- Preface
- Using the Command-Line Interface
-
- Managing Switch Stacks
- Security Features Overview
- Preventing Unauthorized Access
- Controlling Switch Access with Passwords and Privilege Levels
- Configuring TACACS+
- Configuring RADIUS
- Configuring Kerberos
- Configuring Local Authentication and Authorization
- Configuring Secure Shell (SSH)
- Configuring Secure Socket Layer HTTP
- Configuring IPv4 ACLs
- Configuring IPv6 ACLs
- Configuring DHCP
- Configuring IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring Port-Based Traffic Control
- Configuring IPv6 First Hop Security
- Configuring Cisco TrustSec
- Configuring FIPS
- XML Schema for SNMP Endpoint Proxy
- Important Notice
- Index
Cisco 2960-X Switch Series Configuration Guide, Cisco IOS Release 15.0(2)EX
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- June 16, 2016
Chapter: Administering the System
- Finding Feature Information
- Information About Administering the Switch
- How to Administer the Switch
- Setting Up DNS
- Configuring a Message-of-the-Day Login Banner
- Configuring a Login Banner
- Managing the MAC Address Table
- Example: Setting the System Clock
- Examples: Configuring Summer Time
- Example: Configuring a MOTD Banner
- Example: Configuring a Login Banner
- Example: Configuring MAC Address Change Notification Traps
- Example: Configuring MAC Threshold Notification Traps
- Example: Adding the Static Address to the MAC Address Table
- Example: Configuring Unicast MAC Address Filtering
Administering the System
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Information About Administering the Switch
- System Time and Date Management
- System Clock
- Real Time Clock
- Network Time Protocol
- System Name and Prompt
- DNS
- Login Banners
- MAC Address Table
- ARP Table Management
System Time and Date Management
You can manage the system time and date on your switch using automatic configuration methods (RTC and NTP), or manual configuration methods.
 Note | For complete syntax and usage information for the commands used in this section, see the Cisco IOS Configuration Fundamentals Command Referenceon Cisco.com. |
System Clock
The basis of the time service is the system clock. This clock runs from the moment the system starts up and keeps track of the date and time.
The system clock can then be set from these sources:
The system clock can provide time to these services:
The system clock keeps track of time internally based on Coordinated Universal Time (UTC), also known as Greenwich Mean Time (GMT). You can configure information about the local time zone and summer time (daylight saving time) so that the time appears correctly for the local time zone.
The system clock keeps track of whether the time is authoritative or not (that is, whether it has been set by a time source considered to be authoritative). If it is not authoritative, the time is available only for display purposes and is not redistributed.
Real Time Clock
A real-time clock (RTC) keeps track of the current time on the switch. The switch is shipped to you with RTC set to GMT time until you reconfigure clocking parameters.
The benefits of an RTC are:
The RTC and NTP clocks are integrated on the switch. When NTP is enabled, the RTC time is periodically synchronized to the NTP clock to maintain accuracy.
Network Time Protocol
The NTP is designed to time-synchronize a network of devices. NTP runs over User Datagram Protocol (UDP), which runs over IP. NTP is documented in RFC 1305.
An NTP network usually gets its time from an authoritative time source, such as a radio clock or an atomic clock attached to a time server. NTP then distributes this time across the network. NTP is extremely efficient; no more than one packet per minute is necessary to synchronize two devices to within a millisecond of one another.
NTP uses the concept of a stratum to describe how many NTP hops away a device is from an authoritative time source. A stratum 1 time server has a radio or atomic clock directly attached, a stratum 2 time server receives its time through NTP from a stratum 1 time server, and so on. A device running NTP automatically chooses as its time source the device with the lowest stratum number with which it communicates through NTP. This strategy effectively builds a self-organizing tree of NTP speakers.
NTP avoids synchronizing to a device whose time might not be accurate by never synchronizing to a device that is not synchronized. NTP also compares the time reported by several devices and does not synchronize to a device whose time is significantly different than the others, even if its stratum is lower.
The communications between devices running NTP (known as associations) are usually statically configured; each device is given the IP address of all devices with which it should form associations. Accurate timekeeping is possible by exchanging NTP messages between each pair of devices with an association. However, in a LAN environment, NTP can be configured to use IP broadcast messages instead. This alternative reduces configuration complexity because each device can simply be configured to send or receive broadcast messages. However, in that case, information flow is one-way only.
