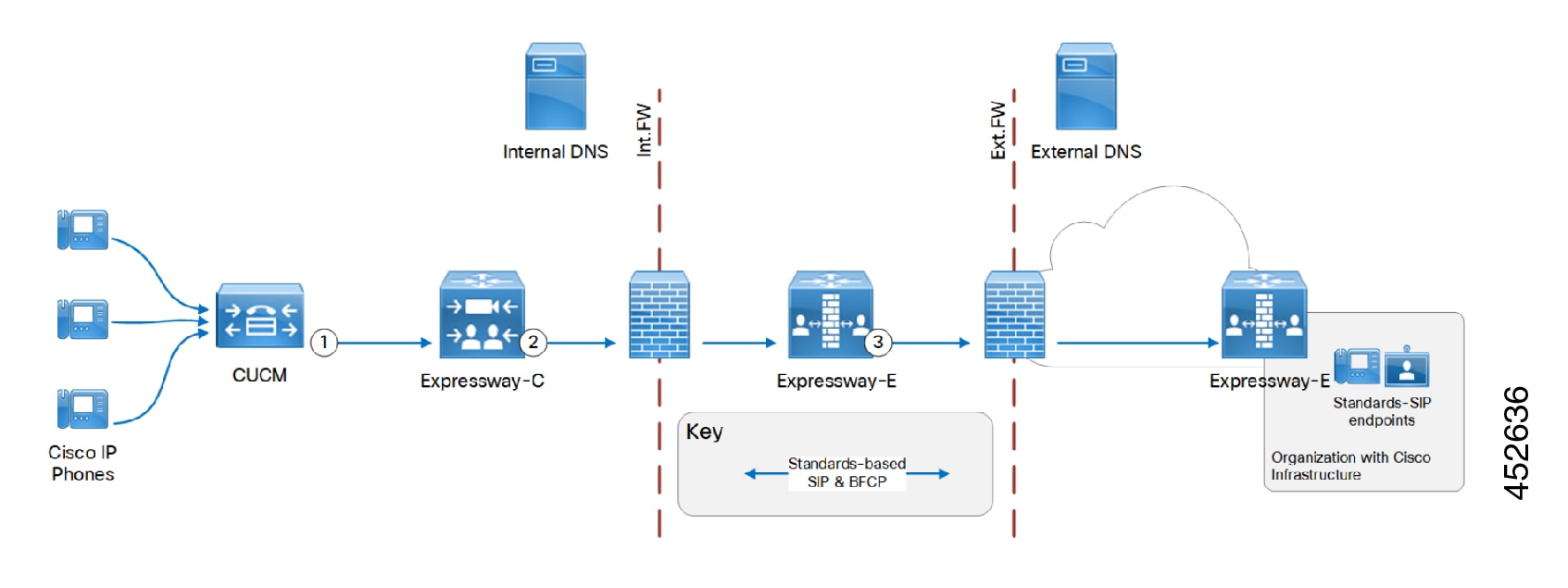
Task 15: Configuring Routes to a Neighbor Zone (Optional)
You can optionally set up neighbor zones and associated search rules on the Expressway-C to route calls to other systems. To another Expressway for example, or to a Cisco VCS, Cisco Meeting Server, or Unified CM.
Example: Cisco VCS Neighbor Zone
This example assumes that you want to route calls toward devices that are registered to a Cisco VCS. The devices have an address
(destination alias) in the format < <alias>@vcs.domain>.
