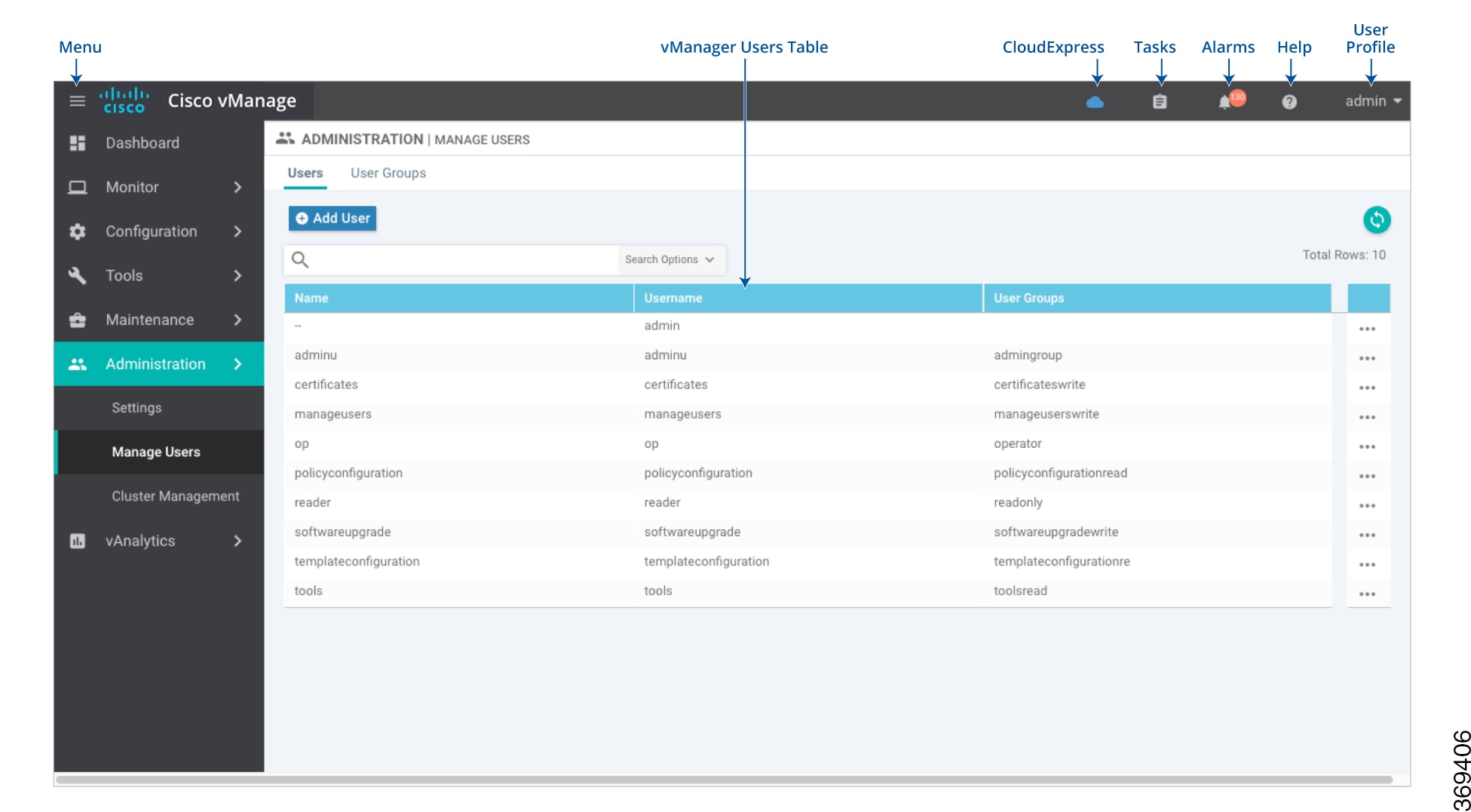
Basic Settings for Cisco vManage
The System template is used to configure system-level Cisco vManage workflows.
