- Index
- Preface
- Overview
- Using the Command-Line Interface
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS Configuration Engine
- Managing Switch Stacks
- Clustering Switches
- Administering the Switch
- Configuring SDM Templates
- Managing Catalyst 3750-X Stack Power
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring Interface Characteristics
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLANs
- Configuring Private VLANs
- Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Flex Links
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IGMP Snooping and MVR
- Configuring IPv6 MLD Snooping
- Configuring Port-Based Traffic Control
- Configuring CDP
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring UDLD
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Embedded Event Manager
- Configuring Network Security with ACLs
- Configuring IPv6 ACLs
- Configuring QoS
- Configuring EtherChannels
- Configuring TelePresence E911 IP Phone Support
- Configuring IP Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring HSRP
- Configuring Cisco IOS IP SLAs Operations
- Configuring Enhanced Object Tracking
- Configuring WCCP
- Configuring IP Multicast Routing
- Configuring MSDP
- Configuring Fallback Bridging
- Troubleshooting
- Configuring Online Diagnostics
- Supported MIBs
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 12.2(55)SE
- Restrictions for Switch Stacks
- Understanding Switch Stacks
- Switch Stack Membership
- Stack Master Election and Re-Election
- Switch Stack Bridge ID and Router MAC Address
- Stack Member Numbers
- Stack Member Priority Values
- Switch Stack Offline Configuration
- Hardware Compatibility and SDM Mismatch Mode in Switch Stacks
- Switch Stack Software Compatibility Recommendations
- Stack Protocol Version Compatibility
- Major Version Number Incompatibility Among Switches
- Minor Version Number Incompatibility Among Switches
- Incompatible Software and Stack Member Image Upgrades
- Switch Stack Configuration Files
- Additional Considerations for System-Wide Configuration on Switch Stacks
- Switch Stack Management Connectivity
- Switch Stack Configuration Scenarios
- Configuring the Switch Stack
Managing Switch Stacks
This chapter provides the concepts and procedures to manage Catalyst 3750-X switch stacks.

Note![]() The LAN base feature set supports switch stacks only when all switches in the stack are run the LAN base feature set.
The LAN base feature set supports switch stacks only when all switches in the stack are run the LAN base feature set.
The switch command reference has command syntax and usage information.
This chapter consists of these sections:
- Restrictions for Switch Stacks
- Understanding Switch Stacks
- Configuring the Switch Stack
- Accessing the CLI of a Specific Stack Member
- Displaying Switch Stack Information
- Troubleshooting Stacks
For other switch stack-related information, such as cabling the switches through their StackWise Plus ports and using the LEDs to display switch stack status, see the hardware installation guide.
The Catalyst 3750-X stackable switch also supports StackPower, where up to four switches can be connected with power stack cables to allow the switch power supplies to share the load across multiple systems in a stack. Switches in a power stack must be members of the same switch (data) stack. For information about StackPower, see Chapter9, “Configuring Catalyst 3750-X StackPower”

Note![]() This chapter describes how to manage Catalyst 3750-X-only switch stacks. For information about managing hardware and software stacks and about using universal software images with software licenses, see the Cisco IOS Software Installation document on Cisco.com.
This chapter describes how to manage Catalyst 3750-X-only switch stacks. For information about managing hardware and software stacks and about using universal software images with software licenses, see the Cisco IOS Software Installation document on Cisco.com.
Restrictions for Switch Stacks
After changing a virtual routing and forwarding (VRF) configuration, followed by the switchover of the master switch, can cause the VRF functionality to not work correctly. Reload the entire switch stack after the VRF configuration change for the VRF functionality to work correctly after a switchover. That is, change the VRF configuration, save the configuration, and reload the entire switch stack.
Understanding Switch Stacks
A switch stack is a set of up to nine stacking-capable switches connected through their StackWise Plus or StackWise ports. You can connect only one switch type in a stack, or you can connect a mix of Catalyst 3750-X, Catalyst 3750-E, and Catalyst 3750 switches in the stack. Catalyst 3750-X and Catalyst 3750-E stack members have StackWise Plus ports, and Catalyst 3750 members have StackWise ports. The stack can have one of these configurations:
- Homogeneous stack—A Catalyst 3750-E-only stack with only Catalyst 3750-E switches as stack members or a Catalyst 3750-X-only stack with only Catalyst 3750-X switches as stack members.
- Mixed stack

Note![]() Mixed stacks are not supported with switches running the LAN base feature set.
Mixed stacks are not supported with switches running the LAN base feature set.
–![]() A mixed hardware stack with a mixture of Catalyst 3750-X, Catalyst 3750-E, and 3750 switches as stack members.
A mixed hardware stack with a mixture of Catalyst 3750-X, Catalyst 3750-E, and 3750 switches as stack members.
For example, a stack with Catalyst 3750-X and 3750 switches supporting the IP services features.
–![]() A mixed software stack with only Catalyst 3750-X, only Catalyst 3750-E, or only Catalyst 3750 switches supporting different features as stack members.
A mixed software stack with only Catalyst 3750-X, only Catalyst 3750-E, or only Catalyst 3750 switches supporting different features as stack members.
For example, a Catalyst 3750-X-only stack with some members running the IP base feature set, other members running the IP services feature set, and the remaining members running the IP services feature set.
–![]() A mixed hardware and software stack with Catalyst 3750-X, Catalyst 3750-E, and Catalyst 3750 switches supporting different features as stack members.
A mixed hardware and software stack with Catalyst 3750-X, Catalyst 3750-E, and Catalyst 3750 switches supporting different features as stack members.
For example, a stack with the Catalyst 3750-X members running the IP services feature set and the Catalyst 3750 members running the IP services software image.
For information about Catalyst 3750 switches, see the “Managing Switch Stacks” chapter in the Catalyst 3750 Switch Software Configuration Guide.
One of the switches controls the operation of the stack and is called the stack master. The stack master and the other switches in the stack are all stack members. The Catalyst 3750-E stack members use the Cisco StackWise Plus technology to work together as a unified system. Layer 2 and Layer 3 protocols present the entire switch stack as a single entity to the network.

