|
Step 1
|
Choose .
|
|
Step 2
|
On the AP Join Profile window, click Add.
The Add AP Join Profile window is displayed.
|
|
Step 3
|
In the General tab, enter a name and description for the AP join profile. The name can be ASCII characters from 32 to 126, without leading
and trailing spaces.
|
|
Step 4
|
Check the
LED State
check box to set the LED state of all APs connected to the device to blink, making them easier to locate.
|
|
Step 5
|
In the Client tab and Statistics Timer section, enter the time in seconds that the AP sends its 802.11 statistics to the controller.
|
|
Step 6
|
In the TCP MSS Configuration section, check the Adjust MSS Enable check box to enter value for Adjust MSS. You can enter or update the maximum segment size (MSS) for transient packets that
traverse a router. TCP MSS adjustment enables the configuration of the maximum segment size (MSS) for transient packets that
traverse a router, specifically TCP segments with the SYN bit set.
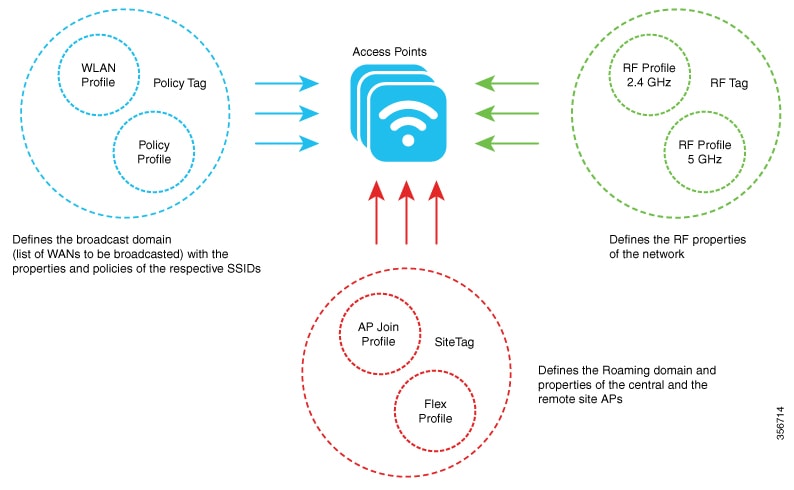
In a CAPWAP environment, a lightweight access point discovers a device by using CAPWAP discovery mechanisms, and then sends
a CAPWAP join request to the device. The device sends a CAPWAP join response to the access point that allows the access point
to join the device.
When the AP joins the device, the device manages its configuration, firmware, control transactions, and data transactions.
|
|
Step 7
|
In the CAPWAP tab, you can configure these options:
-
High Availability
You can configure primary and secondary backup controllers for all access points (which are used if primary, secondary, or tertiary controllers are not responsive) in this
order: primary, secondary, tertiary , primary backup, and secondary backup.In addition, you can configure various timers, including heartbeat timers and discovery request timers. To reduce the controller
failure detection time, you can configure the fast heartbeat interval (between the controller and the access point) with a
smaller timeout value. When the fast heartbeat timer expires (at every heartbeat interval), the access point determines if
any data packets have been received from the controller within the last interval. If no packets have been received, the access
point sends a fast echo request to the controller.
-
In the High Availability tab, enter the time (in seconds) in the Fast Heartbeat Timeout field to configure the heartbeat timer for all access points. Specifying a small heartbeat interval reduces the amount of
time it takes to detect device failure.
-
In the Heartbeat Timeout field, enter the time in seconds to configure the heartbeat timer for all APs. Specifying a small heartbeat interval reduces
the amount of time it takes to detect device failure.
-
In the Discovery Timeout field, enter a value between one and 10 seconds (inclusive) to configure the AP discovery request timer.
-
In the Primary Discovery Timeout field, enter a value between 30 and 3000 seconds (inclusive) to configure the access point primary discovery request timer.
-
In the Primed Join Timeout field, enter a value between 120 and 43200 seconds (inclusive) to configure the access point primed join timeout.
