Administration portal
|
1 |
Menu Icon |
Click the Menu icon ( 
The menu options on the left pane are:
|
||
|
2 |
Top-Right Menu Icons |
|
Interactive Help
The Interactive Help enables users to work effectively with Cisco ISE by providing tips and step-by-step guidance to complete tasks with ease.
This feature is enabled by default. To disable this feature, click the Menu icon (![]() ) and choose
, and uncheck the Enable Interactive Help check box.
) and choose
, and uncheck the Enable Interactive Help check box.
Click the Show button to view the Interactive Help menu.
If you access the Cisco ISE administrator portal through a Google Chrome Incognito window, you must enable third-party cookies to view and access Interactive Help. See Third-party cookie controls in Incognito mode.
Customer Experience Surveys
From Cisco ISE Release 3.2 Patch 4, Cisco ISE presents customer satisfaction surveys to its users within the administration portal. The periodic assessment of customer satisfaction helps us better understand your Cisco ISE experiences, track what is working well, and identify areas of improvement. The survey is displayed in a dialog box when you log in to your Cisco ISE administration portal. After you submit a survey, you are not presented with another survey for the next 90 days.
The Cisco ISE surveys feature is enabled by default in every Cisco ISE deployment and for each user. The feature setting is available in the ISE Surveys area of the page of the administration portal. This feature requires access to the URL *.qualtrics.com.
The Cisco ISE user can choose to disable the surveys feature by carrying out the following steps:
-
Click the profile icon at the top-right corner of the Cisco ISE administration portal.
-
Click Account Settings.
-
Uncheck the Take customer experience surveys to help improve Cisco ISE check box.
When you disable the Cisco ISE surveys feature for a user or a Cisco ISE deployment, the feature remains disabled until you enable it again.
Apply Default or Dark Mode
Procedure
|
Step 1 |
Click the gear icon ( |
|
Step 2 |
Click Account Settings. |
|
Step 3 |
In the Theme area, click the radio button for Default Mode or Dark Mode. |
|
Step 4 |
Click Save. Cisco ISE caches the display mode you choose in the browser storage. Therefore, in the following scenarios where the browser cache that stores the display mode is not available, the Cisco ISE GUI is displayed in the Light mode for a few seconds:
|
Cisco ISE Home Dashboards
The Cisco ISE Home dashboard displays live consolidated and correlated statistical data that is essential for effective monitoring and troubleshooting. Dashboard elements typically display activity over 24 hours. The following figure is an example of the information available in a Cisco ISE dashboard. You can view the Cisco ISE dashboard data only in the primary Policy Administration node (PAN) portal.
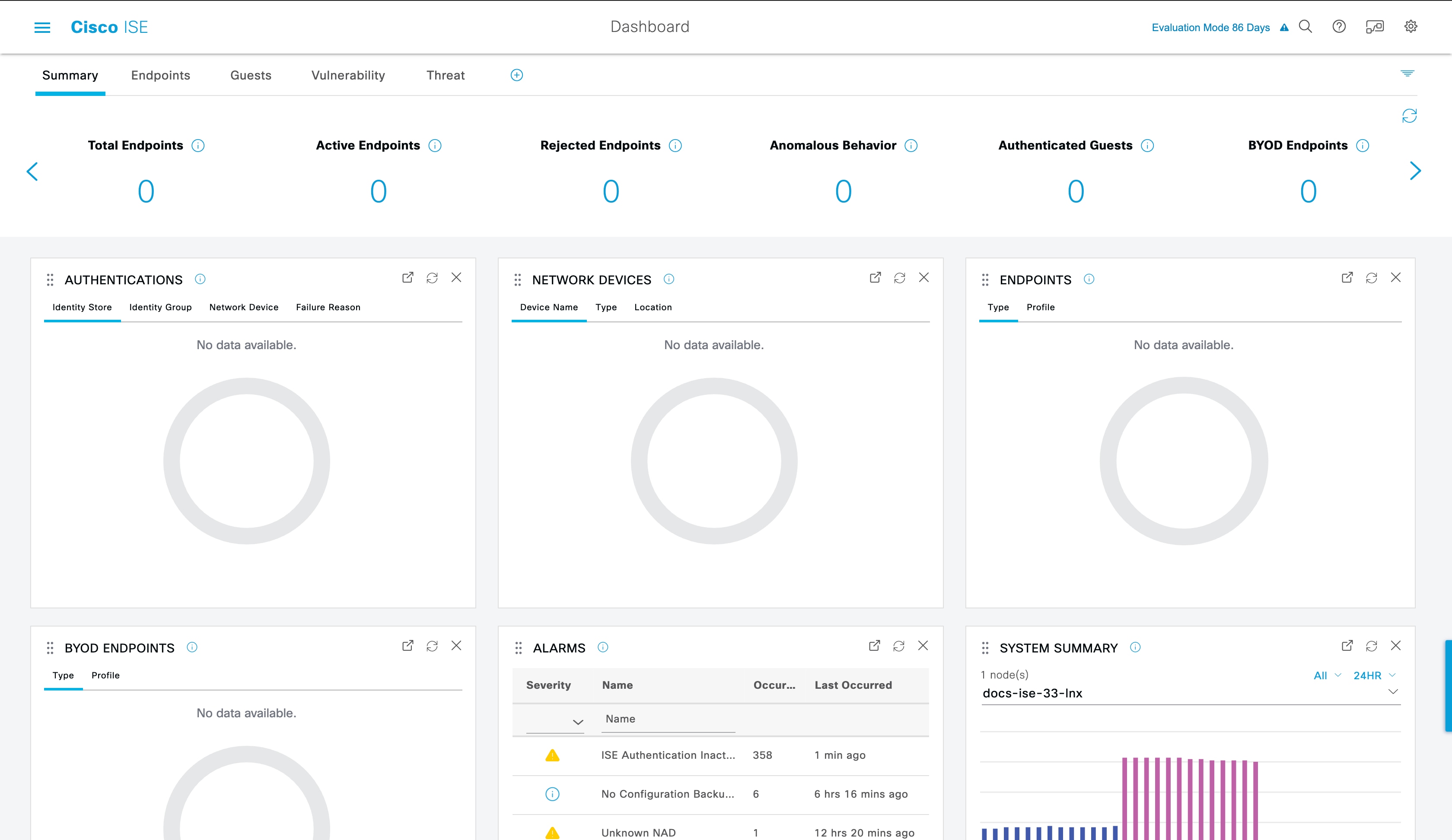
The home page has five default dashboards that display your Cisco ISE data. Each of these dashboards has several predefined dashlets.
