Information About Certificates
The following topics provide information on certificates:
Types of Certificates
IoT FND uses the following three types of certificates:
-
Device Certificate
-
Web Certificate
-
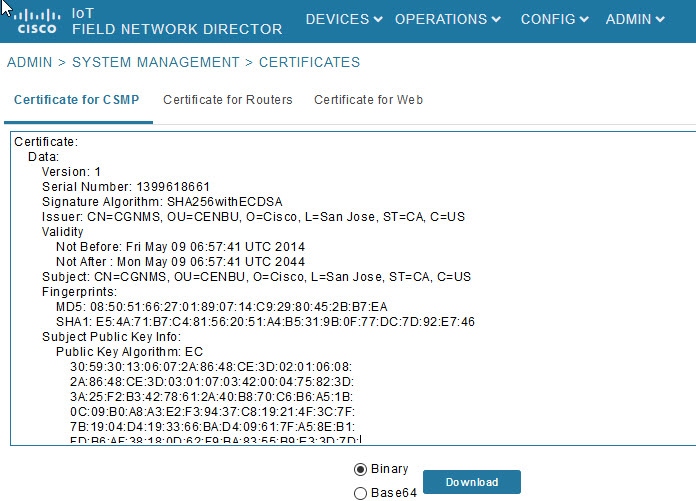
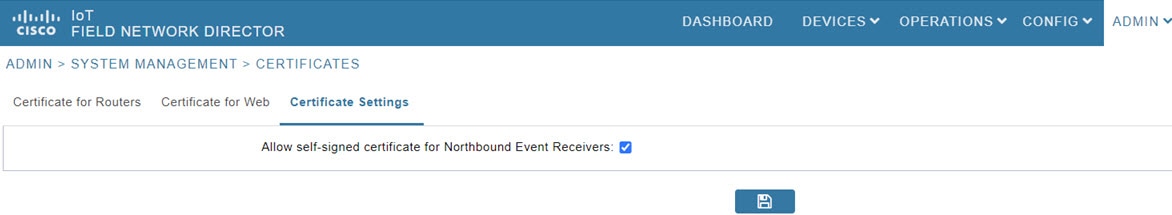
CSMP Certificate
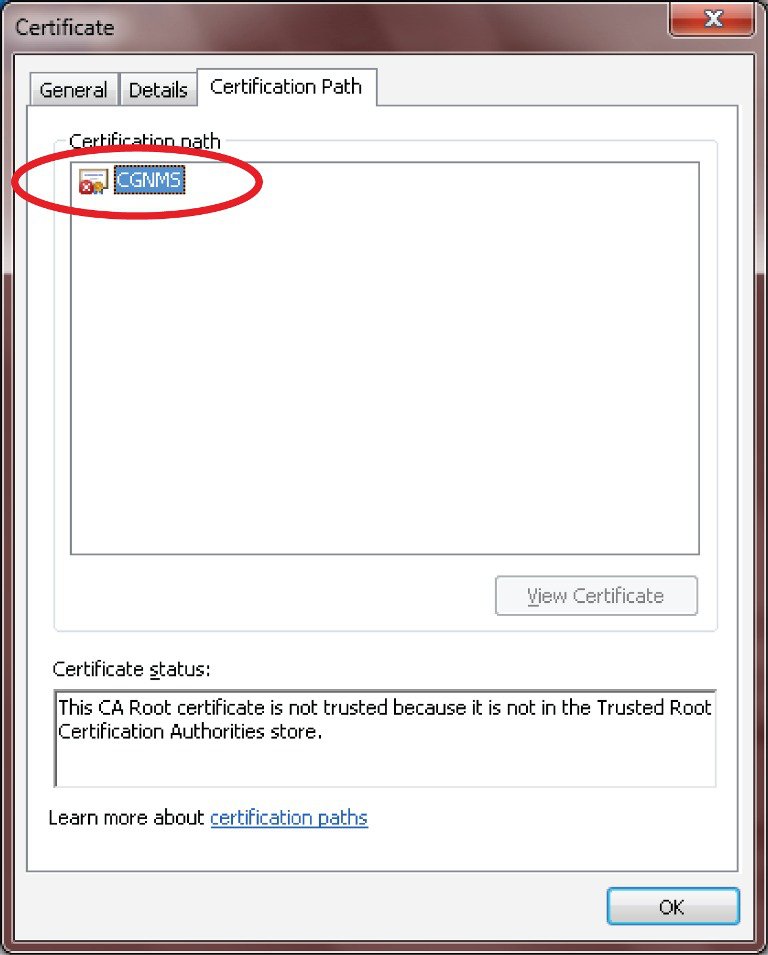
Role of Certificates
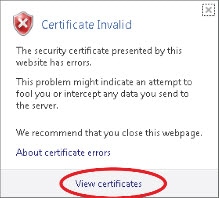
All communications between the CGR1000, IR800s, IR1800s, C800s, ESR C5921s, IR1100, IR8100, IC3000, IXM, and the Cisco Connected IoT Field Network Director (IoT FND) must be authenticated in both directions through mutual authentication. Before mutual authentication occurs, the