 | Choose Monitor > Tags. The Tag Summary page appears. | ||
| Step 2 | To view a summary of tags
associated with a specific MSE, click the
Total Tags link.
| ||
| Step 3 | To search for a specific tag, if you know its MAC address and asset name (not all search values apply to all tags), click the Search link. | ||
| Step 4 | To search for a specific tag
or multiple tags using a broader range of search criteria such as device (MSE
or controller), map location (floor or outdoor area), asset name or category,
or tag vendor, click the
Advanced Search link.
|
Overlapping Tags
When multiple tags are within close proximity of one another, a summary tag is used to represent their location on an Prime Infrastructure map (Monitor > Maps). The summary tag is labeled with the number of tags at that location.
When you hover your mouse cursor over the overlapping tag on the map, a dashlet appears with summary information for the overlapping tags.
Select the Prev and Next links to move between the individual tag summary dashlets. To see detailed information on a specific tag, select the Details link while viewing the summary information of the tag.
Summary information for tags includes Tag MAC address, Asset Name, Asset Group, Asset Category, Vendor (Type), Battery Life, and Last Located data (date and time). If the tag is Cisco CX v.1 compliant, telemetry information also appears.
Monitoring Geo-Location
The MSE provides physical location of wired clients, wired endpoints, switches, Cisco WLCs, and access points present in a wireless network deployment. Currently, MSE provides location information in geo-location format to the external entities through northbound and southbound entities.
To improve the accuracy of the geo-location information provided by MSE, this feature aims to transform the geometric location co-ordinates of a device to geo-location coordinates (latitude and longitude) and provides it to the external entities through northbound and southbound interfaces.
 Note | At least three GPS markers are required for geo-location calculation. The maximum number of GPS markers that you can add is 20. |
Adding a GPS Marker to a Floor Map
To add a GPS marker to a floor map, follow these steps:
| Step 1 | Choose Monitor > Site Maps to display the Maps page. | ||
| Step 2 | Choose Campus Name > Building Name > Floor Name. | ||
| Step 3 | Choose the Add/Edit GPS Markers Information menu option on the top left menu to open the Add/Edit GPS page. A GPS Marker icon appears on the top left corner of the map (X=0 Y=0). | ||
| Step 4 | You can drag the GPS Marker icon and place it in the desired location on the map or enter the X and Y position values in the GPS Marker Details table on the left sidebar menu to move the marker to the desired position.
| ||
| Step 5 | Enter the Latitude and Longitude degrees for the selected GPS Marker icon in the left sidebar menu. | ||
| Step 6 | Click Save. The GPS Marker information is saved to the database. | ||
| Step 7 | Click Apply to other Floors of Building to copy GPS markers on one floor of a building to all the remaining floors of that building. |
Editing a GPS Marker
To edit a GPS marker present on the floor, follow these steps:
| Step 1 | Choose Monitor > Site Maps to display the Maps page. |
| Step 2 | Choose Campus Name > Building Name > Floor Name. |
| Step 3 | Choose the Add/Edit GPS Markers Information menu option to open the Add/Edit GPS page. |
| Step 4 | Select an existing GPS Marker which is present on the floor from the left sidebar menu. |
| Step 5 | From the left sidebar menu, you can change the Latitude, Longitude, X Position, and Y Position which is associated with the GPS marker. |
| Step 6 | Click Save. The modified GPS marker information is now saved to the database. |
Deleting a GPS Marker From the Floor
To delete a GPS marker from the floor, follow these steps:
| Step 1 | Choose Monitor > Site Maps to display the Maps page. | ||
| Step 2 | Choose Campus Name > Building Name > Floor Name. | ||
| Step 3 | Choose the Add/Edit GPS Markers Information menu option to open the Add/Edit GPS page. | ||
| Step 4 | Select an existing GPS marker that is present on the floor from the left sidebar menu.
| ||
| Step 5 | Click Delete GPS Marker. The selected GPS marker is deleted from the database. |
Monitoring Chokepoints
A chokepoint must be assigned to a map for its location to be monitored. After adding the TDOA receiver to a map, you must resynchronize the network designs (Services > Synchronize Services) with the mobility services engine for it to appear on the map.