-
Summary: This dashboard contains a linear metrics dashlet, pie chart dashlets, and list dashlets. The metrics dashlet is not configurable. By default this dashboard contains the dashlets Status Endpoints, Endpoint Categories, and Network Devices.
-
Endpoints: By default, this dashboard contains the dashlets Status, Endpoints, Endpoint Categories, and Network Devices.
-
Guests: This dashboard contains dashlets that provide information on guest user type, log in failures, and location of acitivity.
-
Vulnerability: This dashboard displays the information that vulnerability servers report to Cisco ISE.
-
Threat: This dashboard displays information from the threat servers reports sent to Cisco ISE.
Configuring Home Dashboards
You can customize a home page dashboard by clicking the Inverted Pyramid icon in the top right corner of the window:
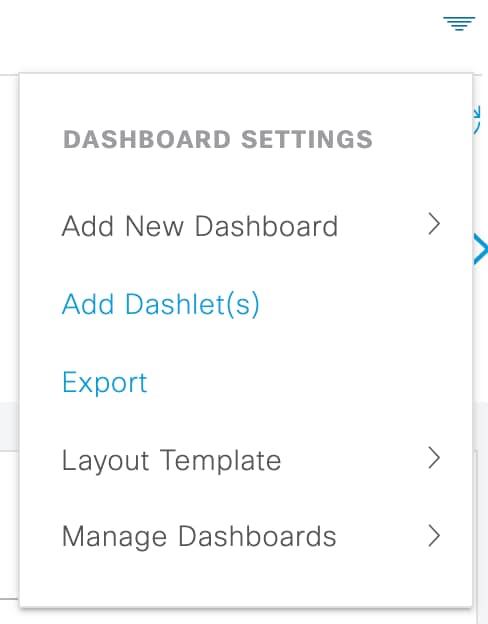
The following options are displayed in the drop-down list:
-
Add New Dashboard allows you to add a new dashboard. Enter a value in the field that is displayed and click Apply.
-
Add Dashlet(s) displays a dialog box with a list of dashlets available. Click Add or Remove next to the dashlet name to add or remove a dashlet from the dashboard.
-
Export saves the selected home page view to a PDF.
-
Layout Template configures the number of columns that are displayed in this view.
-
Manage Dashboards contains two options:
-
Mark As Default Dashboard: Choose this option to make the current dashboard the default view when you choose Home.
-
Reset All Dashboards: Use this option to also reset all the dashboards and remove your configurations on all the Home dashboards.
-
Context Visibility Views
The structure of a Context Visibility window is similar to the home page, except that the Context Visibility windows:
-
Retain your current context (browser window) when you filter the displayed data
-
Are more customizable
-
Focus on endpoint data
You can view the context visibility data only from the primary PAN.
Dashlets on the Context Visibility windows show information about endpoints, and endpoint connections to NADs. The information currently displayed is based on the content in the list of data below the dashlets on each window. Each window displays endpoint data, based on the name of the tab. As you filter the data, both the list and dashlets update. You can filter the data by clicking on parts of one or more of the circular graphs, by filtering rows on the table, or any combination those actions. As you select filters, the effects are additive, also referred to as cascading filter, which allows you to drill down to find the particular data you are looking for. You can also click an endpoint in the list, and get a detailed view of that endpoint.
There are four main menu options under Context Visibility:
-
Endpoints: Filter the endpoints you want to view based on types of devices, compliance status, authentication type, hardware inventory, and more. See The Hardware dashboard for additional information.

Note
We recommend that you enable the accounting settings on the network access devices (NADs) to ensure that the accounting start and update information is sent to Cisco ISE.
Cisco ISE can collect accounting information, such as the latest IP address, status of the session (Connected, Disconnected, or Rejected), the number of days an endpoint has been inactive, only if accounting is enabled. This information is displayed in the Live Logs, Live Sessions and Context Visibility windows in the Cisco ISE administration portal. When accounting is disabled on a NAD, there might be a missing, incorrect, or mismatched accounting information between the Live Sessions, Live Logs and Context Visibility windows.

Note
The Visibility Setup workflow that is available on the Cisco ISE administration portal home page allows you to add a list of IP address ranges for endpoints discovery. After this workflow is configured, Cisco ISE authenticates the endpoints, but the endpoints that are not included in the configured IP address ranges are not displayed in the window and the Endpoints listing page ().
