Protected management frames with 802.11w
A protected management frame is a wireless security feature that
-
uses the 802.11w protocol to safeguard management frames
-
prevents spoofing and forgery of authentication, de-authentication, association, and disassociation frames, and
-
enhances the overall security of Wi-Fi networks by protecting key network management actions from attack.
While data frames can be encrypted, management frames were traditionally sent in the clear, making them vulnerable to interception and forgery. The 802.11w standard addresses this vulnerability by requiring cryptographic protection for certain management frames between client and access point.
Types of management frames protected by 802.11w
The 802.11w protocol protects certain management frames by using the Protected Management Frames (PMF) service. These frames are classified as robust management frames and include:-
Disassociation frames
-
De-authentication frames
-
Robust Action frames
-
Spectrum Management
-
Quality of Service (QoS)
-
Direct Link Setup (DLS)
-
Block acknowledgement
-
Radio Measurement
-
Fast Basic Service Set (BSS) Transition
-
Security Association (SA) Query
-
Protected Dual of Public Action
-
Vendor-specific Protected
Protections offered by 802.11w
When 802.11w is implemented, these protections are provided:
-
Client protection: The AP adds cryptographic protection to de-authentication and dissociation frames, preventing spoofing in DOS attacks.
-
Infrastructure protection: Security Association (SA) teardown protection is implemented using Association Comeback Time and SA-Query procedures to prevent spoofed association requests from disconnecting connected clients.
Integrity Group Temporal Key (IGTK)
An integrity group temporal key (IGTK) is a wireless security mechanism that
-
protects broadcast and multicast robust management frames.
-
uses random values assigned by the authenticator station (such as a wireless LAN controller), and
-
secures MAC management protocol data units (MMPDUs) in 802.11w networks.
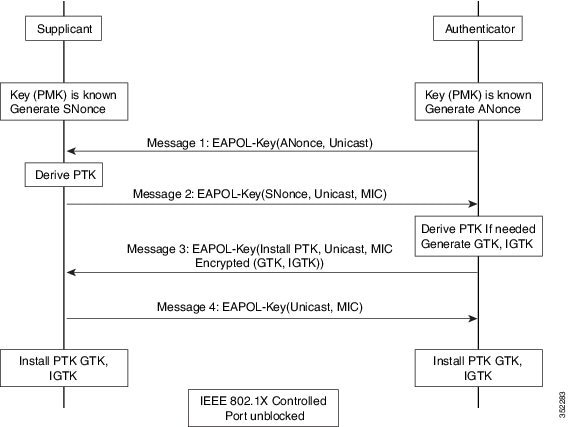
802.11w introduced IGTKs to enhance the security of management frames in wireless networks.
How IGTK is used in 802.11w management frame protection (Process)
When management frame protection is negotiated, the AP encrypts the group temporal key (GTK) and IGTK values within an Extensible Authentication Protocol over LAN-Key frame, which is delivered as part of the third message in the 4-way handshake.
-
IGTK is exchanged during the 4-way handshake process.
-
If the AP later changes the GTK, it sends the new GTK and IGTK to the client using the Group Key Handshake.
Broadcast or multicast integrity protocol (BIP)
-
ensures data integrity of broadcast and multicast robust management frames
-
provides replay protection for these frames after successful establishment of an IGTKSA, and
-
adds a message integrity code (MIC) calculated using the shared IGTK key.
SA teardown protection
SA teardown protection is a wireless network security mechanism that
-
prevents spoofed or replay attacks from disconnecting already associated clients
-
uses Association Comeback Time and an SA-Query procedure to verify the authenticity of association requests, and
-
ensures the AP only accepts new associations after the original security association is proven invalid.
How association comeback time and SA query procedures work
This process describes the mechanisms that protect wireless client sessions from replay-based association teardown attacks using Association Comeback Time and SA Query procedures.
Summary
The key components involved in the process are:
-
Access Point (AP): Implements SA teardown protection and manages association requests.
-
Client Device: Maintains a security association and sends/receives association and SA Query frames.
-
SA Teardown Protection Mechanism: Provides the logic for handling replay and spoofed association attempts.
This process involves the AP and client device exchanging association and SA Query frames to validate security associations and prevent unauthorized session teardown.