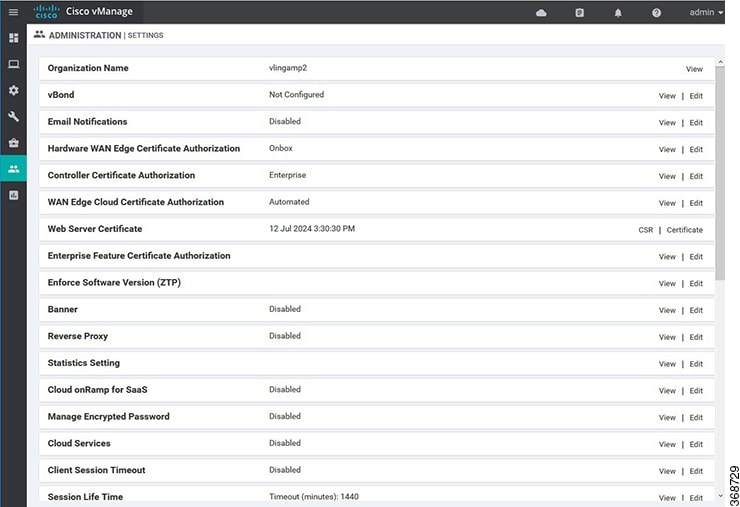
Use the Settings screen to view the current settings and configure the setting for Cisco vManage parameters, including the organization name, vBond orchestrator's DNS name or IP address, certificate settings, and statistics collection.
The current setting for each item is displayed in the bar for each item, immediately following the name.
Configure Organization Name
Before you can generate a Certificate Signing Request (CSR), you must configure the name of your organization. The organization name is included in the CSR.
In public key infrastructure (PKI) systems, a CSR is sent to a certificate authority to apply for a digital identity certificate.
To configure the organization name:
-
Click the Edit button to the right of the Organization Name bar.
-
In the Organization Name field, enter the name of your organization. The organization name must be identical to the name that is configured on the vBond orchestrator.
-
In the Confirm Organization Name field, re-enter and confirm your organization name.
-
Click Save.
Note that once the control connections are up and running, the organization name bar is no longer editable.
Configure Cisco vBond DNS Name or IP Address
-
Click the Edit button to the right of the vBond bar.
-
In the vBond DNS/IP Address: Port field, enter the DNS name that points to the vBond orchestrator or the IP address of the Cisco vBond orchestrator and the port number to use to connect to it.
-
Click Save.
Enable Email Notifications
You can configure the Cisco vManage to send email notifications when alarms occur on devices in the overlay network. First configure the SMTP and email recipient parameters on this screen:
-
Click the Edit button to the right of the Email Notifications bar.
-
In the Enable Email Notifications field, click Enabled.
-
Select the security level for sending the email notifications. The security level can be none, SSL, or TLS.
-
In the SMTP Server field, enter the name or IP address of the SMTP server to receive the email notifications.
-
In the SMTP port field, enter the SMTP port number. For no security, the default port is 25; for SSL it is 465; and for TLS it is 587.
-
In the From Address field, enter the full email address to include as the sender in email notifications.
-
In the Reply To address, enter the full email address to include in the Reply-To field of the email. This address can be a noreply address, such as noreply@cisco.com.
-
To enable SMTP authentication to the SMTP server, click Use SMTP Authentication. Enter the username and password to use for SMTP authentication. The default user email suffix is appended to the username. The password that you type is hidden.
-
Click Save.
Configure alarms that trigger emails by clicking the Email Notifications button on the screen.
Configure Controller Certificate Authorization Settings
Signed certificates are used to authenticate devices in the overlay network. Once authenticated, devices can establish secure sessions between each other. It is from the Cisco vManage that you generate these certificates and install them on the controller devices—Cisco vBond orchestrators,Cisco vManage, and Cisco vSmart controllers. You can use certificates signed by Symantec, or you can use enterprise root certificates.
The controller certification authorization settings establish how the certification generation for all controller devices will be done. They do not generate the certificates.
You need to select the certificate-generation method only once. The method you select is automatically used each time you add a device to the overlay network.
To have the Symantec signing server automatically generate, sign, and install certificates on each controller device:
-
Click the Edit button to the right of the Controller Certificate Authorization bar.
-
Click Symantec Automated (Recommended). This is the recommended method for handling controller signed certificates.