-
Users: Displays user-based information from user identity sources.
If there is a change in the username or password attribute, it reflects in the Users window when there is a change in the authentication status.
If the username is changed in the Microsoft Active Directory, the updated change is displayed in the Users window immediately after re-authentication.
If any other attributes such as Email, Phone, Department, etc are changed in the Microsoft Active Directory, the updated attributes are displayed in the Users window 24 hours after re-authentication.

Note
Updating User Attributes from AD depends on the interval configured under Active Directory Probe. For more information, see Active Directory Probe.
-
Network Devices: This window displays the list of NADs that have endpoints connected to them. For any NAD, click the number of endpoints that is displayed in the corresponding # of endpoints column. A window that lists all the devices filtered by that NAD is displayed.

Important
When a network device is renamed, the previous device name may still appear in the Top N Authentications by Network Device report and in the Network Devices view under Context Visibility. For example, if you rename a device from "SPRT" to "SPRT-New," endpoints previously associated with "SPRT" are not automatically updated or re-tagged with the new name. This is expected behavior. Cisco ISE does not synchronize or update historical data when a network device is renamed.

Note
If you have configured your network device with SNMPv3 parameters, you cannot generate the Network Device Session Status Summary report that is provided by the Cisco ISE monitoring service (). You can generate this report successfully if your network device is configured with SNMPv1 or SNMPv2c parameters.
-
Application: Use this window to identify the number of endpoints that have a specific application installed. The results are displayed in graphical and table formats. The graphical representation helps you make a comparative analysis. For example, you can find out the number of endpoints with the Google Chrome software along with their Version, Vendor, and Category (Anti-phishing, Browser, and so on) in a table as well as a bar chart. For more information, see The Application Tab.
You can create a new tab in the Context Visibility windows and create a custom list for additional filtering. Dashlets are not supported in custom views.
Click a section of a circular graph in a dashlet to view a new window with filtered data from that dashlet in. From this new window, you can continue to filter the displayed data, as described in Filtering Displayed Data in a View.
For more information about using Context Visibility windows to find endpoint data, see the following Cisco YouTube video which uses ISE 2.1 https://www.youtube.com/watch?v=HvonGhrydfg.
Attributes in Context Visibility
The systems and services that provide attributes for Context Visibility sometimes have different values for the same attribute name. The following are a few examples:
For Operating System
-
OperatingSystem: Posture operating system.
-
operating-system: NMAP operating system.
-
operating-system-result: Profiler consolidated operating system.
 Note |
There might be some discrepancies in the endpoint operating system data that is displayed in the Context Visibility window when you enable multiple probes in Cisco ISE for an endpoint. |
For Portal Name
-
Portal.Name: Guest portal name when device registration is turned on.
-
PortalName: Guest portal name when device registration is not turned on.
For Portal User
-
User-Name: Username from RADIUS authentication.
-
GuestUserName: Guest username.
-
PortalUser: Portal username.
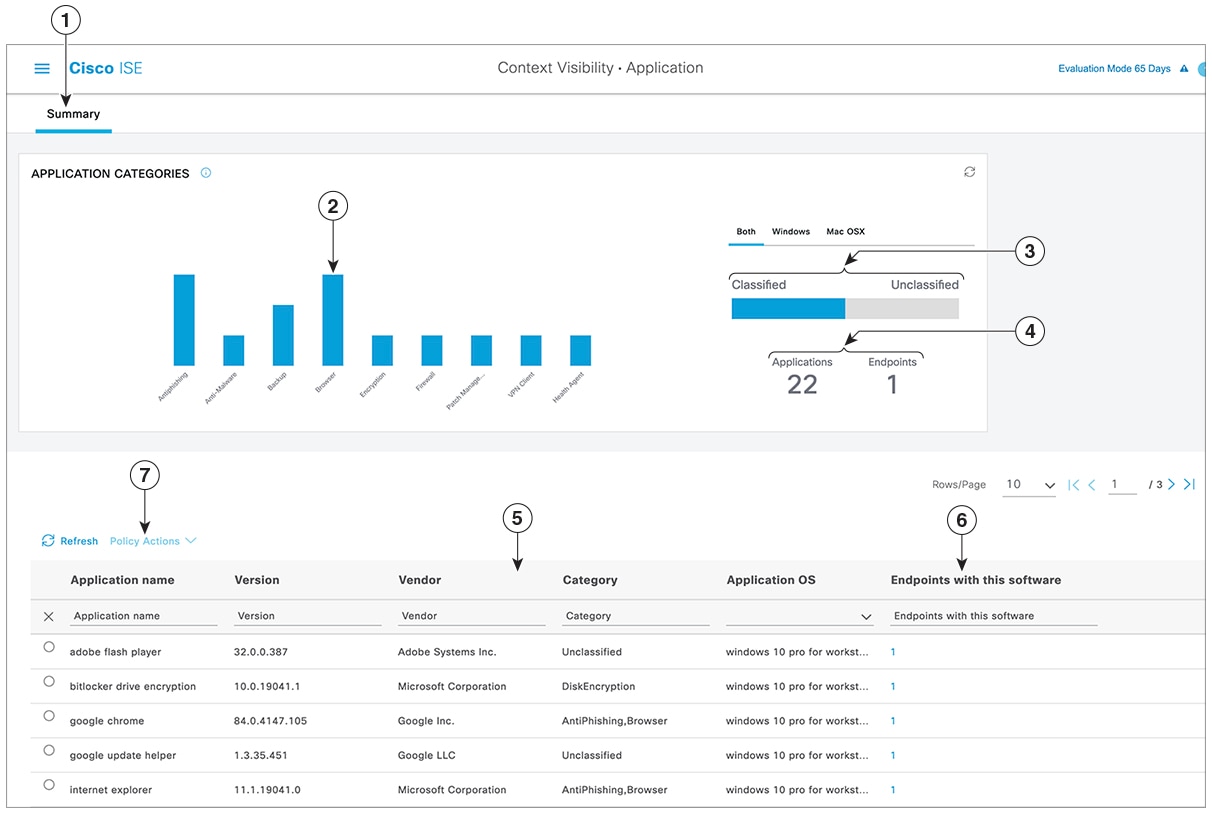
The Application Dashboard
|
Label |
Description |
|||||
|---|---|---|---|---|---|---|
|
1 |
The Summary tab is displayed by default on the home page. It displays the Application Categories dashlet, which contains a bar chart. Applications are classified into 13 categories. Applications that do not fall into any of these categories are grouped as Unclassified. The available categories are Anti-Malware, Anti phishing, Backup, Browser, Data Loss Prevention, Data Storage, Encryption, Firewall, Messenger, Patch Management, Public File Sharing, Virtual Machine, and VPN Client. |
|||||
|
2 |