Cisco IoT FND and the device must each have a certificate that is signed by the same Certificate Authority (CA). You can employ either a root CA or subordinate CA (sub-CA).
For more information on generating certificates for CGRs, refer to Certificate Enrollment Guide for the Cisco 1000 Series Connected Grid Routers.
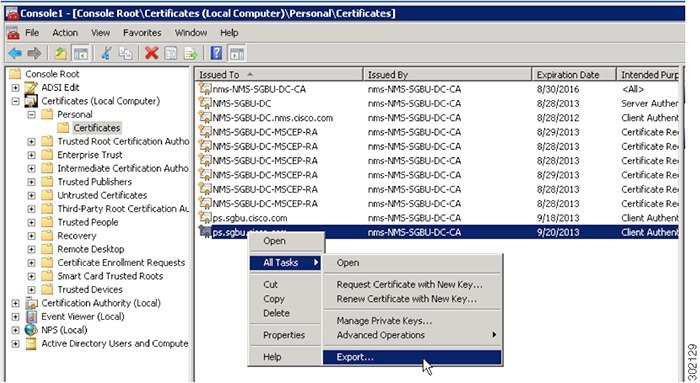
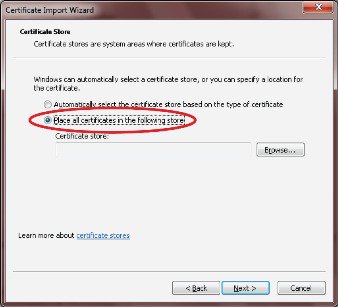
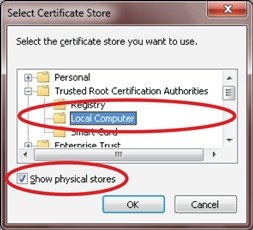
Generating certificates for IoT FND also involves generating and loading certificates on the IoT FND TPS Proxy (tpsproxy). After generating the certificates, import them into the storage location on the TPS proxy and IoT FND known as the Keystore.