-
In the Retransmit Timers Count field, enter the number of times that you want the AP to retransmit the request to the device and vice versa. Valid range
is between three and eight.
-
In the Retransmit TimersInterval field, enter the time duration between retransmission of requests. Valid range is between two and five.
-
Check the Enable Fallback check box to enable fallback.
-
Enter the Primary Controller name and IP address.
-
Enter the Secondary Controller name and IP address.
-
Click Save & Apply to Device.
|
Note
|
The primary and secondary settings in the AP join profile are not used for AP fallback. This means that the AP will not actively
probe for those controllers (which are a part of the AP join profile), when it has joined one of them.
This setting is used only when the AP loses its connection with the controller, and then prioritizes which other controller
it should join. These controllers have a priority of four and five, following APs in the High Availability tab of the AP page.
The APs that are added as the primary, secondary, and tertiary APs in the High Availability tab of the AP configuration page, are actively probed and are used for the AP fallback option.
|
-
In the Advanced tab, check the Enable VLAN Tagging check box to enable VLAN tagging.
-
Check the Enable Data Encryption check box to enable Datagram Transport Layer Security (DTLS) data encryption.
-
Check the Enable Jumbo MTU to enable large maximum transmission unit (MTU). The MTU is the largest physical packet size, measured in bytes, that a network
can transmit. Any messages larger than the MTU are divided into smaller packets before transmission. Jumbo frames exceed the
standard Ethernet frame size, which is 1518 bytes (including Layer 2 (L2) header and FCS). Because vendors may have different
frame size definitions, jumbo frames are not standardized by IEEE.
-
Use the Link Latency drop-down list to select the link latency. Link latency monitors the round-trip time of the CAPWAP heartbeat packets (echo
request and response) from the AP to the controller and back.
-
From the Preferred Mode drop-down list, choose the mode.
-
Click Save & Apply to Device.
|
|
Step 8
|
In the AP tab, you can configure these options:
-
In the General tab, check the Switch Flag check box to enable switches.
-
Check the Power Injector State check box if power injector is being used. Use power injectors to provide flexible powering options for APs, such as local
power, multiport switches with inline power, or multiport power patch panels.
Power Injector Selection parameter enables you to protect your switch port from an accidental overload if the power injector
is inadvertently bypassed.
-
From the Power Injector Type drop-down list, choose power injector type from these options:
-
Installed—This option examines and remembers the MAC address of the currently connected switch port and assumes that a power
injector is connected. Choose this option if your network contains older Cisco 6-Watt switches and you want to avoid possible
overloads by forcing a double-check of any relocated access points.
If you want to configure the switch MAC address, enter the MAC address in theInjector Switch MAC Address text box. If you
want the access point to find the switch MAC address, leave theInjector Switch MAC Address text box blank.
|
Note
|
Each time an access point is relocated, the MAC address of the new switch port fails to match the remembered MAC address,
and the access point remains in low-power mode. You must then physically verify the existence of a power injector and reselect
this option to cause the new MAC address to be remembered.
|
-
Override—This option allows the access point to operate in high-power mode without first verifying a matching MAC address.
You can use this option if your network does not contain any older Cisco 6-W switches that could be overloaded if connected
directly to a 12-W access point. The advantage of this option is that if you relocate the access point, it continues to operate
in high-power mode without any further configuration. The disadvantage of this option is that if the access point is connected
directly to a 6-W switch, an overload occurs.
-
In theInjector Switch MAC field, enter the MAC address of the switch .
-
From the EAP Type drop-down list, choose the EAP type as EAP-FAST , EAP-TLS , or EAP-PEAP.
-
From the AP Authorization Type drop-down list, choose the type as either CAPWAP DTLS + or CAPWAP DTLS.
-
In the Client Statistics ReportingInterval section, enter the interval for 5 GHz and 2.4 GHz radios in seconds.
-
Check the Enable check box to enable extended module.
-
From the Profile Name drop-down list, choose a profile name for mesh.
-
Click Save & Apply to Device.
-
In the Hyperlocation tab, check the Enable Hyperlocation check box.