The time kept on a device is a critical resource; you should use the security features of NTP to avoid the accidental or malicious setting of an incorrect time. Two mechanisms are available: an access list-based restriction scheme and an encrypted authentication mechanism.
Cisco’s implementation of NTP does not support stratum 1 service; it is not possible to connect to a radio or atomic clock. We recommend that the time service for your network be derived from the public NTP servers available on the IP Internet.
The Figure shows a typical network example using NTP. Switch A is the NTP master, with the Switch B, C, and D configured in NTP server mode, in server association with Switch A. Switch E is configured as an NTP peer to the upstream and downstream Switch, Switch B and Switch F, respectively.
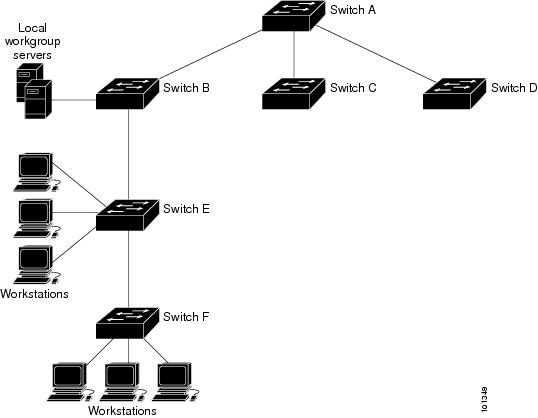
If the network is isolated from the Internet, Cisco’s implementation of NTP allows a device to act as if it is synchronized through NTP, when in fact it has learned the time by using other means. Other devices then synchronize to that device through NTP.
When multiple sources of time are available, NTP is always considered to be more authoritative. NTP time overrides the time set by any other method.
Several manufacturers include NTP software for their host systems, and a publicly available version for systems running UNIX and its various derivatives is also available. This software allows host systems to be time-synchronized as well.
NTP Stratum
NTP uses the concept of a stratum to describe how many NTP hops away a device is from an authoritative time source. A stratum 1 time server has a radio or atomic clock directly attached, a stratum 2 time server receives its time through NTP from a stratum 1 time server, and so on. A device running NTP automatically chooses as its time source the device with the lowest stratum number with which it communicates through NTP. This strategy effectively builds a self-organizing tree of NTP speakers.
NTP avoids synchronizing to a device whose time might not be accurate by never synchronizing to a device that is not synchronized. NTP also compares the time reported by several devices and does not synchronize to a device whose time is significantly different than the others, even if its stratum is lower.
NTP Associations
The communications between devices running NTP (known as associations) are usually statically configured; each device is given the IP address of all devices with which it should form associations. Accurate timekeeping is possible by exchanging NTP messages between each pair of devices with an association. However, in a LAN environment, NTP can be configured to use IP broadcast messages instead. This alternative reduces configuration complexity because each device can simply be configured to send or receive broadcast messages. However, in that case, information flow is one-way only.
NTP Security
The time kept on a device is a critical resource; you should use the security features of NTP to avoid the accidental or malicious setting of an incorrect time. Two mechanisms are available: an access list-based restriction scheme and an encrypted authentication mechanism.
NTP Implementation
Implementation of NTP does not support stratum 1 service; it is not possible to connect to a radio or atomic clock. We recommend that the time service for your network be derived from the public NTP servers available on the IP Internet.

If the network is isolated from the Internet, NTP allows a device to act as if it is synchronized through NTP, when in fact it has learned the time by using other means. Other devices then synchronize to that device through NTP.
When multiple sources of time are available, NTP is always considered to be more authoritative. NTP time overrides the time set by any other method.
Several manufacturers include NTP software for their host systems, and a publicly available version for systems running UNIX and its various derivatives is also available. This software allows host systems to be time-synchronized as well.
NTP Version 4
NTP version 4 is implemented on the switch. NTPv4 is an extension of NTP version 3. NTPv4 supports both IPv4 and IPv6 and is backward-compatible with NTPv3.
NTPv4 provides these capabilities:
-
Improved security compared to NTPv3. The NTPv4 protocol provides a security framework based on public key cryptography and standard X509 certificates.
