- Index
- Preface
- Overview
- Using the Command-Line Interface
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS Configuration Engine
- Managing Switch Stacks
- Clustering Switches
- Administering the Switch
- Configuring SDM Templates
- Managing Catalyst 3750-X Stack Power
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring Interface Characteristics
- Configuring Auto Smartports Macros
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLANs
- Configuring Private VLANs
- Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Flex Links
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IGMP Snooping and MVR
- Configuring IPv6 MLD Snooping
- Configuring Port-Based Traffic Control
- Configuring CDP
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring UDLD
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Embedded Event Manager
- Configuring Network Security with ACLs
- Configuring IPv6 ACLs
- Configuring QoS
- Configuring EtherChannels
- Configuring TelePresence E911 IP Phone Support
- Configuring IP Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring HSRP
- Configuring Cisco IOS IP SLAs Operations
- Configuring Enhanced Object Tracking
- Configuring WCCP
- Configuring IP Multicast Routing
- Configuring MSDP
- Configuring Fallback Bridging
- Troubleshooting
- Configuring Online Diagnostics
- Supported MIBs
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 12.2(53)SE
- Understanding the Boot Process
- Assigning Switch Information
- Checking and Saving the Running Configuration
- Modifying the Startup Configuration
- Scheduling a Reload of the Software Image
Assigning the Switch IP Address and Default Gateway
This chapter describes how to create the initial switch configuration (for example, assigning the IP address and default gateway information) by using a variety of automatic and manual methods. It also describes how to modify the switch startup configuration. Unless otherwise noted, the term switch refers to a Catalyst 3750-X or 3560-X standalone switch and to a Catalyst 3750-X switch stack.

Note![]() For complete syntax and usage information for the commands used in this chapter, see the command reference for this release and the Cisco IOS IP Command Reference, Volume 1 of 3: Addressing and Services, Release 12.2.
For complete syntax and usage information for the commands used in this chapter, see the command reference for this release and the Cisco IOS IP Command Reference, Volume 1 of 3: Addressing and Services, Release 12.2.
This chapter consists of these sections:
- Understanding the Boot Process
- Assigning Switch Information
- Checking and Saving the Running Configuration
- Modifying the Startup Configuration
- Scheduling a Reload of the Software Image

Note![]() Information in this chapter about configuring IP addresses and DHCP is specific to IP Version 4 (IPv4). If you plan to enable IP Version 6 (IPv6) forwarding on your switch, see Chapter 43, “Configuring IPv6 Unicast Routing” for information specific to IPv6 address format and configuration. To enable IPv6, the stack or switch must be running the IP services feature set.
Information in this chapter about configuring IP addresses and DHCP is specific to IP Version 4 (IPv4). If you plan to enable IP Version 6 (IPv6) forwarding on your switch, see Chapter 43, “Configuring IPv6 Unicast Routing” for information specific to IPv6 address format and configuration. To enable IPv6, the stack or switch must be running the IP services feature set.
Understanding the Boot Process
To start your switch, you need to follow the procedures in the hardware installation guide for installing and powering on the switch and setting up the initial switch configuration (IP address, subnet mask, default gateway, secret and Telnet passwords, and so forth).
The normal boot process involves the operation of the boot loader software and includes these activities:
- Performs low-level CPU initialization. It initializes the CPU registers, which control where physical memory is mapped, its quantity, its speed, and so forth.
- Performs power-on self-test (POST) for the CPU subsystem. It tests the CPU DRAM and the portion of the flash device that makes up the flash file system.
- Initializes the flash file system on the system board.
- Loads a default operating system software image into memory and boots up the switch.
The boot loader provides access to the flash file system before the operating system is loaded. Normally, the boot loader is used only to load, uncompress, and start the operating system. After the boot loader gives the operating system control of the CPU, the boot loader is not active until the next system reset or power-on.
The boot loader also provides trap-door access into the system if the operating system has problems serious enough that it cannot be used. The trap-door mechanism provides enough access to the system so that if it is necessary, you can format the flash file system, reinstall the operating system software image by using the Xmodem Protocol, recover from a lost or forgotten password, and finally restart the operating system. For more information, see the “Recovering from a Software Failure” section and the “Recovering from a Lost or Forgotten Password” section.

