Requirements for Identity Providers
This section provides an outline of the requirements that Identity Providers must meet in order to deploy SAML SSO services for Cisco Collaboration applications.
Identity Providers must adhere to the following guidelines:
-
Support is for SAML 2.0 only.
-
Supports Service-Provider initiated SSO only.
-
Set the NameID Format attribute to urn:oasis:names:tc:SAML:2.0:nameid-format:transient
-
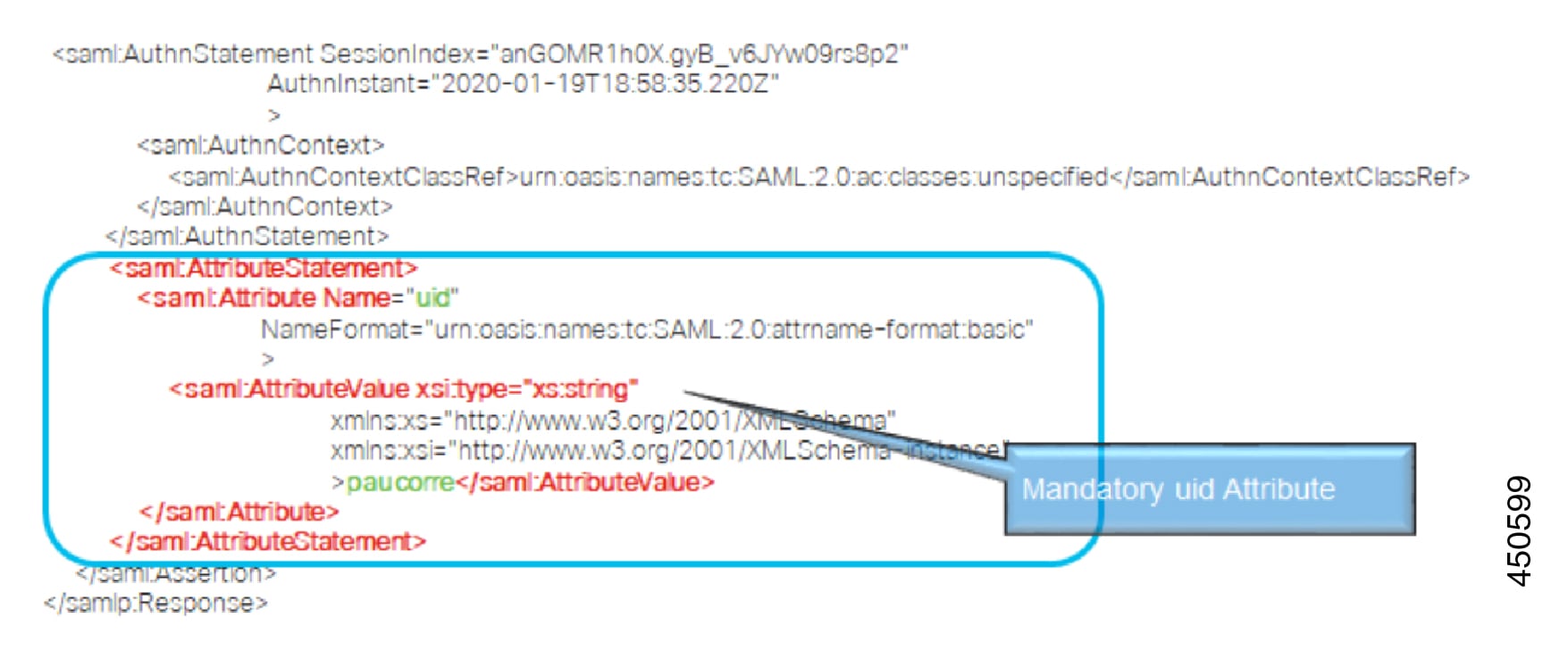
Configure a claim on the IdP to include the uid attribute name with a value that is mapped to LDAP attributes (for example SAMAccountName).