-
Automatic calculation of the time-distribution hierarchy for a network. Using specific multicast groups, NTPv4 automatically configures the hierarchy of the servers to achieve the best time accuracy for the lowest bandwidth cost. This feature leverages site-local IPv6 multicast addresses.
For details about configuring NTPv4, see the Implementing NTPv4 in IPv6 chapter of the Cisco IOS IPv6 Configuration Guide, Release 12.4T.
System Name and Prompt
You configure the system name on the Switch to identify it. By default, the system name and prompt are Switch.
If you have not configured a system prompt, the first 20 characters of the system name are used as the system prompt. A greater-than symbol [>] is appended. The prompt is updated whenever the system name changes.
For complete syntax and usage information for the commands used in this section, see the Cisco IOS Configuration Fundamentals Command Reference, Release 12.4 and the Cisco IOS IP Command Reference, Volume 2 of 3: Routing Protocols, Release 12.4.
Stack System Name and Prompt
If you are accessing a stack member through the stack master, you must use the session stack-member-number privileged EXEC command. The stack member number range is from 1 through 8. When you use this command, the stack member number is appended to the system prompt. For example, Switch-2# is the prompt in privileged EXEC mode for stack member 2, and the system prompt for the switch stack is Switch.
Default System Name and Prompt Configuration
DNS
The DNS protocol controls the Domain Name System (DNS), a distributed database with which you can map hostnames to IP addresses. When you configure DNS on your switch, you can substitute the hostname for the IP address with all IP commands, such as ping, telnet, connect, and related Telnet support operations.
IP defines a hierarchical naming scheme that allows a device to be identified by its location or domain. Domain names are pieced together with periods (.) as the delimiting characters. For example, Cisco Systems is a commercial organization that IP identifies by a com domain name, so its domain name is cisco.com. A specific device in this domain, for example, the File Transfer Protocol (FTP) system is identified as ftp.cisco.com.
To keep track of domain names, IP has defined the concept of a domain name server, which holds a cache (or database) of names mapped to IP addresses. To map domain names to IP addresses, you must first identify the hostnames, specify the name server that is present on your network, and enable the DNS.
Default DNS Settings
Login Banners
You can configure a message-of-the-day (MOTD) and a login banner. The MOTD banner is displayed on all connected terminals at login and is useful for sending messages that affect all network users (such as impending system shutdowns).
The login banner is also displayed on all connected terminals. It appears after the MOTD banner and before the login prompts.
 Note | For complete syntax and usage information for the commands used in this section, see the Cisco IOS Configuration Fundamentals Command Reference, Release 12.4. |
Default Banner Configuration
The MOTD and login banners are not configured.
MAC Address Table
The MAC address table contains address information that the switch uses to forward traffic between ports. All MAC addresses in the address table are associated with one or more ports. The address table includes these types of addresses:
-
Dynamic address—A source MAC address that the switch learns and then ages when it is not in use.
-
Static address—A manually entered unicast address that does not age and that is not lost when the switch resets.
The address table lists the destination MAC address, the associated VLAN ID, and port number associated with the address and the type (static or dynamic).
 Note | For complete syntax and usage information for the commands used in this section, see the command reference for this release. |
MAC Address Table Creation
With multiple MAC addresses supported on all ports, you can connect any port on the switch to other network devices. The switch provides dynamic addressing by learning the source address of packets it receives on each port and adding the address and its associated port number to the address table. As devices are added or removed from the network, the switch updates the address table, adding new dynamic addresses and aging out those that are not in use.
The aging interval is globally configured. However, the switch maintains an address table for each VLAN, and STP can accelerate the aging interval on a per-VLAN basis.
The switch sends packets between any combination of ports, based on the destination address of the received packet. Using the MAC address table, the switch forwards the packet only to the port associated with the destination address. If the destination address is on the port that sent the packet, the packet is filtered and not forwarded. The switch always uses the store-and-forward method: complete packets are stored and checked for errors before transmission.
MAC Addresses and VLANs
All addresses are associated with a VLAN. An address can exist in more than one VLAN and have different destinations in each. Unicast addresses, for example, could be forwarded to port 1 in VLAN 1 and ports 9, 10, and 1 in VLAN 5.
Each VLAN maintains its own logical address table. A known address in one VLAN is unknown in another until it is learned or statically associated with a port in the other VLAN.