-
In the Confirm Certificate Authorization Change popup, click Proceed to confirm that you wish to have the Symantec signing server automatically generate, sign, and install certificates on each controller device.
-
Enter the first and last name of the requestor of the certificate.
-
Enter the email address of the requestor of the certificate. This address is required because the signed certificate and a confirmation email are sent to the requestor via email; they are also made available though the customer portal.
-
Specify the validity period for the certificate. It can be 1, 2, or 3 years.
-
Enter a challenge phrase.The challenge phrase is your certificate password and is required when you renew or revoke a certificate.
-
Confirm your challenge phrase.
-
In the Certificate Retrieve Interval field, specify how often the Cisco vManage server checks if the Symantec signing server has sent the certificate.
-
Click Save.
To manually install certificates that the Symantec signing server has generated and signed:
-
Click the Edit button to the right of the Controller Certificate Authorization bar.
-
Click Symantec Manual.
-
In the Confirm Certificate Authorization Change popup, click Proceed to manually install certificates that the Symantec signing server has generated and signed.
-
Click Save.
To use enterprise root certificates:
-
Click the Edit button to the right of the Controller Certificate Authorization bar.
-
Click Enterprise Root Certificate.
-
In the Confirm Certificate Authorization Change popup, click Proceed to confirm that you wish to use enterprise root certificates.
-
In the Certificate box, either paste the certificate, or click Select a file and upload a file that contains the enterprise root certificate.
-
By default, the enterprise root certificate has the following properties: To view this information, issue the show certificate signing-request decoded command on a controller device, and check the output in the Subject line. For example:
-
Country: United States
-
State: California
-
City: San Jose
-
Organizational unit: ENB
-
Organization: CISCO
-
Domain Name: cisco.com
-
Email: cisco-cloudops-sdwan@cisco.com
vSmart# show certificate signing-request decoded ... Subject: C=US, ST=California, L=San Jose, OU=ENB, O=CISCO, CN=vsmart-uuid .cisco.com/emailAddress=cisco-cloudops-sdwan@cisco.com ...-
Click Set CSR Properties.
-
Enter the domain name to include in the CSR. This domain name is appended to the certificate number (CN).
-
Enter the organizational unit (OU) to include in the CSR.
-
Enter the organization (O) to include in the CSR.
-
Enter the city (L), state (ST), and two-letter country code (C) to include in the CSR.
-
Enter the email address (emailAddress) of the certificate requestor.
-
Specify the validity period for the certificate. It can be 1, 2, or 3 years.
-
-
Click Import & Save.
Enforce Software Version on Devices
If you are using the Cisco SD-WAN hosted service, you can enforce a version of the Cisco SD-WAN software to run on a router when it first joins the overlay network. To do so:
-
Ensure that the software image for the desired device software version is present in the vManage software image repository:
-
In Cisco vManage, select the screen.
The Software Repository screen opens and displays a table of software images. If the desired software image is present in the repository, continue with Step 2.
-
If you need to add a software image, click Add New Software.
-
Select the location from which to download the software images, either Cisco vManage, Remote Server, or Remote Server - vManage.
-
Select an x86-based or a MIPS-based software image.
-
Click Add to play the image in the repository.
-
-
In the screen, click the Edit button to the right of the Enforce Software Version (ZTP) bar.
-
In the Enforce Software Version field, click Enabled.
-
From the Version drop-down, select the version of the software to enforce on the device when they join the network.
-
Click Save.
If you enable this feature on the Cisco vManage, any device joining the network is configured with the version of the software specified in the Enforce Software Version field regardless of whether the device was running a higher or lower version of Cisco SD-WAN software.
Banner
Use the Banner template for Cisco vBond Orchestrators, Cisco vManages, Cisco vSmart Controllers, Cisco vEdge devices, and Cisco IOS XE SD-WAN devices.
You can configure two different banner text strings, one to be displayed before the CLI login prompt on a Cisco SD-WAN device and the other to be displayed after a successful login to the device.
-
To configure the banner text for login screens using Cisco vManage templates, create a Banner feature template to configure PIM parameters, as described in this topic.
