Firmware Upgrade Overview
This section includes the firmware and driver update procedure for Cisco Integrated System for Microsoft Azure Stack Hub. Cisco periodically releases system update for the Azure Stack Hub platform. These system updates include updated firmware and drivers that improve the platform lifecycle and resolve known defects. Customers are required to update their systems to the latest system update within 60 days of the system update release date.
The following components of the Cisco appliance require periodic firmware updates to resolve known functional and security issues:
-
Top-of-Rack Switches
-
Cisco UCS
-
Cisco UCS Manager
-
UCS Fabric Interconnects
-
UCS Fabric Extenders
-
UCS C-Series rack server components, including BIOS, SAS HBA, NIC, HDD, and SSD
-
Server device drivers
-
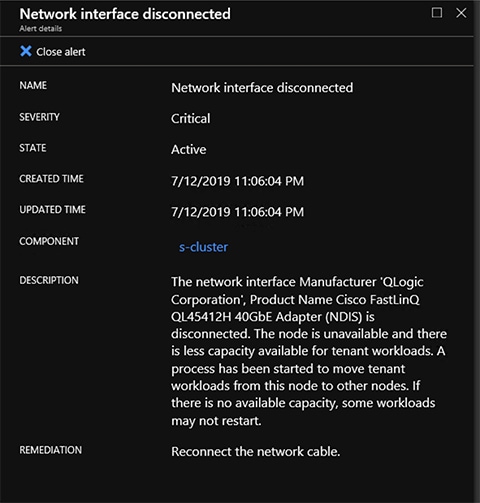
For assistance with firmware upgrade issues or errors, refer the Support Guidance chapter to open a Cisco TAC case for Azure Stack Hub support.
 Note |
Cisco recommends performing firmware upgrade during the scheduled maintenance window. |
Cisco Integrated System for Microsoft Azure Stack Hub firmware download portal can be accessed by selecting Integrated System Azure Stack - System Updates on UCS C-Series Rack-Mount UCS-Managed Server Software Download page. Also, it can be set up to notify you about the availability of the new firmware. Cisco highly recommends that you sign up for these notifications.
The following software components hosted on Microsoft Azure Stack Hub firmware download portal are required for the firmware upgrade procedure:
|
Component |
Description |
|---|---|
|
ucs-6300-k9-bundle-infra.<version number>.A.bin |
UCS Infrastructure Firmware |
|
ucs-k9-bundle-c-series.<version number>.C.bin |
UCS Server Firmware |
|
nxos.<version number>.bin |
ToR Switch Firmware |
|
<OEM extension version number>.zip |
Zip file containing the OEM Extensions Package. The OEM Extensions Package is made of two files. One zip file and one xml file. |
|
Cisco_UCS_AzureStack_FwUpdate_<version number>.zip |
Firmware and Driver Update Automation (CASPU) |
 Feedback
Feedback