This is an example of the one-step installation or converting from bundle mode to install mode:
Router# install add file bootflash:c8kg2be-universalk9.17.15.03.SPA.bin activate commit
May 6 08:35:19.308: %INSTALL-5-INSTALL_START_INFO: R0/0: install_mgr: Started install add_activate_commit bootflash:c8kg2be-universalk9.17.15.03.SPA.bininstall_add_activate_commit: START Tue May 06 08:35:19 UTC 2025
install_add: START Tue May 06 08:35:19 UTC 2025
install_add: Adding IMG
--- Starting initial file syncing ---
Copying bootflash:c8kg2be-universalk9.17.15.03.SPA.bin from R0 to R0
Info: Finished copying to the selected
Finished initial file syncing
--- Starting Add ---
Performing Add on all members
Checking status of Add on [R0]
Add: Passed on [R0]
Image added. Version: 17.15.03.0.5635
Finished Add
install_activate: START Tue May 06 08:36:08 UTC 2025
install_activate: Activating IMG
Following packages shall be activated:
/bootflash/c8kg2be-rpboot.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_nim_xdsl.17.15.03.SPA.pkg
/bootflash/c8kg2be-mono-universalk9.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_sm_1t3e3.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_sm_async.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_ngwic_t1e1.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_nim_async.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_sm_nim_adpt.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_nim_shdsl.17.15.03.SPA.pkg
/bootflash/c8kg2be-firmware_prince.17.15.03.SPA.pkg
This operation may require a reload of the system. Do you want to proceed? [y/n]
May 6 08:36:08.538: %INSTALL-5-INSTALL_START_INFO: R0/0: install_mgr: Started install activate NONEy
--- Starting Activate ---
Performing Activate on all members
[1] Activate package(s) on R0
May 6 08:37:37.284: %INSTALL-5-INSTALL_AUTO_ABORT_TIMER_PROGRESS: R0/0: rollback_timer: Install auto abort timer will expire in 7200 seconds [1] Finished Activate on R0
Checking status of Activate on [R0]
Activate: Passed on [R0]
Finished Activate
--- Starting Commit ---
Performing Commit on all members
[1] Commit package(s) on R0
[1] Finished Commit on R0
Checking status of Commit on [R0]
Commit: Passed on [R0]
Finished Commit operation
SUCCESS: install_add_activate_commit Tue May 06 08:37:59 UTC 2025
Router#
May 6 08:37:59.818: %INSTALL-5-INSTALL_COMPLETED_INFO: R0/0: install_mgr: Completed install add_activate_commitMay 6 0
System integrity status: 0x32042000
Rom image verified correctly
System Bootstrap, Version v17.15(3.1r).s2.cp, RELEASE SOFTWARE
Copyright (c) 1994-2025 by cisco Systems, Inc.
Current image running: Boot ROM0
Last reset cause: LocalSoft
C8375-E-G2 platform with 33554432 Kbytes of main memory
........
boot: reading file c8kg2be-universalk9.17.15.03.SPA.bin
##############################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################################
Performing Signature Verification of OS image...
Image validated
May 6 08:40:59.347: %SYS-4-ROUTER_RUNNING_BUNDLE_BOOT_MODE: R0/0: Warning: Booting with bundle mode will be deprecated in the near future. Migration to install mode is required.
May 6 08:41:21.936: %BOOT-5-OPMODE_LOG: R0/0: binos: System booted in AUTONOMOUS mode
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco IOS Software [IOSXE], c8kg2be Software (ARMV8EL_LINUX_IOSD-UNIVERSALK9-M), Version 17.15.3, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2025 by Cisco Systems, Inc.
Compiled Tue 25-Mar-25 23:37 by mcpre
This software version supports only Smart Licensing as the software licensing mechanism.
Please read the following carefully before proceeding. By downloading,
installing, and/or using any Cisco software product, application, feature,
license, or license key (collectively, the "Software"), you accept and
agree to the following terms. If you do not agree, do not proceed and do not
use this Software.
This Software and its use are governed by Cisco's General Terms and any
relevant supplemental terms found at
https://www.cisco.com/site/us/en/about/legal/contract-experience/index.html.
If you have a negotiated agreement with Cisco that includes this Software, the
terms of that agreement apply as well. In the event of a conflict, the order
of precedence stated in your negotiated agreement controls.
Cisco Software is licensed on a term and/or subscription-basis. The license to
the Software is valid only for the duration of the specified term, or in the
case of a subscription-based license, only so long as all required subscription
payments are current and fully paid-up. While Cisco may provide you
licensing-related alerts, it is your sole responsibility to monitor your usage.
Using Cisco Software without a valid license is not permitted and may result in
fees charged to your account. Cisco reserves the right to terminate access to,
or restrict the functionality of, any Cisco Software, or any features thereof,
that are being used without a valid license.