-
To configure a login banner for the Cisco vManage system, go to .
Configure a Banner
-
In Cisco vManage, select the screen.
-
In the Device tab, click Create Template.
-
From the Create Template drop-down, select From Feature Template.
-
From the Device Model drop-down, select the type of device for which you are creating the template.
-
Click the Additional Templates tab located directly beneath the Description field, or scroll to the Additional Templates section.
-
From the Banner drop-down, click Create Template. The Banner template form is displayed. The top of the form contains fields for naming the template, and the bottom contains fields for defining Banner parameters. 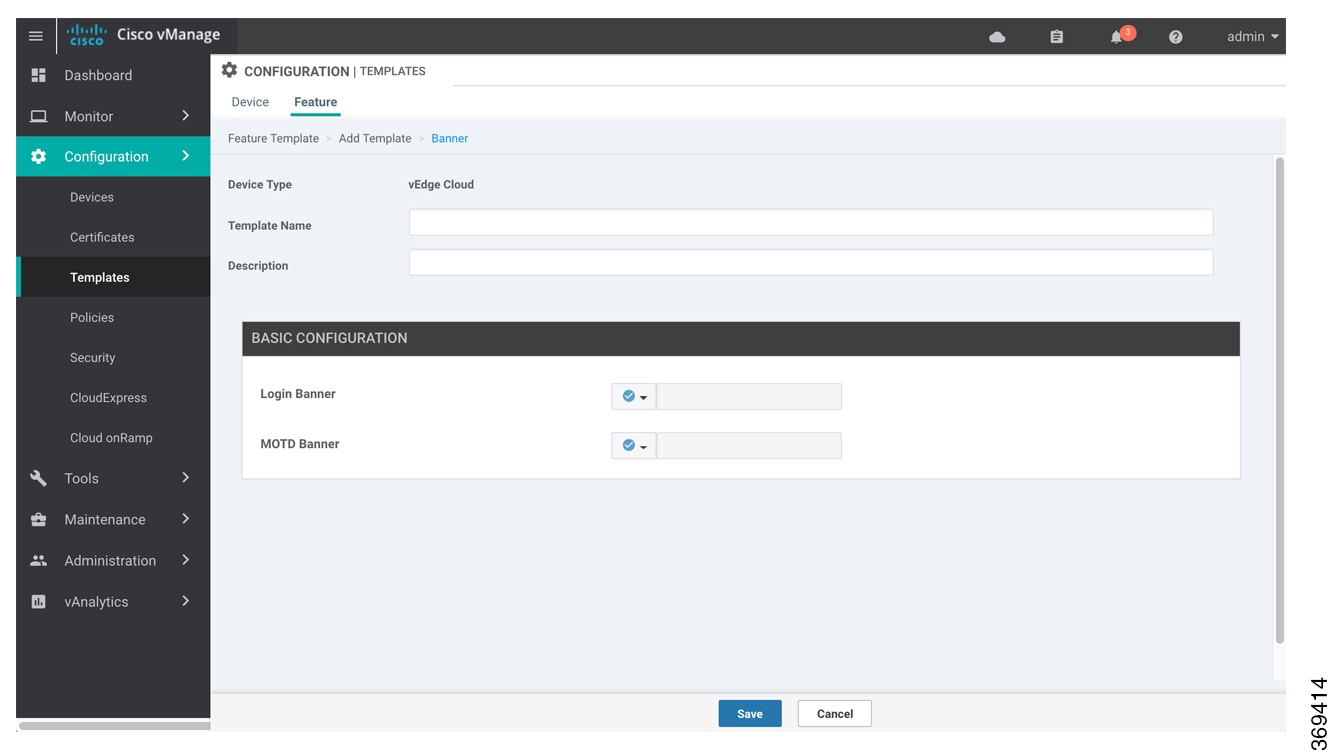
-
In the Template Name field, enter a name for the template. The name can be up to 128 characters and can contain only alphanumeric characters.
-
In the Template Description field, enter a description of the template. The description can be up to 2048 characters and can contain only alphanumeric characters.
When you first open a feature template, for each parameter that has a default value, the scope is set to Default (indicated by a check mark), and the default setting or value is shown. To change the default or to enter a value, click the Scope drop-down to the left of the parameter field.