Note![]() Switch stacks running the LAN base feature set do not support Layer 3 features.
Switch stacks running the LAN base feature set do not support Layer 3 features.
The stack master is the single point of stack-wide management. From the stack master, you configure:
- System-level (global) features that apply to all stack members
- Interface-level features for each stack member
A switch stack is identified in the network by its bridge ID and, if it is operating as a Layer 3 device, its router MAC address. The bridge ID and router MAC address are determined by the MAC address of the stack master. Every stack member is identified by its own stack member number.
All stack members are eligible to be stack masters. If the stack master becomes unavailable, the remaining stack members elect a new stack master from among themselves. The switch with the highest stack member priority value becomes the new stack master.
The system-level features supported on the stack master are supported on the entire switch stack. If a switch in the stack is running the IP base or IP services feature set and the cryptographic (that is, supporting encryption) universal software image, we recommend that this switch be the stack master. Encryption features are unavailable if the stack master is running the IP base or IP services feature set and the noncryptographic software image.

Note![]() In a mixed stack, Catalyst 3750 or Catalyst 3750-E switches running Cisco IOS Release 12.2(53)SE and earlier could be running a noncryptographic image. Catalyst 3750-X switches and Catalyst 3750 and 3750-E switches with Cisco IOS Releases later than 12.2(53)SE run only the cryptographic software image.
In a mixed stack, Catalyst 3750 or Catalyst 3750-E switches running Cisco IOS Release 12.2(53)SE and earlier could be running a noncryptographic image. Catalyst 3750-X switches and Catalyst 3750 and 3750-E switches with Cisco IOS Releases later than 12.2(53)SE run only the cryptographic software image.
The stack master contains the saved and running configuration files for the switch stack. The configuration files include the system-level settings for the switch stack and the interface-level settings for each stack member. Each stack member has a current copy of these files for back-up purposes.
You manage the switch stack through a single IP address. The IP address is a system-level setting and is not specific to the stack master or to any other stack member. You can manage the stack through the same IP address even if you remove the stack master or any other stack member from the stack.
You can use these methods to manage switch stacks:
- Network Assistant (available on Cisco.com)
- Command-line interface (CLI) over a serial connection to the console port of any stack member or the Ethernet management port of a stack member
- A network management application through the Simple Network Management Protocol (SNMP)
Use SNMP to manage network features across the switch stack that are defined by supported MIBs. The switch does not support MIBs to manage stacking-specific features such as stack membership and election.
To manage switch stacks, you should understand:
–![]() Stack Master Election and Re-Election
Stack Master Election and Re-Election
–![]() Switch Stack Bridge ID and Router MAC Address
Switch Stack Bridge ID and Router MAC Address
–![]() Stack Member Priority Values
Stack Member Priority Values
–![]() Switch Stack Offline Configuration
Switch Stack Offline Configuration
–![]() Hardware Compatibility and SDM Mismatch Mode in Switch Stacks
Hardware Compatibility and SDM Mismatch Mode in Switch Stacks
–![]() Switch Stack Software Compatibility Recommendations
Switch Stack Software Compatibility Recommendations
–![]() Stack Protocol Version Compatibility
Stack Protocol Version Compatibility
–![]() Major Version Number Incompatibility Among Switches
Major Version Number Incompatibility Among Switches
–![]() Minor Version Number Incompatibility Among Switches
Minor Version Number Incompatibility Among Switches
–![]() Incompatible Software and Stack Member Image Upgrades
Incompatible Software and Stack Member Image Upgrades
–![]() Switch Stack Configuration Files
Switch Stack Configuration Files
–![]() Additional Considerations for System-Wide Configuration on Switch Stacks
Additional Considerations for System-Wide Configuration on Switch Stacks
–![]() Switch Stack Management Connectivity
Switch Stack Management Connectivity
–![]() Switch Stack Configuration Scenarios
Switch Stack Configuration Scenarios

Note![]() A switch stack is different from a switch cluster. A switch cluster is a set of switches connected through their LAN ports, such as the 10/100/1000 ports. For more information about how switch stacks differ from switch clusters, see the “Planning and Creating Clusters” chapter in the Getting Started with Cisco Network Assistant on Cisco.com.
A switch stack is different from a switch cluster. A switch cluster is a set of switches connected through their LAN ports, such as the 10/100/1000 ports. For more information about how switch stacks differ from switch clusters, see the “Planning and Creating Clusters” chapter in the Getting Started with Cisco Network Assistant on Cisco.com.
Switch Stack Membership
A switch stack has up to nine stack members connected through their StackWise Plus ports. A switch stack always has one stack master.
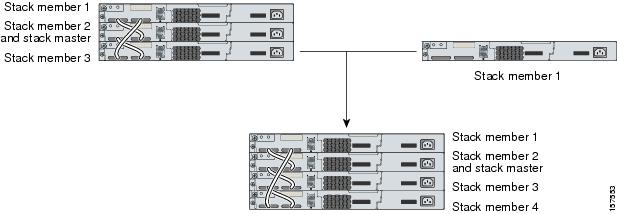
A standalone switch is a switch stack with one stack member that also operates as the stack master. You can connect one standalone switch to another (Figure 5-1) to create a switch stack containing two stack members, with one of them as the stack master. You can connect standalone switches to an existing switch stack (Figure 5-2) to increase the stack membership.
If you replace a stack member with an identical model, the new switch functions with exactly the same configuration as the replaced switch, assuming that the new switch is using the same member number as the replaced switch. For information about the benefits of provisioning a switch stack, see the “Switch Stack Offline Configuration” section. For information about replacing a failed switch, see the “Troubleshooting” chapter in the hardware installation guide.
The operation of the switch stack continues uninterrupted during membership changes unless you remove the stack master or you add powered-on standalone switches or switch stacks.