May 6 08:41:25.397: %FLASH_CHECK-3-DISK_QUOTA: R0/0: flash_check: bootflash quota exceeded [free space is 3172248 kB] - [recommended free space is 5929066 kB] - Please clean up files on bootflash.
cisco C8375-E-G2 (1RU) processor with 11906887K/6147K bytes of memory.
Processor board ID FDO2833M01A
Router operating mode: Autonomous
1 Virtual Ethernet interface
12 2.5 Gigabit Ethernet interfaces
2 Ten Gigabit Ethernet interfaces
32768K bytes of non-volatile configuration memory.
33554432K bytes of physical memory.
20257791K bytes of flash memory at bootflash:.
Warning: When Cisco determines that a fault or defect can be traced to
the use of third-party transceivers installed by a customer or reseller,
then, at Cisco's discretion, Cisco may withhold support under warranty or
a Cisco support program. In the course of providing support for a Cisco
networking product Cisco may require that the end user install Cisco
transceivers if Cisco determines that removing third-party parts will
assist Cisco in diagnosing the cause of a support issue.
WARNING: Command has been added to the configuration using a type 0 password. However, recommended to migrate to strong type-6 encryption
WARNING: ** NOTICE ** The H.323 protocol is no longer supported from IOS-XE release 17.6.1. Please consider using SIP for multimedia applications.
Press RETURN to get started!
*May 6 08:41:23.620: %CRYPTO-5-SELF_TEST_START: Crypto algorithms release (Rel5a), Entropy release (3.4.1)
begin Crypto Module self-tests
*May 6 08:41:23.620: %CRYPTO-5-SELF_TEST_START: Crypto algorithms release (Rel5a), Entropy release (3.4.1)
begin Crypto Module Integrity Test
*May 6 08:41:23.625: %CRYPTO-5-SELF_TEST_END: Crypto Integrity self-test completed successfully
All tests passed.
*May 6 08:41:23.808: %CRYPTO-5-SELF_TEST_END: Crypto Algorithm self-test completed successfully
All tests passed.
*May 6 08:41:24.426: %ISR_THROUGHPUT-6-LEVEL: Throughput level has been set to 3000000 kbps
*May 6 08:41:24.691: %SMART_LIC-6-AGENT_ENABLED: Smart Agent for Licensing is enabled ESG-PM-ACL:[subsys-init] Init ESG-ACL subsystem starting
*May 6 08:41:27.684: ESG-PM-ACL:[subsys-init] Init ESG-ACL platform API reg
*May 6 08:41:27.684: ESG-PM-ACL:[subsys-init] Init ESG-ACL subsystem ended
*May 6 08:41:27.684: NGIOLite module C-NIM-8M success read extended attr from conf file
*May 6 08:41:29.186: %TLSCLIENT-5-TLSCLIENT_IOS: TLS Client is IOS based
*May 6 08:41:29.203: %SPANTREE-5-EXTENDED_SYSID: Extended SysId enabled for type vlan
*May 6 08:41:29.252: %CRYPTO_ENGINE-5-CSDL_COMPLIANCE_ENFORCED: Cisco PSB security compliance is being enforced
*May 6 08:41:29.267: %CUBE-3-LICENSING: SIP trunking (CUBE) licensing is now based on dynamic sessions counting, static license capacity configuration through 'mode border-element license capacity' would be ignored.
*May 6 08:41:29.268: %SIP-5-LICENSING: CUBE license reporting period has been set to the minimum value of 8 hours.
*May 6 08:41:29.286: %VOICE_HA-7-STATUS: CUBE HA-supported platform detected.
*May 6 08:41:30.029: %CRYPTO_SL_TP_LEVELS-6-PLATFORM_BASED_LIC: Platform Based License Support, throughput is un-throttled
*May 6 08:41:30.061: %LINK-3-UPDOWN: Interface EOBC0, changed state to up
*May 6 08:41:30.069: %LINK-3-UPDOWN: Interface Lsmpi0, changed state to up
*May 6 08:41:30.069: %LINEPROTO-5-UPDOWN: Line protocol on Interface LI-Null0, changed state to up
*May 6 08:41:30.069: %LINEPROTO-5-UPDOWN: Line protocol on Interface VoIP-Null0, changed state to up
*May 6 08:41:30.069: %LINK-3-UPDOWN: Interface LIIN0, changed state to up
*May 6 08:41:30.070: %LINK-3-UPDOWN: Interface GigabitEthernet0, changed state to down
*May 6 08:41:30.071: %IOSXE_RP_ALARM-6-INFO: ASSERT CRITICAL GigabitEthernet0 Physical Port Link Down
*May 6 08:41:30.243: %PNP-6-PNP_DISCOVERY_STARTED: PnP Discovery started
*May 6 08:40:41.171: %IOSXE-3-PLATFORM: R0/0: /usr/sbin/updatepcr8d: MPCCE: Failed to read idprom cookie; error code: 100
*May 6 08:40:41.184: %IOSXE-3-PLATFORM: R0/0: /usr/sbin/updatepcr8d: Error logging in to tam device, rc=0x64-TAM_LIB_ERR_MANDATORY_BUS_ENCRYPT_ENABLED
*May 6 08:40:41.184: %IOSXE-3-PLATFORM: R0/0: /usr/sbin/updatepcr8d: Error initializing tam device. PCR8 will not be extended.
