Recommended Policy and Rule Settings
We recommend the following policy settings:
-
Decryption policy:
-
Default action Do Not Decrypt.
-
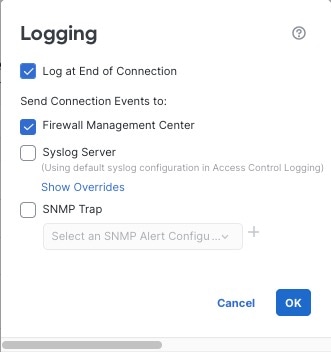
Enable logging.
-
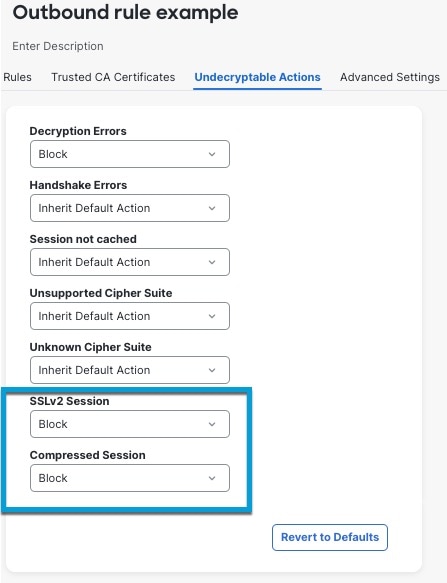
Set Undecryptable Actions to Block for both SSL v2 Session and Compressed Session.
-
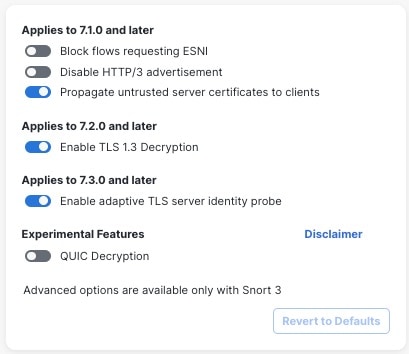
Enable TLS 1.3 decryption and adaptive TLS server identity probe in the policy's advanced settings.
-
-
Decryption rules: Enable logging for every rule except those with a Do Not Decrypt rule action. (It's up to you; if you want to see information about traffic that isn't decrypted, enable logging for those rules also.)
-
Access control policy:
-
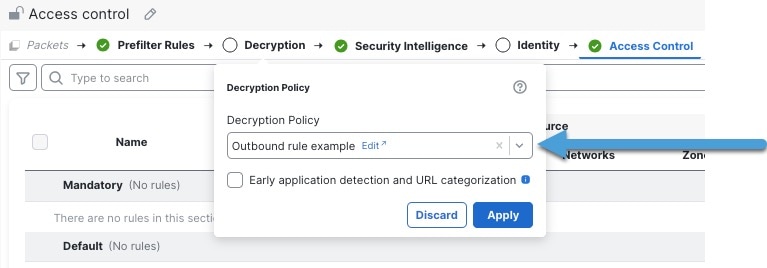
Associate your decryption policy with an access control policy. (If you fail to do this, your decryption policy and rules have no effect.)
-
Set the default policy action to Intrusion Prevention: Balanced Security and Connectivity.
-
Enable logging.
-

 )
)

 )
) Feedback
Feedback