 Note |
You may need more rules or transforms if any H.323 devices have registered E.164 numbers or H.323 IDs without a domain portion. |
To Configure a Neighbor Zone to the Cisco VCS:
Procedure
| Step 1 |
Go to . |
||||||||||||||||||||
| Step 2 |
Click . |
||||||||||||||||||||
| Step 3 |
Configure the fields as follows, and leave all other fields with their default values:
|
||||||||||||||||||||
| Step 4 |
Click . |
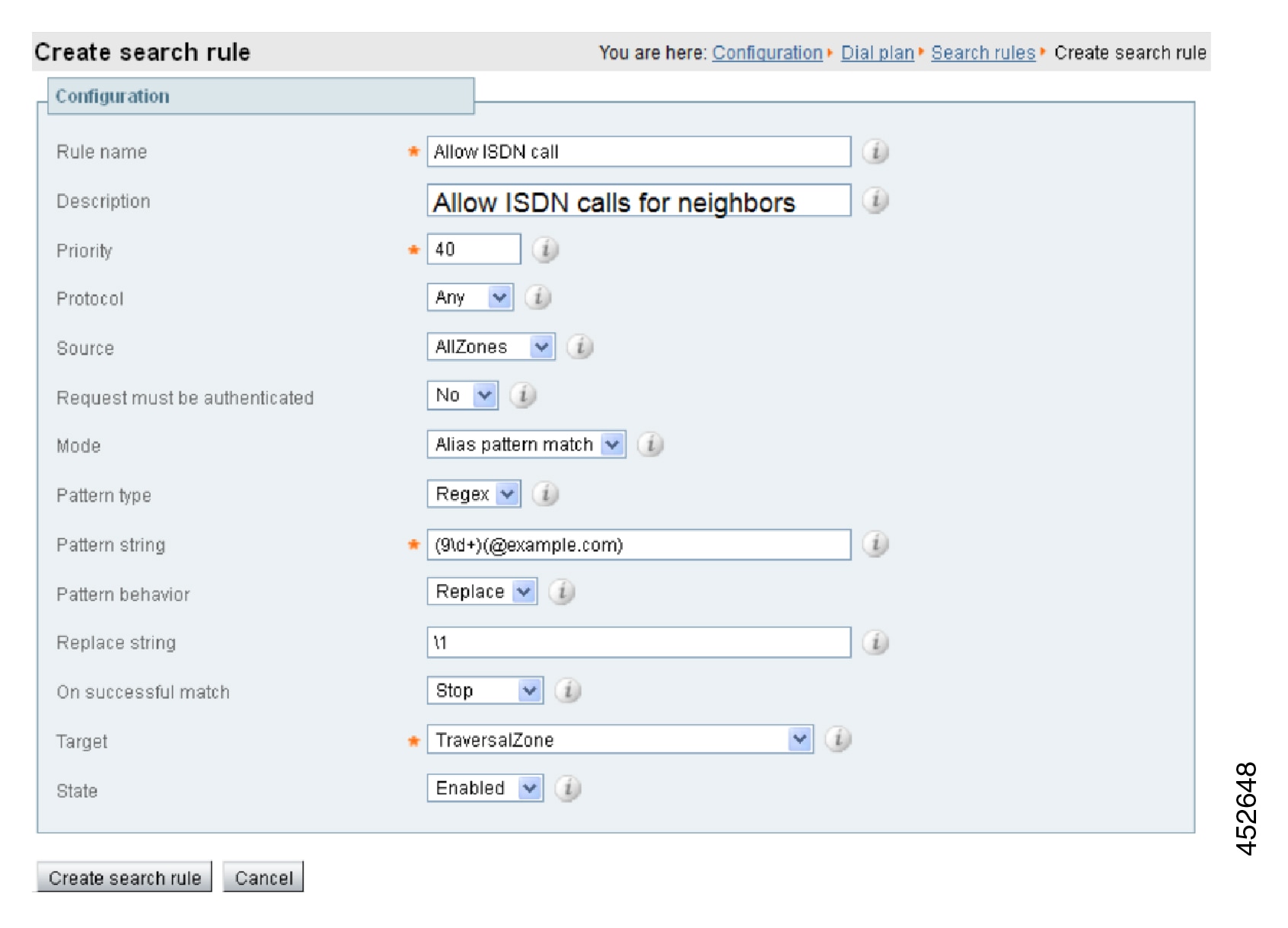
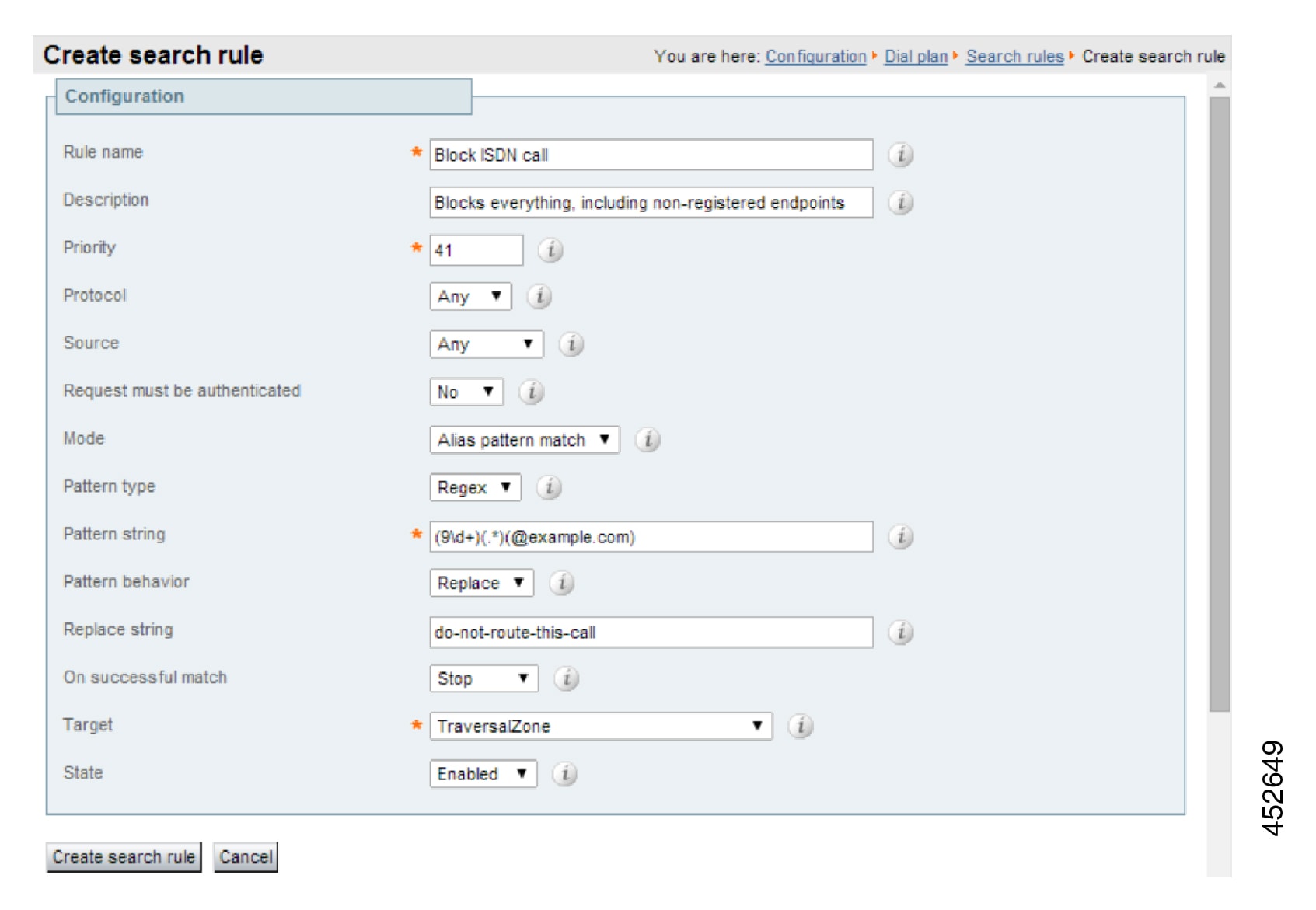