*May 6 08:40:46.480: %IOSXE-3-PLATFORM: R0/0: /usr/sbin/updatepcr8d: MPCCE: Failed to read idprom cookie; error code: 100
*May 6 08:40:46.493: %IOSXE-3-PLATFORM: R0/0: /usr/sbin/updatepcr8d: Error logging in to tam device, rc=0x64-TAM_LIB_ERR_MANDATORY_BUS_ENCRYPT_ENABLED
*May 6 08:40:46.493: %IOSXE-3-PLATFORM: R0/0: /usr/sbin/updatepcr8d: Error initializing tam device. PCR8 will not be extended.
*May 6 08:40:59.263: %SERVICES-2-NORESOLVE_ACTIVE: C0/0: cmcc: Error resolving active FRU: BINOS_FRU_RP
*May 6 08:40:59.346: %SYS-4-ROUTER_RUNNING_BUNDLE_BOOT_MODE: R0/0: Warning: Booting with bundle mode will be deprecated in the near future. Migration to install mode is required.
*May 6 08:41:21.935: %BOOT-5-OPMODE_LOG: R0/0: binos: System booted in AUTONOMOUS mode
*May 6 08:41:25.396: %FLASH_CHECK-3-DISK_QUOTA: R0/0: flash_check: bootflash quota exceeded [free space is 3172248 kB] - [recommended free space is 5929066 kB] - Please clean up files on bootflash.
*May 6 08:41:25.952: %CMRP_PFU-6-PEM_INSERTED: R0/0: cmand: Power Supply in slot 0 not operational.
*May 6 08:41:26.077: %CMRP_PFU-6-FANASSY_INSERTED: R0/0: cmand: Fan Assembly is inserted.
*May 6 08:41:30.313: %SYS-5-CONFIG_P: Configured programmatically by process MGMT VRF Process from console as vty0
*May 6 08:41:30.519: %IOSXE_MGMTVRF-6-CREATE_SUCCESS_INFO: Management vrf Mgmt-intf created with ID 1, ipv4 table-id 0x1, ipv6 table-id 0x1E000001
*May 6 08:41:30.519: %SYS-5-CONFIG_P: Configured programmatically by process MGMT VRF Process from console as vty0
*May 6 08:41:30.688: %IOSXE_RP_ALARM-2-PEM: ASSERT CRITICAL Power Supply Module 0 Power Supply Failure
*May 6 08:41:30.688: %IOSXE_RP_ALARM-6-INFO: ASSERT CRITICAL POE Module 0 Power Supply Failure
*May 6 08:41:30.714: %ONEP_BASE-6-SS_ENABLED: ONEP: Service set Base was enabled by Default
*May 6 08:41:31.046: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to down
*May 6 08:41:31.058: %LINEPROTO-5-UPDOWN: Line protocol on Interface EOBC0, changed state to up
*May 6 08:41:31.066: %LINEPROTO-5-UPDOWN: Line protocol on Interface Lsmpi0, changed state to up
*May 6 08:41:31.066: %LINEPROTO-5-UPDOWN: Line protocol on Interface LIIN0, changed state to up
*May 6 08:41:31.066: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0, changed state to down
*May 6 08:41:31.262: %SMART_LIC-6-USAGE_NO_ACK: A Usage report acknowledgement has not been received in the last 0 days.
*May 6 08:41:31.263: %SIP-5-LICENSING: smart license report is not acknowledged.
*May 6 08:41:31.773: %SYS-7-NVRAM_INIT_WAIT_TIME: Waited 0 seconds for NVRAM to be available
*May 6 08:41:31.944: %SYS-6-PRIVCFG_DECRYPT_SUCCESS: Successfully apply the private config file
*May 6 08:41:32.030: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: TP-self-signed-2220840378 created succesfully
*May 6 08:41:32.031: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: SLA-TrustPoint created succesfully
*May 6 08:41:32.034: %PKI-3-KEY_CMP_MISMATCH: Key in the certificate and stored key does not match for Trustpoint-TP-self-signed-2220840378.