Note![]() Make sure that you power off the switches that you add to or remove from the switch stack.
Make sure that you power off the switches that you add to or remove from the switch stack.
After adding or removing stack members, make sure that the switch stack is operating at full bandwidth (64 Gb/s). Press the Mode button on a stack member until the Stack mode LED is on. The last two right port LEDs on all switches in the stack should be green. Depending on the switch model, the last two right ports are 10-Gigabit Ethernet ports or small form-factor pluggable (SFP) module ports (10/100/1000 ports). If one or both of these LEDs are not green on any of the switches, the stack is not operating at full bandwidth.
- Adding powered-on switches (merging) causes the stack masters of the merging switch stacks to elect a stack master from among themselves. The re-elected stack master retains its role and configuration and so do its stack members. All remaining switches, including the former stack masters, reload and join the switch stack as stack members. They change their stack member numbers to the lowest available numbers and use the stack configuration of the re-elected stack master.
- Removing powered-on stack members causes the switch stack to divide (partition) into two or more switch stacks, each with the same configuration. This can cause an IP address configuration conflict in your network. If you want the switch stacks to remain separate, change the IP address or addresses of the newly created switch stacks. If you did not intend to partition the switch stack:
a.![]() Power off the switches in the newly created switch stacks.
Power off the switches in the newly created switch stacks.
b.![]() Reconnect them to the original switch stack through their StackWise Plus ports.
Reconnect them to the original switch stack through their StackWise Plus ports.
For more information about cabling and powering switch stacks, see the “Switch Installation” chapter in the hardware installation guide.
Figure 5-1 Creating a Switch Stack from Two Standalone Switches

Figure 5-2 Adding a Standalone Switch to a Switch Stack
Stack Master Election and Re-Election
The stack master is elected or re-elected based on one of these factors and in the order listed:
1.![]() The switch that is currently the stack master.
The switch that is currently the stack master.
2.![]() The switch with the highest stack member priority value.
The switch with the highest stack member priority value.

Note![]() We recommend assigning the highest priority value to the switch that you prefer to be the stack master. This ensures that the switch is re-elected as stack master if a re-election occurs.
We recommend assigning the highest priority value to the switch that you prefer to be the stack master. This ensures that the switch is re-elected as stack master if a re-election occurs.
3.![]() The switch that is not using the default interface-level configuration.
The switch that is not using the default interface-level configuration.
4.![]() The switch with the higher priority feature set and software image combination. These combinations are listed from highest to lowest priority.
The switch with the higher priority feature set and software image combination. These combinations are listed from highest to lowest priority.

Note![]() The noncryptographic images apply only to mixed stacks that include Catalyst 3750-E or 3750 switches running Cisco IOS Release 12.2(53)SE or earlier. Catalyst 3750-X switches and Catalyst 3750-E or 3750 switches running later releases support only the cryptographic image.
The noncryptographic images apply only to mixed stacks that include Catalyst 3750-E or 3750 switches running Cisco IOS Release 12.2(53)SE or earlier. Catalyst 3750-X switches and Catalyst 3750-E or 3750 switches running later releases support only the cryptographic image.
–![]() IP services feature set and the cryptographic software image
IP services feature set and the cryptographic software image
–![]() IP services feature set and the noncryptographic software image
IP services feature set and the noncryptographic software image
–![]() IP base feature set and the cryptographic software image
IP base feature set and the cryptographic software image
–![]() IP base feature set and the noncryptographic software image
IP base feature set and the noncryptographic software image

Note![]() In a switch stacks running the LAN base feature set, all switches in the stack must run the LAN base feature set.
In a switch stacks running the LAN base feature set, all switches in the stack must run the LAN base feature set.
During the stack master switch election, differences in start-up times between the feature sets determine the stack master. The switch with the shorter start-up time becomes the stack master.
For example, a switch running the IP services feature set has a higher priority than the switch running the IP base feature set, but the switch running the IP base feature set becomes the stack master because the other switch takes 10 seconds longer to start. To avoid this problem, upgrade the switch running the IP base feature set to same feature set and software image as the other switch, or manually start the master switch and wait at least 8 seconds before starting the new member switch that running the IP base feature set.
5.![]() The switch with the lowest MAC address.
The switch with the lowest MAC address.
A stack master retains its role unless one of these events occurs:
- The switch stack is reset. *
- The stack master is removed from the switch stack.
- The stack master is reset or powered off.
- The stack master fails.
- The switch stack membership is increased by adding powered-on standalone switches or switch stacks. *
In the events marked by an asterisk (*), the current stack master might be re-elected based on the listed factors.
When you power on or reset an entire switch stack, some stack members might not participate in the stack master election. Stack members that are powered on within the same 20-second time frame participate in the stack master election and have a chance to become the stack master. Stack members that are powered on after the 20-second time frame do not participate in this initial election and become stack members. All stack members participate in re-elections. For all powering considerations that affect stack-master elections, see the “Switch Installation” chapter in the hardware installation guide.
The new stack master becomes available after a few seconds. In the meantime, the switch stack uses the forwarding tables in memory to minimize network disruption. The physical interfaces on the other available stack members are not affected during a new stack master election and reset.
After a new stack master is elected and the previous stack master becomes available, the previous stack master does not resume its role as stack master.
As described in the hardware installation guide, you can use the Master LED on the switch to see if the switch is the stack master.
Switch Stack Bridge ID and Router MAC Address
The bridge ID and router MAC address identify the switch stack in the network. When the switch stack initializes, the MAC address of the stack master determines the bridge ID and router MAC address.
If the stack master changes, the MAC address of the new stack master determines the new bridge ID and router MAC address. However, when the persistent MAC address feature is enabled, the stack MAC address changes in approximately 4 minutes. During this time period, if the previous stack master rejoins the stack, the stack continues to use its MAC address as the stack MAC address, even if the switch is now a stack member and not a stack master. If the previous stack master does not rejoin the stack during this period, the switch stack takes the MAC address of the new stack master as the stack MAC address. See Enabling Persistent MAC Address for more information.
Stack Member Numbers
The stack member number (1 to 9) identifies each member in the switch stack. The member number also determines the interface-level configuration that a stack member uses. You can display the stack member number by using the show switch user EXEC command.
A new, out-of-the-box switch (one that has not joined a switch stack or has not been manually assigned a stack member number) ships with a default stack member number of 1. When it joins a switch stack, its default stack member number changes to the lowest available member number in the stack.
Stack members in the same switch stack cannot have the same stack member number. Every stack member, including a standalone switch, retains its member number until you manually change the number or unless the number is already being used by another member in the stack.
- If you manually change the stack member number by using the switch current-stack-member-number renumber new-stack-member-number global configuration command, the new number goes into effect after that stack member resets (or after you use the reload slot stack-member-number privileged EXEC command) and only if that number is not already assigned to any other members in the stack. For more information, see the “Assigning a Stack Member Number” section. Another way to change the stack member number is by changing the SWITCH_NUMBER environment variable, as explained in the “Controlling Environment Variables” section.
If the number is being used by another member in the stack, the switch selects the lowest available number in the stack.
If you manually change the number of a stack member and no interface-level configuration is associated with that new member number, that stack member resets to its default configuration. For more information about stack member numbers and configurations, see the “Switch Stack Configuration Files” section.
You cannot use the switch current-stack-member-number renumber new-stack-member-number global configuration command on a provisioned switch. If you do, the command is rejected.
- If you move a stack member to a different switch stack, the stack member retains its number only if the number is not being used by another member in the stack. If it is being used, the switch selects the lowest available number in the stack.
- If you merge switch stacks, the switches that join the switch stack of a new stack master select the the lowest available numbers in the stack. For more information about merging switch stacks, see the “Switch Stack Membership” section.
As described in the hardware installation guide, you can use the switch port LEDs in Stack mode to visually determine the stack member number of each stack member.
Stack Member Priority Values
A higher priority value for a stack member increases its likelihood of being elected stack master and retaining its stack member number. The priority value can be 1 to 15. The default priority value is 1. You can display the stack member priority value by using the show switch user EXEC command.