Default MAC Address Table Settings
ARP Table Management
To communicate with a device (over Ethernet, for example), the software first must learn the 48-bit MAC address or the local data link address of that device. The process of learning the local data link address from an IP address is called address resolution.
The Address Resolution Protocol (ARP) associates a host IP address with the corresponding media or MAC addresses and the VLAN ID. Using an IP address, ARP finds the associated MAC address. When a MAC address is found, the IP-MAC address association is stored in an ARP cache for rapid retrieval. Then the IP datagram is encapsulated in a link-layer frame and sent over the network. Encapsulation of IP datagrams and ARP requests and replies on IEEE 802 networks other than Ethernet is specified by the Subnetwork Access Protocol (SNAP). By default, standard Ethernet-style ARP encapsulation (represented by the arpa keyword) is enabled on the IP interface.
ARP entries added manually to the table do not age and must be manually removed.
For CLI procedures, see the Cisco IOS Release 12.4 documentation on Cisco.com.
How to Administer the Switch
- Configuring the Time and Date Manually
- Configuring a System Name
- Setting Up DNS
- Configuring a Message-of-the-Day Login Banner
- Configuring a Login Banner
- Managing the MAC Address Table
Configuring the Time and Date Manually
System time remains accurate through restarts and reboot, however, you can manually configure the time and date after the system is restarted.
We recommend that you use manual configuration only when necessary. If you have an outside source to which the switch can synchronize, you do not need to manually set the system clock.
 Note | You must reconfigure this setting if you have manually configured the system clock before the stack master fails and a different stack member assumes the role of stack master. |
Setting the System Clock
If you have an outside source on the network that provides time services, such as an NTP server, you do not need to manually set the system clock.
Follow these steps to set the system clock:
1.
enable
DETAILED STEPS
| Command or Action | Purpose |
|---|
Configuring the Time Zone
1.
enable
3.
clock timezone
zone hours-offset [minutes-offset]
6.
copy running-config
startup-config
DETAILED STEPS
Configuring Summer Time (Daylight Saving Time)
To configure summer time (daylight saving time) in areas where it starts and ends on a particular day of the week each year, perform this task:
1.
enable
3.
clock summer-time
zone
date
date month year hh:mm date
month year hh:mm [offset]]
4.
clock summer-time
zone
recurring [week day month hh:mm week day month hh:mm [offset]]
7.
copy running-config
startup-config
DETAILED STEPS
Follow these steps if summer time in your area does not follow a recurring pattern (configure the exact date and time of the next summer time events):
1.
enable
3. clock summer-time zone date[ month date year hh:mm month date year hh:mm [offset]]orclock summer-time zone date [date month year hh:mm date month year hh:mm [offset]]
6.
copy running-config
startup-config
DETAILED STEPS
Configuring a System Name
1.
enable
6.
copy running-config
startup-config
DETAILED STEPS
Setting Up DNS
If you use the switch IP address as its hostname, the IP address is used and no DNS query occurs. If you configure a hostname that contains no periods (.), a period followed by the default domain name is appended to the hostname before the DNS query is made to map the name to an IP address. The default domain name is the value set by the ip domain-name global configuration command. If there is a period (.) in the hostname, the Cisco IOS software looks up the IP address without appending any default domain name to the hostname.
Follow these steps to set up your switch to use the DNS:
1.
enable
4.
ip name-server
server-address1 [server-address2 ... server-address6]
5.
ip domain-lookup [nsap |
source-interface
interface]
8.
copy running-config
startup-config
DETAILED STEPS
Configuring a Message-of-the-Day Login Banner
You can create a single or multiline message banner that appears on the screen when someone logs in to the switch
Follow these steps to configure a MOTD login banner:
1.
enable
6.
copy running-config
startup-config
DETAILED STEPS
Configuring a Login Banner
You can configure a login banner to be displayed on all connected terminals. This banner appears after the MOTD banner and before the login prompt.