Each bar corresponds to a classified category. Hover over each bar to view the total number of applications and endpoints that correspond to the selected application category. |
|||||
|
3 |
The applications and endpoints that fall under the Classified category are displayed in blue. Unclassified applications and endpoints are displayed in gray. Hover over the classified or unclassified category bars to view the total number of applications and endpoints that belong to that category. You can click Classified and view the results in the bar chart and table in the window. When you click Unclassified, the bar chart is disabled and the results are displayed in the table in the window. |
|||||
|
4 |
The applications and endpoints are displayed based on the selected filter. You can view the breadcrumb trail as you click different filters. You can click Clear All Filters to remove all the applied filters. 
|
|||||
|
5 |
When you click multiple bars, the corresponding classified applications and endpoints are displayed in the table. For example, if you select the Antimalware and Patch Management categories, the following results are displayed: |
|||||
| Application Name | Version | Vendor | Category | Application OS | Endpoints With This Software | |
|
Gatekeeper |
9.9.5 |
Apple Inc. |
Antimalware |
windows 7 64-bit,mac osx 10.10,mac osx 8,mac osx 9 | 5 | |
|
Gatekeeper |
10.9.5 |
Apple Inc. |
Antimalware |
Windows 8 64-bit, mac osx 10.10 | 3 | |
|
Software Update |
2.3 |
Apple Inc. |
Patch Management |
Windows 7 64 bit, mac osx 10.10,mac osx 8,mac osx 9 |
5 |
|
|
6 |
Click an endpoint in the Endpoints With This Software column in the table to view the endpoint details, such as Mac address, NAD IP address, NAD port ID/SSID, IPv4 address, and so on. |
|||||
|
7 |
You can select an application name and choose the Create App Compliance option from the Policy Actions drop-down list to create application compliance condition and remediation. |
|||||
The Hardware dashboard
The endpoint hardware tab in context visibility helps you quickly collect, analyze, and report endpoint hardware inventory information. You can identify endpoints with low memory capacity and determine the BIOS model and version without installing additional modules or directly interacting with the endpoint. You can assess requirements before purchasing assets and ensure that resources are replaced on time, which enables effective asset lifecycle management.
The tab displays the Manufacturers and Endpoint Utilizations dashlets. The dashlets update to show changes according to the selected filter. The Manufacturers dashlet displays hardware inventory details for endpoints with Windows and macOS. The Endpoint Utilizations dashlet displays the CPU, memory, and disk utilization for endpoints. You can select any of the three options to view utilization as a percentage.
-
Devices that have a CPU usage over n%.
-
Devices that have a memory usage over n%.
-
Devices that have a disk usage over n%.
 Note |
The hardware inventory data takes 120 seconds to be displayed in the Cisco ISE GUI. Cisco ISE collects hardware inventory data for posture compliant and non-compliant states. |
 Note |
|
The attribute table displays the hardware attributes of an endpoint and its connected external devices. The table columns are initially displayed based on your deployment and the dashlets shown. You can add more columns using the Settings icon and reorder columns as needed. The hardware attributes displayed include:
-
MAC address
-
BIOS manufacturer
-
BIOS serial number
-
BIOS model
-
Attached devices
-
CPU name
-
CPU speed (GHz)
-
CPU usage (%)
-
Number of cores
-
Number of processors
-
Memory size (GB)
-
Memory usage (%)
-
Total internal disk(s) size (GB)
-
Total internal disk(s) free size (GB)
-
Total internal disk(s) usage (GB) and (%)
-
Number of internal disks
-
NAD port ID
-
Status
-
Network device name
-
Location
-
UDID
-
IPv4 address
-
Username
-
Hostname
-
OS types
-
Anomalous behavior
-
Endpoint profile
-
Description
-
Endpoint type
-
Identity group
-
Registration date
-
Identity store
-
Authorization profile
You can click the number in the Attached Devices column that corresponds to an endpoint to view the name, category, manufacturer, type, product ID, and vendor ID of the USB devices that are currently attached to the endpoint.