*May 6 08:41:32.041: %AAA-6-USERNAME_CONFIGURATION: user with username: admin configured
*May 6 08:41:32.041: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, recommended to migrate to strong type-6 encryption
*May 6 08:41:32.041: %AAA-6-USER_PRIVILEGE_UPDATE: username: admin privilege updated with priv-15
*May 6 08:41:32.259: %SYS-5-CONFIG_I: Configured from memory by console
*May 6 08:41:32.268: %IOSXE_OIR-6-REMSPA: SPA removed from subslot 0/0, interfaces disabled
*May 6 08:41:32.268: %IOSXE_OIR-6-REMSPA: SPA removed from subslot 0/1, interfaces disabled
*May 6 08:41:32.275: %SPA_OIR-6-OFFLINECARD: SPA (4M-2xSFP+) offline in subslot 0/0
*May 6 08:41:32.278: %SPA_OIR-6-OFFLINECARD: SPA (C-NIM-8M) offline in subslot 0/1
*May 6 08:41:32.306: %IOSXE_RP_ALARM-2-ESP: ASSERT CRITICAL module R0 No Working ESP
*May 6 08:41:32.309: %IOSXE_OIR-6-INSCARD: Card (fp) inserted in slot F0
*May 6 08:41:32.309: %IOSXE_OIR-6-INSCARD: Card (cc) inserted in slot 0
*May 6 08:41:32.309: %IOSXE_OIR-6-INSCARD: Card (cc) inserted in slot 1
*May 6 08:41:32.325: %CRYPTO-5-SELF_TEST_START: Crypto algorithms release (Rel5a), Entropy release (3.4.1)
begin Crypto Module self-tests
*May 6 08:41:32.329: %CRYPTO-5-SELF_TEST_END: Crypto Algorithm self-test completed successfully
All tests passed.
*May 6 08:41:32.712: %UICFGEXP-6-SERVER_NOTIFIED_START: R0/0: psd: Server iox has been notified to start
*May 6 08:41:33.077: %SYS-5-RESTART: System restarted --
Cisco IOS Software [IOSXE], c8kg2be Software (ARMV8EL_LINUX_IOSD-UNIVERSALK9-M), Version 17.15.3, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2025 by Cisco Systems, Inc.
Compiled Tue 25-Mar-25 23:37 by mcpre
*May 6 08:41:33.084: %SNMP-5-COLDSTART: SNMP agent on host Router is undergoing a cold start
*May 6 08:41:33.084: %SYS-5-CONFIG_I: Configured from console by console
*May 6 08:41:33.759: %IOSXE_OIR-6-ONLINECARD: Card (fp) online in slot F0
*May 6 08:41:34.091: %SYS-6-BOOTTIME: Time taken to reboot after reload = 215 seconds
*May 6 08:41:35.051: %LINEPROTO-5-UPDOWN: Line protocol on Interface VirtualPortGroup0, changed state to up
*May 6 08:41:35.063: %LINEPROTO-5-UPDOWN: Line protocol on Interface VirtualPortGroup1, changed state to up
*May 6 08:41:35.063: %LINEPROTO-5-UPDOWN: Line protocol on Interface VirtualPortGroup10, changed state to up
*May 6 08:41:38.437: %PNP-6-PNP_BEST_UDI_UPDATE: Best UDI [PID:C8375-E-G2,VID:V01,SN:FDO2833M01A] identified via (entity-mibs)
*May 6 08:41:38.437: %PNP-6-PNP_CDP_UPDATE: Device UDI [PID:C8375-E-G2,VID:V01,SN:FDO2833M01A] identified for CDP
*May 6 08:41:38.437: %PNP-6-PNP_DISCOVERY_STOPPED: PnP Discovery stopped (Startup Config Present)
*May 6 08:41:39.699: %LINK-3-UPDOWN: Interface GigabitEthernet0, changed state to up
*May 6 08:41:40.707: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0, changed state to up
*May 6 08:41:42.333: %SYS-5-CONFIG_P: Configured programmatically by process EPM CREATE DEFAULT CWA URL ACL from console as console
*May 6 08:41:46.197: %IOSXE_OIR-6-ONLINECARD: Card (cc) online in slot 0
*May 6 08:41:46.230: %IOSXE_OIR-6-INSSPA: SPA inserted in subslot 0/0
*May 6 08:41:46.587: %IOSXE_OIR-6-ONLINECARD: Card (cc) online in slot 1
*May 6 08:41:47.126: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
*May 6 08:41:47.126: %CRYPTO-6-GDOI_ON_OFF: GDOI is OFF
*May 6 08:41:48.779: %IOSXE_OIR-6-INSSPA: SPA inserted in subslot 0/1
*May 6 08:41:49.452: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
*May 6 08:41:49.452: %CRYPTO-6-GDOI_ON_OFF: GDOI is OFF
*May 6 08:41:49.571: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: CISCO_IDEVID_SUDI created succesfully
*May 6 08:41:49.573: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named CISCO_IDEVID_SUDI has been generated or imported by pki-sudi
*May 6 08:41:49.609: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: CISCO_IDEVID_SUDI0 created succesfully
*May 6 08:41:49.610: %PKI-2-NON_AUTHORITATIVE_CLOCK: PKI functions can not be initialized until an authoritative time source, like NTP, can be obtained.
