Decryption Rules Best Practices
This chapter provides an example decryption policy with decryption rules that illustrates our best practices and recommendations. First we'll discuss settings for the decryption policies and access control policies and then walk through all the rules and why we recommend they be ordered in a particular way.
Some general guidelines:
-
Decrypting traffic requires processing and memory; decrypting too much traffic can impact performance. Before you set up decryption policies and rules, see When to Decrypt Traffic, When Not to Decrypt in the Cisco Secure Firewall Management Center Device Configuration Guide.
-
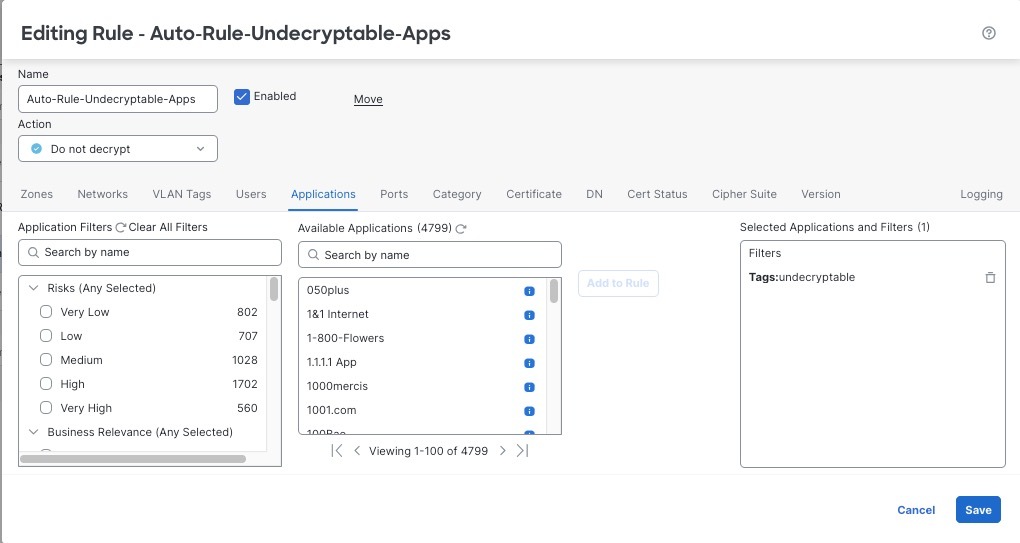
Among the types of traffic you should exclude from decryption is traffic that is by nature undecryptable; typically, undecryptable traffic uses TLS/SSL certificate pinning. The decryption policy wizard assists you by automatically creating Do Not Decrypt rules for traffic determined to be undecryptable according to distinguished name or category. For more information, see Create a Decryption Policy with Outbound Connection Protection in the Cisco Secure Firewall Management Center Device Configuration Guide. .
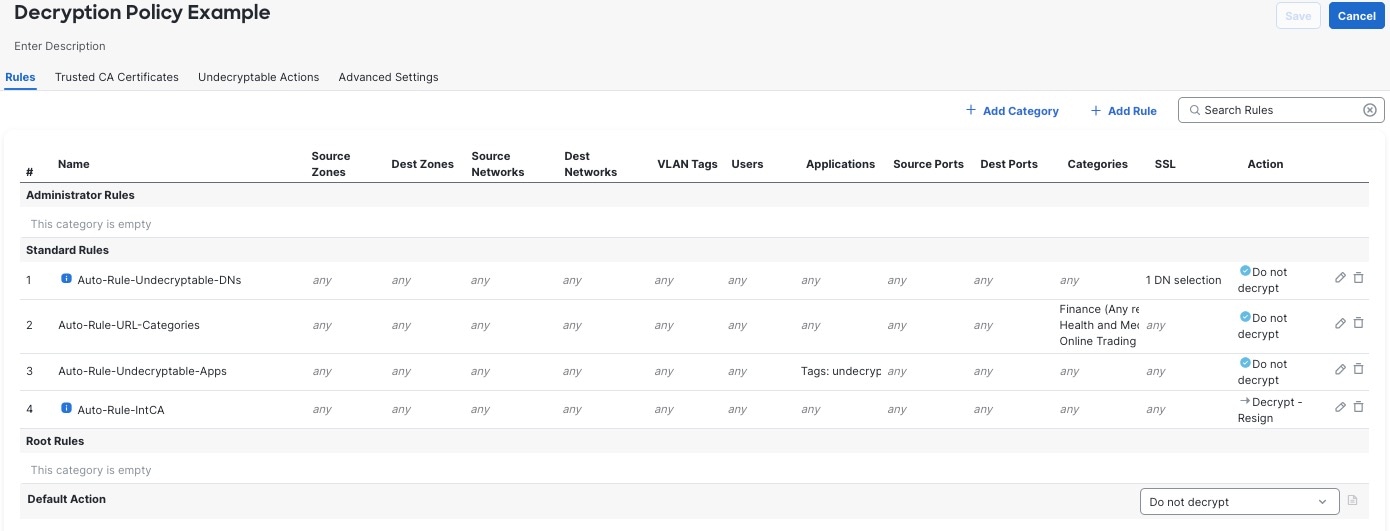
Following are the decryption rules we'll discuss in this chapter.

In the preceding example, the decryption policy wizard creates all rules whose name starts with Auto-Rule (that is, rules 3, 4, 5, and 8). You must create the other decryption rules shown in this example and order them manually.
We recommend you add the rules in this order to allow the most intensive operation (decryption) to occur last and also to take advantage of TLS certificate caching, which is defined in RFC 7924.
The managed device that evaluates the traffic uses TLS server certificate caching wherever possible to dramatically improve subsequent certificate matching connections and can dramatically improve throughput and performance.
-
Rule 1 matches traffic on source network so no TLS certificate is required.
-
Rules 2 through 5 match on the TLS certificate, but if there is no certificate in the cache when the managed device sees the ClientHello, the system attempts to fall back to the server name indication (SNI). If the TLS probe connection is successful, the device should have the certificate in the cache for the next connection.
-
Rule 6 requires a TLS certificate. If no certificate is in the cache and the TLS probe was successful, the certificate is cached for the next connection.
-
Rule 7 is matched on negotiated protocol version, so no TLS certificate is required. The negotiated protocol version waits until we receive the ServerHello.
The preceding recommended rule order also has the advantage of starting with a rule that doesn't need a TLS certificate at all and is followed by rules (2 through 6) that can cache the TLS certificate with the ClientHello. Rules (like rule 7) that require ServerHello should be later in the policy because those take longer to evaluate.
The adaptive TLS server identity probe is a recommended advanced decryption policy option that is discussed in more detail in Decryption Policy Advanced Options in the Cisco Secure Firewall Management Center Device Configuration Guide.
The following topics provide more information.


 Feedback
Feedback