 Note |
Cisco ISE profiles most hardware attributes for each client system, but some attributes may not be included. If an attribute is not profiled, it does not appear in the Hardware tab. |
You can adjust the hardware inventory data collection interval in the page. The default interval is five minutes.
Dashlets
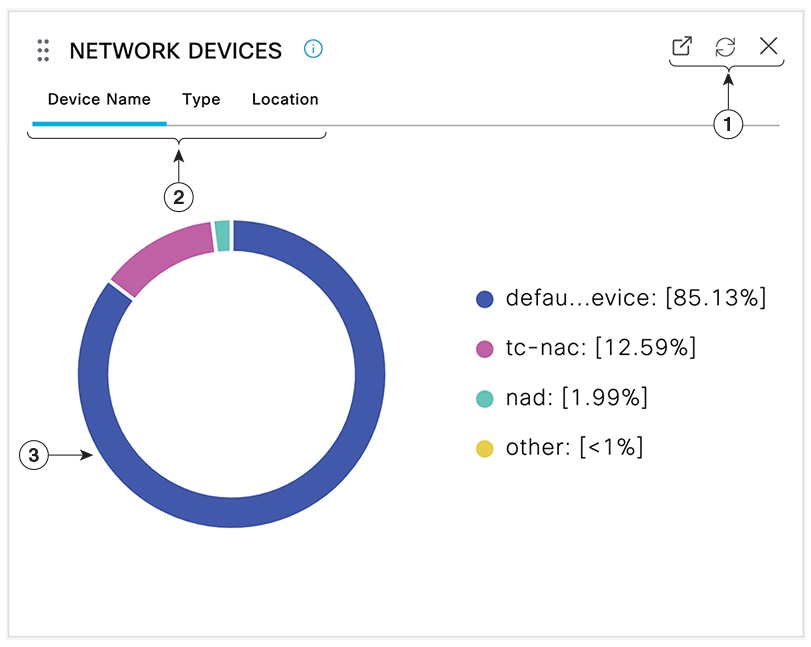
The following image is an example of a dashlet:
-
The Open New Window icon opens this dashlet in a new browser window. The pie chart refreshes. Click the X to delete this dashlet. This option is only available on the home page. You delete dashlets in Context Visibility windows using the gear symbol in the top-right corner of the screen.
-
Some dashlets have different categories of data. Click the category to see a pie chart with that set of data.
-
The pie chart shows the data that you have selected. Click one of the pie segments to open a new tab in with the filtered data, based on that pie segment.
