- Preface
- Using the Command-Line Interface
-
- Managing Switch Stacks
- Security Features Overview
- Preventing Unauthorized Access
- Controlling Switch Access with Passwords and Privilege Levels
- Configuring TACACS+
- Configuring RADIUS
- Configuring Kerberos
- Configuring Local Authentication and Authorization
- Configuring Secure Shell (SSH)
- Configuring Secure Socket Layer HTTP
- Configuring IPv4 ACLs
- Configuring IPv6 ACLs
- Configuring DHCP
- Configuring IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring Port-Based Traffic Control
- Configuring IPv6 First Hop Security
- Configuring Cisco TrustSec
- Configuring FIPS
- XML Schema for SNMP Endpoint Proxy
- Important Notice
- Index
Cisco 2960-X Switch Series Configuration Guide, Cisco IOS Release 15.0(2)EX
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- June 16, 2016
Chapter: Configuring Dynamic ARP Inspection
- Finding Feature Information
- Restrictions for Dynamic ARP Inspection
- Understanding Dynamic ARP Inspection
- Default Dynamic ARP Inspection Configuration
- Relative Priority of ARP ACLs and DHCP Snooping Entries
- Configuring ARP ACLs for Non-DHCP Environments
- Configuring Dynamic ARP Inspection in DHCP Environments
- Limiting the Rate of Incoming ARP Packets
- Performing Dynamic ARP Inspection Validation Checks
- Monitoring DAI
- Verifying the DAI Configuration
- Additional References
Configuring Dynamic ARP Inspection
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Restrictions for Dynamic ARP Inspection
-
Dynamic ARP inspection is an ingress security feature; it does not perform any egress checking.
-
Dynamic ARP inspection is not effective for hosts connected to switches that do not support dynamic ARP inspection or that do not have this feature enabled. Because man-in-the-middle attacks are limited to a single Layer 2 broadcast domain, separate the domain with dynamic ARP inspection checks from the one with no checking. This action secures the ARP caches of hosts in the domain enabled for dynamic ARP inspection.
-
Dynamic ARP inspection depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically assigned IP addresses.
When DHCP snooping is disabled or in non-DHCP environments, use ARP ACLs to permit or to deny packets.
-
Dynamic ARP inspection is supported on access ports, trunk ports, and EtherChannel ports.

Note
Do not enable Dynamic ARP inspection on RSPAN VLANs. If Dynamic ARP inspection is enabled on RSPAN VLANs, Dynamic ARP inspection packets might not reach the RSPAN destination port. -
A physical port can join an EtherChannel port channel only when the trust state of the physical port and the channel port match. Otherwise, the physical port remains suspended in the port channel. A port channel inherits its trust state from the first physical port that joins the channel. Consequently, the trust state of the first physical port need not match the trust state of the channel.
Conversely, when you change the trust state on the port channel, the switch configures a new trust state on all the physical ports that comprise the channel.
-
The rate limit is calculated separately on each switch in a switch stack. For a cross-stack EtherChannel, this means that the actual rate limit might be higher than the configured value. For example, if you set the rate limit to 30 pps on an EtherChannel that has one port on switch 1 and one port on switch 2, each port can receive packets at 29 pps without causing the EtherChannel to become error-disabled.
-
The operating rate for the port channel is cumulative across all the physical ports within the channel. For example, if you configure the port channel with an ARP rate-limit of 400 pps, all the interfaces combined on the channel receive an aggregate 400 pps. The rate of incoming ARP packets on EtherChannel ports is equal to the sum of the incoming rate of packets from all the channel members. Configure the rate limit for EtherChannel ports only after examining the rate of incoming ARP packets on the channel-port members.
The rate of incoming packets on a physical port is checked against the port-channel configuration rather than the physical-ports configuration. The rate-limit configuration on a port channel is independent of the configuration on its physical ports.
If the EtherChannel receives more ARP packets than the configured rate, the channel (including all physical ports) is placed in the error-disabled state.
-
Make sure to limit the rate of ARP packets on incoming trunk ports. Configure trunk ports with higher rates to reflect their aggregation and to handle packets across multiple dynamic ARP inspection-enabled VLANs. You also can use the ip arp inspection limit none interface configuration command to make the rate unlimited. A high rate-limit on one VLAN can cause a denial-of-service attack to other VLANs when the software places the port in the error-disabled state.
-
When you enable dynamic ARP inspection on the switch, policers that were configured to police ARP traffic are no longer effective. The result is that all ARP traffic is sent to the CPU.
-
In the presence of vlan-bridging & IP device tracking, the cross-stack ARP packet forwarding will not work.