*May 6 08:41:53.146: %IOX-3-PD_PARTITION_CREATE: R0/0: run_ioxn_caf: IOX may take upto 3 mins to be ready. Wait for iox to be ready before installing the apps
*May 6 08:41:53.429: %IOX-3-PD_PARTITION_CREATE: R0/0: run_ioxn_caf: Successfully allocated 4.0G in flash for hosting ApplicationsNGIOLite module C-NIM-8M success read extended attr from conf file
*May 6 08:42:15.679: %SPA_OIR-6-ONLINECARD: SPA (C-NIM-8M) online in subslot 0/1
*May 6 08:42:16.292: %ENVIRONMENTAL-6-NOTICE: V: PEM Out, Location: P0, State: Minor_Low, Reading: 0 mV
*May 6 08:42:20.701: %ONEP_BASE-3-AUTHEN_ERR: [Element]: Authentication/authorization failed. Application (utd_snort-utd): Username (*INVALID*)
*May 6 08:42:22.179: %TRANSCEIVER-6-INSERTED: C0/0: iomd: transceiver module inserted in Te0/0/4
*May 6 08:42:22.255: %TRANSCEIVER-6-INSERTED: C0/0: iomd: transceiver module inserted in Te0/0/5
*May 6 08:42:22.643: %LINK-3-UPDOWN: Interface TwoGigabitEthernet0/1/6, changed state to up
*May 6 08:42:23.345: %SPA_OIR-6-ONLINECARD: SPA (4M-2xSFP+) online in subslot 0/0
*May 6 08:42:23.644: %LINEPROTO-5-UPDOWN: Line protocol on Interface TwoGigabitEthernet0/1/6, changed state to up
*May 6 08:42:28.999: %LINK-3-UPDOWN: Interface TenGigabitEthernet0/0/4, changed state to up
*May 6 08:42:29.011: %LINK-3-UPDOWN: Interface TenGigabitEthernet0/0/5, changed state to up
*May 6 08:42:29.975: %LINK-3-UPDOWN: Interface TwoGigabitEthernet0/0/0, changed state to up
*May 6 08:42:30.004: %LINEPROTO-5-UPDOWN: Line protocol on Interface TenGigabitEthernet0/0/4, changed state to up
*May 6 08:42:30.010: %LINEPROTO-5-UPDOWN: Line protocol on Interface TenGigabitEthernet0/0/5, changed state to up
*May 6 08:42:29.901: %IM-6-IOX_INST_INFO: R0/0: ioxman: IOX SERVICE guestshell LOG: Guestshell is up at 04/06/2025 08:42:29
*May 6 08:42:30.974: %LINK-3-UPDOWN: Interface TwoGigabitEthernet0/0/1, changed state to up
*May 6 08:42:30.976: %LINEPROTO-5-UPDOWN: Line protocol on Interface TwoGigabitEthernet0/0/0, changed state to up
*May 6 08:42:31.975: %LINEPROTO-5-UPDOWN: Line protocol on Interface TwoGigabitEthernet0/0/1, changed state to up
*May 6 08:42:31.983: %LINK-3-UPDOWN: Interface TwoGigabitEthernet0/0/3, changed state to up
*May 6 08:42:32.644: %LINK-3-UPDOWN: Interface TwoGigabitEthernet0/1/7, changed state to up
*May 6 08:42:32.366: %CMRP-5-CHASSIS_MONITOR_BOOT_TIME_PRINT: R0/0: cmand: Card F0 took 59 secs to boot
*May 6 08:42:32.367: %CMRP-5-CHASSIS_MONITOR_BOOT_TIME_PRINT: R0/0: cmand: Card 0 took 54 secs to boot
*May 6 08:42:32.367: %CMRP-5-CHASSIS_MONITOR_BOOT_TIME_PRINT: R0/0: cmand: Card 1 took 54 secs to boot
*May 6 08:42:32.984: %LINEPROTO-5-UPDOWN: Line protocol on Interface TwoGigabitEthernet0/0/3, changed state to up
*May 6 08:42:33.642: %LINEPROTO-5-UPDOWN: Line protocol on Interface TwoGigabitEthernet0/1/7, changed state to up
*May 6 08:42:34.003: ALL modules are online!
*May 6 08:42:34.765: %IM-6-IOX_ENABLEMENT: R0/0: ioxman: IOX is ready.
