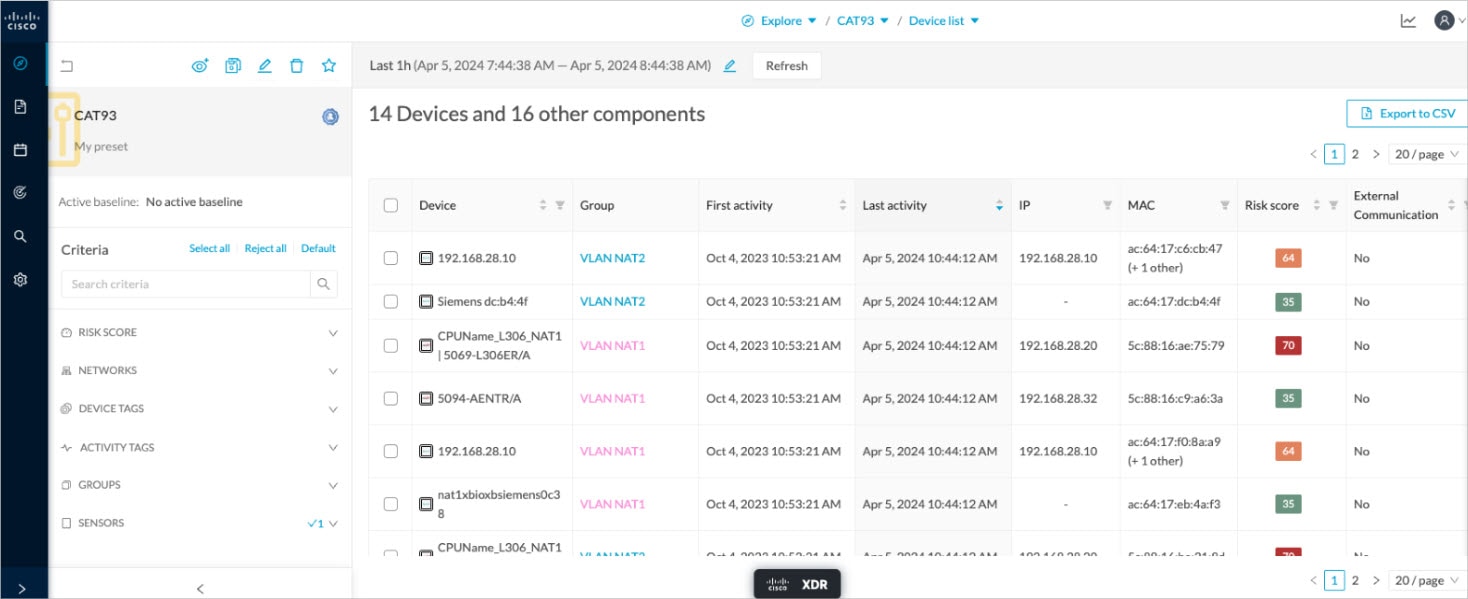
pxGrid
From Platform Exchange Grid page, you can configure ISE pxGrid Cisco Cyber Vision integration.
Cisco Platform Exchange Grid (pxGrid) is an open, scalable data-sharing and threat control platform that allows seamless integration between multivendor identity, network, security and asset management systems.
To access the Platform Exchange Grid page, choose Admin > Integrations > pxGrid from the main menu.
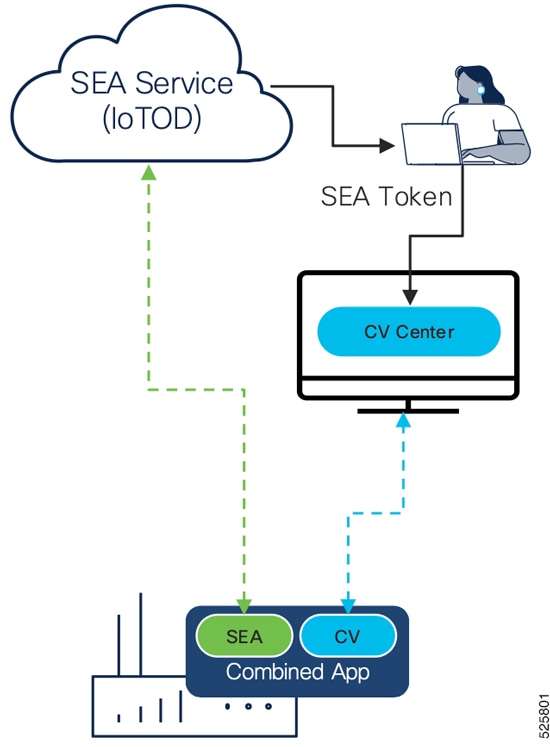
For more information about how to perform this integration, refer to the manual "Integrating Cisco Cyber Vision with Cisco Identity Services Engine (ISE) via pxGrid".


 Feedback
Feedback