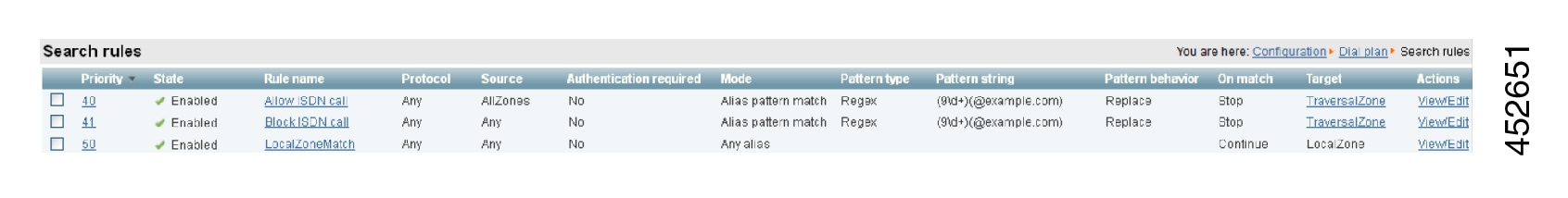
To Configure the Search Rule to Route Calls to the Cisco VCS:
Procedure
| Step 1 |
Go to . |
||||||||||||||||||||||||||||||
| Step 2 |
Click . |
||||||||||||||||||||||||||||||
| Step 3 |
Configure the search rule fields as follows:
|
||||||||||||||||||||||||||||||
| Step 4 |
Click . |
SIP Trunks to Unified CM
To configure a SIP trunk to Unified CM, see Cisco Unified Communications Manager with Expressway Deployment Guide.

 Feedback
Feedback