Note![]() You can disable password recovery. For more information, see the “Disabling Password Recovery” section.
You can disable password recovery. For more information, see the “Disabling Password Recovery” section.
Before you can assign switch information, make sure you have connected a PC or terminal to the console port or a PC to the Ethernet management port, and make sure you have configured the PC or terminal-emulation software baud rate and character format to match these of the switch console port:

Note![]() If the data bits option is set to 8, set the parity option to none.
If the data bits option is set to 8, set the parity option to none.
Assigning Switch Information
You can assign IP information through the switch setup program, through a DHCP server, or manually.
Use the switch setup program if you want to be prompted for specific IP information. With this program, you can also configure a hostname and an enable secret password. It gives you the option of assigning a Telnet password (to provide security during remote management) and configuring your switch as a command or member switch of a cluster or as a standalone switch. For more information about the setup program, see the hardware installation guide.
The switch stack is managed through a single IP address. The IP address is a system-level setting and is not specific to the stack master or to any other stack member. You can still manage the stack through the same IP address even if you remove the stack master or any other stack member from the stack, provided there is IP connectivity.

Note![]() Stack members retain their IP address when you remove them from a switch stack. To avoid a conflict by having two devices with the same IP address in your network, change the IP address of the switch that you removed from the switch stack.
Stack members retain their IP address when you remove them from a switch stack. To avoid a conflict by having two devices with the same IP address in your network, change the IP address of the switch that you removed from the switch stack.
Use a DHCP server for centralized control and automatic assignment of IP information after the server is configured.

Note![]() If you are using DHCP, do not respond to any of the questions in the setup program until the switch receives the dynamically assigned IP address and reads the configuration file.
If you are using DHCP, do not respond to any of the questions in the setup program until the switch receives the dynamically assigned IP address and reads the configuration file.
If you are an experienced user familiar with the switch configuration steps, manually configure the switch. Otherwise, use the setup program described previously.
These sections contain this configuration information:
- Default Switch Information
- Understanding DHCP-Based Autoconfiguration
- Manually Assigning IP Information
Default Switch Information
Table 3-1 shows the default switch information.
|
|
|
|---|---|
Understanding DHCP-Based Autoconfiguration
DHCP provides configuration information to Internet hosts and internetworking devices. This protocol consists of two components: one for delivering configuration parameters from a DHCP server to a device and a mechanism for allocating network addresses to devices. DHCP is built on a client-server model, in which designated DHCP servers allocate network addresses and deliver configuration parameters to dynamically configured devices. The switch can act as both a DHCP client and a DHCP server.
During DHCP-based autoconfiguration, your switch (DHCP client) is automatically configured at startup with IP address information and a configuration file.
With DHCP-based autoconfiguration, no DHCP client-side configuration is needed on your switch. However, you need to configure the DHCP server for various lease options associated with IP addresses. If you are using DHCP to relay the configuration file location on the network, you might also need to configure a Trivial File Transfer Protocol (TFTP) server and a Domain Name System (DNS) server.