*May 6 08:42:34.766: %IM-6-START_MSG: R0/0: ioxman: app-hosting: Start succeeded: utd is started Current is in RUNNING
May 6 08:42:36.712: %PKI-6-AUTHORITATIVE_CLOCK: The system clock has been set.
May 6 08:42:38.080: %SMART_LIC-6-REPORTING_REQUIRED: A Usage report acknowledgement will be required in 0 days.
May 6 08:42:38.081: ALL modules are online!
May 6 08:42:41.695: %SMART_LIC-6-REPORTING_REQUIRED: A Usage report acknowledgement will be required in 0 days.
Router>
May 6 08:42:51.407: %ONEP_BASE-6-CONNECT: [Element]: ONEP session Application:utd_snort Host:utd ID:3545 User: has connected.
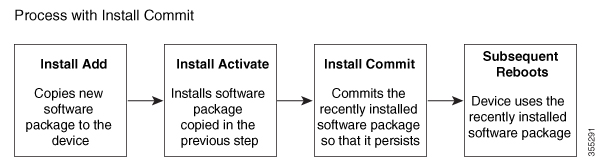
This is an example of the three-step installation:
Router#install add file bootflash:c8kg2be-universalk9.17.15.03a.SPA.bin
install_add: START Wed May 21 09:03:39 UTC 2025
install_add: Adding IMG
% UTD: Received appnav notification from LXC for (src 192.0.2.5, dst 192.0.2.6)
% UTD successfully registered with Appnav (src 192.0.2.5, dst 192.0.2.6)
% UTD redirect interface set to VirtualPortGroup1 internally
--- Starting initial file syncing ---
Copying bootflash:c8kg2be-universalk9.17.15.03a.SPA.bin from R0 to R0
Info: Finished copying to the selected
Finished initial file syncing
--- Starting Add ---
Performing Add on all members
Checking status of Add on [R0]
Add: Passed on [R0]
Image added. Version: 17.15.03a.0.176
Finished Add
SUCCESS: install_add /bootflash/c8kg2be-universalk9.17.15.03a.SPA.bin Wed May 21 09:04:43 UTC 2025
Router#show install log
[0|install_op_boot]: START Wed May 21 09:02:03 Universal 2025
[0|install_op_boot(INFO, )]: Mount IMG INI state base image
[0|install_op_boot]: END SUCCESS Wed May 21 09:02:03 Universal 2025
[0|install_op_boot(INFO, )]: cleanup_trap remote_invocation 0 operation install_op_boot .. 0 .. 0
[remote|COMP_CHECK]: START Wed May 21 09:04:42 UTC 2025
[remote|COMP_CHECK]: END FAILED exit(1) Wed May 21 09:04:43 UTC 2025
Router#
Router#install activate
install_activate: START Wed May 21 09:07:21 UTC 2025
install_activate: Activating IMG
Following packages shall be activated:
/bootflash/c8kg2be-rpboot.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_sm_nim_adpt.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_nim_async.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_sm_async.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_prince.17.15.03a.SPA.pkg
/bootflash/c8kg2be-mono-universalk9.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_nim_shdsl.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_ngwic_t1e1.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_sm_1t3e3.17.15.03a.SPA.pkg
/bootflash/c8kg2be-firmware_nim_xdsl.17.15.03a.SPA.pkg
This operation may require a reload of the system. Do you want to proceed? [y/n]y
--- Starting Activate ---
Performing Activate on all members
[1] Activate package(s) on R0
[1] Finished Activate on R0
Checking status of Activate on [R0]
Activate: Passed on [R0]
Finished Activate
SUCCESS: install_activate Wed May 21 09:09:31 UTC 2025
Router#May 21 09:
System integrity status: 0x32042000
Rom image verified correctly
System Bootstrap, Version v17.15(3.1r).s2.cp, RELEASE SOFTWARE
Copyright (c) 1994-2025 by cisco Systems, Inc.
Current image running: Boot ROM0
Last reset cause: LocalSoft
C8375-E-G2 platform with 33554432 Kbytes of main memory
........
boot: reading file packages.conf
#
##########################################################
Performing Signature Verification of OS image...
Image validated
May 21 09:11:47.581: %BOOT-5-OPMODE_LOG: R0/0: binos: System booted in AUTONOMOUS mode
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco IOS Software [IOSXE], c8kg2be Software (ARMV8EL_LINUX_IOSD-UNIVERSALK9-M), Version 17.15.3a, RELEASE SOFTWARE (fc4)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2025 by Cisco Systems, Inc.
Compiled Fri 02-May-25 11:27 by mcpre
This software version supports only Smart Licensing as the software licensing mechanism.
Please read the following carefully before proceeding. By downloading,
installing, and/or using any Cisco software product, application, feature,
license, or license key (collectively, the "Software"), you accept and
agree to the following terms. If you do not agree, do not proceed and do not
use this Software.
