HTTPS Networking
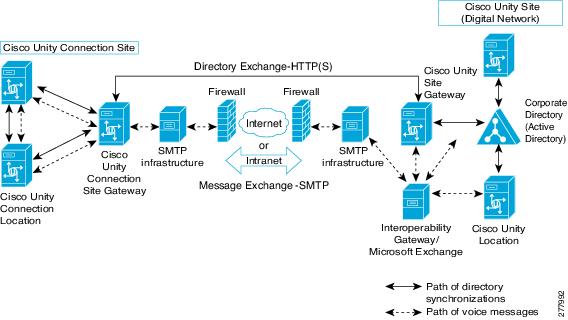
Unity Connection supports HTTPS Networking, that allows you to connect different Unity Connection servers and clusters in a single site network. HTTP networking provides more scalable Unity Connection deployments as compared to legacy networking. The architecture of HTTPS networking is scalable both in terms of number of Unity Connection locations and the total directory size. HTTPS Protocol is used for directory synchronization within a network.
In addition to HTTPS networking, Unity Connection also supports legacy networking to connect multiple Unity Connection servers in a network. However, you should deploy a new network as per HTTPS networking. Legacy networking includes both intrasite (digital) and intersite networking.The legacy and HTTPS networking are not supported simultaneously in the same network. In legacy networking, SMTP is the method used within a site, and HTTPS is used in Intersite networking when linking two separate sites.
Designing a Unity Connection Network using HTTPS
When the messaging needs of your organization require more than one Unity Connection server or cluster, you need a way to combine multiple Unity Connection directories or to ensure that the connected servers can communicate with each other. The concept of networking, HTTPS Networking, is introduced to connect different Unity Connection servers and clusters in a network.
 Note |
The legacy (SMTP) and new HTTPS networking are not supported simultaneously in the same network. |
In hub-spoke topology, all the directory information among the spokes is shared through the hub(s) connecting the spokes. For example, in the above figure, if spoke A needs to synchronize directory information with spoke E, the directory information flows from spoke A to hub B, hub B to hub C, hub C to hub D, and then from hub D to spoke E.
Each Unity Connection server (or cluster) is represented in the network as a single Unity Connection location, which is created locally during installation and which cannot be deleted from the server itself. When you join the server (or cluster) to an existing location in a network, a Unity Connection location is automatically created for the server (or cluster).
 Note |
In an HTTPS network the round-trip latency should not be more than 250 ms between Hub and Spoke nodes. |
 Note |
HTTPS networking supports single site networks only. You cannot connect multiple HTTPS networks or single site networks together to form a larger network. The maximum number of Unity Connection locations that you can connect in an HTTPS network is 25. |
OVA Selection and HTTPS
When deciding which OVA template to deploy, it is important to determine the role of the servers in your environment relative to HTTPS networking. For example, if you are building a VPIM server to support 150,000 VPIM users, you would use the largest OVA template, and the server would only contain VPIM accounts, not subscribers.
Due to the limitations of the smaller OVA templates, you need to take careful consideration of growth as well as whether the node is a hub or spoke in the network when choosing your OVA. If your network size grows past the directory size limits of your chosen OVA, you need to rebuild or replace your servers with larger Novas to accommodate the larger directory size. It is a good idea to select a larger template than you think you need for just this reason. The smallest OVA template, in most cases, should only be used for spoke servers in the network.
For information about the maximum number of locations and other directory objects supported in a Unity Connection site, see the “Directory Object Limits” section in the System Requirements for Cisco Unity Connection, Release 12.x, at http://www.cisco.com/c/en/us/td/docs/voice_ip_comm/connection/12x/requirements/b_12xcucsysreqs.html
Migrating from Legacy (SMTP) Networking to HTTPS Networking
Currently, the only supported method of migrating from legacy networking to HTTPS networking is a manual method. In the future, there is a migration tool available to make the process easier. The migration method is outlined in the HTTPS Networking Guide for Cisco Unity Connection , Release 12.x.
For information about the migration method, see the “Migration from Legacy network to HTTPS Network” chapter in the HTTPS Networking Guide for Cisco Unity Connection , Release 12.x, at https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/connection/12x/https_networking/guide/b_12xcuchttpsnet.html.

 Feedback
Feedback