Understanding Dynamic ARP Inspection
ARP provides IP communication within a Layer 2 broadcast domain by mapping an IP address to a MAC address. For example, Host B wants to send information to Host A but does not have the MAC address of Host A in its ARP cache. Host B generates a broadcast message for all hosts within the broadcast domain to obtain the MAC address associated with the IP address of Host A. All hosts within the broadcast domain receive the ARP request, and Host A responds with its MAC address. However,because ARP allows a gratuitous reply from a host even if an ARP request was not received, an ARP spoofing attack and the poisoning of ARP caches can occur. After the attack, all traffic from the device under attack flows through the attacker’s computer and then to the router, switch, or host.
A malicious user can attack hosts, switches, and routers connected to your Layer 2 network by poisoning the ARP caches of systems connected to the subnet and by intercepting traffic intended for other hosts on the subnet. Figure 26-1 shows an example of ARP cache poisoning.
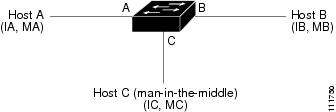
Hosts A, B, and C are connected to the switch on interfaces A, B and C, all of which are on the same subnet. Their IP and MAC addresses are shown in parentheses; for example, Host A uses IP address IA and MAC address MA. When Host A needs to communicate to Host B at the IP layer, it broadcasts an ARP request for the MAC address associated with IP address IB. When the switch and Host B receive the ARP request, they populate their ARP caches with an ARP binding for a host with the IP address IA and a MAC address MA; for example, IP address IA is bound to MAC address MA. When Host B responds, the switch and Host A populate their ARP caches with a binding for a host with the IP address IB and the MAC address MB.
Host C can poison the ARP caches of the switch, Host A, and Host B by broadcasting forged ARP responses with bindings for a host with an IP address of IA (or IB) and a MAC address of MC. Hosts with poisoned ARP caches use the MAC address MC as the destination MAC address for traffic intended for IA or IB. This means that Host C intercepts that traffic. Because Host C knows the true MAC addresses associated with IA and IB, it can forward the intercepted traffic to those hosts by using the correct MAC address as the destination. Host C has inserted itself into the traffic stream from Host A to Host B, the classic man-in-the middleattack.
Dynamic ARP inspection is a security feature that validates ARP packets in a network. It intercepts, logs,and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from certain man-in-the-middle attacks.
Dynamic ARP inspection ensures that only valid ARP requests and responses are relayed. The switch performs these activities:
- Intercepts all ARP requests and responses on untrusted ports
- Verifies that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination
Drops invalid ARP packets
Dynamic ARP inspection determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On untrusted interfaces, the switch forwards the packet only if it is valid.
You enable dynamic ARP inspection on a per-VLAN basis by using the ip arp inspection vlan vlan-range global configuration command.
In non-DHCP environments, dynamic ARP inspection can validate ARP packets against user-configured ARP access control lists (ACLs) for hosts with statically configured IP addresses. You define an ARP ACL by using the arp access-list acl-name global configuration command.
You can configure dynamic ARP inspection to drop ARP packets when the IP addresses in the packets are invalid or when the MAC addresses in the body of the ARP packets do not match the addresses specified in the Ethernet header. Use the ip arp inspection validate {[src-mac] [dst-mac] [ip]} global configuration command.
- Interface Trust States and Network Security
- Rate Limiting of ARP Packets
- Relative Priority of ARP ACLs and DHCP Snooping Entries
- Logging of Dropped Packets
Interface Trust States and Network Security
Dynamic ARP inspection associates a trust state with each interface on the switch. Packets arriving on trusted interfaces bypass all dynamic ARP inspection validation checks, and those arriving on untrusted interfaces undergo the dynamic ARP inspection validation process.
In a typical network configuration, you configure all switch ports connected to host ports as untrusted and configure all switch ports connected to switches as trusted. With this configuration, all ARP packets entering the network from a given switch bypass the security check. No other validation is needed at any other place in the VLAN or in the network. You configure the trust setting by using theip arp inspection trust interface configuration command.
 Caution | Use the trust state configuration carefully. Configuring interfaces as untrusted when they should betrusted can result in a loss of connectivity. |
In the following figure, assume that both Switch A and Switch B are running dynamic ARP inspection on the VLAN that includes Host 1 and Host 2. If Host 1 and Host 2 acquire their IP addresses from the DHCP server connected to Switch A, only Switch A binds the IP-to-MAC address of Host 1. Therefore, if the interface between Switch A and Switch B is untrusted, the ARP packets from Host 1 are dropped by Switch B. Connectivity between Host 1 and Host 2 is lost.