-
To set a banner, configure the following parameters:
Table 1. Parameters to be configured while setting a banner: Parameter Name
Description
MOTD Banner
On a Cisco vEdge device enter message-of-the-day text to display after a successful login. The string can be up to 2048 characters long. To insert a line break, type \n.
On a Cisco IOS XE SD-WAN device enter message-of-the-day text to display prior to the login banner. The string can be up to 2048 characters long. To insert a line break, type \n.
Login Banner
Enter text to display before the login prompt. The string can be up to 2048 characters long. To insert a line break, type \n.
-
To save the feature template, click Save.
CLI equivalent:
banner{login text | motd text}
banner{login login-string | motd motd-string}
Release Information
Introduced in Cisco vManage NMS in Release 15.2.
Create a Custom Banner
To create a custom banner that is displayed after you log in to the Cisco vManage:
-
Click the Edit button to the right of the Banner bar.
-
In the Enable Banner field, click Enabled.
-
In the Banner Info text box, enter the text string for the login banner or click Select a File to download a file that contains the text string.
-
Click Save.
Enable Reverse Proxy
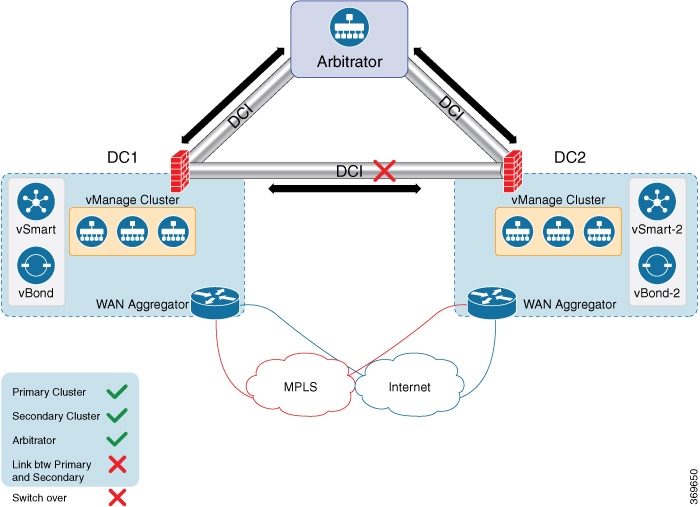
In a standard overlay network, vEdge routers initiate direct connections to the Cisco SD-WAN controllers—Cisco vManage and Cisco vSmart Controllers—over which they exchange control plane information. Because vEdge routers are typically located in branch sites and hence access the Cisco SD-WAN controllers over the internet, the result is that Cisco vManage and Cisco vSmart Controllers have connections directly to the internet.
If, for security or other reasons, you do not want these devices to have direct internet connections, you can insert a reverse proxy between the Cisco SD-WAN controllers and the vEdge routers. The reverse proxy acts as an intermediary to pass control traffic between the Cisco SD-WAN controllers and the vEdge routers. So instead of communicating directly with Cisco vManage and the Cisco vSmart Controllers, the vEdge routers communicate directly with the intermediate proxy device, and the proxy device relays the traffic to and from Cisco vManage and Cisco vSmart Controller controller devices.
The following figure illustrates a reverse proxy inserted between a Cisco vEdge device and the vSmart and vManage controllers.
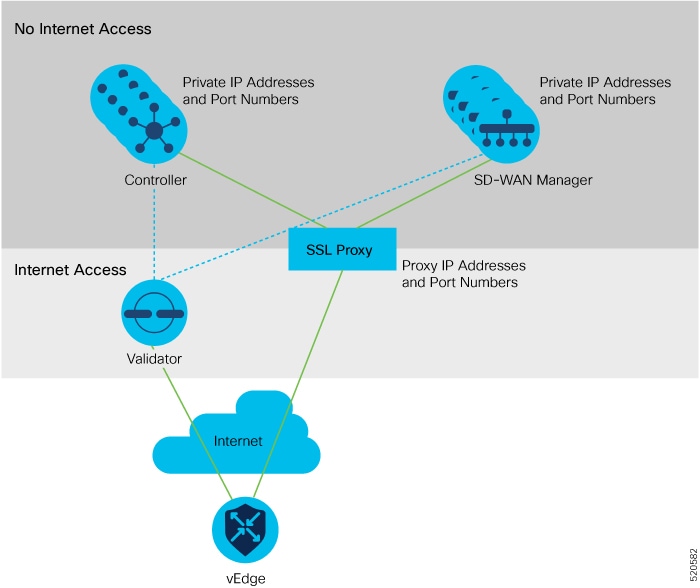
Enable Reverse Proxy
To enable reverse proxy services in the overlay network:
-
Click the Edit button to the right of the Reverse Proxy bar.