Click a section of the pie chart in a home page dashboard to open the chart in a new browser window. The new window displays data that is filtered by the section of the pie chart that you clicked on.
When you click a section of the pie chart in a Context Visibility window, the displayed data is filtered but context does not change. You view the filtered data in the same browser window.
Filtering Displayed Data in a View
When you click a dashlet in a Context Visibility window, the corresponding data is filtered by the item you click and displayed. For example, when you click a section of a pie chart, the data for the chosen section is filtered and displayed.
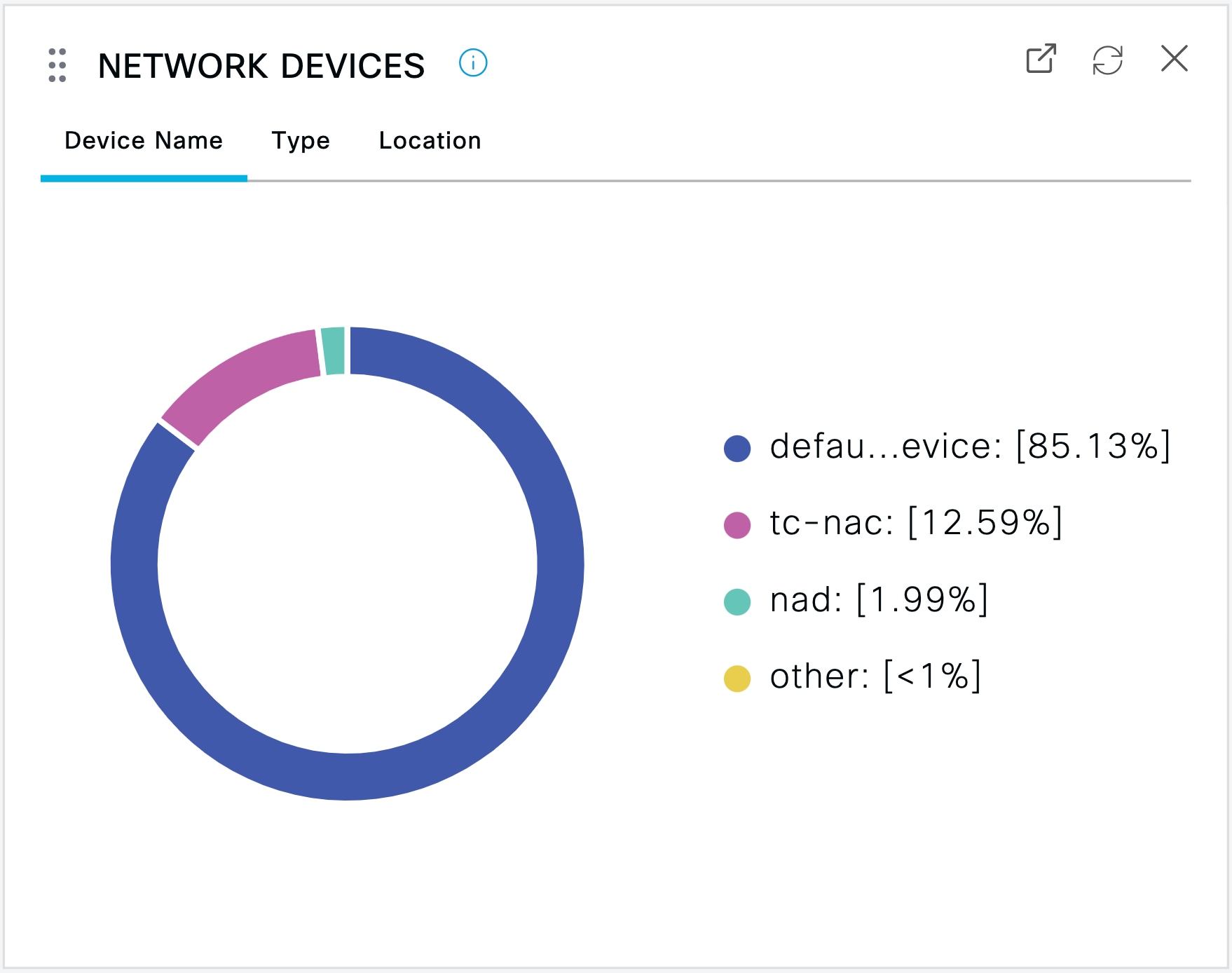
If you click defau...evice in the Network Devices dashlet, a new window displays the data, as shown in the following image:
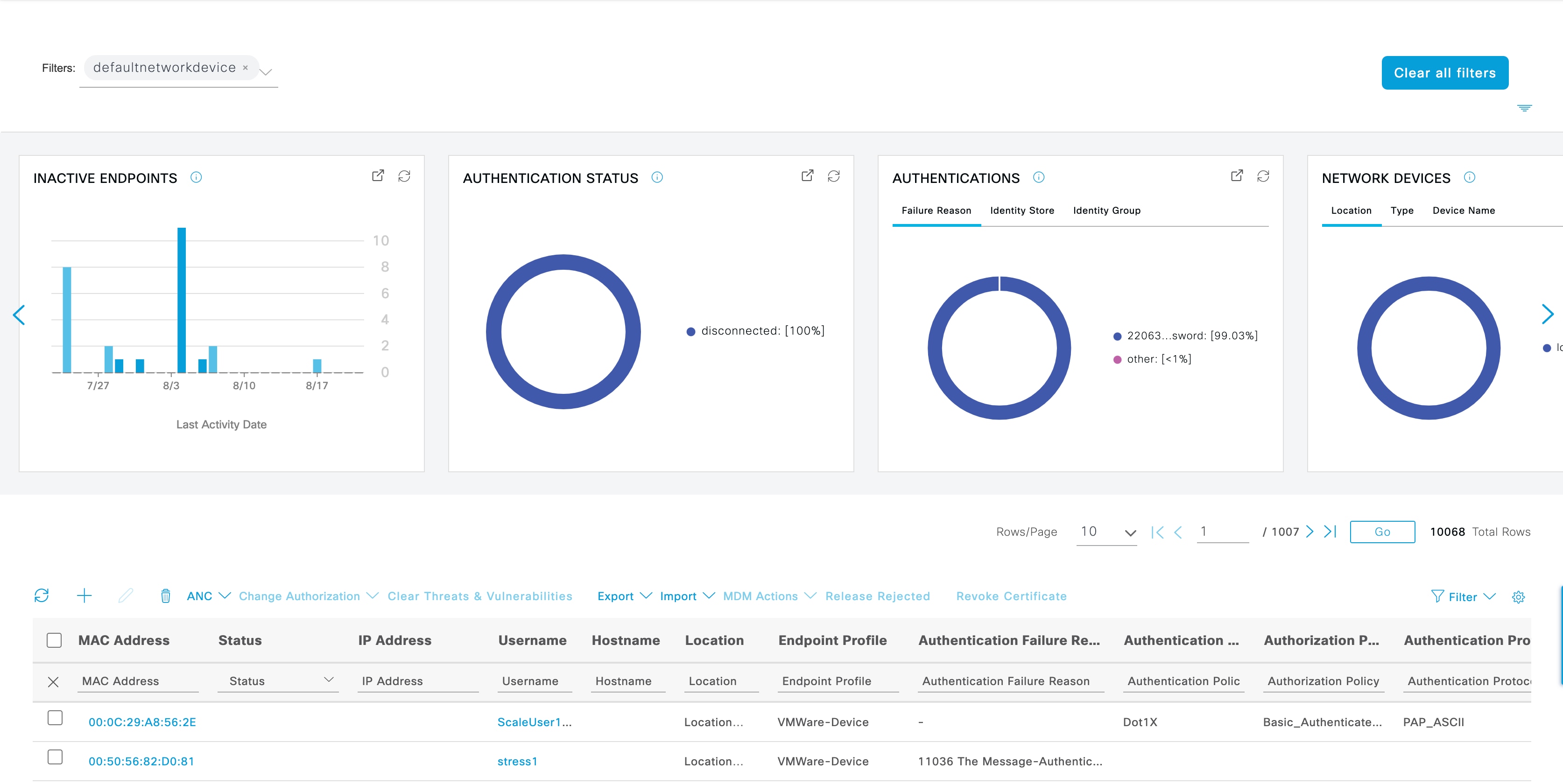
Filter the data further by clicking more sections of the pie charts. You can also use the Filter drop-down list or the gear icon at the top-right corner of the list of data to manage the data displayed.
