Understanding Switch Clusters
A switch cluster is a set of up to 16 connected, cluster-capable Catalyst switches that are managed as a single entity. The Switch in the cluster use the Switch clustering technology so that you can configure and troubleshoot a group of different Catalyst desktop Switch platforms through a single IP address.
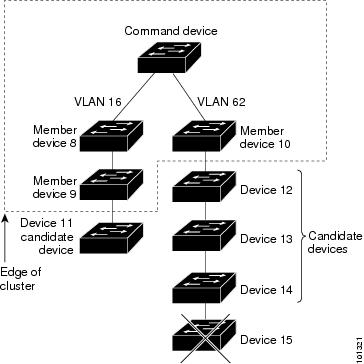
In a Switch cluster, 1 Switch must be the cluster command Switch and up to 15 other Switch can be cluster member switches . The total number of Switch in a cluster cannot exceed 16 Switch. The cluster command Switch is the single point of access used to configure, manage, and monitor the cluster member Switch. Cluster members can belong to only one cluster at a time.
 Note |
A Switch cluster is different from a switch stack . A switch stack is a set of Catalyst 3750-X, Catalyst 3750-E, or Catalyst 3750 Switch connected through their stack ports. |
- Management of Catalyst Switch regardless of their interconnection media and their physical locations. The Switch can be in the same location, or they can be distributed across a Layer 2 or Layer 3 (if your cluster is using a Catalyst 3560, Catalyst 3750, Catalyst 3560-E, Catalyst 3750-E, Catalyst 3560-X, or Catalyst 3750-X Switch as a Layer 3 router between the Layer 2 Switch in the cluster) network.
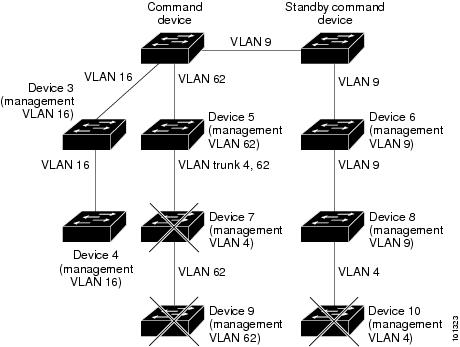
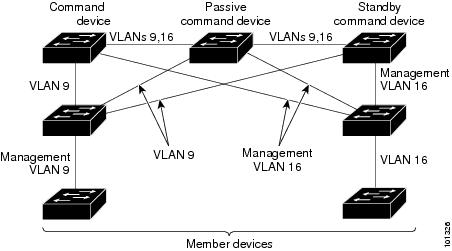
- Command-switch redundancy if a cluster command Switch fails. One or more Switch can be designated as standby cluster command switches to avoid loss of contact with cluster members. A cluster standby group is a group of standby cluster command Switch.
- Management of a variety of Catalyst Switch through a single IP address. This conserves on IP addresses, especially if you have a limited number of them. All communication with the switch cluster is through the cluster command Switch IP address.
The below table lists the Catalyst switches eligible for Switch clustering, including which ones can be cluster command switches and which ones can only be cluster member switches, and the required software versions.
| Switch | Cisco IOS Release | Cluster Capability |
| Catalyst 3750-X | 12.2(53)SE2 or later | Member or command switch |
| Catalyst 3750-E | 12.2(35)SE2 or later | Member or command switch |
| Catalyst 3750 | 12.1(11)AX or later | Member or command switch |
| Catalyst 3560-X | 12.2(53)SE1 or later | Member or command switch |
| Catalyst 3560-E | 12.2(35)SE2 or later | Member or command switch |
| Catalyst 3560 | 12.1(19)EA1b or later | Member or command switch |
| Catalyst 3550 | 12.1(4)EA1 or later | Member or command switch |
| Catalyst 2970 | 12.1(11)AX or later | Member or command switch |
| Catalyst 2960 | 12.2(25)FX or later | Member or command switch |
| Catalyst 2955 | 12.1(12c)EA1 or later | Member or command switch |
| Catalyst 2950 | 12.0(5.2)WC(1) or later | Member or command switch |
| Catalyst 2950 LRE | 12.1(11)JY or later | Member or command switch |
| Catalyst 2940 | 12.1(13)AY or later | Member or command switch |
| Catalyst 3500 XL | 12.0(5.1)XU or later | Member or command switch |
| Catalyst 2900 XL (8-MB switches) | 12.0(5.1)XU or later | Member or command switch |
| Catalyst 2900 XL (4-MB switches) | 11.2(8.5)SA6 (recommended) | Member switch only |
| Catalyst 1900 and 2820 | 9.00(-A or -EN) or later | Member switch only |
Cluster Command Switch Characteristics
A cluster command Switch must meet these requirements:
- It is running a supported software release.