Note![]() We recommend assigning the highest priority value to the switch that you prefer to be the stack master. This ensures that the switch is re-elected as stack master.
We recommend assigning the highest priority value to the switch that you prefer to be the stack master. This ensures that the switch is re-elected as stack master.
You can change the priority value for a stack member by using the switch stack-member-number priority new-p riority-value global configuration command. For more information, see the “Setting the Stack Member Priority Value” section. Another way to change the member priority value is by changing the SWITCH_PRIORITY environment variable, as explained in the “Controlling Environment Variables” section.
The new priority value takes effect immediately but does not affect the current stack master. The new priority value helps determine which stack member is elected as the new stack master when the current stack master or the switch stack resets.
Switch Stack Offline Configuration
You can use the offline configuration feature to provision (to supply a configuration to) a new switch before it joins the switch stack. You can configure in advance the stack member number, the switch type, and the interfaces associated with a switch that is not currently part of the stack. The configuration that you create on the switch stack is called the provisioned configuration . The switch that is added to the switch stack and that receives this configuration is called the provisioned switch .
You manually create the provisioned configuration through the switch stack-member-number provision type global configuration command. The provisioned configuration is automatically created when a switch is added to a switch stack and when no provisioned configuration exists.
When you configure the interfaces associated with a provisioned switch (for example, as part of a VLAN), the switch stack accepts the configuration, and the information appears in the running configuration. The interface associated with the provisioned switch is not active, operates as if it is administratively shut down, and the no shutdown interface configuration command does not return it to active service. The interface associated with the provisioned switch does not appear in the display of the specific feature; for example, it does not appear in the show vlan user EXEC command output.
The switch stack retains the provisioned configuration in the running configuration whether or not the provisioned switch is part of the stack. You can save the provisioned configuration to the startup configuration file by entering the copy running-config startup-config privileged EXEC command. The startup configuration file ensures that the switch stack can reload and can use the saved information whether or not the provisioned switch is part of the switch stack.
Effects of Adding a Provisioned Switch to a Switch Stack
When you add a provisioned switch to the switch stack, the stack applies either the provisioned configuration or the default configuration. Table 5-1 lists the events that occur when the switch stack compares the provisioned configuration with the provisioned switch.
If you add a provisioned switch that is a different type than specified in the provisioned configuration to a powered-down switch stack and then apply power, the switch stack rejects the (now incorrect) switch stack-member-number provision type global configuration command in the startup configuration file. However, during stack initialization, the nondefault interface configuration information in the startup configuration file for the provisioned interfaces (potentially of the wrong type) is executed. Depending on the differences between the actual switch type and the previously provisioned switch type, some commands are rejected, and some commands are accepted.
For example, suppose the switch stack is provisioned for a 48-port switch with Power over Ethernet (PoE), the configuration is saved, and the stack is powered down. Then a 24-port switch without PoE support is connected to the switch stack, and the stack is powered up. In this situation, the configuration for ports 25 through 48 is rejected, and error messages appear during initialization. In addition, any configured PoE-related commands that are valid only on PoE-capable interfaces are rejected, even for ports 1 through 24.