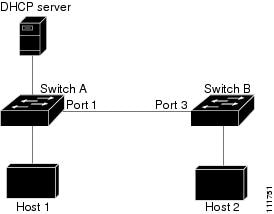
Configuring interfaces to be trusted when they are actually untrusted leaves a security hole in the network. If Switch A is not running dynamic ARP inspection, Host 1 can easily poison the ARP cache of Switch B (and Host 2, if the link between the switches is configured as trusted). This condition can occur even though Switch B is running dynamic ARP inspection.
Dynamic ARP inspection ensures that hosts (on untrusted interfaces) connected to a switch running dynamic ARP inspection do not poison the ARP caches of other hosts in the network. However, dynamic ARP inspection does not prevent hosts in other portions of the network from poisoning the caches of the hosts that are connected to a switch running dynamic ARP inspection.
In cases in which some switches in a VLAN run dynamic ARP inspection and other switches do not, configure the interfaces connecting such switches as untrusted. However, to validate the bindings of packets from nondynamic ARP inspection switches, configure the switch running dynamic ARP inspection with ARP ACLs. When you cannot determine such bindings, at Layer 3, isolate switches running dynamic ARP inspection from switches not running dynamic ARP inspection switches.
 Note | Depending on the setup of the DHCP server and the network, it might not be possible to validate a given ARP packet on all switches in the VLAN. |
Rate Limiting of ARP Packets
The switch CPU performs dynamic ARP inspection validation checks; therefore, the number of incoming ARP packets is rate-limited to prevent a denial-of-service attack. By default, the rate for untrusted interfaces is 15 packets per second (pps). Trusted interfaces are not rate-limited. You can change this setting by using the ip arp inspection limit interface configuration command.
When the rate of incoming ARP packets exceeds the configured limit, the switch places the port in the error-disabled state. The port remains in that state until you intervene. You can use the errdisable recovery global configuration command to enable error disable recovery so that ports automatically emerge from this state after a specified timeout period.
 Note | The rate limit for an EtherChannel is applied separately to each switch in a stack. For example, if a limit of 20 pps is configured on the EtherChannel, each switch with ports in the EtherChannel can carry up to 20 pps. If any switch exceeds the limit, the entire EtherChannel is placed into the error-disabled state. |
Relative Priority of ARP ACLs and DHCP Snooping Entries
Dynamic ARP inspection uses the DHCP snooping binding database for the list of valid IP-to-MAC address bindings.
ARP ACLs take precedence over entries in the DHCP snooping binding database. The switch uses ACLs only if you configure them by using the ip arp inspection filter vlan global configuration command. The switch first compares ARP packets to user-configured ARP ACLs. If the ARP ACL denies the ARP packet, the switch also denies the packet even if a valid binding exists in the database populated by DHCP snooping.
Logging of Dropped Packets
When the switch drops a packet, it places an entry in the log buffer and then generates system messages on a rate-controlled basis. After the message is generated, the switch clears the entry from the log buffer. Each log entry contains flow information, such as the receiving VLAN, the port number, the source and destination IP addresses, and the source and destination MAC addresses.
You use the ip arp inspection log-buffer global configuration command to configure the number of entries in the buffer and the number of entries needed in the specified interval to generate system messages. You specify the type of packets that are logged by using the ip arp inspection vlan logging global configuration command.
Default Dynamic ARP Inspection Configuration
| Feature | Default Settings |
|---|---|
| Dynamic ARP inspection | Disabled on all VLANs. |
| Interface trust state | All interfaces are untrusted. |
| Rate limit of incoming ARP packets | The rate is 15 pps on untrusted interfaces, assuming that the
network is a switched network with a host connecting to as many as 15 new hosts
per second.
The rate is unlimited on all trusted interfaces. The burst interval is 1 second. |
| ARP ACLs for non-DHCP environments | No ARP ACLs are defined. |
| Validation checks | No checks are performed. |
| Log buffer |
When dynamic ARP inspection is enabled, all denied or dropped ARP packets are logged. The number of entries in the log is 32. The number of system messages is limited to 5 per second. The logging-rate interval is 1 second. |
| Per-VLAN logging | All denied or dropped ARP packets are logged. |
Relative Priority of ARP ACLs and DHCP Snooping Entries
Dynamic ARP inspection uses the DHCP snooping binding database for the list of valid IP-to-MAC address bindings.
ARP ACLs take precedence over entries in the DHCP snooping binding database. The switch uses ACLs only if you configure them by using the ip arp inspection filter vlan global configuration command. The switch first compares ARP packets to user-configured ARP ACLs. If the ARP ACL denies the ARP packet, the switch also denies the packet even if a valid binding exists in the database populated by DHCP snooping.