-
Click Enabled.
-
Click Save.
To configure reverse proxy on individual Cisco vManage and Cisco vSmart Controller devices, in Cisco vManage, select and click the Controllers tab. For the desired device, click the More Actions icon to the right of the row, and click Add Reverse Proxy. Configure the private and proxy IP addresses and ports for the device.
Provision Certificates on the Proxy
For reverse proxy to work, the reverse proxy device and the vEdge routers must authenticate each other.
On the reverse proxy device you must provision a certificate that is signed by the same CA with which the Cisco SD-WAN controller's certificate is signed.
On the reverse proxy, you also need to provision the Cisco vManage certificate bundle exported form Cisco vManage. This certificate is used by the reverse proxy to verify the vEdge routers. To do this:
-
In Cisco vManage, select the Configuration ► Certificates screen.
-
Click Controllers in the top bar.
-
Click Export Root Certificate in the top bar.
Configure Reverse Proxy on Controllers
To configure reverse proxy on individual Cisco vManage and Cisco vSmart Controller devices:
-
In Cisco vManage select the Configuration ► Devices screen.
-
Click the Controllers tab.
-
For the desired device, click the More Actions icon to the right of the row, and click Add Reverse Proxy. The Add Reverse Proxy popup is displayed.
-
Click Add Reverse Proxy.
-
Configure the private IP address and port number for the device. The private IP address is the IP address of the transport interface in VPN 0. The default port number is 12346. This is the port used to establish the connections that handle control and traffic in the overlay network.
-
Configure the proxy IP address and port number for the device, to create the mapping between the private and public IP addresses and port numbers.
-
If the Cisco vManage or Cisco vSmart Controller has multiple cores, repeat Steps 5 and 6 for each core.
-
Click Add.
-
In the Security feature configuration template for Cisco vManage and the Cisco vSmart Controller, set the transport protocol to be TLS.
To display a device's private and proxy (public) IP addresses and port numbers, in the vManage Monitor ► Network screen, select the device, click Real Time, and select the Control Connections command. To display these IP address and pot numbers in the CLI, issue the show control local-properties command.
To verify the mapping between the private and proxy IP addresses and port numbers, issue the show orchestrator reverse-proxy-mapping command on the Cisco vBond Orchestrator.
In the output of the show control connections command on a vEdge router, if the Proxy column value is Yes, the Peer Public IP and Peer Public Port fields show the proxy IP address and port number, respectively, and the output indicates that the connection is the controller device is through the proxy.
Have vEdge Router Generate Certificate
After you configure reverse proxy on the overlay network controllers, any vEdge router that joins the overlay network or that is already operating in the overlay network requires a signed certificate to establish a secure connection to the proxy device. The process for generating the signed certificate is initiated automatically by the vEdge router as soon as it learns that reverse proxy is enabled in the network, and the vEdge router receives a signed certificate that it uses to establish a secure connection to the reverse proxy device.
To view the signed certificate, issue the show certificate reverse-proxy command on the vEdge router.
Collect Device Statistics
To enable or disable the collection of statistics for devices in the overlay network:
-
Click the Edit button to the right of the Statistics Settings bar. By default, all statistics collection settings are enabled for all Cisco SD-WAN devices.