Follow these steps to configure a login banner:
1.
enable
6.
copy running-config
startup-config
DETAILED STEPS
Managing the MAC Address Table
- Changing the Address Aging Time
- Configuring MAC Address Change Notification Traps
- Configuring MAC Address Move Notification Traps
- Configuring MAC Threshold Notification Traps
- Adding and Removing Static Address Entries
- Configuring Unicast MAC Address Filtering
Changing the Address Aging Time
Follow these steps to configure the dynamic address table aging time:
1.
enable
3.
mac address-table
aging-time [0 |
10-1000000] [routed-mac |
vlan
vlan-id]
6.
copy running-config
startup-config
DETAILED STEPS
Configuring MAC Address Change Notification Traps
Follow these steps to configure the switch to send MAC address change notification traps to an NMS host:
1.
enable
3.
snmp-server host
host-addr
community-string
notification-type {
informs |
traps } {version {1 |
2c |
3}} {vrf
vrf
instance name}
4.
snmp-server enable
traps mac-notification change
5.
mac address-table
notification change
6.
mac address-table
notification change [interval
value] [history-size
value]
8.
snmp trap mac-notification
change {added |
removed}
11.
copy running-config
startup-config
DETAILED STEPS
Configuring MAC Address Move Notification Traps
When you configure MAC-move notification, an SNMP notification is generated and sent to the network management system whenever a MAC address moves from one port to another within the same VLAN.
Follow these steps to configure the switch to send MAC address-move notification traps to an NMS host:
1.
enable
3.
snmp-server host
host-addr {traps |
informs} {version {1 |
2c |
3}}
community-string
notification-type
4.
snmp-server
enable traps mac-notification move
5.
mac address-table
notification mac-move
8.
copy running-config
startup-config
DETAILED STEPS
To disable MAC address-move notification traps, use the no snmp-server enable traps mac-notification move global configuration command. To disable the MAC address-move notification feature, use the no mac address-table notification mac-move global configuration command.
You can verify your settings by entering the show mac address-table notification mac-move privileged EXEC commands.
Configuring MAC Threshold Notification Traps
When you configure MAC threshold notification, an SNMP notification is generated and sent to the network management system when a MAC address table threshold limit is reached or exceeded.
Follow these steps to configure the switch to send MAC address table threshold notification traps to an NMS host:
1.
enable
3.
snmp-server host
host-addr {traps
|
informs} {version {1 |
2c
|
3}}
community-string
notification-type
4.
snmp-server
enable traps mac-notification threshold
5.
mac address-table
notification threshold
6.
mac address-table
notification threshold [limit
percentage] | [interval
time]
9.
copy running-config
startup-config
DETAILED STEPS
Adding and Removing Static Address Entries
Follow these steps to add a static address:
1.
enable
3.
mac address-table
static
mac-addr
vlan
vlan-id
interface
interface-id
4.
end
6.
copy running-config
startup-config
DETAILED STEPS
Configuring Unicast MAC Address Filtering
Follow these steps to configure the Switch to drop a source or destination unicast static address:
1.
enable
3.
mac address-table
static
mac-addr
vlan
vlan-id
drop
6.
copy running-config
startup-config
DETAILED STEPS
Monitoring and Maintaining Administration of the Switch
| Command | Purpose |
|---|---|
clear mac address-table dynamic |
Removes all dynamic entries. |
clear mac address-table dynamic address mac-address |
Removes a specific MAC address. |
clear mac address-table dynamic interface interface-id |
Removes all addresses on the specified physical port or port channel. |
clear mac address-table dynamic vlan vlan-id |
Removes all addresses on a specified VLAN. |
show clock [detail] |
Displays the time and date configuration. |
show ip igmp snooping groups |
Displays the Layer 2 multicast entries for all VLANs or the specified VLAN. |
show mac address-table address mac-address |
Displays MAC address table information for the specified MAC address. |
show mac address-table aging-time |
Displays the aging time in all VLANs or the specified VLAN. |
show mac address-table count |
Displays the number of addresses present in all VLANs or the specified VLAN. |
show mac address-table dynamic |
Displays only dynamic MAC address table entries. |
show mac address-table interface interface-name |
Displays the MAC address table information for the specified interface. |
show mac address-table move update |
Displays the MAC address table move update information. |
show mac address-table multicast |
Displays a list of multicast MAC addresses. |
show mac address-table notification {change | mac-move | threshold} |
Displays the MAC notification parameters and history table. |
show mac address-table secure |
Displays the secure MAC addresses. |
