Device Zeroization
Zeroization consists of erasing any and all potentially sensitive information in the device. This includes erasure of Main memory, cache memories, and other memories containing packet data, NVRAM, and Flash memory. The process of zeroization is launched upon the initiation of a user command and a subsequent trigger.
 Important |
service declassify erase-nvram is NOT guaranteed to securely and completely erase the data from the underlying file system. The data may be recoverable by forensic analysis techniques. Consider using service declassify erase-all to securely delete all data on the device |
 Important |
IOS cannot securely erase an SD Card, so integrators that want secure erasure must not include the SD Card. |
By default, the device will have the zeroization feature disabled. SPI: Flash, I2C, and ACT2 are not impacted by this feature.
 Note |
Ensure that you are familiar with the Emergency Recovery Installation procedure BEFORE attempting to test the Zeroize feature. |
When zeroization is functionally active, the SYS LED indicates blinking yellow until the device reloads.
Factory reset
When you want to remove an undesirable configuration that is present in the switch securely. If you have configured a switch and the configuration has become very complex, or if you want to move a switch from one network to other, you can reset the switch to factory defaults and configure it as a new switch. For more information on performing factory reset, refer factory reset.
WARNING!
The CLI service declassify erase-all is a software self-destruct mechanism intended for defense and intelligence environments that attempts to wipe clean, all of the writable non-volatile storage on the device to clear the device configuration, other stored configurations and all security credentials including any additional license keys.
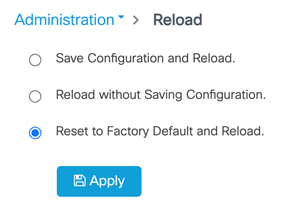
Please do not use this feature in lieu of doing a write erase from the CLI or from the Administration page, Reload option of the WebUI. Invoke the reload with the Reset to Factory Default and Reload option and click Apply. See the following figure.
If service declassify erase-all is invoked, after restoring the IOS-XE image and device configuration, you must re-license the device using the standard Cisco Smart Licensing procedures which ultimately require a Cisco Smart Account and access to the internet or a satellite license server.

 Feedback
Feedback