-
To set statistics collection parameters for all devices in the network, click Disable All for the parameter you wish to disable statistics collection for. To return to the saved settings during an edit operation, click Reset. To return the saved settings to the factory-default settings, click Restore Factory Default
-
To set statistics collection parameters for individual devices in the network, click Custom to select devices on which to enable or disable statistics collection. The Select Devices popup screen opens listing the hostname and device IP of all devices in the network. Select one or more devices from the Enabled Devices column on the left and click the arrow pointing right to move the device to the Disabled Devices column on the right. To move devices from the Disabled Devices to the Enabled Devices column, select one or more devices and click the arrow pointing left. To select all devices in the Select Devices popup screen, click the Select All checkbox in either window. Click Done when all selections are made.
-
Click Save.
Set the Time Interval to Collect Device Statistics
To set the time interval at which vManage NMS should collect statistics for devices in the overlay network, use the screen.
-
Click the Edit button to the right of the Statistics Configuration bar. By default, statistics is collected for all Viptela devices every 30 minutes.
-
Click the up or down arrow in the Collection Interval drop-down to change the frequency at which to collect device statistics. The minimum time you can specify is 5 minutes and the maximum is 180 minutes.
-
Click Save.
Enable vAnalytics
-
Open a support case with Cisco, https://mycase.cloudapps.cisco.com/case, and provide the following information:
-
Customer name
-
Organization Name (as configured in vManage)
-
Cisco Sales/SE contact
-
Approved by (customer contact)
-
Customer email
-
Approved by customer on (specify date)
Customer approval is needed as vAnalytics collects network and application-related data (PII data), and this data is stored in the US-West cloud region in Amazon Web Services.
After receiving this information, Cisco takes approximately 24 to 48 hours to ready the backend set up and provide the appropriate log-on credentials for vAnalytics.
Once you receive log-on credentials for vAnalytics: - Navigate to the Cisco vManage Dashboard tab.
- Click the Edit button to the right of the vAnalytics bar.
- In the Enable vAnalytics field, click Enabled.
- Enter SSO Username and SSO Password.
- Check the I agree check box.
- Click Save.
-
Web Server Certificate for vManage
To establish a secure connection between your web browser and the vManage server using authentication certificates, you must generate a CSR to create a certificate, have it signed by a root CA, and then install it. To do so:
-
Click the CSR button to the right of the Web Server Certificate bar.
-
In the Common Name field, enter the domain name or IP address of the vManage server. For example, the fully-qualified domain name of vManage could be vmanage.org.local.
-
In the Organizational Unit field, enter the unit name within your organization, for example, Network Engineering.
-
In the Organization field, enter the exact name of your organization as specified by your root CA, for example, Viptela Inc.
-
In the City field, enter the name of the city where your organization is located, for example, San Jose.
-
In the State field, enter the state in which your city is located, for example, California.
-
In the 2-Letter Country Code field, enter the two-letter code for the country in which your state is located. For example, the two-letter country code for the United States of America is US.
-
From the Validity drop-down, select the validity period for the certificate.
-
Beginning with Cisco IOS XE SD-WAN release 16.11 and Cisco SD-WAN release 19.1, in the Subject Alternative Name (SAN) DNS Names field, enter the names of DNS severs to which the certificate trust should be extended. If you enter more than one DNS server name, separate each name with a space or a comma.
-
Beginning with Cisco IOS XE SD-WAN release 16.11 and Cisco SD-WAN release 19.1, in the Subject Alternative Name (SAN) URIs field, enter the URIs of resources to which the certificate trust should be extended. If you enter more than one URI, separate each URI with a space or a comma.
-
Click Generate to generate the CSR.
-
Send the CSR to your CA server to have it signed.
-
When you receive the signed certificate, click the Certificate button to the right of the Web Server Certificate bar to install the new certificate. The View box displays the current certificate on the vManage server.
-
Copy and paste the new certificate in the box. Or click the Import button, click Select a File to download the new certificate file, and click Import.
-
Restart the application server.
View Web Server Certificate Expiration Date
When you establish a secure connection between your web browser and the vManage server using authentication certificates, you configure the time period for which the certification is valid (in Step 8 in the previous section). At the end of this time period, the certificate expires. The Web Server Certificate bar shows the expiration date and time.
Starting 60 days before the certificate expires, the vManage Dashboard displays a notification indicating that the certificate is about to expire. This notification is then redisplayed 30, 15, and 7 days before the expiration date, and then daily.