Note![]() If the switch stack does not contain a provisioned configuration for a new switch, the switch joins the stack with the default interface configuration. The switch stack then adds to its running configuration a switch stack-member-number provision type global configuration command that matches the new switch.
If the switch stack does not contain a provisioned configuration for a new switch, the switch joins the stack with the default interface configuration. The switch stack then adds to its running configuration a switch stack-member-number provision type global configuration command that matches the new switch.
For configuration information, see the “Provisioning a New Member for a Switch Stack” section.
Effects of Replacing a Provisioned Switch in a Switch Stack
When a provisioned switch in a switch stack fails, is removed from the stack, and is replaced with another switch, the stack applies either the provisioned configuration or the default configuration to it. The events that occur when the switch stack compares the provisioned configuration with the provisioned switch are the same as those described in the “Effects of Adding a Provisioned Switch to a Switch Stack” section.
Effects of Removing a Provisioned Switch from a Switch Stack
If you remove a provisioned switch from the switch stack, the configuration associated with the removed stack member remains in the running configuration as provisioned information. To completely remove the configuration, use the no switch stack-member-number provision global configuration command.
Hardware Compatibility and SDM Mismatch Mode in Switch Stacks
The Catalyst 3750-X switch supports only the desktop Switch Database Management (SDM) templates.
All stack members use the SDM template configured on the stack master.
Version-mismatch (VM) mode has priority over SDM-mismatch mode. If a VM-mode condition and an SDM-mismatch mode exist, the switch stack first attempts to resolve the VM-mode condition.
You can use the show switch privileged EXEC command to see if any stack members are in SDM-mismatch mode.
For more information about SDM templates and SDM-mismatch mode, see Chapter8, “Configuring SDM Templates”
For information about mixed hardware stacks, see the Cisco IOS Software Installation document on Cisco.com.
Switch Stack Software Compatibility Recommendations
To ensure complete compatibility between stack members, use the information in this section and also in the “Hardware Compatibility and SDM Mismatch Mode in Switch Stacks” section.
All stack members must run the same Cisco IOS software image and feature set to ensure compatibility between stack members. For example, all stack members should run the universal software image and have the IP services feature set enabled for the Cisco IOS Release 12.2(53)SE2 or later.
For more information, see the “Stack Protocol Version Compatibility” section and the Cisco IOS Software Installation document on Cisco.com.
For information about mixed hardware and software stacks, see the Cisco IOS Software Activation document on Cisco.com.
Stack Protocol Version Compatibility
Each software image includes a stack protocol version. The stack protocol version has a major version number and a minor version number (for example 1.4, where 1 is the major version number and 4 is the minor version number). Both version numbers determine the level of compatibility among the stack members. You can display the stack protocol version by using the show platform stack-manager all privileged EXEC command.
Switches with the same Cisco IOS software version have the same stack protocol version. Such switches are fully compatible, and all features function properly across the switch stack. Switches with the same Cisco IOS software version as the stack master immediately join the switch stack.
If an incompatibility exists, the fully functional stack members generate a system message that describes the cause of the incompatibility on the specific stack members. The stack master sends the message to all stack members. For more information, see the Major Version Number Incompatibility Among Switches and the Minor Version Number Incompatibility Among Switches.
Major Version Number Incompatibility Among Switches
Switches with different major Cisco IOS software versions usually have different stack protocol versions. Switches with different major version numbers are incompatible and cannot exist in the same switch stack.
Minor Version Number Incompatibility Among Switches
Switches with the same major version number but with a different minor version number are considered partially compatible. When connected to a switch stack, a partially compatible switch enters version-mismatch (VM) mode and cannot join the stack as a fully functioning member. The software detects the mismatched software and tries to upgrade (or downgrade) the switch in VM mode with the switch stack image or with a tar file image from the switch stack flash memory. The software uses the automatic upgrade (auto-upgrade) and the automatic advise (auto-advise) features. For more information, see the “Understanding Auto-Upgrade and Auto-Advise” section.
To see if there are switches in VM mode, use the show switch user EXEC command. The port LEDs on switches in VM mode stay off. Pressing the Mode button does not change the LED mode.
You can use the boot auto-download-sw global configuration command to specify a URL pathname for the master switch to use to get an image in case of version mismatch.
Understanding Auto-Upgrade and Auto-Advise
When the software detects mismatched software and tries to upgrade the switch in VM mode, two software processes are involved: automatic upgrade and automatic advise.
- The automatic upgrade (auto-upgrade) process includes an auto-copy process and an auto-extract process. By default, auto-upgrade is enabled (the boot auto-copy-sw global configuration command is enabled). You can disable auto-upgrade by using the no boot auto-copy-sw global configuration command on the stack master. You can check the status of auto-upgrade by using the show boot privileged EXEC command and by checking the Auto upgrade line in the display.
–![]() Auto-copy automatically copies the software image running on any stack member to the switch in VM mode to upgrade (auto-upgrade) it. Auto-copy occurs if auto-upgrade is enabled, if there is enough flash memory in the switch in VM mode, and if the software image running on the switch stack is suitable for the switch in VM mode.
Auto-copy automatically copies the software image running on any stack member to the switch in VM mode to upgrade (auto-upgrade) it. Auto-copy occurs if auto-upgrade is enabled, if there is enough flash memory in the switch in VM mode, and if the software image running on the switch stack is suitable for the switch in VM mode.

Note![]() A switch in VM mode might not run all released software. For example, new switch hardware is not recognized in earlier versions of software.
A switch in VM mode might not run all released software. For example, new switch hardware is not recognized in earlier versions of software.
–![]() Automatic extraction (auto-extract) occurs when the auto-upgrade process cannot find the appropriate software in the stack to copy to the switch in VM mode. In that case, the auto-extract process searches all switches in the stack, whether they are in VM mode or not, for the tar file needed to upgrade the switch stack or the switch in VM mode. The tar file can be in any flash file system in the switch stack (including the switch in VM mode). If a tar file suitable for the switch in VM mode is found, the process extracts the file and automatically upgrades that switch.
Automatic extraction (auto-extract) occurs when the auto-upgrade process cannot find the appropriate software in the stack to copy to the switch in VM mode. In that case, the auto-extract process searches all switches in the stack, whether they are in VM mode or not, for the tar file needed to upgrade the switch stack or the switch in VM mode. The tar file can be in any flash file system in the switch stack (including the switch in VM mode). If a tar file suitable for the switch in VM mode is found, the process extracts the file and automatically upgrades that switch.
The auto-upgrade (auto-copy and auto-extract) processes wait for a few minutes after the mismatched software is detected before starting.
When the auto-upgrade process is complete, the switch that was in VM mode reloads and joins the stack as a fully functioning member. If you have both StackWise Plus cables connected during the reload, network downtime does not occur because the switch stack operates on two rings.

Note![]() Auto-upgrade performs the upgrade only when the two feature sets are the same type. For example, it does not automatically upgrade a switch in VM mode from IP services feature set to IP base feature set (or the reverse).
Auto-upgrade performs the upgrade only when the two feature sets are the same type. For example, it does not automatically upgrade a switch in VM mode from IP services feature set to IP base feature set (or the reverse).
- Automatic advise (auto-advise) occurs when the auto-upgrade process cannot find appropriate stack member software to copy to the switch in VM mode. This process tells you the command (archive copy-sw or archive download-sw privileged EXEC command) and the image name (tar filename) needed to manually upgrade the switch stack or the switch in VM mode. The recommended image can be the running switch stack image or a tar file in any flash file system in the switch stack (including the switch in VM mode). If an appropriate image is not found in the stack flash file systems, the auto-advise process tells you to install new software on the switch stack. Auto-advise cannot be disabled, and there is no command to check its status.
The auto-advise software does not give suggestions when the switch stack software and the software of the switch in VM mode do not contain the same feature sets. For example, if the switch stack is running the IP base image and you add a switch that is running the IP services image, the auto-advise software does not provide a recommendation.
You can use the archive-download-sw /allow-feature-upgrade privileged EXEC command to allow installing an different software image.
Auto-Upgrade and Auto-Advise Example Messages
When you add a switch that has a different minor version number to the switch stack, the software displays messages in sequence (assuming that there are no other system messages generated by the switch).
This example shows that the switch stack detected a new switch that is running a different minor version number than the switch stack. Auto-copy starts, finds suitable software to copy from a stack member to the switch in VM mode, upgrades the switch in VM mode, and then reloads it:
*Mar 11 20:36:15.038:%IMAGEMGR-6-AUTO_COPY_SW: Image
Feature:IP|LAYER_3|PLUS|MIN_DRAM_MEG=128
This example shows that the switch stack detected a new switch that is running a different minor version number than the switch stack. Auto-copy starts but cannot find software in the switch stack to copy to the VM-mode switch to make it compatible with the switch stack. The auto-advise process starts and recommends that you download a tar file from the network to the switch in VM mode:
For information about using the archive download-sw privileged EXEC command, see the “Working with Software Images” section.