Workflow
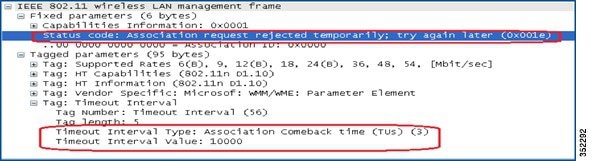
These stages describe how the Association Comeback Time and SA Query procedures operate to protect client sessions:
- When an AP receives an Association Request from a client with an existing valid security association (SA) negotiated with 802.11w, the AP rejects the request with status code 30 (“Association request rejected temporarily; try again later”) and sends an Association Comeback Time.
- The AP does not modify the existing association during the comeback interval.
- If no ongoing SA Query session with the client exists, the AP sends SA Query requests repeatedly until it receives a valid SA Query response or the comeback time expires.
- Receipt of a matching SA Query response or a valid protected frame indicates a valid SA; the AP may then allow a new association attempt without further SA Query cycles.
Result
This process ensures that spoofed requests cannot disconnect valid clients, protecting against replay-based association teardown attacks.
Prerequisites for 802.11w
-
To configure 802.11w feature for optional and mandatory, you must have WPA and AKM configured.

Note
The RNS (Robust Secure Network) IE must be enabled with an AES Cipher.
Restrictions for 802.11w
-
You cannot use 802.11w with open WLANs, Wired Equivalent Privacy (WEP)-encrypted WLANs, or Temporal Key Integrity Protocol (TKIP)-encrypted WLANs.
-
You can use 802.11w with Protected Management Frames (PMF) for non-Apple clients. For Apple iOS version 11 and earlier, request a fix from Apple to resolve association issues
-
When clients do not use 802.11w PMF, the controller ignores disassociation frames or deauthentication frames they send. If a client uses PMF, its entry is deleted immediately when the controller receives such a frame. This process helps prevent denial-of-service attacks by malicious devices, since frames without PMF are not secure.
How to Configure 802.11w
Configuring 802.11w (GUI)
Before you begin
WPA and AKM must be configured.
Procedure
|
Step 1 |
Choose . |
|
Step 2 |
Click Add to create WLANs. The Add WLAN page is displayed. |
|
Step 3 |
In the tab, navigate to the Protected Management Frame section. |
|
Step 4 |
Choose PMF as Disabled, Optional, or Required. By default, the PMF is disabled. If you choose PMF as Optional or Required, you get to view the following fields:
|
|
Step 5 |
Click Save & Apply to Device. |
Configuring 802.11w (CLI)
Before you begin
WPA and AKM must be configured.
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 2 |
wlan profile-name wlan-id ssid Example: |
Configures a WLAN and enters configuration mode. |
|
Step 3 |
security wpa akm dot1x-sha256 Example: |
Configures 802.1x support. |
|
Step 4 |
security pmf association-comeback comeback-interval Example: |
Configures the 802.11w association comeback time. |
|
Step 5 |
security pmf mandatory Example: |
Requires clients to negotiate 802.11w PMF protection on a WLAN. |
|
Step 6 |
security pmf saquery-retry-time timeout Example: |
Time interval identified in milliseconds before which the SA query response is expected. If the device does not get a response, another SQ query is tried. |
Disabling 802.11w
Procedure
| Command or Action | Purpose | |
|---|---|---|
|
Step 1 |
configure terminal Example: |
Enters global configuration mode. |
|
Step 2 |
wlan profile-name wlan-id ssid Example: |
Configures a WLAN and enters configuration mode. |
|
Step 3 |
no security wpa akm dot1x-sha256 Example: |
Disables 802.1x support. |
|
Step 4 |
no security pmf association-comeback comeback-interval Example: |
Disables the 802.11w association comeback time. |
|
Step 5 |
no security pmf mandatory Example: |
Disables client negotiation of 802.11w PMF protection on a WLAN. |
|
Step 6 |
no security pmf saquery-retry-time timeout Example: |
Disables SQ query retry. |
Monitoring 802.11w
Use the following commands to monitor 802.11w.
Procedure
|
Step 1 |
show wlan name wlan-name Displays the WLAN parameters on the WLAN. The PMF parameters are displayed. |
|
Step 2 |
show wireless client mac-address mac-address detail Displays the summary of the 802.11w authentication key management configuration on a client. |
 Feedback
Feedback