- It has an IP address.
- It has Cisco Discovery Protocol (CDP) Version 2 enabled (the default).
- It is not a command or cluster member Switch of another cluster.
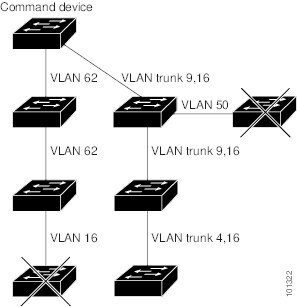
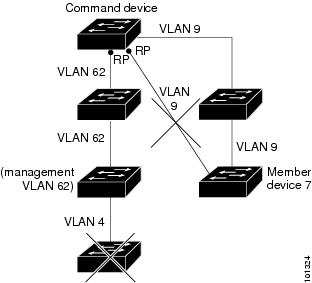
- It is connected to the standby cluster command Switch through the management VLAN and to the cluster member Switch through a common VLAN.
Standby Cluster Command Switch Characteristics
A standby cluster command Switch must meet these requirements:
- It is running a supported software release.
- It has an IP address.
- It has CDP Version 2 enabled.
- It is connected to the command Switch and to other standby command Switch through its management VLAN.
- It is connected to all other cluster member Switch (except the cluster command and standby command Switch) through a common VLAN.
- It is redundantly connected to the cluster so that connectivity to cluster member Switch is maintained.
- It is not a command or member Switch of another cluster.
 Note |
Standby cluster command Switch must be the same type of Switch as the cluster command Switch. For example, if the cluster command Switch is a Catalyst 3750-E Switch, the standby cluster command Switch must also be Catalyst 3750-E Switch. See the switch configuration guide of other cluster-capable Switch for their requirements on standby cluster command Switch. |
Candidate Switch and Cluster Member Switch Characteristics
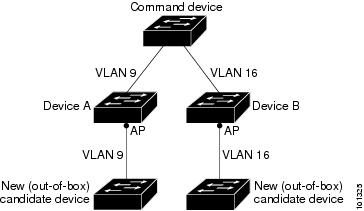
Candidate switches are cluster-capable Switch and Switch stacks that have not yet been added to a cluster. Cluster member Switch are switches and switch stacks that have actually been added to a Switch cluster. Although not required, a candidate or cluster member Switch can have its own IP address and password.
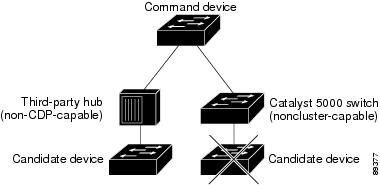
- It is running cluster-capable software.
- It has CDP Version 2 enabled.
- It is not a command or cluster member Switch of another cluster.
- If a cluster standby group exists, it is connected to every standby cluster command Switch through at least one common VLAN. The VLAN to each standby cluster command Switch can be different.
- The ip http server global configuration command must be configured on the Switch.
- It is connected to the cluster command Switch through at least one common VLAN.
 Note |
Catalyst 1900, Catalyst 2820, Catalyst 2900 XL, Catalyst 2940, Catalyst 2950, and Catalyst 3500 XL candidate and cluster member Switch must be connected through their management VLAN to the cluster command switch and standby cluster command switches. For complete information about these Switch in a switch-cluster environment, see the software configuration guide for that specific switch. This requirement does not apply if you have a Catalyst 2960, Catalyst 2970, Catalyst 3550, Catalyst 3560, Catalyst 3560-E, Catalyst 3750, Catalyst 3750-E, Catalyst 3650-X, or Catalyst 3750-X cluster command switch. Candidate and cluster member Switch can connect through any VLAN in common with the cluster command switch. |
 Feedback
Feedback