Note![]() We recommend a redundant connection between a switch stack and the DHCP, DNS, and TFTP servers. This is to help ensure that these servers remain accessible in case one of the connected stack members is removed from the switch stack.
We recommend a redundant connection between a switch stack and the DHCP, DNS, and TFTP servers. This is to help ensure that these servers remain accessible in case one of the connected stack members is removed from the switch stack.
The DHCP server for your switch can be on the same LAN or on a different LAN than the switch. If the DHCP server is running on a different LAN, you should configure a DHCP relay device between your switch and the DHCP server. A relay device forwards broadcast traffic between two directly connected LANs. A router does not forward broadcast packets, but it forwards packets based on the destination IP address in the received packet.
DHCP-based autoconfiguration replaces the BOOTP client functionality on your switch.
DHCP Client Request Process
When you boot up your switch, the DHCP client is invoked and requests configuration information from a DHCP server when the configuration file is not present on the switch. If the configuration file is present and the configuration includes the ip address dhcp interface configuration command on specific routed interfaces, the DHCP client is invoked and requests the IP address information for those interfaces.
Figure 3-1 shows the sequence of messages that are exchanged between the DHCP client and the DHCP server.
Figure 3-1 DHCP Client and Server Message Exchange
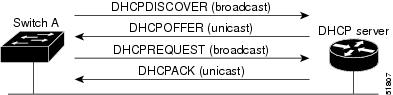
The client, Switch A, broadcasts a DHCPDISCOVER message to locate a DHCP server. The DHCP server offers configuration parameters (such as an IP address, subnet mask, gateway IP address, DNS IP address, a lease for the IP address, and so forth) to the client in a DHCPOFFER unicast message.
In a DHCPREQUEST broadcast message, the client returns a formal request for the offered configuration information to the DHCP server. The formal request is broadcast so that all other DHCP servers that received the DHCPDISCOVER broadcast message from the client can reclaim the IP addresses that they offered to the client.
The DHCP server confirms that the IP address has been allocated to the client by returning a DHCPACK unicast message to the client. With this message, the client and server are bound, and the client uses configuration information received from the server. The amount of information the switch receives depends on how you configure the DHCP server. For more information, see the “Configuring the TFTP Server” section.
If the configuration parameters sent to the client in the DHCPOFFER unicast message are invalid (a configuration error exists), the client returns a DHCPDECLINE broadcast message to the DHCP server.
The DHCP server sends the client a DHCPNAK denial broadcast message, which means that the offered configuration parameters have not been assigned, that an error has occurred during the negotiation of the parameters, or that the client has been slow in responding to the DHCPOFFER message (the DHCP server assigned the parameters to another client).
A DHCP client might receive offers from multiple DHCP or BOOTP servers and can accept any of the offers; however, the client usually accepts the first offer it receives. The offer from the DHCP server is not a guarantee that the IP address is allocated to the client; however, the server usually reserves the address until the client has had a chance to formally request the address. If the switch accepts replies from a BOOTP server and configures itself, the switch broadcasts, instead of unicasts, TFTP requests to obtain the switch configuration file.
The DHCP hostname option allows a group of switches to obtain hostnames and a standard configuration from the central management DHCP server. A client (switch) includes in its DCHPDISCOVER message an option 12 field used to request a hostname and other configuration parameters from the DHCP server. The configuration files on all clients are identical except for their DHCP-obtained hostnames.
If a client has a default hostname (the hostname name global configuration command is not configured or the no hostname global configuration command is entered to remove the hostname), the DHCP hostname option is not included in the packet when you enter the ip address dhcp interface configuration command. In this case, if the client receives the DCHP hostname option from the DHCP interaction while acquiring an IP address for an interface, the client accepts the DHCP hostname option and sets the flag to show that the system now has a hostname configured.
Understanding DHCP-based Autoconfiguration and Image Update
You can use the DHCP image upgrade features to configure a DHCP server to download both a new image and a new configuration file to one or more switches in a network. This helps ensure that each new switch added to a network receives the same image and configuration.
There are two types of DHCP image upgrades: DHCP autoconfiguration and DHCP auto-image update.
DHCP Autoconfiguration
DHCP autoconfiguration downloads a configuration file to one or more switches in your network from a DHCP server. The downloaded configuration file becomes the running configuration of the switch. It does not over write the bootup configuration saved in the flash, until you reload the switch.
DHCP Auto-Image Update
You can use DHCP auto-image upgrade with DHCP autoconfiguration to download both a configuration and a new image to one or more switches in your network. The switch (or switches) downloading the new configuration and the new image can be blank (or only have a default factory configuration loaded).
If the new configuration is downloaded to a switch that already has a configuration, the downloaded configuration is appended to the configuration file stored on the switch. (Any existing configuration is not overwritten by the downloaded one.)
To enable a DHCP auto-image update on the switch, the TFTP server where the image and configuration files are located must be configured with the correct option 67 (the configuration filename), option 66 (the DHCP server hostname) option 150 (the TFTP server address), and option 125 (description of the file) settings.