Configuring ARP ACLs for Non-DHCP Environments
This procedure shows how to configure dynamic ARP inspection when Switch B shown in Figure 2 does not support dynamic ARP inspection or DHCP snooping.
If you configure port 1 on Switch A as trusted, a security hole is created because both Switch A and Host 1 could be attacked by either Switch B or Host 2. To prevent this possibility, you must configure port 1 on Switch A as untrusted. To permit ARP packets from Host 2, you must set up an ARP ACL and apply it to VLAN 1. If the IP address of Host 2 is not static (it is impossible to apply the ACL configuration on Switch A) you must separate Switch A from Switch B at Layer 3 and use a router to route packets between them.
Follow these steps to configure an ARP ACL on Switch A. This procedure is required in non-DHCP environments.
1.
enable
3.
arp access-list
acl-name
4.
permit ip host
sender-ip
mac
host
sender-mac
5.
exit
6.
ip arp inspection filter
arp-acl-name vlan
vlan-range [static]
7.
interface
interface-id
8.
no ip arp inspection trust
9.
end
10.
Use the following show
commands:
12.
copy running-config
startup-config
DETAILED STEPS
Configuring Dynamic ARP Inspection in DHCP Environments
 Note | Dynamic ARP inspection depends on the entries in the DHCP snooping binding database to verify IP-to-MAC address bindings in incoming ARP requests and ARP responses. Make sure to enable DHCP snooping to permit ARP packets that have dynamically assigned IP addresses. |
Follow these steps to configure dynamic ARP inspection. You must perform this procedure on both switches. This procedure is required.
1.
enable
2.
show cdp
neighbors
4.
ip arp inspection vlan
vlan-range
5.
Interfaceinterface-id
6.
ip arp inspection trust
7.
end
8.
show ip arp inspection interfaces
9.
show ip arp inspection vlan
vlan-range
10.
show ip dhcp snooping binding
11.
show ip arp inspection statistics vlan
vlan-range
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 |
show cdp
neighbors
Example: Switch(config-if)#show cdp neighbors
|
Verify the connection between the switches. |
| Step 3 | configure
terminal
Example: Switch# configure terminal | |
| Step 4 | ip arp inspection vlan
vlan-range
Example: Switch(config)# ip arp inspection vlan 1
|
Enable dynamic ARP inspection on a per-VLAN basis. By default, dynamic ARP inspection is disabled on all VLANs. For vlan-range, specify a single VLAN identified by VLAN ID number, a range of VLANs separated by a hyphen, or a series of VLANs separated by a comma. The range is 1 to 4094. Specify the same VLAN ID for both switches. |
| Step 5 | Interfaceinterface-id
Example: Switch(config)# interface gigabitethernet1/0/1
|
Specifies the interface connected to the other switch, and enter interface configuration mode. |
| Step 6 | ip arp inspection trust
Example: Switch(config-if)#ip arp inspection trust
|
Configures the connection between the switches as trusted. By default, all interfaces are untrusted. The switch does not check ARP packets that it receives from the other switch on the trusted interface. It simply forwards the packets. For untrusted interfaces, the switch intercepts all ARP requests and responses. It verifies that the intercepted packets have valid IP-to-MAC address bindings before updating the local cache and before forwarding the packet to the appropriate destination. The switch drops invalid packets and logs them in the log buffer according to the logging configuration specified with the ip arp inspection vlan logging global configuration command. |
| Step 7 | end
Example: Switch(config-if)#end
|
Returns to privileged EXEC mode. |
| Step 8 | show ip arp inspection interfaces
Example: |
Verifies the dynamic ARP inspection configuration on interfaces. |
| Step 9 | show ip arp inspection vlan
vlan-range
Example: Switch(config-if)#show ip arp inspection vlan 1
|
Verifies the dynamic ARP inspection configuration on VLAN. |
| Step 10 | show ip dhcp snooping binding
Example: Switch(config-if)#show ip dhcp snooping binding
|
Verifies the DHCP bindings. |
| Step 11 | show ip arp inspection statistics vlan
vlan-range
Example: Switch(config-if)#show ip arp inspection statistics vlan 1
|
Checks the dynamic ARP inspection statistics on VLAN. |
| Step 12 | configure
terminal
Example: Switch# configure terminal | |
| Step 13 | configure
terminal
Example: Switch# configure terminal |
Limiting the Rate of Incoming ARP Packets
The switch CPU performs dynamic ARP inspection validation checks; therefore, the number of incoming ARP packets is rate-limited to prevent a denial- of-service attack.