This Software and its use are governed by Cisco's General Terms and any
relevant supplemental terms found at
https://www.cisco.com/site/us/en/about/legal/contract-experience/index.html.
If you have a negotiated agreement with Cisco that includes this Software, the
terms of that agreement apply as well. In the event of a conflict, the order
of precedence stated in your negotiated agreement controls.
Cisco Software is licensed on a term and/or subscription-basis. The license to
the Software is valid only for the duration of the specified term, or in the
case of a subscription-based license, only so long as all required subscription
payments are current and fully paid-up. While Cisco may provide you
licensing-related alerts, it is your sole responsibility to monitor your usage.
Using Cisco Software without a valid license is not permitted and may result in
fees charged to your account. Cisco reserves the right to terminate access to,
or restrict the functionality of, any Cisco Software, or any features thereof,
that are being used without a valid license.
May 21 09:11:51.161: %FLASH_CHECK-3-DISK_QUOTA: R0/0: flash_check: bootflash quota exceeded [free space is 1111072 kB] - [recommended free space is 5929066 kB] - Please clean up files on bootflash.
cisco C8375-E-G2 (1RU) processor with 11906881K/6147K bytes of memory.
Processor board ID FDO2833M01A
Router operating mode: Autonomous
1 Virtual Ethernet interface
12 2.5 Gigabit Ethernet interfaces
2 Ten Gigabit Ethernet interfaces
32768K bytes of non-volatile configuration memory.
33554432K bytes of physical memory.
20257791K bytes of flash memory at bootflash:.
Warning: When Cisco determines that a fault or defect can be traced to
the use of third-party transceivers installed by a customer or reseller,
then, at Cisco's discretion, Cisco may withhold support under warranty or
a Cisco support program. In the course of providing support for a Cisco
networking product Cisco may require that the end user install Cisco
transceivers if Cisco determines that removing third-party parts will
assist Cisco in diagnosing the cause of a support issue.
The process for the command is not responding or is otherwise unavailable
WARNING: Command has been added to the configuration using a type 0 password. However, recommended to migrate to strong type-6 encryption
WARNING: ** NOTICE ** The H.323 protocol is no longer supported from IOS-XE release 17.6.1. Please consider using SIP for multimedia applications.
Press RETURN to get started!
% UTD: Received appnav notification from LXC for (src 192.0.2.5, dst 192.0.2.6)
% UTD successfully registered with Appnav (src 192.0.2.5, dst 192.0.2.6)
% UTD redirect interface set to VirtualPortGroup1 internally
Router>
Router>en
Router#
Router#install commit
install_commit: START Wed May 21 09:22:28 UTC 2025
--- Starting Commit ---
Performing Commit on all members
[1] Commit packages(s) on R0
[1] Finished Commit packages(s) on R0
Checking status of Commit on [R0]
Commit: Passed on [R0]
Finished Commit operation
SUCCESS: install_commit Wed May 21 09:22:31 UTC 2025
These are sample outputs for show commands:
show install log
Device# show install log
[0|install_op_boot]: START Thu Oct 28 22:09:29 Universal 2021
[0|install_op_boot(INFO, )]: Mount IMG INI state base image
[0|install_op_boot]: END SUCCESS Thu Oct 28 22:09:30 Universal 2021
show install summary
Device# show install summary
[ R0 ] Installed Package(s) Information:
State (St): I - Inactive, U - Activated & Uncommitted,
C - Activated & Committed, D - Deactivated & Uncommitted
--------------------------------------------------------------------------------
Type St Filename/Version
--------------------------------------------------------------------------------
IMG C 17.15.03a.0.176 --------------------------------------------------------------------------------
Auto abort timer: inactive
--------------------------------------------------------------------------------
show install package
filesystem: filename
Device# show install package bootflash:c8kg2be-universalk9.17.15.03a.SPA.bin
Package: c8kg2be-universalk9.17.15.03a.SPA.bin
Size: 953231736
Timestamp:
Canonical path: /bootflash/c8kg2be-universalk9.17.15.03a.SPA.bin
Raw disk-file SHA1sum:
d358592ccd2dd626889ef091401d06fae5458ff1
Header size: 1084 bytes
Package type: 30000
Package flags: 0
Header version: 3
Internal package information:
Name: rp_super
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: arm64
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: universalk9
Build: 17.15.03a
CardTypes:
Package is bootable from media and tftp.
Package contents:
Package: c8kg2be-firmware_prince.17.15.03a.SPA.pkg
Size: 10444800
Timestamp:
Raw disk-file SHA1sum:
fa82bed30d349686d1d9700892076a3d66375698
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_prince
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_prince
Build: 17.15.03a
CardTypes:
Package is not bootable.