Note![]() For procedures to configure the switch as a DHCP server, see the “Configuring DHCP Autoconfiguration (Only Configuration File)” section and the “Configuring DHCP” section of the “IP Addressing and Services” section of the Cisco IOS IP Configuration Guide, Release 12.2 at this URL:
For procedures to configure the switch as a DHCP server, see the “Configuring DHCP Autoconfiguration (Only Configuration File)” section and the “Configuring DHCP” section of the “IP Addressing and Services” section of the Cisco IOS IP Configuration Guide, Release 12.2 at this URL:
http://www.cisco.com/en/US/docs/ios/12_2/ip/configuration/guide/1cfdhcp.html
After you install the switch in your network, the auto-image update feature starts. The downloaded configuration file is saved in the running configuration of the switch, and the new image is downloaded and installed on the switch. When you reboot the switch, the configuration is stored in the saved configuration on the switch.
Limitations and Restrictions
- The DHCP-based autoconfiguration with a saved configuration process stops if there is not at least one Layer 3 interface in an up state without an assigned IP address in the network.
- Unless you configure a timeout, the DHCP-based autoconfiguration with a saved configuration feature tries indefinitely to download an IP address.
- The auto-install process stops if a configuration file cannot be downloaded or it the configuration file is corrupted.

Note![]() The configuration file that is downloaded from TFTP is merged with the existing configuration in the running configuration but is not saved in the NVRAM unless you enter the write memory or copy running-configuration startup-configuration privileged EXEC command. Note that if the downloaded configuration is saved to the startup configuration, the feature is not triggered during subsequent system restarts.
The configuration file that is downloaded from TFTP is merged with the existing configuration in the running configuration but is not saved in the NVRAM unless you enter the write memory or copy running-configuration startup-configuration privileged EXEC command. Note that if the downloaded configuration is saved to the startup configuration, the feature is not triggered during subsequent system restarts.
Configuring DHCP-Based Autoconfiguration
These sections contain this configuration information:
- DHCP Server Configuration Guidelines
- Configuring the TFTP Server
- Configuring the DNS
- Configuring the Relay Device
- Obtaining Configuration Files
- Example Configuration