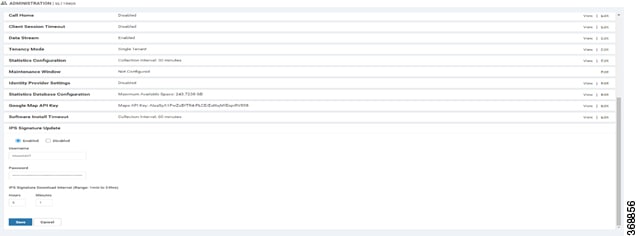
Update IPS Signatures
IPS uses Cisco Talos signatures to monitor the network. Cisco recommends following this procedure to download the latest signatures.
 Note |
To download the signatures, vManage requires access to the following domains using port 443:
|
-
In Cisco vManage, select the tab in the left side panel to configure IPS Signature Update.
-
Click on Edit to Enable/Disable and provide your Cisco.com Username and Password details to save the Policy details as shown in the following screenshot.

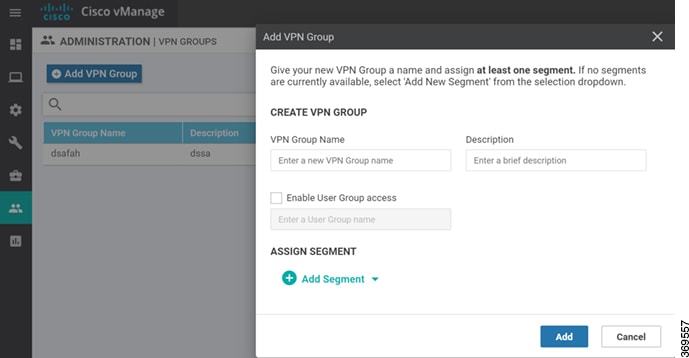
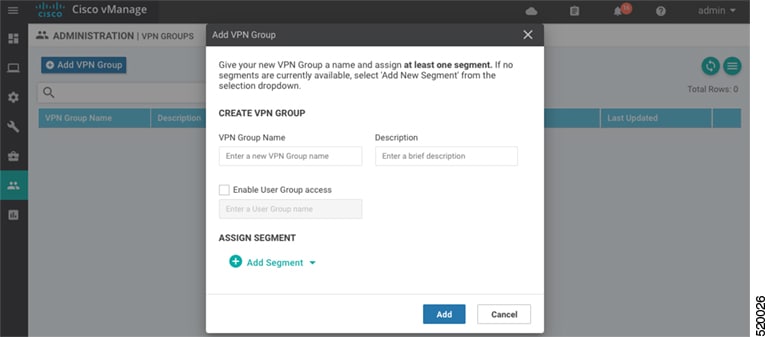
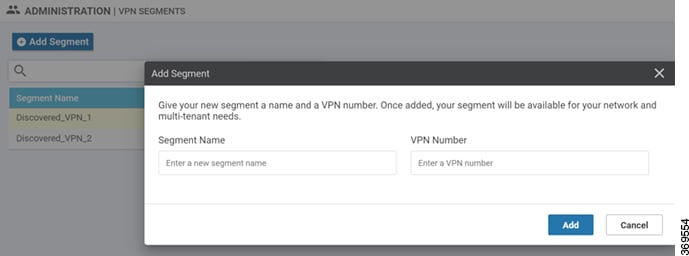
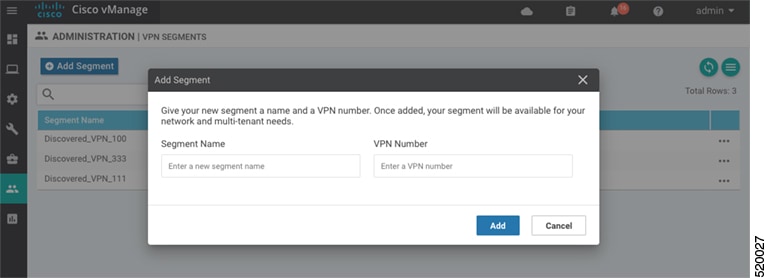
 Feedback
Feedback