When a new chokepoint is created, it is available in all the virtual domains. After placing it on a floor, it is updated so that it is available in the same virtual domain as that of a floor. When a chokepoint is removed from a floor, it will be available in all the virtual domains again.
If the existing chokepoints are on a floor, then they all belong to the same virtual domain as the floor. If the chokepoints are not placed on a floor, then they are available in all virtual domains.
If a chokepoint is not assigned to a map, you are not able to find that chokepoint using Search or Advanced Search. All chokepoint setup is done using the AeroScout System Manager.
 Note | See the AeroScout Context-Aware Engine for Tags, for Cisco Mobility Services Engine Users Guide for configuration details at the following URL: http://support.aeroscout.com. |
To monitor chokepoints, follow these steps:
| Step 1 | Choose Monitor > Chokepoints. The Chokepoint page appears showing all mapped chokepoints. |
| Step 2 | To refine the search criteria when an extensive list appears, search by MAC address or chokepoint name.
|
Monitoring Wi-Fi TDOA Receivers
A Wi-Fi TDOA receiver must be assigned to a map for its location to be monitored. After adding the TDOA receiver to a map, you must resynchronize network designs (Services > Synchronize Services) with the mobility services engine for it to appear on the map.
If a TDOA receiver is not assigned to a map, you cannot find it using Search or Advanced Search.
All TDOA receiver setup is done using the AeroScout System Manager.
When a new TDOA receiver is created, it is available in all the virtual domains. After placing it on a floor, it is updated so that it is available in the same virtual domain as that of the floor. When a TDOA receiver is removed from a floor, it will be available in all the virtual domains again.
If the existing TDOA receivers are on a floor, then they all belong to the same virtual domain as the floor. If the chokepoints are not placed on a floor, then they are available in all virtual domains.
 Note | See the AeroScout Context-Aware Engine for Tags, for Cisco Mobility Services Engine Users Guide for configuration details at the following URL: http://support.aeroscout.com. |
To monitor TDOA receivers, follow these steps:
Ekahau Site Survey Integration
Ekahau Site Survey (ESS) tool is used for designing, deploying, maintaining, and troubleshooting high performance Wi-Fi networks. ESS works over any 802.11 network and is optimized for centrally managed 802.11n Wi-Fi networks.
You can use the ESS tool to import the existing floor maps from the Prime Infrastructure and export the project to the Prime Infrastructure. For more information, see the Cisco Prime Infrastructure Integration section in the ESS online help.
 Note | The Prime Infrastructure site survey calibration requires that you have collected at least 150 survey data points at 50 distinct locations. If you do not have enough survey data points, a warning is given when trying to export the survey data. |
 Note | If there are no access points in the Prime Infrastructure during the site survey, the site survey will not happen. |
 Note | If the floor map scales are incorrect in the Prime Infrastructure, the visualizations in the ESS will be distorted. |
AirMagnet Survey and Planner Integration
AirMagnet survey and AirMagnet planner is integrated with the Cisco Prime Infrastructure. This integration increases the operational efficiencies by eliminating the need to repeat the wireless planning and site survey tasks commonly associated with deployment and management of wireless LAN networks.
The AirMagnet survey tool allows you to export real world survey data to the Prime Infrastructure for calibrating planner modeling. With the AirMagnet planner, you can create and export planner projects directly to the Prime Infrastructure. This enables the Prime Infrastructure to create its own project directly from the imported AirMagnet Planner tool. For more information, see the AirMagnet Survey and Planning documentation which is available at Fluke Networks website.
Monitoring Wired Clients
You can view details on a wired client (MAC address, IP address, username, serial number, UDI, model no., software version, and VLAN ID), its port, and its civic information.