Note![]() If your DHCP server is a Cisco device, for additional information about configuring DHCP see the “Configuring DHCP” section of the “IP Addressing and Services” section of the Cisco IOS IP Configuration Guide, Release 12.2 at this URL:
If your DHCP server is a Cisco device, for additional information about configuring DHCP see the “Configuring DHCP” section of the “IP Addressing and Services” section of the Cisco IOS IP Configuration Guide, Release 12.2 at this URL:
http://www.cisco.com/en/US/docs/ios/12_2/ip/configuration/guide/1cfdhcp.html
DHCP Server Configuration Guidelines
Follow these guidelines if you are configuring a device as a DHCP server:
- You should configure the DHCP server with reserved leases that are bound to each switch by the switch hardware address.
- If you want the switch to receive IP address information, you must configure the DHCP server with these lease options:
–![]() IP address of the client (required)
IP address of the client (required)
–![]() Subnet mask of the client (required)
Subnet mask of the client (required)
–![]() DNS server IP address (optional)
DNS server IP address (optional)
–![]() Router IP address (default gateway address to be used by the switch) (required)
Router IP address (default gateway address to be used by the switch) (required)
- If you want the switch to receive the configuration file from a TFTP server, you must configure the DHCP server with these lease options:
–![]() Boot filename (the name of the configuration file that the client needs) (recommended)
Boot filename (the name of the configuration file that the client needs) (recommended)
- Depending on the settings of the DHCP server, the switch can receive IP address information, the configuration file, or both.
- If you do not configure the DHCP server with the lease options described previously, it replies to client requests with only those parameters that are configured. If the IP address and the subnet mask are not in the reply, the switch is not configured. If the router IP address or the TFTP server name are not found, the switch might send broadcast, instead of unicast, TFTP requests. Unavailability of other lease options does not affect autoconfiguration.
- The switch can act as a DHCP server. By default, the Cisco IOS DHCP server and relay agent features are enabled on your switch but are not configured. These features are not operational. If your DHCP server is a Cisco device, for additional information about configuring DHCP, see the “Configuring DHCP” section of the “IP Addressing and Services” section of the Cisco IOS IP Configuration Guide.
Configuring the TFTP Server
Based on the DHCP server configuration, the switch attempts to download one or more configuration files from the TFTP server. If you configured the DHCP server to respond to the switch with all the options required for IP connectivity to the TFTP server, and if you configured the DHCP server with a TFTP server name, address, and configuration filename, the switch attempts to download the specified configuration file from the specified TFTP server.
If you did not specify the configuration filename, the TFTP server, or if the configuration file could not be downloaded, the switch attempts to download a configuration file by using various combinations of filenames and TFTP server addresses. The files include the specified configuration filename (if any) and these files: network-config, cisconet.cfg, hostname.config, or hostname.cfg, where hostname is the switch’s current hostname. The TFTP server addresses used include the specified TFTP server address (if any) and the broadcast address (255.255.255.255).
For the switch to successfully download a configuration file, the TFTP server must contain one or more configuration files in its base directory. The files can include these files:
- The configuration file named in the DHCP reply (the actual switch configuration file).
- The network-confg or the cisconet.cfg file (known as the default configuration files).
- The router-confg or the ciscortr.cfg file (These files contain commands common to all switches. Normally, if the DHCP and TFTP servers are properly configured, these files are not accessed.)
If you specify the TFTP server name in the DHCP server-lease database, you must also configure the TFTP server name-to-IP-address mapping in the DNS-server database.
If the TFTP server to be used is on a different LAN from the switch, or if it is to be accessed by the switch through the broadcast address (which occurs if the DHCP server response does not contain all the required information described previously), a relay must be configured to forward the TFTP packets to the TFTP server. For more information, see the “Configuring the Relay Device” section. The preferred solution is to configure the DHCP server with all the required information.
Configuring the DNS
The DHCP server uses the DNS server to resolve the TFTP server name to an IP address. You must configure the TFTP server name-to-IP address map on the DNS server. The TFTP server contains the configuration files for the switch.
You can configure the IP addresses of the DNS servers in the lease database of the DHCP server from where the DHCP replies will retrieve them. You can enter up to two DNS server IP addresses in the lease database.
The DNS server can be on the same or on a different LAN as the switch. If it is on a different LAN, the switch must be able to access it through a router.
Configuring the Relay Device
You must configure a relay device, also referred to as a relay agent, when a switch sends broadcast packets that require a response from a host on a different LAN. Examples of broadcast packets that the switch might send are DHCP, DNS, and in some cases, TFTP packets. You must configure this relay device to forward received broadcast packets on an interface to the destination host.
If the relay device is a Cisco router, enable IP routing (ip routing global configuration command), and configure helper addresses by using the ip helper-address interface configuration command.
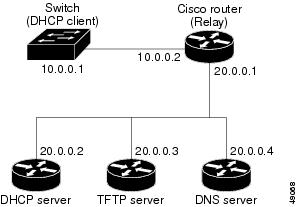
For example, in Figure 3-2, configure the router interfaces as follows:
router(config-if)# ip helper-address 20.0.0.2
router(config-if)# ip helper-address 20.0.0.3
router(config-if)# ip helper-address 20.0.0.4
router(config-if)# ip helper-address 10.0.0.1

Note![]() If the switch is acting as the relay device, configure the interface as a routed port. For more information, see the “Routed Ports” section and the “Configuring Layer 3 Interfaces” section.
If the switch is acting as the relay device, configure the interface as a routed port. For more information, see the “Routed Ports” section and the “Configuring Layer 3 Interfaces” section.
Figure 3-2 Relay Device Used in Autoconfiguration
Obtaining Configuration Files
Depending on the availability of the IP address and the configuration filename in the DHCP reserved lease, the switch obtains its configuration information in these ways:
- The IP address and the configuration filename is reserved for the switch and provided in the DHCP reply (one-file read method).
The switch receives its IP address, subnet mask, TFTP server address, and the configuration filename from the DHCP server. The switch sends a unicast message to the TFTP server to retrieve the named configuration file from the base directory of the server and upon receipt, it completes its boot up process.
- The IP address and the configuration filename is reserved for the switch, but the TFTP server address is not provided in the DHCP reply (one-file read method).
The switch receives its IP address, subnet mask, and the configuration filename from the DHCP server. The switch sends a broadcast message to a TFTP server to retrieve the named configuration file from the base directory of the server, and upon receipt, it completes its boot up process.
- Only the IP address is reserved for the switch and provided in the DHCP reply. The configuration filename is not provided (two-file read method).
The switch receives its IP address, subnet mask, and the TFTP server address from the DHCP server. The switch sends a unicast message to the TFTP server to retrieve the network-confg or cisconet.cfg default configuration file. (If the network-confg file cannot be read, the switch reads the cisconet.cfg file.)
The default configuration file contains the hostnames-to-IP-address mapping for the switch. The switch fills its host table with the information in the file and obtains its hostname. If the hostname is not found in the file, the switch uses the hostname in the DHCP reply. If the hostname is not specified in the DHCP reply, the switch uses the default Switch as its hostname.
After obtaining its hostname from the default configuration file or the DHCP reply, the switch reads the configuration file that has the same name as its hostname ( hostname -confg or hostname.cfg, depending on whether network-confg or cisconet.cfg was read earlier) from the TFTP server. If the cisconet.cfg file is read, the filename of the host is truncated to eight characters.
If the switch cannot read the network-confg, cisconet.cfg, or the hostname file, it reads the router-confg file. If the switch cannot read the router-confg file, it reads the ciscortr.cfg file.