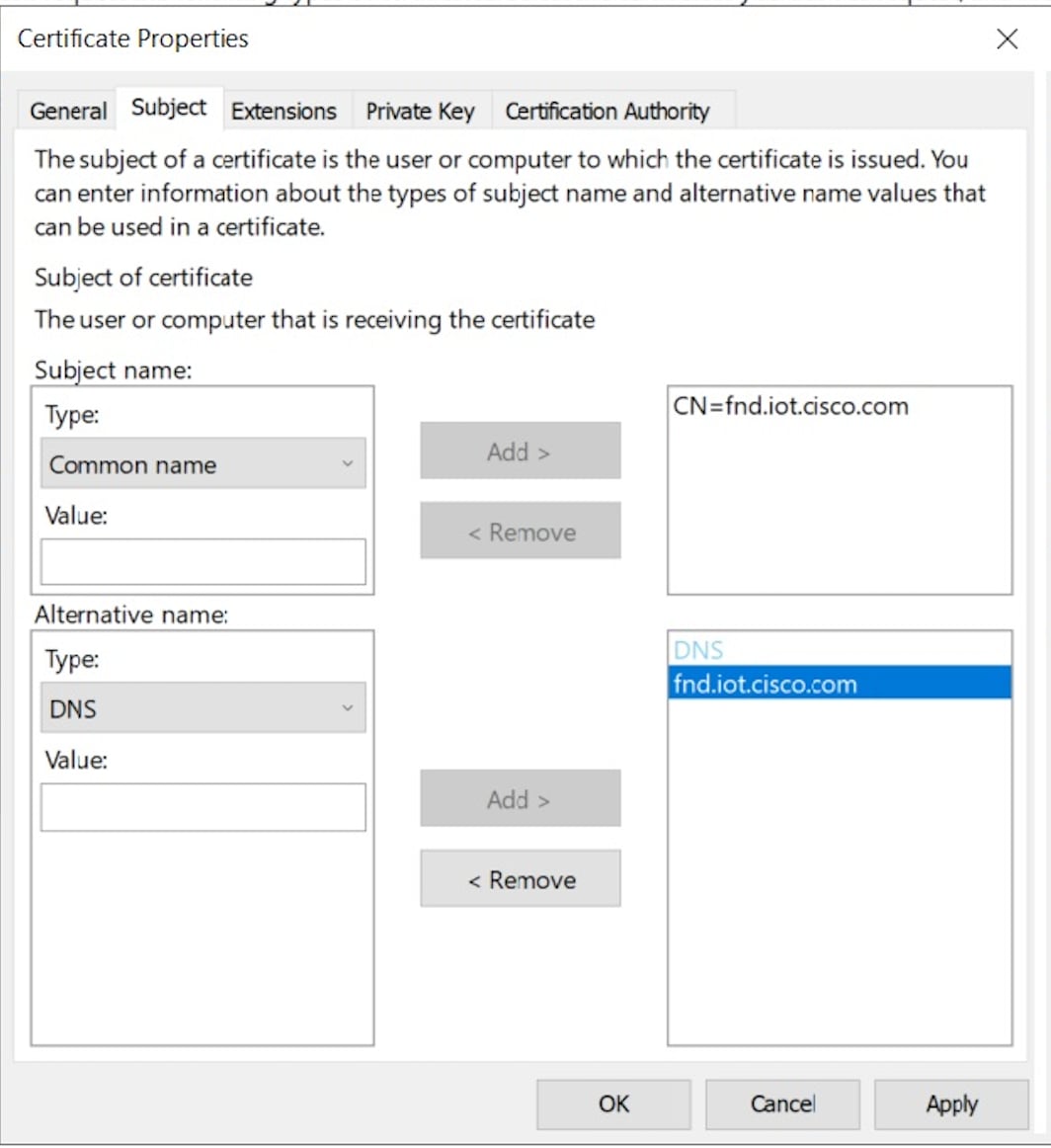
Keystore
The keystore provides details for a specific system such as IoT FND server or TPS proxy. IoT FND server and TPS server use Java keystore to store their own device certificate and the corresponding private keys that are referenced using an alias.
The following table lists the certificate types used by IoT FND and the keystore location of the certificates:
|
IoT FND Certificate Type |
Keystore Location |
|---|---|
|
Device Certificate |
|
|
Web Certificate |
|
|
CSMP Certificate |
HSM or SSM |
 Note |
By default, the |
The keystore must contain the following information:
-
Cisco SUDI or the device manufacturing certificate.
-
The root CA certificate of the issuing root CA or sub-CA server.
-
The certificate that is generated for FND server or TPS server for TPS (private key for the system).
 Note |
The IoT FND key and the certificates are stored in |
 Feedback
Feedback