 Note | Unless you configure a rate limit on an interface, changing the trust state of the interface also changes its rate limit to the default value for that trust state. After you configure the rate limit, the interface retains the rate limit even when its trust state is changed. If you enter the no ip arp inspection limit interface configuration command, the interface reverts to its default rate limit. |
Follow these steps to limit the rate of incoming ARP packets. This procedure is optional.
1.
enable
3.
interface
interface-id
4.
ip arp inspection limit {rate pps [burst interval seconds] |
none}
5.
exit
6.
Use the
following commands:
7.
exit
8.
Use the following show
commands:
10.
copy running-config
startup-config
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | interface
interface-id
|
Specifies the interface to be rate-limited, and enter interface configuration mode. |
| Step 4 | ip arp inspection limit {rate pps [burst interval seconds] |
none}
|
Limits the rate of incoming ARP requests and responses on the interface. The default rate is 15 pps on untrusted interfaces and unlimited on trusted interfaces. The burst interval is 1 second. The keywords have these meanings:
|
| Step 5 | exit
|
Returns to global configuration mode. |
| Step 6 | Use the following commands: |
(Optional) Enables error recovery from the dynamic ARP inspection error-disabled state, and configure the dynamic ARP inspection recover mechanism variables. By default, recovery is disabled, and the recovery interval is 300 seconds. For interval interval, specify the time in seconds to recover from the error-disabled state. The range is 30 to 86400. |
| Step 7 | exit
|
Returns to privileged EXEC mode. |
| Step 8 | Use the following show commands: |
Verifies your settings. |
| Step 9 | show running-config
Example: Switch# show running-config | |
| Step 10 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Performing Dynamic ARP Inspection Validation Checks
Dynamic ARP inspection intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. You can configure the switch to perform additional checks on the destination MAC address, the sender and target IP addresses, and the source MAC address.
Follow these steps to perform specific checks on incoming ARP packets. This procedure is optional.
1.
enable
3.
ip arp inspection validate {[src-mac] [dst-mac] [ip]}
4.
exit
5.
show ip arp inspection vlan
vlan-range
7.
copy running-config
startup-config
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip arp inspection validate {[src-mac] [dst-mac] [ip]}
|
Performs a specific check on incoming ARP packets. By default, no checks are performed. The keywords have these meanings:
You must specify at least one of the keywords. Each command overrides the configuration of the previous command; that is, if a command enables src and dst mac validations, and a second command enables IP validation only, the src and dst mac validations are disabled as a result of the second command. |
| Step 4 | exit
|
Returns to privileged EXEC mode. |
| Step 5 | show ip arp inspection vlan
vlan-range
|
Verifies your settings. |
| Step 6 | show running-config
Example: Switch# show running-config | |
| Step 7 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Monitoring DAI
To monitor DAI, use the following commands:
| Command | Description |
|---|---|
| clear ip arp inspection statistics | Clears dynamic ARP inspection statistics. |
| show ip arp inspection statistics [vlan vlan-range] | Displays statistics for forwarded, dropped, MAC validation failure, IP validation failure, ACL permitted and denied, and DHCP permitted and denied packets for the specified VLAN. If no VLANs are specified or if a range is specified, displays information only for VLANs with dynamic ARP inspection enabled (active). |
| clear ip arp inspection log | Clears the dynamic ARP inspection log buffer. |
| show ip arp inspection log | Displays the configuration and contents of the dynamic ARP inspection log buffer. |
For the show ip arp inspection statistics command, the switch increments the number of forwarded packets for each ARP request and response packet on a trusted dynamic ARP inspection port. The switch increments the number of ACL or DHCP permitted packets for each packet that is denied by source MAC, destination MAC, or IP validation checks, and the switch increments the appropriate.
Verifying the DAI Configuration
To display and verify the DAI configuration, use the following commands:
| Command | Description |
|---|---|
| show arp access-list [acl-name] | Displays detailed information about ARP ACLs. |
| show ip arp inspection interfaces [interface-id] | Displays the trust state and the rate limit of ARP packets for the specified interface or all interfaces. |
| show ip arp inspection vlan vlan-range | Displays the configuration and the operating state of dynamic ARP inspection for the specified VLAN. If no VLANs are specified or if a range is specified, displays information only for VLANs with dynamic ARP inspection enabled (active). |
Additional References
Error Message Decoder
| Description | Link |
|---|---|
|
To help you research and resolve system error messages in this release, use the Error Message Decoder tool. |
https://www.cisco.com/cgi-bin/Support/Errordecoder/index.cgi |
MIBs
| MIB | MIBs Link |
|---|---|
|
All supported MIBs for this release. |
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Technical Assistance
| Description | Link |
|---|---|
|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
 Feedback
Feedback