show mac address-table static |
Displays only static MAC address table entries. |
show mac address-table vlan vlan-id |
Displays the MAC address table information for the specified VLAN. |
Configuration Examples for Switch Administration
Example: Setting the System Clock
This example shows how to manually set the system clock:
Switch# clock set 13:32:00 23 July 2013
Examples: Configuring Summer Time
This example (for daylight savings time) shows how to specify that summer time starts on March 10 at 02:00 and ends on November 3 at 02:00:
Switch(config)# clock summer-time PDT recurring PST date
10 March 2013 2:00 3 November 2013 2:00
This example shows how to set summer time start and end dates:
Switch(config)#clock summer-time PST date
20 March 2013 2:00 20 November 2013 2:00
Example: Configuring a MOTD Banner
This example shows how to configure a MOTD banner by using the pound sign (#) symbol as the beginning and ending delimiter:
Switch(config)# banner motd # This is a secure site. Only authorized users are allowed. For access, contact technical support. # Switch(config)#
This example shows the banner that appears from the previous configuration:
Unix> telnet 192.0.2.15 Trying 192.0.2.15... Connected to 192.0.2.15. Escape character is '^]'. This is a secure site. Only authorized users are allowed. For access, contact technical support. User Access Verification Password:
Example: Configuring a Login Banner
This example shows how to configure a login banner by using the dollar sign ($) symbol as the beginning and ending delimiter:
Switch(config)# banner login $ Access for authorized users only. Please enter your username and password. $ Switch(config)#
Example: Configuring MAC Address Change Notification Traps
This example shows how to specify 172.20.10.10 as the NMS, enable MAC address notification traps to the NMS, enable the MAC address-change notification feature, set the interval time to 123 seconds, set the history-size to 100 entries, and enable traps whenever a MAC address is added on the specified port:
Switch(config)# snmp-server host 172.20.10.10 traps private mac-notification Switch(config)# snmp-server enable traps mac-notification change Switch(config)# mac address-table notification change Switch(config)# mac address-table notification change interval 123 Switch(config)# mac address-table notification change history-size 100 Switch(config)# interface gigabitethernet1/2/1 Switch(config-if)# snmp trap mac-notification change added
Example: Configuring MAC Threshold Notification Traps
This example shows how to specify 172.20.10.10 as the NMS, enable the MAC address threshold notification feature, set the interval time to 123 seconds, and set the limit to 78 per cent:
Switch(config)# snmp-server host 172.20.10.10 traps private mac-notification Switch(config)# snmp-server enable traps mac-notification threshold Switch(config)# mac address-table notification threshold Switch(config)# mac address-table notification threshold interval 123 Switch(config)# mac address-table notification threshold limit 78
Example: Adding the Static Address to the MAC Address Table
This example shows how to add the static address c2f3.220a.12f4 to the MAC address table. When a packet is received in VLAN 4 with this MAC address as its destination address, the packet is forwarded to the specified port:
Switch(config)# mac address-table static c2f3.220a.12f4 vlan 4 interface gigabitethernet1/1/1
Example: Configuring Unicast MAC Address Filtering
This example shows how to enable unicast MAC address filtering and how to configure drop packets that have a source or destination address of c2f3.220a.12f4. When a packet is received in VLAN 4 with this MAC address as its source or destination, the packet is dropped:
Switch(config)# mac address-table static c2f3.220a.12f4 vlan 4 drop
Additional References for Switch Administration
Related Documents
| Related Topic | Document Title |
|---|---|
Switch administration commands |
Catalyst 2960-X Switch System Management Command Reference |
Network management configuration |
Catalyst 2960-X Switch Network Management Configuration Guide |
Layer 2 configuration |
Catalyst 2960-X Switch Layer 2 Configuration Guide |
VLAN configuration |
Catalyst 2960-X Switch VLAN Management Configuration Guide |
| Platform-independent command references | Cisco IOS 15.3M&T Command References |
| Platform-independent configuration information | Cisco IOS 15.3M&T Configuration Guides |
Standards and RFCs
| Standard/RFC | Title |
|---|---|
| None | — |
MIBs
| MIB | MIBs Link |
|---|---|
All supported MIBs for this release. |
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Technical Assistance
| Description | Link |
|---|---|
|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Feature History and Information for Switch Administration
Release |
Modification |
|---|---|
Cisco IOS 15.0(2)EX |
This feature was introduced. |
 Feedback
Feedback