Package: c8kg2be-mono-universalk9.17.15.03a.SPA.pkg
Size: 891244544
Timestamp:
Raw disk-file SHA1sum:
af7ba58491731d788d9f4528d74b5bfef9dfc7f2
Header size: 4096 bytes
Package type: 30000
Package flags: 0
Header version: 3
Internal package information:
Name: mono
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: arm64
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: mono-universalk9
Build: 17.15.03a
CardTypes:
Package is bootable from media and tftp.
Package contents:
Package: c8kg2be-firmware_nim_xdsl.17.15.03a.SPA.pkg
Size: 5677056
Timestamp:
Raw disk-file SHA1sum:
4af7a8764651253c73c7fadebeba6f3a8f0a133d
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_nim_xdsl
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_nim_xdsl
Build: 17.15.03a
CardTypes:
Package is not bootable.
Package: c8kg2be-firmware_sm_1t3e3.17.15.03a.SPA.pkg
Size: 13889536
Timestamp:
Raw disk-file SHA1sum:
526aa41ccd8398e7691d316ca24289801e0417a8
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_sm_1t3e3
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_sm_1t3e3
Build: 17.15.03a
CardTypes:
Package is not bootable.
Package: c8kg2be-firmware_sm_async.17.15.03a.SPA.pkg
Size: 14671872
Timestamp:
Raw disk-file SHA1sum:
7c7f4c06da5b3b0e1db879e074998130db22298f
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_sm_async
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_sm_async
Build: 17.15.03a
CardTypes:
Package is not bootable.
Package: c8kg2be-firmware_nim_async.17.15.03a.SPA.pkg
Size: 13254656
Timestamp:
Raw disk-file SHA1sum:
27132c3a41c79991d1f71488ad325ad05cc7b0bb
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_nim_async
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_nim_async
Build: 17.15.03a
CardTypes:
Package is not bootable.
Package: c8kg2be-firmware_nim_shdsl.17.15.03a.SPA.pkg
Size: 11804672
Timestamp:
Raw disk-file SHA1sum:
51da21dffb39d2ef6b266b7ffab083b3fb339651
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_nim_shdsl
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_nim_shdsl
Build: 17.15.03a
CardTypes:
Package is not bootable.
Package: c8kg2be-firmware_ngwic_t1e1.17.15.03a.SPA.pkg
Size: 11956224
Timestamp:
Raw disk-file SHA1sum:
19376efa2ed616672c0d488b628a768e262bd8e6
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_ngwic_t1e1
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_ngwic_t1e1
Build: 17.15.03a
CardTypes:
Package is not bootable.
Package: c8kg2be-firmware_sm_nim_adpt.17.15.03a.SPA.pkg
Size: 204800
Timestamp:
Raw disk-file SHA1sum:
b3a7ddd80df900d6217bb8db36ff8bdbc6241fa3
Header size: 4096 bytes
Package type: 40000
Package flags: 0
Header version: 3
Internal package information:
Name: firmware_sm_nim_adpt
BuildTime: 2025-05-02_11.57
ReleaseDate: 2025-05-02_16.50
BootArchitecture: none
RouteProcessor: mirabile
Platform: C8KG2BE
User: mcpre
PackageName: firmware_sm_nim_adpt
Build: 17.15.03a
CardTypes:
Package is not bootable.
show install active
Device# show install active
[ R0 ] Active Package(s) Information:
State (St): I - Inactive, U - Activated & Uncommitted,
C - Activated & Committed, D - Deactivated & Uncommitted
--------------------------------------------------------------------------------
Type St Filename/Version
--------------------------------------------------------------------------------
IMG C 17.15.03a.0.158
--------------------------------------------------------------------------------
Auto abort timer: inactive
--------------------------------------------------------------------------------
show install inactive
Device# show install inactive
[ R0 ] Inactive Package(s) Information:
State (St): I - Inactive, U - Activated & Uncommitted,
C - Activated & Committed, D - Deactivated & Uncommitted
-------------------------------------------------------------------------------
Type St Filename/Version
-------------------------------------------------------------------------------
No Inactive Packages
show install committed
Device# show install committed
[ R0 ] Committed Package(s) Information:
State (St): I - Inactive, U - Activated & Uncommitted,
C - Activated & Committed, D - Deactivated & Uncommitted
--------------------------------------------------------------------------------
Type St Filename/Version
--------------------------------------------------------------------------------
IMG C 17.15.03a.0.158
-------------------------------------------------------------------------------- --------------------------------------------------------------------------------
Auto abort timer: inactive
--------------------------------------------------------------------------------
show install uncommitted
Device# show install uncommitted
[ R0 ] Uncommitted Package(s) Information:
State (St): I - Inactive, U - Activated & Uncommitted,
C - Activated & Committed, D - Deactivated & Uncommitted
--------------------------------------------------------------------
Type St Filename/Version
--------------------------------------------------------------------
No Uncommitted Packages

 Feedback
Feedback