Note![]() Auto-advise and auto-copy identify which images are running by examining the info file and by searching the directory structure on the switch stack. If you download your image by using the copy tftp: boot loader command instead of the archive download-sw privileged EXEC command, the proper directory structure is not created. For more information about the info file, see the “File Format of Images on a Server or Cisco.com” section.
Auto-advise and auto-copy identify which images are running by examining the info file and by searching the directory structure on the switch stack. If you download your image by using the copy tftp: boot loader command instead of the archive download-sw privileged EXEC command, the proper directory structure is not created. For more information about the info file, see the “File Format of Images on a Server or Cisco.com” section.
Incompatible Software and Stack Member Image Upgrades
You can upgrade a switch that has an incompatible universal software image by using the archive copy-sw privileged EXEC command. It copies the software image from an existing stack member to the one with incompatible software. That switch automatically reloads and joins the stack as a fully functioning member. For more information, see the “Copying an Image File from One Stack Member to Another” section.
Switch Stack Configuration Files
The configuration files record these settings:
- System-level (global) configuration settings—such as IP, STP, VLAN, and SNMP settings—that apply to all stack members
- Stack member interface-specific configuration settings that are specific for each stack member
The stack master has the saved and running configuration files for the switch stack. All stack members periodically receive synchronized copies of the configuration files from the stack master. If the stack master becomes unavailable, any stack member assuming the role of stack master has the latest configuration files.

Note![]() The interface-specific settings of the stack master are saved if the stack master is replaced without saving the running configuration to the startup configuration.
The interface-specific settings of the stack master are saved if the stack master is replaced without saving the running configuration to the startup configuration.
When a new, out-of-box switch joins a switch stack, it uses the system-level settings of that switch stack. If a switch is moved to a different switch stack, that switch loses its saved configuration file and uses the system-level configuration of the new switch stack.
The interface-specific configuration of each stack member is associated with the stack member number. As mentioned in the “Stack Member Numbers” section, stack members retain their numbers unless they are manually changed or they are already used by another member in the same switch stack.
- If an interface-specific configuration does not exist for that member number, the stack member uses its default interface-specific configuration.
- If an interface-specific configuration exists for that member number, the stack member uses the interface-specific configuration associated with that member number.
If a stack member fails and you replace with it with an identical model, the replacement switch automatically uses the same interface-specific configuration as the failed switch. Hence, you do not need to reconfigure the interface settings. The replacement switch must have the same stack member number as the failed switch. For information about the benefits of provisioning a switch stack, see the “Switch Stack Offline Configuration” section.
You back up and restore the stack configuration in the same way as you would for a standalone switch configuration. For more information about file systems and configuration files, see Appendix B, “Working with the Cisco IOS File System, Configuration Files, and Software Images.”
Additional Considerations for System-Wide Configuration on Switch Stacks
These sections provide additional considerations for configuring system-wide features on switch stacks:
- “Planning and Creating Clusters” chapter in the Getting Started with Cisco Network Assistant, available on Cisco.com
- “MAC Addresses and Switch Stacks” section
- “Setting the SDM Template” section
- “802.1x Authentication and Switch Stacks” section
- “VTP and Switch Stacks” section
- “Private VLANs and Switch Stacks” section
- “Spanning Tree and Switch Stacks” section
- “MSTP and Switch Stacks” section
- “DHCP Snooping and Switch Stacks” section
- “IGMP Snooping and Switch Stacks” section
- “Port Security and Switch Stacks” section
- “CDP and Switch Stacks” section
- “SPAN and RSPAN and Switch Stacks” section
- “ACLs and Switch Stacks” section
- “EtherChannel and Switch Stacks” section
- “IP Routing and Switch Stacks” section
- “IPv6 and Switch Stacks” section
- “HSRP and Switch Stacks” section
- “Multicast Routing and Switch Stacks” section
- “Fallback Bridging and Switch Stacks” section
Switch Stack Management Connectivity
You manage the switch stack and the stack member interfaces through the stack master. You can use the CLI, SNMP, Network Assistant, and CiscoWorks network management applications. You cannot manage stack members on an individual switch basis.
These sections provide switch stack connectivity information:
Connectivity to the Switch Stack Through an IP Address
The switch stack is managed through a single IP address. The IP address is a system-level setting and is not specific to the stack master or to any other stack member. You can still manage the stack through the same IP address even if you remove the stack master or any other stack member from the stack, provided there is IP connectivity.

Note![]() Stack members retain their IP addresses when you remove them from a switch stack. To avoid a conflict by having two devices with the same IP address in your network, change the IP addresses of any switches that you remove from the switch stack.
Stack members retain their IP addresses when you remove them from a switch stack. To avoid a conflict by having two devices with the same IP address in your network, change the IP addresses of any switches that you remove from the switch stack.
For related information about switch stack configurations, see the “Switch Stack Configuration Files” section.
Connectivity to the Switch Stack Through an SSH Session
In a mixed stack, Secure Shell (SSH) connectivity to the switch stack can be lost if a stack master running the cryptographic software image and the IP base or IP services feature set fails and is replaced by a switch that is running the noncryptographic image and the same feature set. We recommend that a switch running the cryptographic software image and the IP base or IP services feature set be the stack master. Encryption features are unavailable if the stack master is running the noncryptographic software image.