Save your custom filters.
Create Custom Filters
Create and save user-specific custom filters that are accessible only to you. Other users logging in to Cisco ISE cannot view the custom filters that you create. These custom filters are saved in the Cisco ISE database. You can access them from any computer or browser with which you log in to Cisco ISE.
Procedure
|
Step 1 |
Click Filter and choose Advanced Filter from the drop-down list. |
|
Step 2 |
Specify the search attributes, such as fields, operators, and values from the Filter menus. |
|
Step 3 |
Click + to add more conditions. |
|
Step 4 |
Click Go to display the entries that match the specified attributes. |
|
Step 5 |
Click Save to save the filter. |
|
Step 6 |
Enter a name and click Save. The filter now appears in the Filter drop-down list. |
Filter Data by Conditions Using the Advanced Filter
The Advanced Filter allows you to filter information based on specified conditions, such as, First Name = Mike and User Group = Employee. You can specify more than one condition.
Procedure
|
Step 1 |
Click Filter and choose Advanced Filter drop-down list. |
|
Step 2 |
Specify search the search attributes, such as fields, operators, and values from the filter menus. |
|
Step 3 |
Click + to add more conditions. |
|
Step 4 |
Click Go to view the entries that match the specified attributes. |
Filter Data by Field Attributes Using the Quick Filter
The Quick Filter allows you to enter a value for any of the field attributes displayed in the listing page, refreshes the page, and lists only those records that match your filter criteria.
Procedure
|
Step 1 |
Click Filter and choose Quick Filter from the drop-down list. |
|
Step 2 |
Enter search criteria in one or more of the attribute fields, and the entries that match the specified attributes display automatically. |
Endpoint actions in dashlet views
The toolbar at the top of the list allows you to act on endpoints in the list that you select. Not all actions are enabled for every list. Some actions depend on the feature that is enabled for use. The following list shows two endpoint actions that must be enabled in Cisco ISE before you can use them.
-
Adaptive Network Control Actions
If you enable the Adaptive Network Control service, you can select endpoints in the list and assign or revoke network access. You can also issue a change of authorization.
When you click the pie chart on a home page dashlet, the new window that is displayed contains the options ANC and Change Authorization. Check the check box for the endpoint you want to perform an action on, and choose the necessary action from the drop-down lists of ANC and Change Authorization.
Figure 5. Endpoint Actions in Dashlet Views 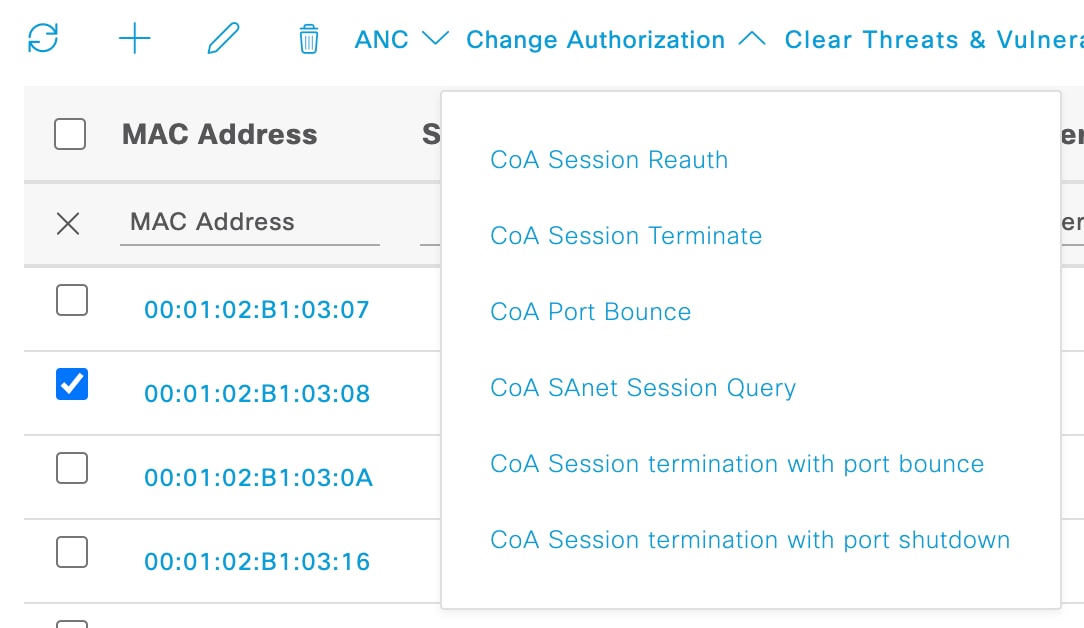
-
MDM Actions
If you connect an MDM server to Cisco ISE, you can perform MDM actions on selected endpoints. Choose the necessary action from the MDM Actions drop-down list.
-
Clear Threats & Vulnerabilities
You can remove threats and vulnerabilities from selected endpoints when applicable.
-
Release Rejected
You have the option to release rejected endpoints when appropriate.
-
Revoke Certificate
You can revoke the certificates of selected endpoints as needed.
-
Export
You can export endpoint data based on your preferences: either selected or filtered endpoints, or all endpoints within your deployment.
-
Import
You can import endpoint data from either a local file or an LDAP directory.