Wired client data is downloaded to the mobility services engine through the Prime Infrastructure when the switch and the mobility services engine are synchronized (Services > Synchronize Services > Switches).
You can view the details of the wired clients in either the Wired Switches page (Context Aware Service > Wired > Wired Switches) or wired clients page (Context Aware Service > Wired > Wired Clients).
- If you know the IP address, MAC address, VLAN ID, serial number, or username, you can use the Search text box in the Wired Clients page.
- If you want to examine wired clients as they relate to a specific switch, you can view that information in the Wired Switches page.
To view details on a wired client, follow these steps:
| Step 1 | Choose Services > Mobility Services Engines. The Mobility Services page appears. | ||
| Step 2 | Click the device name link of the appropriate wired location switch. | ||
| Step 3 | Choose Context Aware Service > Wired > Wired Clients. In the Wired Clients summary page, clients are grouped by their switch. The status of a client is noted as connected, disconnected, or unknown. Definitions are summarized as follows:
| ||
| Step 4 | Click the Port Association tab to show the physical location of the switch port/slot/module on which the wired client terminates, the client status (connected, disconnected, unknown), and the switch IP address. | ||
| Step 5 | Click the Civic Address tab to show any civic address information. | ||
| Step 6 | Click the Advanced tab to see extended physical address details for the wired clients, if any.
|
Monitoring Wired Switches
You can review details on the wired switch (IP address, serial number, software version, and ELIN), its ports, its wired clients (count and status), and its civic information.
Wired switch data is downloaded to the mobility services engine through the Prime Infrastructure when the Ethernet switch and the mobility services engine are synchronized (Services > Synchronize Services > Switches). Communication between a location-capable switch and a mobility services engine occurs over NMSP. The Prime Infrastructure and the MSE communicate over XML.
To view details on wired switches, follow these steps:
| Step 1 | Choose Services > Mobility Services Engines. | ||
| Step 2 | In the Mobility Services page, click the device name link of the appropriate wired location switch. | ||
| Step 3 | Choose Context Aware Service > Wired > Wired Switches. A summary of wired switches that are synchronized with the MSE appears. | ||
| Step 4 | To see more
details on the switch, its ports, its wired clients (count and status), and its
civic information, click the
IP address
link.
You can view detailed wired client information by clicking one of the client count links (total clients, connected, disconnected, and unknown). | ||
| Step 5 | Click the
Switch Ports
tab to see a detailed list of the ports on the switch.
You can change the listing order (ascending, descending) of port IP addresses, slot numbers, module number, and port number by clicking the respective column heading. | ||
| Step 6 | Click the Civic tab to see a detailed list of the civic information for the wired switch. | ||
| Step 7 | Click the Advanced tab to see a detailed list of the additional civic information for the wired switch |
Monitoring Interferers
Monitor > Interferers > AP Detected Interferers
Choose Monitor > Interferers to view all the interfering devices detected by the CleanAir-enabled access points on your wireless network. This page enables you to view a summary of the interfering devices including the following default information:
- Interferer ID—A unique identifier for the interferer. Click this link to learn more about the interferer.
- Type—Indicates the category of the interferer. Click to read more about the type of device. The pop-up dialog appears displaying more details. The categories include the following:
- Bluetooth link—A Bluetooth link (802.11b/g/n only)
- Microwave Owen—A microwave oven (802.11b/g/n only)
- 802.11 FH—An 802.11 frequency-hopping device (802.11b/g/n only)
- Bluetooth Discovery—A Bluetooth discovery (802.11b/g/n only)
- TDD Transmitter—A time division duplex (TDD) transmitter
- Jammer—A jamming device
- Continuous Transmitter—A continuous transmitter
- DECT-like Phone—A Digital Enhanced Cordless Telecommunication (DECT)-compatible phone
- Video—A video camera
- 802.15.4—An 802.15.4 device (802.11b/g/n only)
- WiFi Inverted—A device using spectrally inverted Wi-Fi signals
- WiFi Invalid—A device using non-standard Wi-Fi channels
- SuperAG—An 802.11 SuperAG device
- Canopy—A Motorola Canopy device
- Radar—A radar device (802.11a/n only)
- XBox—A Microsoft Xbox (802.11b/g/n only)
- WiMAX Mobile—A WiMAX mobile device (802.11a/n only)
- WiMAX Fixed—A WiMAX fixed device (802.11a/n only)
- Status—Indicates the status of the interfering device.