Note![]() The noncryptographic software image was available only on Catalyst 3750 or Catalyst 3750-E switches running Cisco IOS Release 12.2(53)SE and earlier. The Catalyst 3750-X switches run only the cryptographic software image.
The noncryptographic software image was available only on Catalyst 3750 or Catalyst 3750-E switches running Cisco IOS Release 12.2(53)SE and earlier. The Catalyst 3750-X switches run only the cryptographic software image.
Connectivity to the Switch Stack Through Console Ports or Ethernet Management Ports
You can connect to the stack master by using one of these methods:
- You can connect a terminal or a PC to the stack master through the console port of one or more stack members.
- You can connect a PC to the stack master through the Ethernet management ports of one or more Catalyst 3750-X stack members. For more information about connecting to the switch stack through Ethernet management ports, see the “Using the Ethernet Management Port” section.
Be careful when using multiple CLI sessions to the stack master. Commands that you enter in one session are not displayed in the other sessions. Therefore, it is possible that you might not be able to identify the session from which you entered a command.
We recommend using only one CLI session when managing the switch stack.
Connectivity to Specific Stack Members
If you want to configure a specific stack member port, you must include the stack member number in the CLI command interface notation. For more information, see the “Using Interface Configuration Mode” section.
To debug a specific stack member, you can access it from the stack master by using the session stack-member-number privileged EXEC command. The stack member number is appended to the system prompt. For example, Switch-2# is the prompt in privileged EXEC mode for stack member 2, and the system prompt for the stack master is Switch. Only the show and debug commands are available in a CLI session to a specific stack member.
Switch Stack Configuration Scenarios
Table 5-2 provides switch stack configuration scenarios. Most of the scenarios assume that at least two switches are connected through their StackWise Plus ports.
|
|
|
|
|---|---|---|
Stack master election specifically determined by existing stack masters |
Connect two powered-on switch stacks through the StackWise Plus ports. |
Only one of the two stack masters becomes the new stack master. None of the other stack members become the stack master. |
Stack master election specifically determined by the stack member priority value |
1. 2. |
The stack member with the higher priority value is elected stack master. |
Stack master election specifically determined by the configuration file |
Assuming that both stack members have the same priority value: 1. |
The stack member with the saved configuration file is elected stack master. |
Stack master election specifically determined by the cryptographic software image and the IP services feature set and the IP services feature set |
Assuming that all stack members have the same priority value: 1. |
The stack member with the cryptographic image and the IP services feature set is elected stack master. Note Only Catalyst 3650-E or 3750 switches running Cisco IOS Release 12.2(53)SE or earlier could be running the noncyrptographic image. |
Stack master election specifically determined by the cryptographic software image and the IP base feature set |
Assuming that all stack members have the same priority value: 1. |
The stack member with the cryptographic image and the IP base feature set is elected stack master. Note Only Catalyst 3650-E or 3750 switches running Cisco IOS Release 12.2(53)SE or earlier could be running the noncyrptographic image. |
Stack master election specifically determined by the MAC address |
Assuming that both stack members have the same priority value, configuration file, and feature set, restart both stack members at the same time. |
The stack member with the lower MAC address is elected stack master. |
Assuming that one stack member has a higher priority value than the other stack member: 1. |
The stack member with the higher priority value retains its stack member number. The other stack member has a new stack member number. |
|
| 2. |
The stack master is retained. The new switch is added to the switch stack. |
|
Based on the factors described in the “Stack Master Election and Re-Election” section, one of the remaining stack members becomes the new stack master. All other stack members in the stack remain as stack members and do not reboot. |
||
1. |
Two switches become stack masters. One stack master has nine stack members. The other stack master remains as a standalone switch. Use the Mode button and port LEDs on the switches to identify which switches are stack masters and which switches belong to each stack master. For information about using the Mode button and the LEDs, see the hardware installation guide. |
|
Configuring the Switch Stack
These sections contain this configuration information:
- Default Switch Stack Configuration
- Enabling Persistent MAC Address
- Assigning Stack Member Information
Default Switch Stack Configuration
Table 5-3 shows the default switch stack configuration.
|
|
|
|---|---|
Enabling Persistent MAC Address
The switch stack MAC address is determined by the MAC address of the stack master. When a stack master is removed from the stack and a new stack master takes over, the default is for the MAC address of the new stack master to immediately become the new stack MAC router address. However, you can enable the persistent MAC address feature to allow a time delay before the stack MAC address changes. During this time period, if the previous stack master rejoins the stack, the stack continues to use its MAC address as the stack MAC address, even if the switch is now a stack member and not a stack master. If the previous stack master does not rejoin the stack during this period, the switch stack takes the MAC address of the new stack master as the stack MAC address.You can also configure stack MAC persistency so that the stack never switches to the MAC address of the new stack master.

Note![]() When you enter the command to configure this feature, a warning message appears containing the consequences of your configuration. You should use this feature cautiously. Using the old stack master MAC address elsewhere in the same domain could result in lost traffic.
When you enter the command to configure this feature, a warning message appears containing the consequences of your configuration. You should use this feature cautiously. Using the old stack master MAC address elsewhere in the same domain could result in lost traffic.
You can configure the time period as 0 to 60 minutes.
- If you enter the command with no value, the default delay is 4 minutes. We recommend that you always enter a value. If the command is entered without a value, the time delay appears in the running-config file with an explicit timer value of 4 minutes.
- If you enter 0, the stack MAC address of the previous stack master is used until you enter the no stack-mac persistent timer command, which immediately changes the stack MAC address to that of the current stack master. If you do not enter the no stack-mac persistent timer command, the stack MAC address never changes.
- If you enter a time delay of 1 to 60 minutes, the stack MAC address of the previous stack master is used until the configured time period expires or until you enter the no stack-mac persistent timer command.

Note![]() If the entire switch stack reloads, it uses the MAC address of the stack master as the stack MAC address.
If the entire switch stack reloads, it uses the MAC address of the stack master as the stack MAC address.
Beginning in privileged EXEC mode, follow these steps to enable persistent MAC address. This procedure is optional.
Use the no stack-mac persistent timer global configuration command to disable the persistent MAC address feature.
This example shows how to configure the persistent MAC address feature for a 7-minute time delay and to verify the configuration:
Assigning Stack Member Information
These sections describe how to assign stack member information:
- Assigning a Stack Member Number (optional)
- Setting the Stack Member Priority Value (optional)
- Provisioning a New Member for a Switch Stack (optional)
Assigning a Stack Member Number

Note![]() This task is available only from the stack master.
This task is available only from the stack master.
Beginning in privileged EXEC mode, follow these steps to assign a member number to a stack member. This procedure is optional.
Setting the Stack Member Priority Value

Note![]() This task is available only from the stack master.
This task is available only from the stack master.
Beginning in privileged EXEC mode, follow these steps to assign a priority value to a stack member: This procedure is optional.
Provisioning a New Member for a Switch Stack