Note![]() The switch broadcasts TFTP server requests if the TFTP server is not obtained from the DHCP replies, if all attempts to read the configuration file through unicast transmissions fail, or if the TFTP server name cannot be resolved to an IP address.
The switch broadcasts TFTP server requests if the TFTP server is not obtained from the DHCP replies, if all attempts to read the configuration file through unicast transmissions fail, or if the TFTP server name cannot be resolved to an IP address.
Example Configuration
Figure 3-3 shows a sample network for retrieving IP information by using DHCP-based autoconfiguration.
Figure 3-3 DHCP-Based Autoconfiguration Network Example
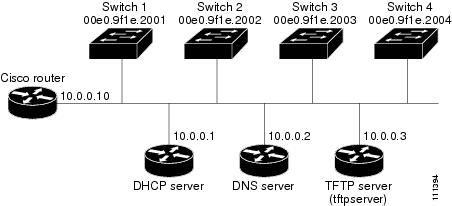
Table 3-2 shows the configuration of the reserved leases on the DHCP server.
|
|
|
|
|
|
|---|---|---|---|---|
The DNS server maps the TFTP server name tftpserver to IP address 10.0.0.3.
TFTP Server Configuration (on UNIX)
The TFTP server base directory is set to /tftpserver/work/. This directory contains the network-confg file used in the two-file read method. This file contains the hostname to be assigned to the switch based on its IP address. The base directory also contains a configuration file for each switch ( switcha-confg, switchb-confg, and so forth) as shown in this display:
No configuration file is present on Switch A through Switch D.
In Figure 3-3, Switch A reads its configuration file as follows:
- It obtains its IP address 10.0.0.21 from the DHCP server.
- If no configuration filename is given in the DHCP server reply, Switch A reads the network-confg file from the base directory of the TFTP server.
- It adds the contents of the network-confg file to its host table.
- It reads its host table by indexing its IP address 10.0.0.21 to its hostname (switcha).
- It reads the configuration file that corresponds to its hostname; for example, it reads switch1-confg from the TFTP server.
Switches B through D retrieve their configuration files and IP addresses in the same way.
Configuring the DHCP Auto Configuration and Image Update Features
Using DHCP to download a new image and a new configuration to a switch requires that you configure at least two switches: One switch acts as a DHCP and TFTP server. The client switch is configured to download either a new configuration file or a new configuration file and a new image file.
Configuring DHCP Autoconfiguration (Only Configuration File)
Beginning in privileged EXEC mode, follow these steps to configure DHCP autoconfiguration of the TFTP and DHCP settings on a new switch to download a new configuration file.
This example shows how to configure a switch as a DHCP server so that it will download a configuration file:
Configuring DHCP Auto-Image Update (Configuration File and Image)
Beginning in privileged EXEC mode, follow these steps to configure DHCP autoconfiguration to configure TFTP and DHCP settings on a new switch to download a new image and a new configuration file.