-
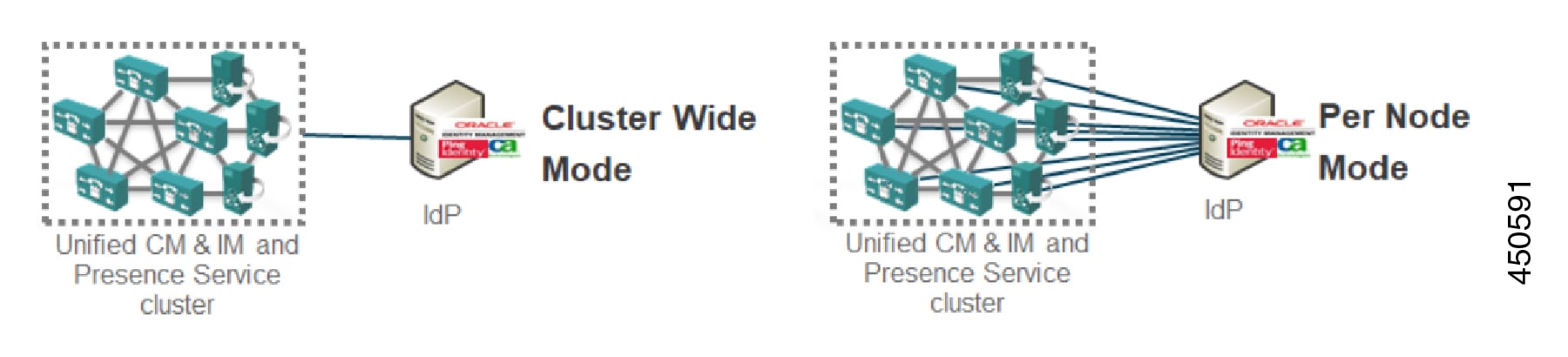
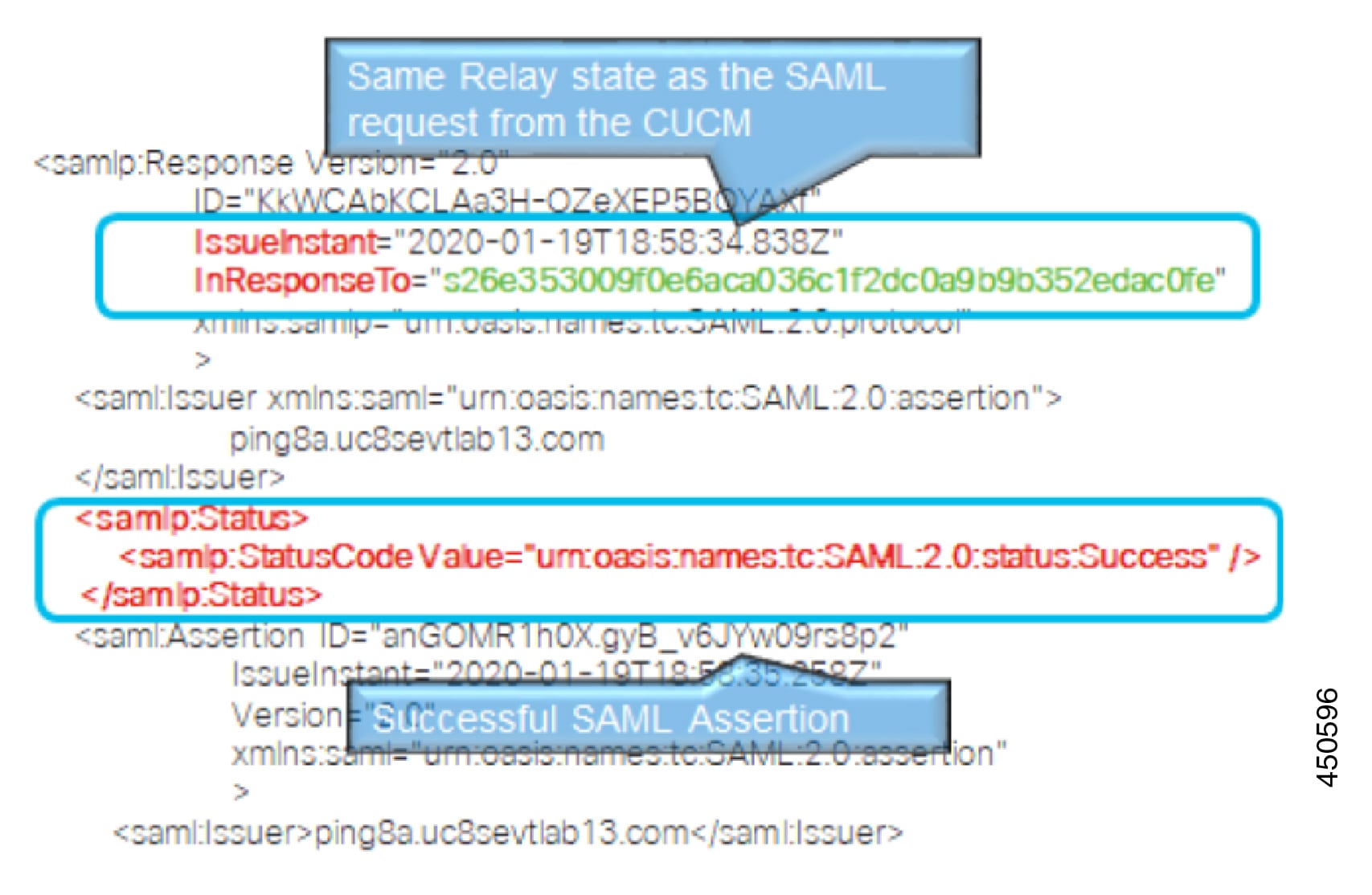
Cisco Unified Communications Manager uses ACS url index in the Authentication Request. The IdP must be able the index to the ACS url in the Service Provider metadata. This is compliant with SAML standards.
-
It's not supported to have multiple certificates in the Signing and Encryption portion of the SAML Assertion. See CSCvq78479.
When configuring SAML SSO, make sure to deploy the following in your Cisco Collaboration Deployment:
-
Network Time Protocol—Deploy NTP in your environment so that the times in your Cisco Collaboration Deployment and your Identity Provider are synced. Make sure that the time difference between the IdP and the Cisco Collaboration deployment does not exceed 3 seconds.
-
DNS—Your Cisco Collaboration applications and your Identity Provider must be able to resolve each other’s addresses.
-
LDAP—You must have an LDAP Directory sync configured in your Cisco Collaboration deployment. However, we recommend that you disable LDAP authentication.
-
Certificates—You must exchange metadata files between your Cisco Collaboration deployment and the Identity Provider. The metadata contains the certificates that are required to create a trust relationship between your Collaboration deployment and the Identity Provider. You can use either a tomcat certificate or a system-generated self-signed certificate to establish trust.




 Feedback
Feedback