- Active—Indicates that the interferer is currently being detected by the CleanAir-enabled access point.
- Inactive—Indicates that the interferer is no longer being detected by the CleanAir-enabled access point or the CleanAir-enabled access point detected that the interferer is no longer reachable by Prime Infrastructure.
- Severity—Shows the severity ranking of the interfering device.
- Affected Band—Shows the band in which this device is interfering.
- Affected Channels—Shows the affected channels.
- Duty Cycle (%)—The duty cycle of interfering device in percentage.
- Discovered—Shows the time at which it was discovered.
- Last Updated—The last time the interference was detected.
- Floor—The location where the interfering device is present.

NoteThese devices appear only if the option to track Interferers is enabled in the Tracking Parameters page. This option is disabled by default. For more information on tracking parameters, see the Modifying Tracking Parameters.
Monitor > Interferers > Edit View
The Edit View page allows you to add, remove, or reorder columns in the AP Detected Interferers Summary page. It also allows you to search for Interferers. By default, only those interferers that are in Active state and with, severity greater than or equal to 5 are displayed in the AP Detected Interferers page.
To edit the columns in the AP Detected Interferers page, follow these steps:
| Step 1 | Choose Monitor > Interferers. The AP Detected Interferers page appears showing details of the interferers detected by the CleanAir-enabled access points. |
| Step 2 | Click the Edit View link in the AP Detected Interferers page. |
| Step 3 | To add an additional column to the access points table, click to highlight the column heading in the left column. Click Show to move the heading to the right column. All items in the right column are displayed in the table. |
| Step 4 | To remove a column from the access points table, click to highlight the column heading in the right column. Click Hide to move the heading to the left column. All items in the left column are not displayed in the table. |
| Step 5 | Use the Up/Down buttons to specify the order in which the information appears in the table. Highlight the desired column heading and click Up or Down to move it higher or lower in the current list. |
| Step 6 | Click Reset to restore the default view. |
| Step 7 | Click Submit to confirm the changes. |
Clustering of Monitor Mode APs Using MSE
Where value is the distance in feet for clustering. The default value is 150.
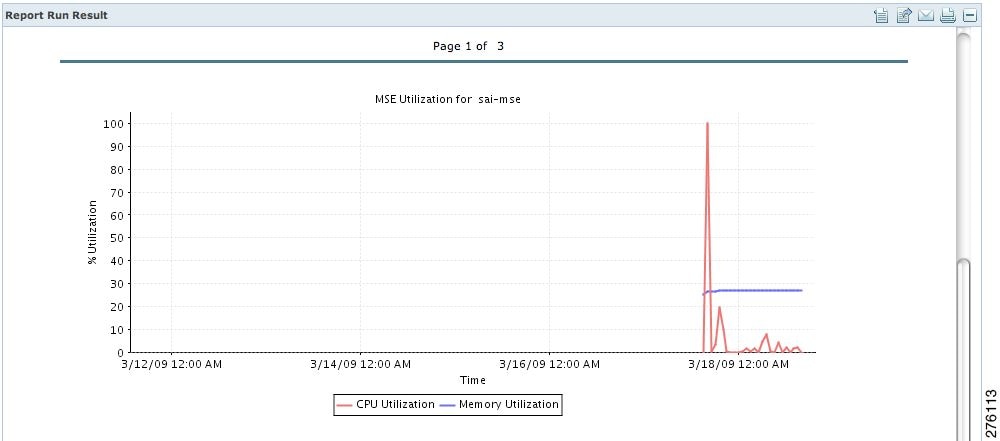
 Feedback
Feedback