Note![]() Before following the steps in this table, you must create a text file (for example, autoinstall_dhcp) that will be uploaded to the switch. In the text file, put the name of the image that you want to download (for example, 3750x-ipservices-mz.122-53.3.SE2.tar). This image must be a tar and not a bin file.
Before following the steps in this table, you must create a text file (for example, autoinstall_dhcp) that will be uploaded to the switch. In the text file, put the name of the image that you want to download (for example, 3750x-ipservices-mz.122-53.3.SE2.tar). This image must be a tar and not a bin file.
This example shows how to configure a switch as a DHCP server so it downloads a configuration file:
Configuring the Client
Beginning in privileged EXEC mode, follow these steps to configure a switch to download a configuration file and new image from a DHCP server:
This example uses a Layer 3 SVI interface on VLAN 99 to enable DHCP-based autoconfiguration with a saved configuration:

Note![]() You should only configure and enable the Layer 3 interface. Do not assign an IP address or DHCP-based autoconfiguration with a saved configuration.
You should only configure and enable the Layer 3 interface. Do not assign an IP address or DHCP-based autoconfiguration with a saved configuration.
Manually Assigning IP Information
Beginning in privileged EXEC mode, follow these steps to manually assign IP information to multiple switched virtual interfaces (SVIs):

Note![]() If the switch is running the IP services feature set, you can also manually assign IP information to a port if you first put the port into Layer 3 mode by using the no switchport interface configuration command.
If the switch is running the IP services feature set, you can also manually assign IP information to a port if you first put the port into Layer 3 mode by using the no switchport interface configuration command.
To remove the switch IP address, use the no ip address interface configuration command. If you are removing the address through a Telnet session, your connection to the switch will be lost. To remove the default gateway address, use the no ip default-gateway global configuration command.
For information on setting the switch system name, protecting access to privileged EXEC commands, and setting time and calendar services, see Chapter7, “Administering the Switch”
Checking and Saving the Running Configuration
You can check the configuration settings you entered or changes you made by entering this privileged EXEC command:
To store the configuration or changes you have made to your startup configuration in flash memory, enter this privileged EXEC command:
This command saves the configuration settings that you made. If you fail to do this, your configuration will be lost the next time you reload the system. To display information stored in the NVRAM section of flash memory, use the show startup-config or more startup-config privileged EXEC command.
For more information about alternative locations from which to copy the configuration file, see Appendix B, “Working with the Cisco IOS File System, Configuration Files, and Software Images.”
Modifying the Startup Configuration
These sections describe how to modify the switch startup configuration:
- Default Boot Configuration
- Automatically Downloading a Configuration File
- Booting Manually
- Booting a Specific Software Image
- Controlling Environment Variables
See also Appendix B, “Working with the Cisco IOS File System, Configuration Files, and Software Images,” for information about switch configuration files. See the “Switch Stack Configuration Files” section for information about switch stack configuration files.
Default Boot Configuration
Table 3-3 shows the default boot configuration.
Automatically Downloading a Configuration File
You can automatically download a configuration file to your switch by using the DHCP-based autoconfiguration feature. For more information, see the “Understanding DHCP-Based Autoconfiguration” section.
Specifying the Filename to Read and Write the System Configuration
By default, the Cisco IOS software uses the file config.text to read and write a nonvolatile copy of the system configuration. However, you can specify a different filename, which will be loaded during the next boot cycle.

Note![]() This command only works properly from a standalone switch.
This command only works properly from a standalone switch.
Beginning in privileged EXEC mode, follow these steps to specify a different configuration filename:
To return to the default setting, use the no boot config-file global configuration command.
Booting Manually
By default, the switch automatically boots up; however, you can configure it to manually boot up.

