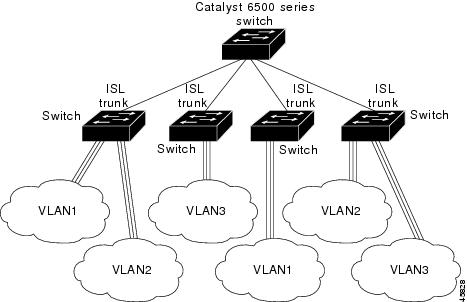
By default, a trunk
port sends traffic to and receives traffic from all VLANs. All VLAN IDs, 1 to
4094, are allowed on each trunk. However, you can remove VLANs from the allowed
list, preventing traffic from those VLANs from passing over the trunk.
VLAN 1 is the default VLAN on
all trunk ports in all Cisco
switches, and it has previously been a
requirement that VLAN 1 always be enabled on every trunk link. You can use the
VLAN 1 minimization feature to disable VLAN 1 on any individual VLAN trunk link
so that no user traffic (including spanning-tree advertisements) is sent or
received on VLAN 1.
To reduce the risk of
spanning-tree loops or storms, you can disable VLAN 1 on any individual VLAN
trunk port by removing VLAN 1 from the allowed list. When you remove VLAN 1
from a trunk port, the interface continues to send and receive management
traffic, for example, Cisco Discovery Protocol (CDP), Port Aggregation Protocol
(PAgP), Link Aggregation Control Protocol (LACP), DTP, and VTP in VLAN 1.
If a trunk port with
VLAN 1 disabled is converted to a nontrunk port, it is added to the access
VLAN. If the access VLAN is set to 1, the port will be added to VLAN 1,
regardless of the
switchport trunk
allowed setting. The same is true for any VLAN that has been
disabled on the port.
A trunk port can
become a member of a VLAN if the VLAN is enabled, if VTP knows of the VLAN, and
if the VLAN is in the allowed list for the port. When VTP detects a newly
enabled VLAN and the VLAN is in the allowed list for a trunk port, the trunk
port automatically becomes a member of the enabled VLAN. When VTP detects a new
VLAN and the VLAN is not in the allowed list for a trunk port, the trunk port
does not become a member of the new VLAN.


 Feedback
Feedback