Note![]() This task is available only from the stack master.
This task is available only from the stack master.
Beginning in privileged EXEC mode, follow these steps to provision a new member for a switch stack. This procedure is optional.
To remove provisioned information and to avoid receiving an error message, remove the specified switch from the stack before you use the no form of this command.
For example, if you are removing a provisioned switch in a stack with this configuration:
and want to remove the provisioned information and to avoid receiving an error message, you can remove power from stack member 3, disconnect the StackWise Plus cables between the stack member 3 and switches to which it is connected, reconnect the cables between the remaining stack members, and enter the no switch stack-member-number provision global configuration command.
This example shows how to provision a switch with a stack member number of 2 for the switch stack. The show running-config command output shows the interfaces associated with the provisioned switch:
Accessing the CLI of a Specific Stack Member

Note![]() This task is only for debugging purposes, and is only available from the master.
This task is only for debugging purposes, and is only available from the master.
You can access all or specific members by using the remote command { all | stack-member-number } privileged EXEC command. The stack member number range is 1 to 9.
You can access specific members by using the session stack-member-number privileged EXEC command. The member number is appended to the system prompt. For example, the prompt for member 2 is Switch-2#, and system prompt for the master is Switch#. Enter exi t to return to the CLI session on the master. Only the show and debug commands are available on a specific member.
Displaying Switch Stack Information
To display saved configuration changes after resetting a specific member or the stack, use these privileged EXEC commands:
Troubleshooting Stacks
- Manually Disabling a Stack Port
- Re-Enabling a Stack Port While Another Member Starts
- Understanding the show switch stack-ports summary Output
- Identifying Loopback Problems
- Finding a Disconnected Stack Cable
- Fixing a Bad Connection Between Stack Ports
Manually Disabling a Stack Port
If a stack port is flapping and causing instability in the stack ring, to disable the port, enter the switch stack-member-number stack port port-number disable privileged EXEC command. To re-enable the port, enter the switch stack-member-number stack port port-number enable command.

Note![]() Be careful when using the switch stack-member-number stack port port-number disable command. When you disable the stack port, the stack operates at half bandwidth.
Be careful when using the switch stack-member-number stack port port-number disable command. When you disable the stack port, the stack operates at half bandwidth.
- A stack is in the full-ring state when all members are connected through the stack ports and are in the ready state.
- The stack is in the partial-ring state when
–![]() All members are connected through the stack ports, but some all are not in the ready state.
All members are connected through the stack ports, but some all are not in the ready state.
–![]() Some members are not connected through the stack ports.
Some members are not connected through the stack ports.
When you enter the switch stack-member-number stack port port-number disable privileged EXEC command and
Re-Enabling a Stack Port While Another Member Starts
Stack Port 1 on Switch 1 is connected to Port 2 on Switch 4. If Port 1 is flapping, disable Port 1 with the switch 1 stack port 1 disable privileged EXEC command.
While Port 1 on Switch 1 is disabled and Switch 1 is still powered on:
1.![]() Disconnect the stack cable between Port 1 on Switch 1 and Port 2 on Switch 4.
Disconnect the stack cable between Port 1 on Switch 1 and Port 2 on Switch 4.
2.![]() Remove Switch 4 from the stack.
Remove Switch 4 from the stack.
3.![]() Add a switch to replace Switch 4 and assign it switch-number 4.
Add a switch to replace Switch 4 and assign it switch-number 4.
4.![]() Reconnect the cable between Port 1 on Switch 1 and Port 2 on Switch 4 (the replacement switch).
Reconnect the cable between Port 1 on Switch 1 and Port 2 on Switch 4 (the replacement switch).
5.![]() Re-enable the link between the switches. Enter the switch 1 stack port 1 enable privileged EXEC command to enable Port 1 on Switch 1.
Re-enable the link between the switches. Enter the switch 1 stack port 1 enable privileged EXEC command to enable Port 1 on Switch 1.

If Switch 4 is powered on first, you might need to enter the switch 1 stack port 1 enable and the switch 4 stack port 2 enable privileged EXEC commands to bring up the link.
Understanding the show switch stack-ports summary Output
Only Port 1 on stack member 2 is disabled.
Identifying Loopback Problems
Software Loopback
In a stack with three members, stack cables connect all the members.
If you disconnect the stack cable from Port 1 on Switch 1, these messages appear:
If you disconnect the stack cable from Port 2 on Switch 1, the stack splits.
Switch 2 and Switch 3 are now in a two-member stack connected through stack cables.
Switch 1 is a standalone switch.
Software Loopback Example: No Connected Stack Cable
Catalyst 3750 switch port status:
Catalyst 3750-E or 3750-X switch port status:
Software Loopback Examples: Connected Stack Cables
On Port 2 on Switch 1, the port status is Absent, and no cable is connected.
- In a physical loopback, a cable connects both stack ports on a switch. You can use this configuration to test
–![]() Cables on a switch that is running properly
Cables on a switch that is running properly
–![]() Stack ports with a cable that works properly
Stack ports with a cable that works properly
Hardware Loopback
The show platform stack ports buffer privileged EXEC command output shows the hardware loopback values.
Hardware Loopback Example: LINK OK event
On a Catalyst 3750-E or 3750-X switch:
Hardware Loop Example: LINK NOT OK Event
On a Catalyst 3750-E or 3750-X switch:
Finding a Disconnected Stack Cable
Stack cables connect all stack members. Port 2 on Switch 1 connects to Port 1 on Switch 2.
This is the port status for the members:
If you disconnect the cable from Port 2 on Switch 1, these messages appear:
Only one end of the cable connects to a stack port, Port 1 on Switch 2.
- The Stack Port Status value for Port 2 on Switch 1 is Absent, and the value for Port 1 on Switch 2 is Down.
- The Cable Length value is No cable.
- Verify the cable connection for Port 2 on Switch 1.
- Port 2 on Switch 1 has a port or cable problem if
Fixing a Bad Connection Between Stack Ports
Stack cables connect all members. Port 2 on Switch 1 connects to Port 1 on Switch 2.
- The Stack Port Status value is Down.
- Link OK, Link Active, and Sync OK values are No.
- The Cable Length value is 50 cm. The switch detects and correctly identifies the cable.
The connection between Port 2 on Switch 1 and Port 1 on Switch 2 is unreliable on at least one of the connector pins.
 Feedback
Feedback