Note![]() This command only works properly from a standalone switch.
This command only works properly from a standalone switch.
Beginning in privileged EXEC mode, follow these steps to configure the switch to manually boot up during the next boot cycle:
To disable manual booting, use the no boot manual global configuration command.
Booting a Specific Software Image
By default, the switch attempts to automatically boot up the system using information in the BOOT environment variable. If this variable is not set, the switch attempts to load and execute the first executable image it can by performing a recursive, depth-first search throughout the flash file system. In a depth-first search of a directory, each encountered subdirectory is completely searched before continuing the search in the original directory. However, you can specify a specific image to boot up.
Beginning in privileged EXEC mode, follow these steps to configure the switch to boot up a specific image during the next boot cycle:
To return to the default setting, use the no boot system global configuration command.
Controlling Environment Variables
With a normally operating switch, you enter the boot loader mode only through a switch console connection configured for 9600 b/s. Unplug the switch power cord, and press the switch Mode button while reconnecting the power cord. You can release the Mode button a second or two after the LED above port 1 turns off. Then the boot loader switch: prompt appears.
The switch boot loader software provides support for nonvolatile environment variables, which can be used to control how the boot loader, or any other software running on the system, behaves. Boot loader environment variables are similar to environment variables that can be set on UNIX or DOS systems.
Environment variables that have values are stored in flash memory outside of the flash file system.
Each line in these files contains an environment variable name and an equal sign followed by the value of the variable. A variable has no value if it is not listed in this file; it has a value if it is listed in the file even if the value is a null string. A variable that is set to a null string (for example, “ ”) is a variable with a value. Many environment variables are predefined and have default values.
Environment variables store two kinds of data:
- Data that controls code, which does not read the Cisco IOS configuration file. For example, the name of a boot loader helper file, which extends or patches the functionality of the boot loader can be stored as an environment variable.
- Data that controls code, which is responsible for reading the Cisco IOS configuration file. For example, the name of the Cisco IOS configuration file can be stored as an environment variable.
You can change the settings of the environment variables by accessing the boot loader or by using Cisco IOS commands. Under normal circumstances, it is not necessary to alter the setting of the environment variables.

Note![]() For complete syntax and usage information for the boot loader commands and environment variables, see the command reference for this release.
For complete syntax and usage information for the boot loader commands and environment variables, see the command reference for this release.
Table 3-4 describes the function of the most common environment variables.
When the switch is connected to a PC through the Ethernet management port, you can download or upload a configuration file to the boot loader by using TFTP. Make sure the environment variables in Table 3-5 are configured.
Scheduling a Reload of the Software Image
You can schedule a reload of the software image to occur on the switch at a later time (for example, late at night or during the weekend when the switch is used less), or you can synchronize a reload network-wide (for example, to perform a software upgrade on all switches in the network).

Note![]() A scheduled reload must take place within approximately 24 days.
A scheduled reload must take place within approximately 24 days.
Configuring a Scheduled Reload
To configure your switch to reload the software image at a later time, use one of these commands in privileged EXEC mode:
This command schedules a reload of the software to take affect in the specified minutes or hours and minutes. The reload must take place within approximately 24 days. You can specify the reason for the reload in a string up to 255 characters in length.
To reload a specific switch in a switch stack, use the reload slot stack-member-number privileged EXEC command.
This command schedules a reload of the software to take place at the specified time (using a 24-hour clock). If you specify the month and day, the reload is scheduled to take place at the specified time and date. If you do not specify the month and day, the reload takes place at the specified time on the current day (if the specified time is later than the current time) or on the next day (if the specified time is earlier than the current time). Specifying 00:00 schedules the reload for midnight.

Note![]() Use the at keyword only if the switch system clock has been set (through Network Time Protocol (NTP), the hardware calendar, or manually). The time is relative to the configured time zone on the switch. To schedule reloads across several switches to occur simultaneously, the time on each switch must be synchronized with NTP.
Use the at keyword only if the switch system clock has been set (through Network Time Protocol (NTP), the hardware calendar, or manually). The time is relative to the configured time zone on the switch. To schedule reloads across several switches to occur simultaneously, the time on each switch must be synchronized with NTP.
The reload command halts the system. If the system is not set to manually bootup, it reboots itself. Use the reload command after you save the switch configuration information to the startup configuration (copy running-config startup-config).
If your switch is configured for manual booting, do not reload it from a virtual terminal. This restriction prevents the switch from entering the boot loader mode and thereby taking it from the remote user’s control.
If you modify your configuration file, the switch prompts you to save the configuration before reloading. During the save operation, the system requests whether you want to proceed with the save if the CONFIG_FILE environment variable points to a startup configuration file that no longer exists. If you proceed in this situation, the system enters setup mode upon reload.
This example shows how to reload the software on the switch on the current day at 7:30 p.m:
This example shows how to reload the software on the switch at a future time:
To cancel a previously scheduled reload, use the reload cancel privileged EXEC command.
Displaying Scheduled Reload Information
To display information about a previously scheduled reload or to find out if a reload has been scheduled on the switch, use the show reload privileged EXEC command.
It displays reload information including the time the reload is scheduled to occur and the reason for the reload (if it was specified when the reload was scheduled).
 Feedback
Feedback