-
Enter the Detection Threshold value to filter out packets with low RSSI. The valid range is –100 dBm to –50 dBm.
-
Enter the Trigger Threshold value to set the number of scan cycles before sending a BAR to clients. The valid range is zero to 99.
-
Enter the Reset Threshold value to reset value in scan cycles after trigger. The valid range is zero to 99.
-
Enter the NTP Server IP address.
-
Click Save & Apply to Device.
-
BLE: If your APs are Bluetooth Low Energy (BLE) enabled, they can transmit beacon messages that are packets of data or attributes
transmitted over a low energy link. These BLE beacons are frequently used for health monitoring, proximity detection, asset
tracking, and in-store navigation. For each AP, you can customize BLE Beacon settings configured globally for all APs.
-
In the BLE tab, enter a value in the BeaconInterval field to indicate how often you want your APs to send out beacon advertisements to nearby devices. The range is from one
to 10, with a default value of one.
-
In the Advertised Attenuation Level field, enter the attenuation level. The range is from 40 to 100, with a default of 59.
-
Click Save & Apply to Device.
-
In the Packet Capture tab, choose an AP Packet Capture Profile from the drop-down list.
-
You can also create a new profile by clicking the + sign.
-
Enter a name and description for the AP packet capture profile.
-
Enter the Buffer Size.
-
Enter the Duration.
-
Enter the Truncate Length information.
-
In the Server IP field, enter the IP address of the TFTP server.
-
In the File Path field, enter the directory path.
-
Enter the username and password details.
-
From the Password Type drop-down list, choose the type.
-
In the Packet Classifiers section, use the option to select or enter the packets to be captured.
-
Click Save.
-
Click Save & Apply to Device.
|
|
Step 9
|
In the Management tab, you can configure these options:
-
In the Device tab, enter the IPv4/IPv6 Address of the TFTP server, TFTP Downgrade section.
-
In the Image File Name field, enter the name of the software image file.
-
From the Facility Value drop-down list, choose the appropriate facility.
-
Enter the IPv4 or IPv6 address of the host.
-
Choose the appropriate Log Trap Value.
-
Enable Telnet, SSH or both configurations, if required.
-
Enable core dump, if required.
-
Click Save & Apply to Device.
-
In the User tab, enter username and password details.
-
Choose the appropriate password type.
-
In the Secret field, enter a custom secret code.
-
Choose the appropriate secret type.
-
Choose the appropriate encryption type.
-
Click Save & Apply to Device.
-
In the Credentials tab, enter local username and password details.
-
Choose the appropriate local password type.
-
Enter 802.1x username and password details.
-
Choose the appropriate 802.1x password type.
-
Enter the time in seconds after which the session should expire.
-
Enable local credentials, 802.1x credentials, or both as required.
-
Click Save & Apply to Device.
-
In the CDPInterface tab, enable the CDP state, if required.
-
Click Save & Apply to Device.
|
|
Step 10
|
In the Rogue AP tab, check the Rogue Detection check box to enable rogue detection.
|
|
Step 11
|
In the Rogue Detection Minimum RSSI field, enter the RSSI value.
This field specifies the minimum RSSI value for which a Rogue AP should be reported. All Rogue APs with RSSI lower than what
is configured will not be reported to controller.
|
|
Step 12
|
In the Rogue Detection TransientInterval field, enter the transient interval value.
This field indicates how long the Rogue AP should be seen before reporting the controller.
|
|
Step 13
|
In the Rogue Detection ReportInterval field, enter the report interval value.
This field indicates the frequency (in seconds) of Rogue reports sent from AP to controller.
|
|
Step 14
|
Check the
Rogue Containment Automatic Rate Selection
check box to enable rogue containment automatic rate selection.
The AP selects the best rate for the target Rogue, based on its RSSI.
|
|
Step 15
|
Check the
Auto Containment on FlexConnect Standalone
check box to enable the feature.
The AP continues containment if it moves to FlexConnect standalone mode.
|
|
Step 16
|
Click Save & Apply to Device.
|

 Feedback
Feedback