You can guarantee the
availability of buffers, set WTD thresholds, and configure the maximum
allocation for a queue-set by using the
mls qos queue-set
output
qset-id
threshold
queue-id
drop-threshold1
drop-threshold2 reserved-threshold maximum-threshold
global configuration command.
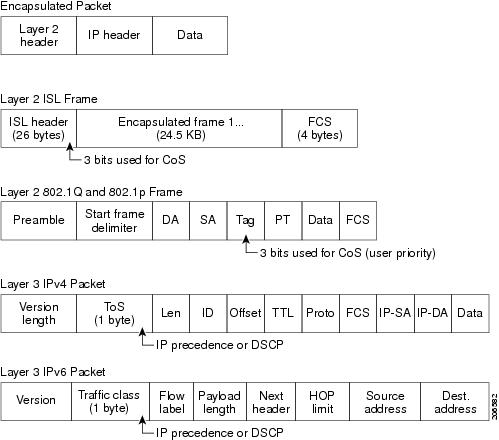
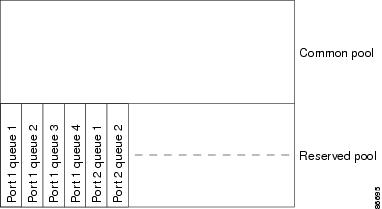
Each threshold value is a
percentage of the queue’s allocated buffers, which you specify by using the
mls qos queue-set
output
qset-id
buffers
allocation1 ...
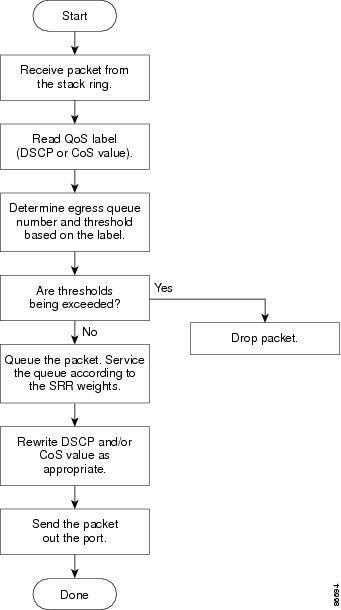
allocation4 global configuration command. The queues use WTD to
support distinct drop percentages for different traffic classes.

Note
|
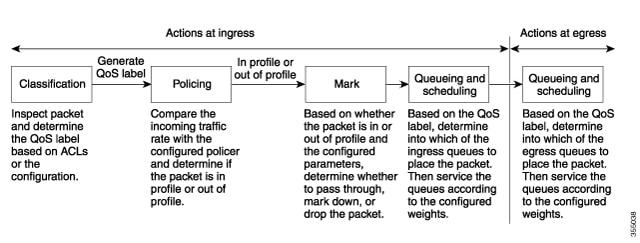
The egress queue default
settings are suitable for most situations. You should change them only when you
have a thorough understanding of the egress queues and if these settings do not
meet your QoS solution.
|
Beginning in privileged EXEC
mode, follow these steps to configure the memory allocation and to drop
thresholds for a queue-set. This procedure is optional.

 Feedback
Feedback