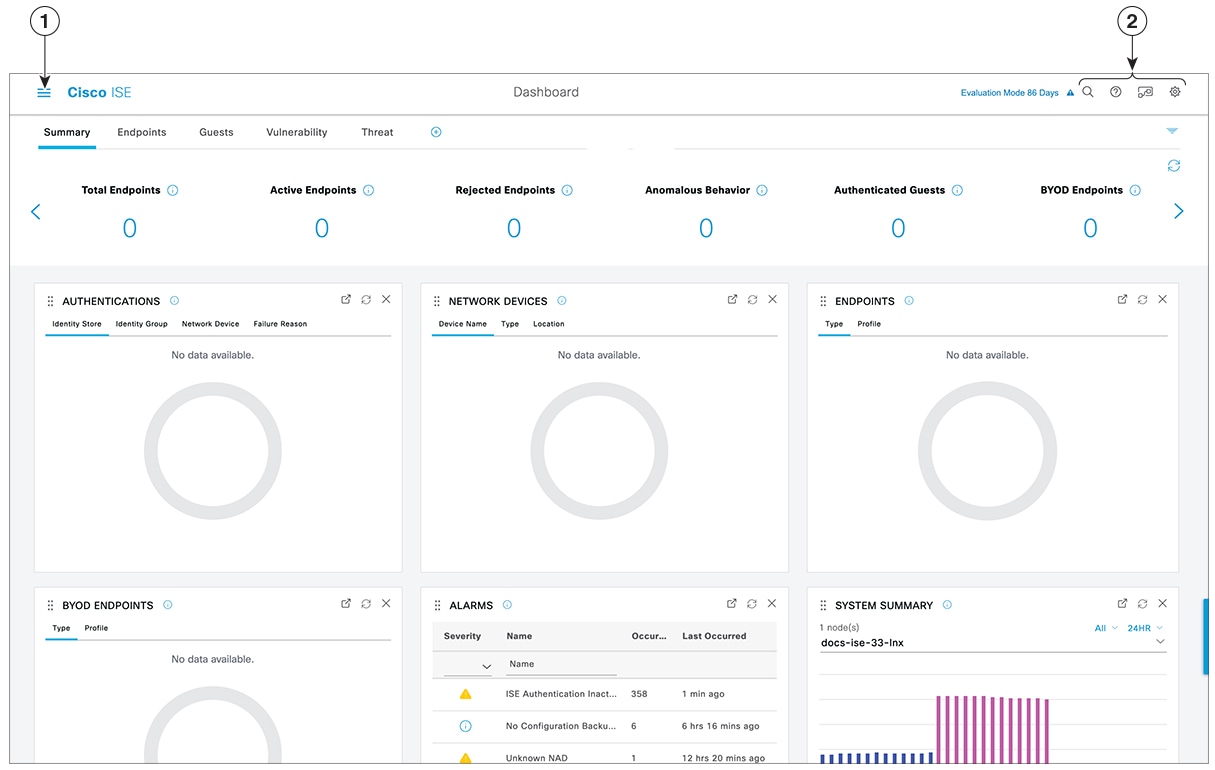
Cisco ISE Dashboard
The Cisco ISE dashboard or home page (click the Menu icon (![]() ) and choose Dashboard) is the landing page that you view after you log in to the Cisco ISE administration portal. The dashboard is a centralized
management console consisting of metric meters along the top of the window, with dashlets below. The default dashboards are
Summary, Endpoints, Guests, Vulnerability, and Threat. See Cisco ISE Home Dashboards.
) and choose Dashboard) is the landing page that you view after you log in to the Cisco ISE administration portal. The dashboard is a centralized
management console consisting of metric meters along the top of the window, with dashlets below. The default dashboards are
Summary, Endpoints, Guests, Vulnerability, and Threat. See Cisco ISE Home Dashboards.
 Note |
You can view this dashboard data only in the Cisco ISE primary PAN portal. |
The dashboard’s real-time data provides an at-a-glance status of the devices and users accessing your network, and an overview of the system's health.
Click the gear icon in the second level menu bar for a drop-down list of dashboard settings. The following table contains descriptions for the dashboard settings options available in the drop-down list:
|
Drop-Down List Option |
Description |
||
|---|---|---|---|
|
Add New Dashboard |
You can have a maximum of 20 dashboards, including the five default dashboards. |
||
|
Rename Dashboard |
(This option is available only for custom dashboards) To rename a dashboard:
|
||
|
Add Dashlet |
To add a dashlet to the home page dashboard:
|
||
|
Export |
You can export the dashboard data as a PDF or a CSV file.
When you export a custom dashboard, the zip file is exported with the same name. For example, if you export a custom dashboard that is named MyDashboard, then the exported file's name is MyDashboard.zip. |
||
|
Layout Template |
You can change the layout of the template in which the dashlets are displayed. To change the layout:
|
||
|
Manage Dashboards |
Click Manage Dashboards and choose one of the following options:
|
You can delete a dashboard that you have created by clicking the close (x) icon next to the corresponding custom dashboard.
 Note |
You cannot rename or delete a default dashboard. |
Each dashlet has a toolbar at the top-right corner where you can perform the following operations:
-
Detach: To view a dashlet in a separate window.
-
Refresh: To refresh a dashlet.
-
Remove: To remove a dashlet from the dashboard.
You can drag and drop the dashlet using the gripper icon that is present at the top-left corner of the dashlet.
The Alarms dashlet contains a quick filter for the Severity column. You can filter alarms by their severity by choosing Critical, Warning, or Info from the Severity drop-down list.





 Feedback
Feedback